
What is a Security Operations Center (SOC)? (Ultimate Guide)
A Security Operation Center (SOC) is a centralized function inside an organization that uses people, processes, and technology to continually monitor and enhance an organization’s security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents. Security analysts, engineers, and managers who supervise security operations are usually found in security operations centers.
Staff from the SOC collaborate closely with organizational incident response teams to ensure that security vulnerabilities are handled as soon as they are discovered.
A security operations center (SOC) must recognize threats and evaluate them, investigate the source, report on any weaknesses uncovered, and devise plans to prevent repeat occurrences. In other words, they’re dealing with security issues in real-time while also looking for methods to strengthen the company’s security posture.
SOCs are critical to reducing the costs of a possible data breach since they assist firms in responding swiftly to breaches and work to enhance detection and prevention methods over time.
Most major corporations have their own SOCs, but those without the human resources or resources to do so may choose to outsource part or all of their SOC obligations to a managed service provider (MSP), the cloud, or a hosted virtual SOC.
SOCs may be found in various areas, including healthcare, education, banking, e-commerce, government, military operations, and sophisticated technology.
How Do Security Operation Centers (SOCs) Work?
The SOC leads real-time incident response and pushes continuing security enhancements to defend the enterprise from cyber threats. A well-functioning SOC will give the following benefits by employing a complicated combination of the proper technologies and the right people to monitor and control the whole network:
- Continuous behavioral monitoring entails reviewing all systems 24 hours a day, seven days a week, all year. As a result, SOCs may provide equal weight to reactive and proactive efforts because anomaly inactivity is identified immediately. Behavioral models may be used to educate data gathering systems on what actions are suspect and alter data that may register as false positives.
- Keeping activity records allows members of the SOC team to go back in time and discover past acts that may have led to a breach. The SOC should keep track of all communications and activities inside a company.
- Threat detection and intelligence capabilities that evaluate the source, effect, and severity of each cyber event
- Reporting to guarantee that all incidents and threats are fed into the data repository in the future, making it more accurate and responsive.
- Compliance management is essential for ensuring that members of the SOC team and the company adhere to regulatory and organizational requirements when executing business goals. Typically, one team member is in charge of compliance education and enforcement.
- The SOC team is also in charge of the security center’s operation, management, and upkeep as an organizational resource. This situation entails formulating an overarching strategy, plan, and processes to support the center’s operations. The group also assesses, deploys, and manages tools, devices, and applications and oversees their integration, maintenance, and updates.
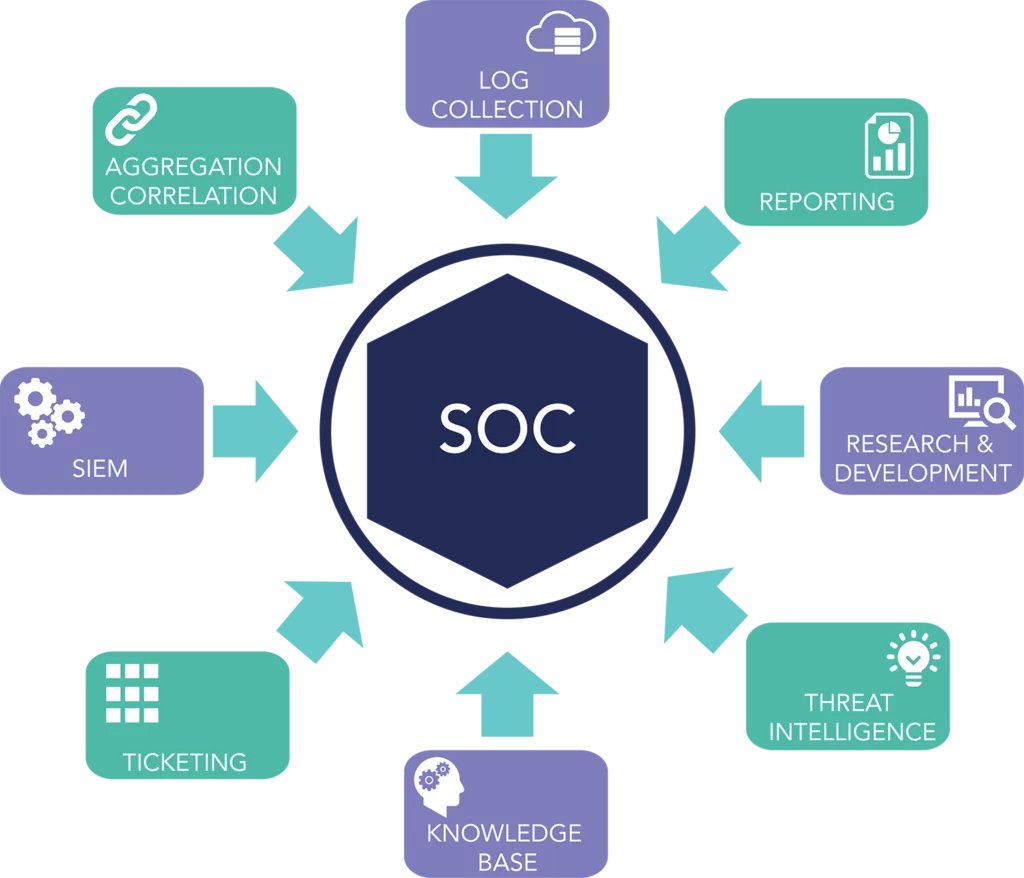
In addition to managing specific incidents, the SOC gathers data feeds from each asset to build a baseline picture of regular network activity. The SOC then employs this information to detect unusual activity with incredible speed and precision.
One of the SOC’s most essential features is that it constantly runs, offering monitoring, detection, and response capabilities 24 hours a day, seven days a week. This helps enterprises shorten their “breakout time” — the critical window between when an intruder compromises the first machine and when they can move laterally to other sections of the network — by ensuring threats are isolated and handled fast.
Are Security Operations Centers (SOC) Doing Enough?
SOCs are maturing, but enterprises recognize that strengthening their performance must be a top priority in the coming year with the heightened threat landscape.
Attackers are always one step ahead of SOC teams. This has gotten increasingly challenging in recent years. The top three problems that any SOC team encounters are listed below:
- Cybersecurity skills shortage: According to a Dimensional Research poll, 53% of SOCs are having trouble finding qualified people. As a result, many SOC teams are understaffed and lack the sophisticated capabilities required to detect and respond to threats quickly and effectively. According to the (ISC)2 Workforce Study, the cybersecurity workforce needs to increase by 145 percent to address the skills gap and effectively protect enterprises worldwide.
- Operational Overhead: Many businesses employ a variety of disparate security systems. This necessitates security workers translating security warnings and regulations between contexts, resulting in costly, inefficient security operations.
- Too many alarms: As businesses add new threat detection capabilities, the number of security alerts continues to rise. This can cause threat weariness, mainly for security professionals already overburdened. Many of these warnings lack sufficient knowledge or context to be investigated, or they are false positives. False positives not only waste time and resources but may also cause teams to become distracted from actual situations.

Vulnerability Management Made Easier
Vulnerability management is critical to a company’s network security. As said earlier, a typical organization faces several
The concept of a SOC is a good one. Still, the costs are considerable, and a successful operation demands employing, allocating resources, and purchasing lots of new instruments with extensive monitoring. In the end, security operations centers will require someone who can be a “cool operator” in a crisis and not take every high-alert event as if it were the significant security incident the SOC has been anticipating.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































