
What is SIM Swapping?
[Update] February 11, 2025: “Guilty Plea in SEC X Account Hijacking and Bitcoin ETF Hoax”
SIM swapping attacks have emerged as a formidable and increasingly prevalent challenge in the ever-evolving cyber landscape.
This sophisticated form of cybercrime involves attackers manipulating cellular service providers to transfer a victim’s phone service to a SIM card under their control.
This malicious act effectively hijacks the victim’s phone number, providing the attacker with unprecedented access to sensitive personal and financial information.
The growing concern around SIM swapping is underscored by a recent high-profile incident involving the U.S. Securities and Exchange Commission (SEC).
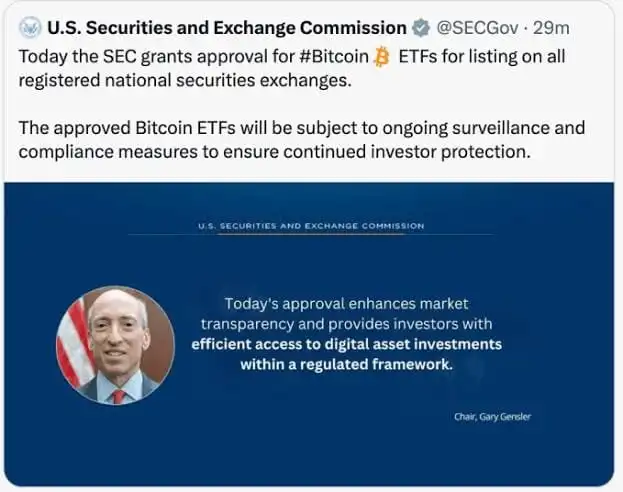
A fake news tweet from hijacked SEC Account (Binance)
In this breach, the SEC’s official account on the social media platform X (formerly known as Twitter) was compromised due to a SIM swap attack.
This incident not only showcased the vulnerability of even the most secure government entities but also highlighted the far-reaching implications of such attacks in the digital age.
Understanding SIM Swapping
SIM swapping, also sometimes falsely known as SIM Hijacking, is a malicious technique that has gained notoriety in the realm of cybercrimes in recent years.
However, there is another meaning that SIM Hijacking refers to: SIM Hijacking (also known as SIM Jacker) remains a persistent vulnerability dating back to 2019, affecting a significant number of SIM cards. This exploit involves sending one or more SMS messages to the target, containing carefully crafted malicious instructions designed to exploit vulnerabilities in SIM card applications, such as S@T Browser or similar programs. These instructions can trigger specific events on the SIM card, ultimately enabling manipulation of the device’s logic, such as a mobile phone.
SIM swapping involves cybercriminals tricking cellular service providers into switching a victim’s service to a SIM card under their control. In essence, it’s a stealthy takeover of the victim’s mobile identity, which can have devastating consequences.
The process of SIM swapping is a complex web of deception, typically initiated by attackers who seek to gain control of a victim’s phone number.
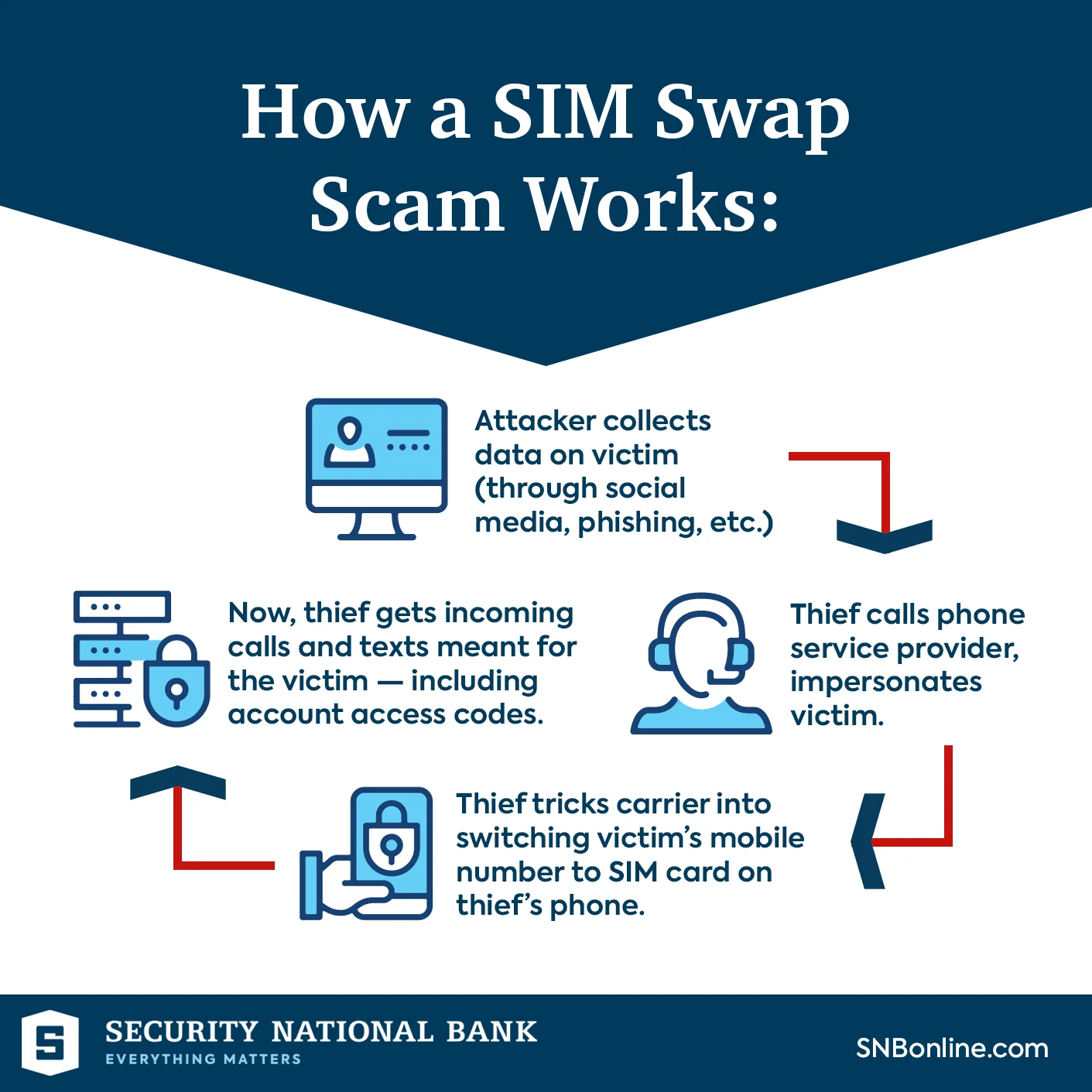
SIM Swap Infographic (Security National Bank)
Here’s how it unfolds:
- Information Gathering: Attackers begin by collecting sensitive information about the victim. This information may be obtained through various means, including data breaches, phishing attacks, or social engineering tactics.
- Impersonation: Armed with the victim’s personal information, the attackers contact the victim’s mobile carrier and impersonate the victim. They may pretend to be the victim seeking a new SIM card due to a lost or damaged phone.
- Manipulating Carrier Employees: The success of a SIM swap often hinges on the attackers’ ability to manipulate carrier employees. This can be achieved through social engineering tactics or, in some cases, bribery. The attackers convince carrier staff to transfer the victim’s mobile service to a new SIM card, often without arousing suspicion.
- Seizing Control: Once the attackers successfully execute the SIM swap, they gain control of the victim’s phone number. This control extends to all aspects of the victim’s digital life associated with that number, including text messages and voice calls.
- Exploitation: With access to the victim’s phone number, attackers can exploit it for various purposes, ranging from intercepting sensitive authentication codes sent via SMS to impersonating the victim in online accounts. This newfound access to the victim’s digital identity can lead to financial losses, identity theft, and other harmful consequences.
It’s important to note that SIM swapping attacks are not limited to individuals; government agencies, corporations, and high-profile individuals have also fallen victim to this insidious form of cybercrime.
The SEC Twitter Breach
One of the most alarming examples of a SIM swapping attack infiltrating the highest points of cybersecurity took place recently, shaking the foundations of digital security. In this incident, the U.S. Securities and Exchange Commission (SEC), the very institution tasked with overseeing financial markets and safeguarding investors, fell victim to a SIM swapping attack.
The breach occurred on January 9, when an unauthorized party gained access to the SEC’s official account on X, formerly known as Twitter. What followed was a brazen act of deception that sent shockwaves through the financial world.
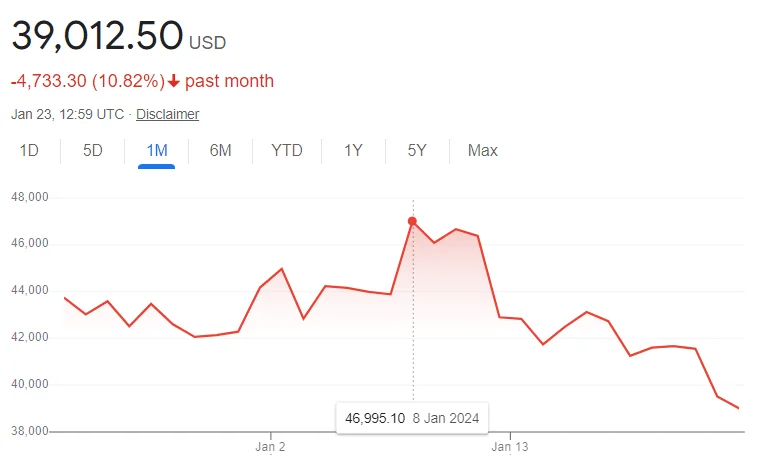
Bitcoin prices around the incident, Graph by Google
The attacker posted a false announcement, claiming that the SEC had granted approval for the first-ever spot Bitcoin Exchange-Traded Funds (ETFs). This fictitious post had an immediate and profound impact on the cryptocurrency market, causing Bitcoin prices to skyrocket to nearly $48,000 from a daily low of just above $45,000. However, the euphoria was short-lived, as the SEC promptly clarified that no such approval had been granted. Consequently, Bitcoin prices plunged below $46,000.
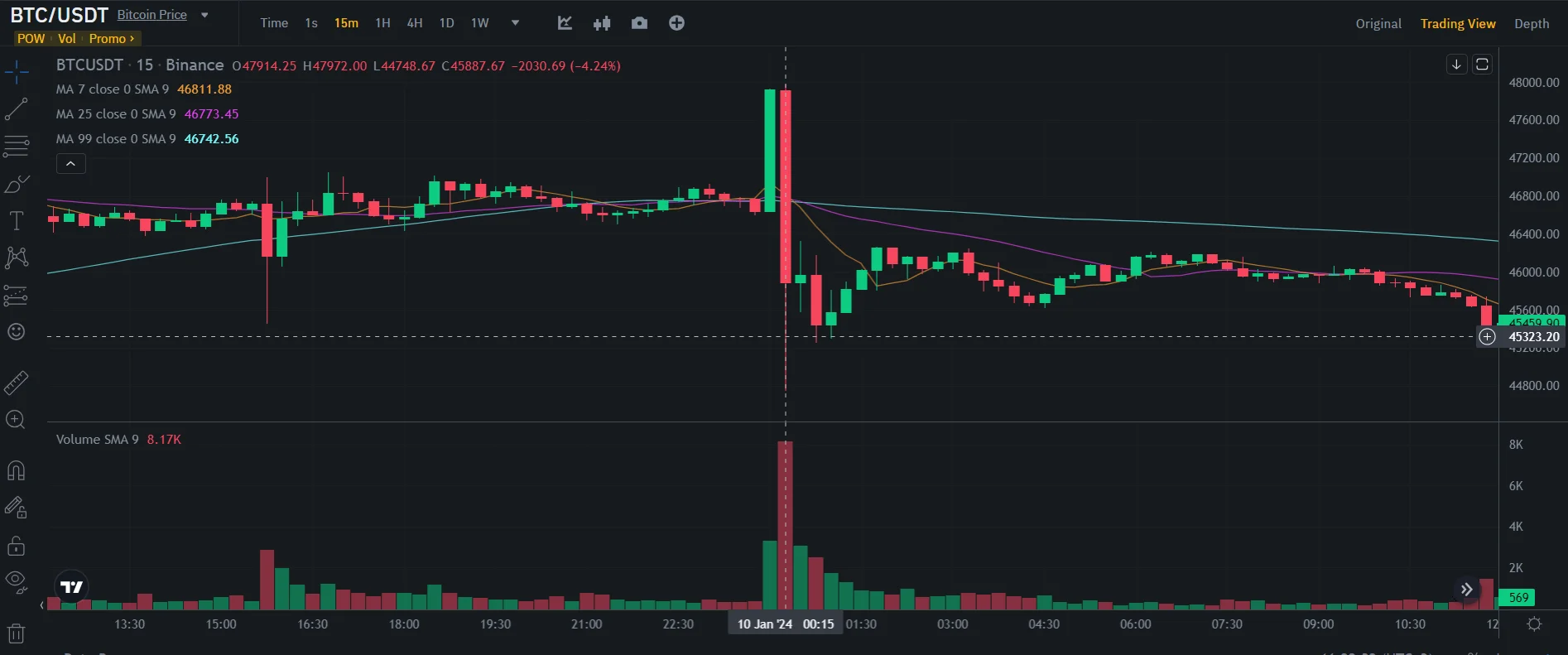
Sharp drop just around the time of the announcement (Binance)
In the aftermath of this high-profile incident, the SEC launched an investigation into the breach. It was determined that the unauthorized party had gained control of the SEC’s cell phone number associated with the compromised account through a “SIM swap” attack. This devious maneuver grants the attacker access to all SMS messages and voice calls intended for the victim.
Currently, it is not clear exactly how the phone number was obtained. According to the SEC, law enforcement is currently conducting an investigation to determine how the attacker discovered the specific phone number associated with its X account and the method employed to persuade the mobile carrier to initiate a SIM card replacement.
With control of the SEC’s phone number secured, the unidentified attacker proceeded to reset the account password. Astonishingly, due to a critical security oversight, the SEC did not have Two-Factor Authentication (2FA) enabled for the compromised account. Consequently, the SIM swap and the subsequent password change were the only two steps necessary for the attacker to gain full access to the agency’s official account on X.
The security lapse in this incident was further exacerbated by the fact that Multi-Factor Authentication (MFA) had been previously enabled on the @SECGov X account. However, MFA had been disabled by X Support in July 2023, based on staff requests citing difficulties in accessing the account. It remained disabled until after the account was compromised on January 9. The SEC asserted that it had the capability to re-enable Two-Factor Authentication for their X account and was not reliant on X to do so.
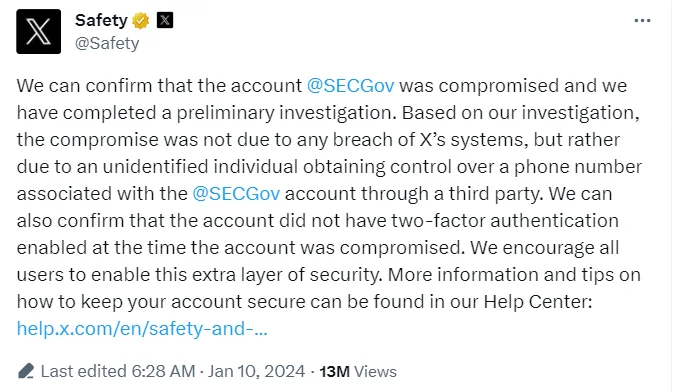
Statement of X about the SEC incident (X)
X’s owner and Chief Technology Officer, Elon Musk, took the opportunity to mock the SEC, an agency he has had contentious interactions with for years. Musk also retweeted a post from Twitter Safety, affirming that the compromise “was not due to any breach of X’s systems.” The incident prompted questions about X’s continued cooperation with investigators and potential changes to its design or features associated with government agency accounts in response to the SEC account breach.
This incident, in which we can see how dangerous and far-reaching it is and how many people and institutions are affected, has revealed the danger. But we must continue to look at how wide the attack surface is.
Guilty Plea in SEC X Account Hijacking and Bitcoin ETF Hoax
In an important update to the SEC X hack, Eric Council Jr., a 25-year-old man from Alabama, has pleaded guilty for the cyber attack. Council had initially pleaded not guilty but now faces a maximum penalty of five years in prison after admitting his role in the scheme.
Council used fraudulent identification to gain control of the phone number of the SEC account’s custodian, resetting the account password and enabling the posting of a fake announcement about Bitcoin ETFs. This fraudulent post caused Bitcoin’s value to surge by $1,000 before quickly plummeting after the SEC confirmed the account was compromised.
As part of his plea, Council admitted to working with co-conspirators who paid him $50,000 in Bitcoin to further the attack. The authorities found that Council was also searching for information related to an FBI investigation into his actions. He is scheduled for sentencing on May 16, 2025.
For more details, you can refer to the full press release from the U.S. Department of Justice.
Risks and Impacts of SIM Swapping
As SIM swapping attacks continue to occur the risks and impacts associated with this cybercrime have become increasingly severe. Beyond the financial losses incurred by individuals, these attacks now pose significant threats to government agencies, corporations, and individuals of influence.
Here, we delve into the risks and far-reaching impacts of SIM swapping:
- Target Diversity: Originally, SIM swapping attacks flourished as a means for cybercriminals to hijack an individual’s cryptocurrency wallet or account. However, these attacks have evolved and diversified in their targets. Government agencies, corporations, and even influential individuals are now in the crosshairs of SIM swappers, amplifying the potential damage.
- Financial Consequences: SIM swapping can lead to devastating financial losses for individuals and organizations alike. Attackers who gain control of victims’ phone numbers can intercept sensitive financial information, such as authentication codes and transaction confirmations. This allows them to conduct fraudulent transactions, steal funds, and wreak havoc on victims’ financial lives.
- Identity Theft: SIM swapping opens the door to identity theft on a grand scale. Attackers can assume the digital identity of victims, accessing their emails, social media accounts, and personal data. This stolen identity can be exploited for further malicious activities, including spreading disinformation and conducting reputational damage campaigns.
- Disinformation and Reputation Damage: Increasingly, SIM swapping attacks have been used to seize control of influential social media accounts. Attackers may use these accounts for pump-and-dump stock schemes, spreading disinformation, or tarnishing the reputation of high-profile individuals or organizations. The dissemination of false information through compromised accounts can have far-reaching consequences, both financially and in terms of reputation.
- Nation-State Involvement: SIM swapping attacks are no longer limited to individual criminals. Nation-states and organized cybercrime groups have recognized the potential of these attacks and have incorporated them into their repertoire of cyber weaponry. This raises concerns about the implications of state-sponsored SIM swapping attacks on national security and international relations.
- Continuing Vulnerabilities: Despite the growing severity of SIM swapping attacks and their expanding target base, many organizations and agencies continue to make basic security mistakes. Inadequate security protocols, lack of multi-factor authentication, and failure to recognize the evolving threat landscape leave entities vulnerable to these attacks.
In summary, the risks and impacts of SIM swapping extend far beyond the initial financial losses incurred by individuals. These attacks have the potential to disrupt financial markets, damage reputations, and even pose national security risks when government agencies are targeted.
Prevention and Protection Against SIM Swapping
A factor that greatly increases the danger of SIM Swapping is that there is no definitive solution, but some precautions are of course valid.
The rising prevalence and evolving sophistication of SIM swapping attacks necessitate proactive measures to safeguard individuals, organizations, and government entities from falling victim to this insidious cyber threat. Here, we outline key strategies for prevention and protection against SIM swapping.
- Employee Training: Educate employees about the risks of SIM swapping and train them to recognize social engineering attempts. Make them aware of the potential consequences of divulging sensitive information.
- Strong Authentication Protocols: Implement robust authentication protocols within the organization. This includes requiring employees to use multi-factor authentication and encouraging the use of authentication apps rather than SMS-based codes.
- Secure Communication Channels: Encourage the use of secure communication channels for sensitive information exchange. Ensure that employees are aware of the risks of discussing confidential matters over unsecured channels.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and weaknesses in the organization’s cybersecurity measures. Address any issues promptly to prevent potential breaches.
- Incident Response Plan: Develop a comprehensive incident response plan that includes specific procedures for addressing SIM swapping incidents. This should involve cooperation with law enforcement and relevant agencies.
- Monitor Account Activity: Implement systems that continuously monitor account activity for unusual or suspicious behavior. This can help detect potential SIM swapping attempts in real-time.
How Can SOCRadar Help?
The most crucial proactive step to address this situation involves staying vigilant regarding the security of various pieces of information, including your Personally Identifiable Information (PII), and taking necessary precautions. This information can potentially be compromised from various organizations’ servers, even without your involvement, and may be offered for sale on the Dark Web. Ultimately, cyber attackers exploit such information for their malicious purposes.
SOCRadar Platform, Dark Web Monitoring
To assist in this regard, the SOCRadar Platform offers a valuable solution known as Dark Web Monitoring. SOCRadar provides a comprehensive Dark & Deep Web Monitoring solution, empowering organizations to detect and counter threats across the surface, deep, and dark web. Leveraging our unmatched reconnaissance capabilities and threat analysis, we provide actionable intelligence to proactively safeguard your organization. The integration of automated external cyber intelligence with a dedicated analyst team enables Security Operations Center (SOC) teams to gain control over the external cyber landscape beyond their traditional boundaries.
Conclusion
In an era where our digital identities hold immense value, the emergence of SIM swapping attacks serves as a stark reminder of the ever-evolving landscape of cybersecurity threats. These attacks, once confined to targeting individuals for cryptocurrency theft, have now evolved to pose substantial risks to government agencies, corporations, and influential individuals. As we conclude our exploration of SIM swapping, it is imperative to reflect on the gravity of this menace and the steps we must take to protect ourselves and our digital assets.
The recent breach of the U.S. Securities and Exchange Commission’s (SEC) official account on X, triggered by a SIM swap attack, underscores the urgency of this issue. This incident revealed not only the vulnerability of even the most secure entities but also the far-reaching consequences of such attacks in our interconnected digital world.
In conclusion, the rise of SIM swapping attacks demands our unwavering attention and concerted efforts. The digital era has granted us unprecedented connectivity and convenience, but it has also exposed us to new vulnerabilities. We must remain vigilant, educate ourselves and our communities, and implement robust security measures. In doing so, we can navigate the digital landscape with greater confidence, safeguarding our identities and assets from the ever-present threat of SIM swapping and other cybercrimes.



































