
What is YARA, YARA v4.5.0 and YARA-X
Effective threat detection and analysis are essential for safeguarding digital assets in cybersecurity. YARA stands as a key tool in the arsenal of cybersecurity professionals, enabling analysts to identify and mitigate threats efficiently. As a rule-based malware detection and classification tool, YARA plays a pivotal role in Cyber Threat Intelligence (CTI), allowing organizations to proactively defend against malicious actors.

YARA, the pattern matching swiss knife for malware researchers (and everyone else)
YARA’s significance lies in its versatility and adaptability in crafting intricate rulesets that pinpoint specific patterns or behaviors indicative of malicious activity. These rules, manually crafted by analysts, serve as the linchpin of threat detection systems, facilitating the swift identification of malware, suspicious files, or malicious behaviors within an organization’s network or systems.
Recent advancements in the YARA ecosystem further enhance its capabilities and relevance in CTI. The release of YARA 4.5.0 introduces enhancements, including performance improvements, bug fixes, and new command-line options, enhancing the tool’s efficacy and usability for cybersecurity practitioners.
Additionally, the continuing development of YARA-X, a Rust-based implementation of YARA, signifies a new era of innovation and scalability within the YARA framework. With promises of improved efficiency and robustness, YARA-X aims to redefine the landscape of malware detection, positioning itself as a formidable successor to its predecessor.
YARA: A Foundation of CTI
YARA stands as a pillar of Cyber Threat Intelligence (CTI), serving as a foundational tool for threat detection, analysis, and classification. At its core, YARA embodies the essence of flexibility and precision, allowing cybersecurity professionals to construct intricate rulesets capable of identifying the subtlest indicators of malicious activity.
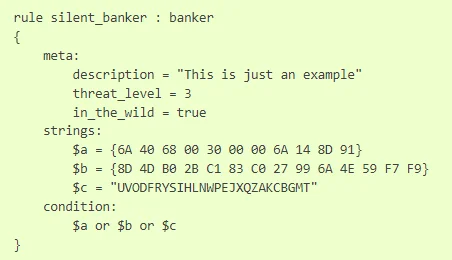
An example rule (YARA by VirusTotal)
YARA, an acronym for “Yet Another Ridiculous Acronym,” is an open-source tool developed by Victor Alvarez of VirusTotal in 2013. Primarily designed for identifying and classifying malware, YARA operates based on a rule-based approach, where analysts define patterns or signatures indicative of malicious behavior.
In the context of CTI, YARA plays a few role:
Threat Detection: YARA enables the proactive detection of malware, suspicious files, and other security threats within an organization’s network or systems. Analysts can swiftly identify and mitigate potential threats by crafting rules that encapsulate the characteristics of known malware families or attack vectors.
Malware Analysis: YARA facilitates the analysis of malware specimens by allowing analysts to define rules that extract specific attributes or behaviors exhibited by malicious code. This capability aids in dissecting and understanding the inner workings of malware, thereby informing incident response strategies and countermeasures.
Threat Intelligence Sharing: YARA rulesets serve as a standardized format for sharing threat intelligence across organizations and security communities. By exchanging YARA rules, cybersecurity professionals can disseminate information about emerging threats, malware variants, and malicious infrastructure, fostering collective defense efforts.
Capabilities and Use Cases:
The versatility of YARA extends across various CTI workflows, enabling a wide range of use cases:
Signature-Based Detection: YARA excels in signature-based detection, where predefined rules are used to identify known malware based on specific patterns or characteristics. Analysts can leverage YARA to create rules targeting file attributes, binary structures, code snippets, or behavioral indicators associated with malicious software.
Behavioral Analysis: Beyond static signatures, YARA supports behavioral analysis by allowing analysts to define rules that capture dynamic behaviors exhibited by malware during execution. This approach enables the detection of polymorphic or obfuscated threats that evade traditional signature-based detection methods.
Indicator Extraction: YARA facilitates the extraction of Indicators of Compromise (IoCs) from malware samples, such as file hashes, network artifacts, Command-and-Control (C2) communications, or registry modifications. Analysts can identify patterns indicative of ongoing or past cyberattacks by correlating these IoCs with threat intelligence feeds or historical data.
Custom Rule Development: One of YARA’s most powerful features is its flexibility in rule creation. Analysts can tailor rules to suit specific organizational requirements, adapting them to target unique threats, proprietary software, or industry-specific malware trends. This capability empowers organizations to customize their threat detection strategies and stay ahead of evolving threats.
How to use it and write the rule deserves to be an important topic. But we have another article for this. Check out our blog post, “Writing YARA Rules with Custom GPTs and SOCRadar Platform!“
YARA 4.5.0: What’s New?
The release of YARA 4.5.0 introduces a host of new features, enhancements, and bug fixes aimed at elevating its capabilities and usability. Let’s check the developments.
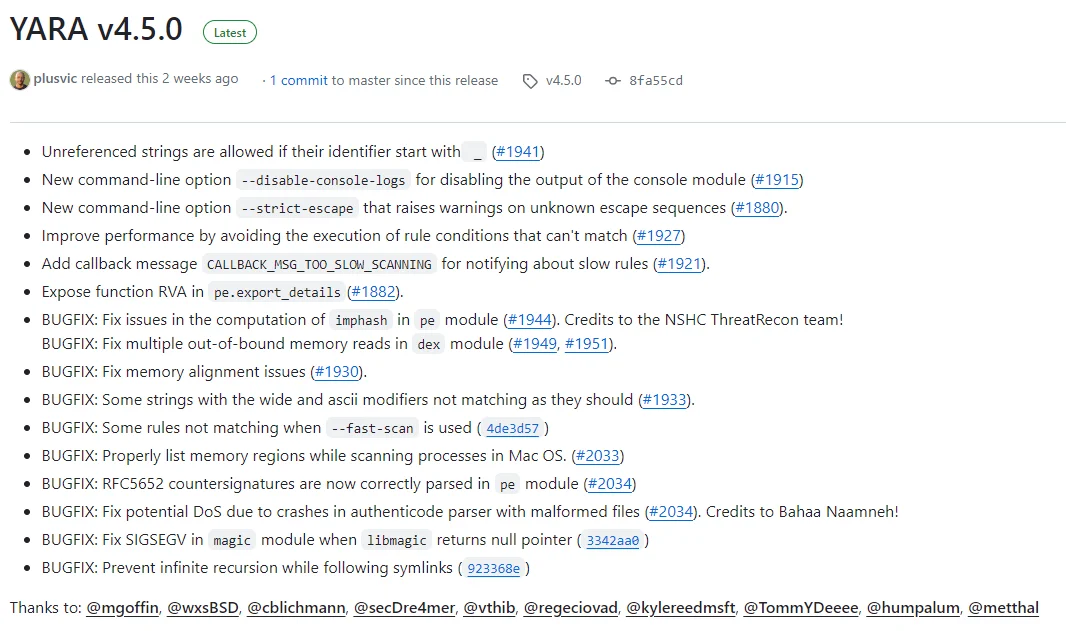
YARA v4.5.0’s changelog in project’s GitHub repository
Enhanced Performance and Usability:
- Unreferenced Strings with ‘_’ Identifier: YARA 4.5.0 introduces support for unreferenced strings if their identifier starts with ‘_’, offering greater flexibility in rule creation. This enhancement simplifies rule development by allowing analysts to include descriptive strings without referencing them explicitly, streamlining the rule-writing process.
- New Command-Line Options: The latest release introduces several new command-line options aimed at enhancing usability and customization:
- –disable-console-logs: This option allows users to disable the output of the console module, reducing clutter in the console output and improving readability during rule execution.
- –strict-escape: YARA 4.5.0 introduces the –strict-escape option, which raises warnings on unknown escape sequences in rule conditions. This feature enhances rule validation and helps identify potential errors or inconsistencies in rule syntax.
Improved Rule Evaluation and Execution:
- Performance Optimization: YARA 4.5.0 includes optimizations to improve performance by avoiding the execution of rule conditions that cannot match, leading to faster and more efficient rule evaluation. This enhancement enhances the scalability of YARA, allowing it to handle larger rule sets and analyze complex malware samples with greater speed and accuracy.
- Callback Message for Slow Scanning: The latest release introduces a new callback message, CALLBACK_MSG_TOO_SLOW_SCANNING, for notifying users about slow rules during scanning. This feature enables analysts to identify and optimize rules that contribute to scanning bottlenecks, ensuring smoother and more efficient threat detection processes.
2.3 Bug Fixes and Stability Improvements:
YARA 4.5.0 addresses several bugs and stability issues identified in previous versions, including:
- Fixes in PE Module: The release includes fixes for issues related to the computation of imphash and multiple out-of-bound memory reads in the Portable Executable (PE) module, enhancing the accuracy and reliability of PE file analysis.
- Memory Alignment and String Matching Fixes: YARA 4.5.0 resolves issues related to memory alignment, string matching with wide and ascii modifiers, and rules not matching when using the –fast-scan option, improving overall rule efficacy and accuracy.
- Enhancements for Mac OS and Authenticode Parsing: The release includes fixes for issues related to scanning processes in Mac OS, parsing RFC5652 countersignatures in the PE module, and potential Denial of Service (DoS) vulnerabilities in the Authenticode parser, enhancing compatibility and security across different platforms and file formats.
YARA-X: The Rust Implementation
YARA-X represents a slight departure from the traditional YARA implementation, leveraging the power and versatility of the Rust programming language to reimagine malware detection and classification. Developed to serve as the future replacement for YARA, YARA-X embodies a commitment to innovation, scalability, and performance.
Key Differences from YARA 4.x:
YARA-X introduces several notable differences compared to its predecessor, YARA 4.x. These differences, while evolving, signify a paradigm shift in rule-based malware detection and analysis:
- Negative Number Handling: YARA-X eschews the acceptance of negative numbers in array indexing, presenting a departure from the behavior observed in YARA 4.x. This change underscores YARA-X’s commitment to strict rule validation and adherence to programming best practices.
- Duplicate Rule Modifiers: Unlike YARA 4.x, which permits duplicate rule modifiers, YARA-X imposes restrictions on the repetition of modifiers within a rule definition. This approach enhances rule clarity and readability, fostering a more structured and consistent rule-writing process.
- <Quantifier> of <Tuple> Statements: YARA-X introduces enhancements to <quantifier> of <tuple> statements, allowing for more expressive and flexible rule definitions. By accepting tuples of boolean expressions, YARA-X expands the scope of rule matching criteria, enabling finer-grained control over threat detection logic.
- Base64 Modifier Limitations: YARA-X imposes restrictions on the usage of the base64 modifier with strings shorter than three characters, mitigating potential false positives associated with base64-encoded data. This refinement enhances the accuracy and reliability of base64-based rule matching, aligning with industry best practices.
- Differential Alphabets for Base64 Modifiers: YARA-X introduces the capability to specify different alphabets for base64 and base64wide modifiers within the same string, offering greater flexibility and customization in rule crafting. This feature enables more precise matching of base64-encoded data, catering to diverse use cases and requirements.
- Behavior of XOR and Fullword Combination: YARA-X alters the behavior of the XOR and fullword combination, ensuring consistency and accuracy in rule evaluation. By XORing bytes before and after the pattern, YARA-X enhances the fidelity of fullword matching, aligning with the intended behavior in most scenarios.
- Hex Pattern Jump Bounds: YARA-X expands the capabilities of hex pattern jump bounds by accepting values in various formats, including hexadecimal and octal. This enhancement enhances rule expressiveness and readability, empowering analysts to craft more robust and versatile rulesets.
- Stricter Escaped Characters in Regular Expressions: YARA-X enforces stricter rules for escaped characters in regular expressions, mitigating potential errors and inconsistencies in rule syntax. This enhancement promotes rule validation and accuracy, minimizing the risk of false positives and enhancing overall rule efficacy.
Conclusion
In the rapidly evolving threat landscape, staying updated with the latest versions and implementations of YARA is paramount for effective CTI. Regularly updating YARA rulesets, monitoring for new releases, and leveraging community contributions can help organizations stay ahead of emerging threats and evolving attack techniques.
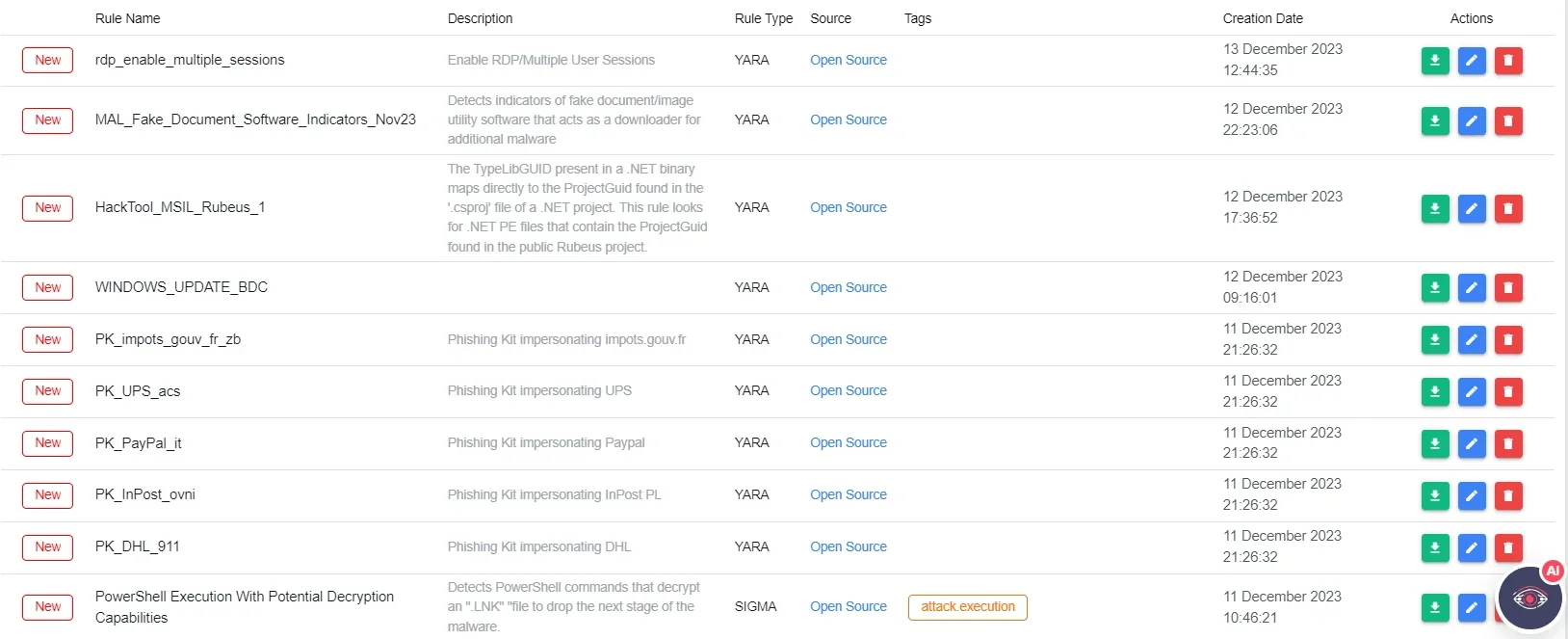
SOCRadar Platform , Threat Hunting Rules
A source for a continuous stream of YARA Rules is the Threat Hunting Rules section on the SOCRadar Platform.



































