
CTI is So Critical to SOC Teams for DNS Security
Google reported that it served more than 400 billion DNS queries per day.[1] Furthermore, Let’s Encrypt issues around 600,000 digital certificates per day. These statistics alone can show how critical DNS security is.
Many monitoring tools will demonstrate great detail on what happens within the network, but it can be a struggle to get a good insight into the external world. Such tools sharpen your worldview outside of your firewall and monitor adversaries and suspicious activity using domain signaling and DNS space. These signals are crucial for any threat intelligence response, as it can make a difference to sort benign from attackers by knowing the root of attack, history, threat ranking, and ownership associated with any IP addresses or domains.
Security teams may gain crucial awareness into potentially malicious behaviors and broader knowledge from their knowledge of DNS functions to inform quick response and preventive efforts to DNS attacks.
What is DNS and how it works?
The Domain Name System (DNS) is the phonebook of the Internet.[2]
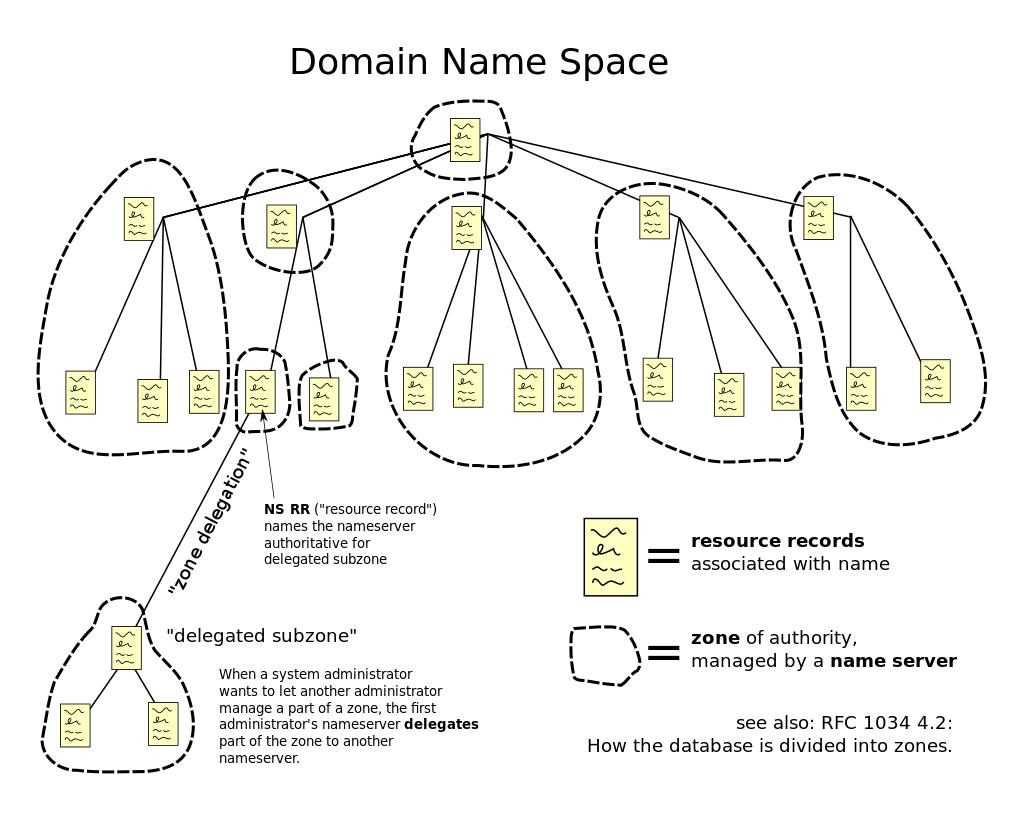
Source
The Internet Protocol (IP) addresses to communicate with web browsers. In order to allow browsers to load Internet services, DNS converts domain names into IP addresses.
When type, let’s say, www.socradar.io on your browser;
- If the DNS records are located in your computer’s DNS cache, you’ll be taken straight to www.socradar.io to avoid the remainder of your DNS quest.
- If no data is detected, a query will be forwarded to your local DNS server. This is typically the directory of your Internet Service and is also referred to as a “resolving nameserver.”
- If the data on the resolving nameserver are not cached then the request to find the DNS records is forwarded to a root nameserver. Root nameservers are named worldwide servers that are responsible for the collection and running of DNS.
- When the DNS records are found, a link is opened to the server where the site is stored and www.socradar.io is seen on the computer.
What is DNS used for?
- Resolving names of World Wide Web (WWW) sites
- Communication between IoT devices, gateways and servers
- Peer-to-peer sharing programs
- Connecting app servers, databases and middleware within a web application
- Routing messages to email servers and webmail services
- Multiplayer games
- Instant messaging and online meeting services
- Virtual Private Networks (VPN)
What is DNSSEC?
DNS Security Extensions were an attempt to protect communication between the different layers of DNS servers. It was developed by ICANN (Internet Corporation for Assigned Names and Numbers), the company responsible for the DNS scheme.
You can do a simple test by visiting http://www.dnssec-failed.org. This site has been specifically configured to return a DNS error due to a broken authentication chain. If you don’t receive an error, you are not using DNSSEC.
What is DNS intelligence?
It is possible to describe DNS intelligence as all the intelligence data from the DNS system and user interactions.
DNS intelligence plays a vital role in any OSINT and data collection policy when you look at a particular goal from a red team point of view, or when you do the blue teaming in order to avoid cyber attacks by checking and doing analysis on your own assets.
Data intelligence includes;[3]
- Associated IPs: In a similar manner, you can detect related IPs on the same network by looking into DNS information
- Forward DNS records: All present DNS records on the current website
- DNS historical records: Historical DNS records from days, months or years ago
- Subdomain mapping: By accessing all current DNS records, you can also perform subdomain enumeration for current and past subdomains over a period of time
- Reverse DNS records: Current rDNS records obtained by performing a reverse DNS lookup
- Registrar name servers: Current NS records at the domain registrar
- Glue record history: DNS records created at the domain registrar
- Historical registrar name servers: Past information about NS used on the registrar, going back by years
- DNS software identification: Software information for the DNS server you’re running, including name and current version
- Associated domain names: DNS intelligence also provides the ability to detect associated domains hosted on the same networks as the main apex domain
How CTI can be used for DNS security?
Due to its omnipresence, DNS gives sophisticated threat actors an extremely desirable way of utilizing the DNS system with a range of threat vectors.
The following picture illustrates numerous cases in which actors use DNS for attacks. An example is that a domain name close to a well recognized domain can easily be missed by a phishing email customer, or an attacker can register domain names that are intended to misrepresent the destination of a victim. Known as typosquatting.
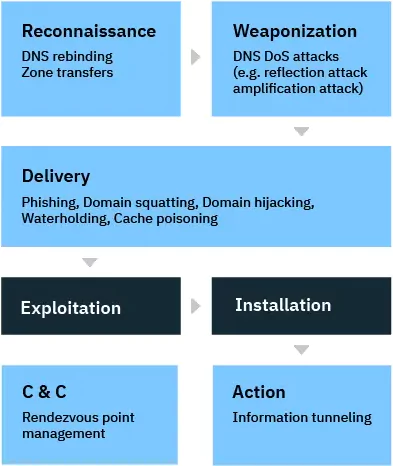
Source
The DNS protocol is also one of the few device protocols approved to cross organizations’ network perimeters. As such, DNS offers threat actors and botnet operators a platform by which they can create hard-to-block and steady contact chains between infected devices and C&C (command-and-control) infrastructures.
The enhancement of DNS’s threat intelligence requires some attributes from the DNS distributor to identify DNS attack trends that are still missing for many conventional DNS vendors. This intelligence typically depends on query logging and reporting. After the review of the results, possible internal DNS-based threats can be identified.
Which attacks can be detected by monitoring DNS?
Business email compromise
Business email compromise (BEC) is an attack in which an attacker gains access to a business email account and imitates the identity of the owner in order to defraud the company, its employees, customers, and partners.
CTI platforms would easily identify BEC attacks as a key risk to organisations, especially ones paying many large accounts; and therefore analyse the processes and procedures for accounts/receivable.
APT attacks
Advanced persistent threat (APT) is a sophisticated, long-term malicious attack that seems to play the long game by spying on the target infrastructure for months or years before successfully breaking through the network.
Cyber threat intelligence (CTI) helps you understand APT groups’ intents and tactics so you can stay ahead of attacks, instead of just reacting to them.
Phishing attacks
Phishing refers to an attacker’s attempt to steal a user’s personal information, resulting in the theft of personal information such as email addresses, phone numbers, and passwords. If a fraudster can trick someone into clicking on a malicious link in a personal app, the trick can give the fraudster access to his or her phone details as well as their credit card and bank account details.
A good CTI platform such as SOCRadar analyzes millions of domains across most major domain registrars to detect malicious domains targeting your brand and entire business network. Alerts are triggered whenever anything changes on the detected suspicious domain. Machine learning algorithms allow SOCRadar to analyze a vast collection of domain data to unveil lookalike domains. At the same time, real-time alerts will enable you to get notified before your domains and SSL certificates are expiring keeping your digital presence secure.
Which steps should be taken for DNS security?
Following steps need to be taken in defense side for DNS security;
- Create next-gen DNS-based firewalls
- Create other DNS-based email blocking lists
- Monitor brand usage and copyright violations
- Find and remove unknown, old and stale DNS records
- Find malicious domain and subdomain names
- Build a complete map of all domains and their DNS records
- Investigate malware campaigns
- Detect phishing attacks
- Prevent subdomain attacks by analyzing stale DNS records
What are the top DNS threat intelligence tools?
There are many tools available on the market for DNS intelligence, most popular ones, however, listed below;
DNSRecon
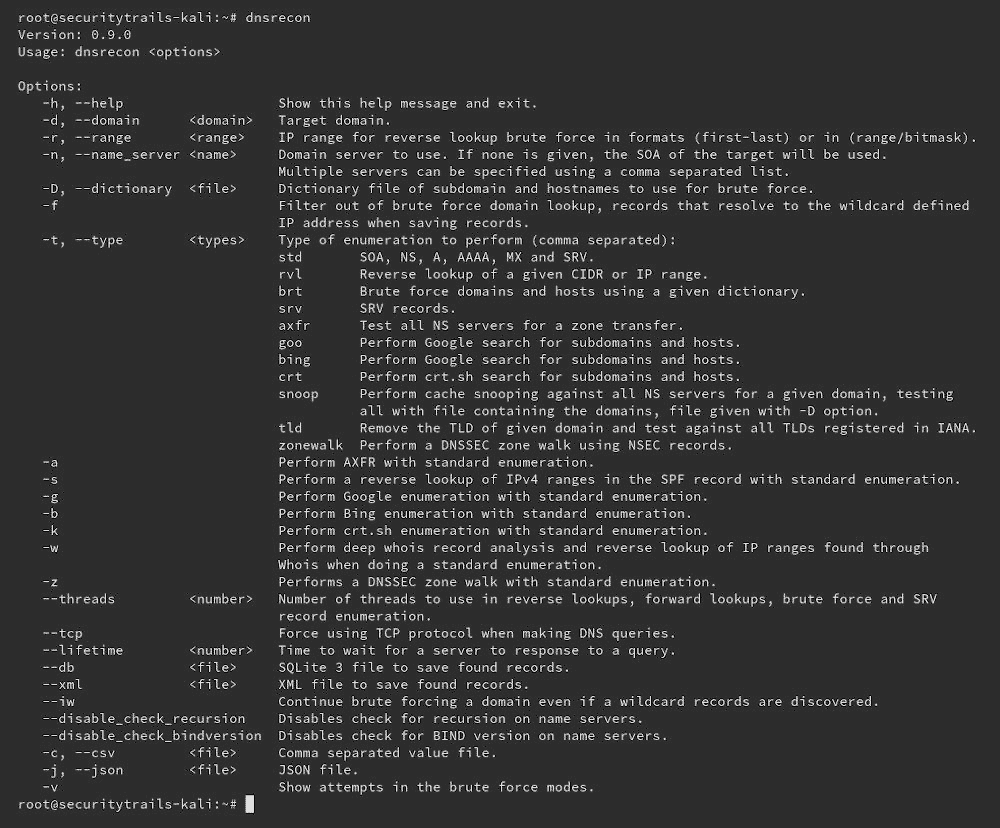
DNSRecon provides the ability to perform:
- Check all NS Records for Zone Transfers.
- Enumerate General DNS Records for a given Domain (MX, SOA, NS, A, AAAA, SPF and TXT).
- Perform common SRV Record Enumeration.
- Top Level Domain (TLD) Expansion.
- Check for Wildcard Resolution.
- Brute Force subdomain and host A and AAAA records given a domain and a wordlist.
- Perform a PTR Record lookup for a given IP Range or CIDR.
- Check a DNS Server Cached records for A, AAAA and CNAME Records provided a list of host records in a text file to check.
OWASP Amass

The OWASP Amass Project performs network mapping of attack surfaces and external asset discovery using open source information gathering and active reconnaissance techniques. Including;
- Brute forcing,
- Reverse DNS sweeping,
- NSEC zone walking,
- Zone transfers,
- FQDN alterations/permutations,
- FQDN Similarity-based Guessing
SOCRadar DNS Monitoring
Many attack vectors are leveraged by attackers and organizations address these threats using multiple layers of perimeter security. These include next-generation firewalls, secure web gateways, sandboxing, intrusion prevention systems, anti-virus, EDR and more. Yet despite these safeguards, bad actors continue to find ways by exploiting gaps outside of your perimeter. Over the last few years, a large number of organizations have been affected by DNS record manipulation (DNS Hijacking) including telecoms, ISP providers and infrastructure providers. In addition to global-scale mass scanning of SSL certificates related to your domain, SOCRadar has the capacity to monitor auto-discovered DNS records with an interval of 10 minutes and generates real-time email alerts if there’s any change in A, AAAA, CNAME, NS, MX, SPF, DKIM, DMARC records.
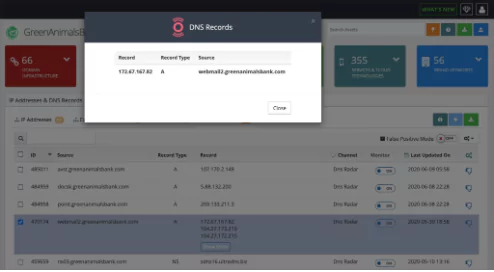
SOCRadar DNS Monitoring includes;
- Scalable continuity: Continuously monitor all of your domain DNS infrastructure.
- Auto-discovery: Discover, map and monitor your DNS configurations automatically.
- Rogue DNS server alerts: Get alerted immediately when DNS records are changed.
- Dynamic DNS: Detect malicious dynamic DNS hostnames targeting your brand.
- Stop sender fraud: Reduce the risk of malicious forgeries by monitoring the existence of SPF and DMARC.
- Open zone transfer risk: Detect if you’re revealing hostnames, subdomains and other DNS records publicly.
- Unsecured Recursive Resolvers: Detect if you’re at risk of being part of DNS amplification DDoS attacks.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































