
What You Need to Know About Non-Human Identities?
Meta CEO Mark Zuckerberg recently stated that AI will replace mid-level engineers by 2025, taking over coding tasks to allow human developers to focus on innovation and complex problem-solving. Tech giants like Google are already incorporating AI into software development. While it remains to be seen how quickly this shift will happen, one thing is sure: fresh frontiers in cyberspace are emerging. Nonetheless, the concern isn’t a novel threat but a rapidly growing one—Non-Human Identities.
Securing identities is one of organizations’ top priorities. While much attention is given to human users, a more elusive security risk often goes unnoticed: non-human identities (NHIs). These include service accounts, APIs, automation scripts, and machine identities interacting with systems without direct human intervention. As businesses adopt automation, cloud computing, and AI-driven workflows, NHIs are proliferating, making them an increasingly attractive target for cybercriminals.
Today, NHIs outnumber human identities by 10 to 50 times, forming a vast and complex ecosystem. Cloud providers, SaaS platforms, and on-prem systems each manage NHIs differently, using various authentication methods. Furthermore, unlike human identities, NHIs often lack the security of Multi-Factor Authentication (MFA). The threat is obvious.
What Are Non-Human Identities?
Non-human identities refer to digital entities that require authentication and authorization but are not associated with a physical person. These mostly include:
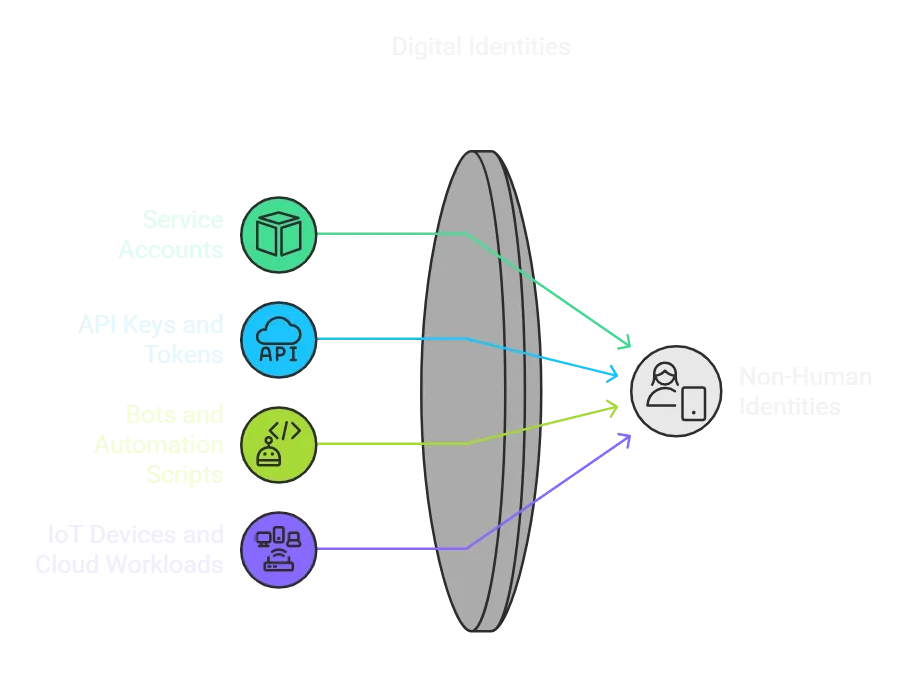
General categories of Non-Human (Digital) Identities (Napkin.ai)
- Service Accounts: These are used by applications or background services to interact with databases and other systems.
- API Keys and Tokens: Essential for machine-to-machine communication, enabling integrations and automation.
- Bots and Automation Scripts: Frequently deployed to handle repetitive tasks, from chatbots to CI/CD pipeline automation.
- IoT Devices and Cloud Workloads: Internet-connected devices and virtual machines that require access to resources.
The Security Risks of Non-Human Identities
Unlike human users, NHIs usually don’t follow traditional security policies like password rotation or Multi-Factor Authentication (MFA). They often have high privileges and broad access, making them prime targets for exploitation. Some of the most significant risks include:
Furthermore, employees frequently grant external entities access to automate tasks, leading to an explosion of third-party non-human connections to critical systems like GitHub. According to Astrix, this creates a largely ungoverned attack surface, with companies averaging 10,000 NHIs for every 1,000 users.
R&D teams further complicate security by creating secrets to connect internal services, often storing them across various managers without visibility or proper access controls. Unlike human identities, machine credentials lack essential security measures like MFA and expiration policies. Attackers exploit this weak spot, using compromised API keys, tokens, and service accounts to gain undetected access to business-critical assets. Without proper governance, these credentials remain a prime target for cyber threats.
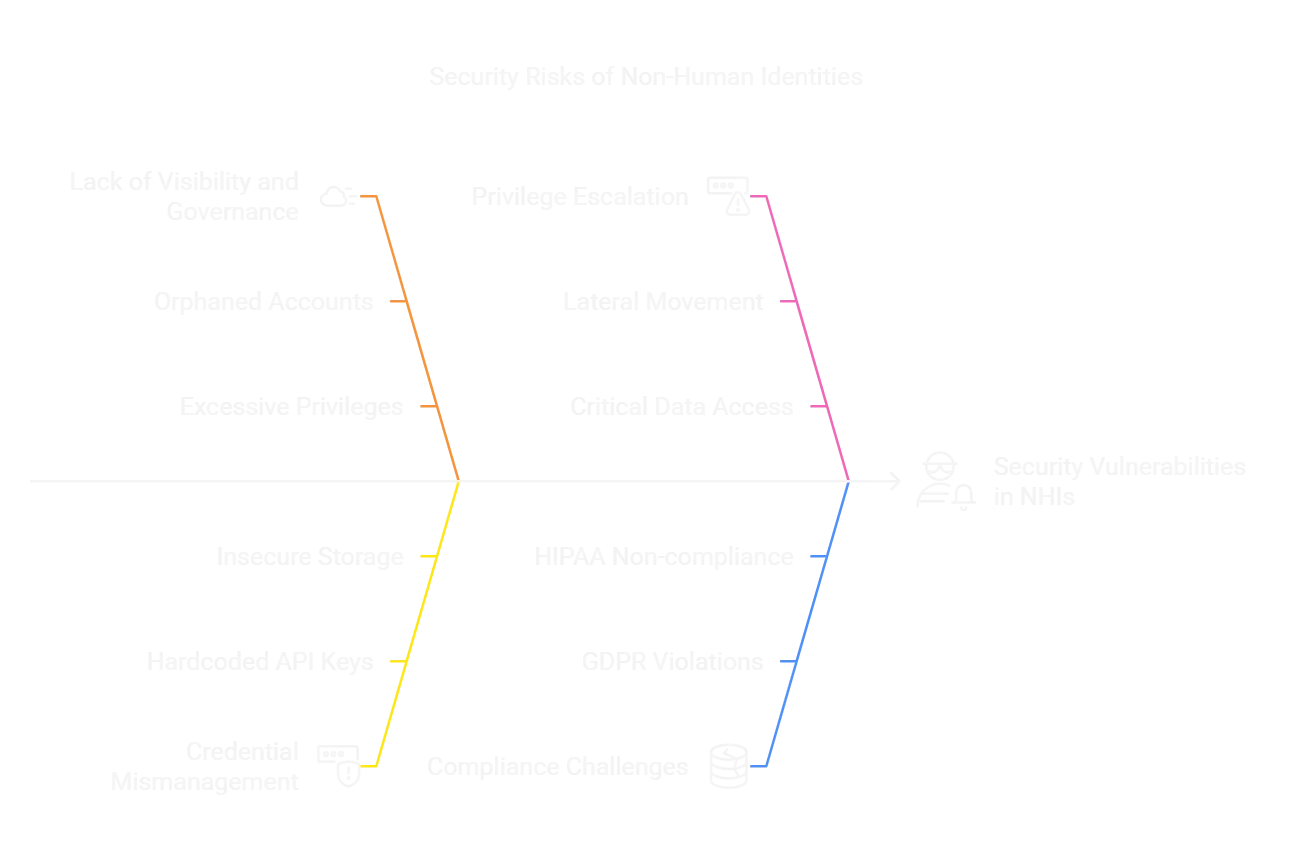
Security risks of Non-Human Identities (Napkin.ai)
Some of the most significant risks include:
- Lack of Visibility and Governance: Many organizations lack proper oversight over NHIs, leading to orphaned accounts, excessive privileges, and hidden attack vectors.
- Credential Mismanagement: API keys, tokens, and secrets are frequently hardcoded in source code, stored insecurely, or shared across teams, increasing the risk of leaks.
- Privilege Escalation: If an attacker gains control of an NHI, they can move laterally within the network, accessing critical data and systems.
- Compliance Challenges: Regulations like GDPR, HIPAA, and SOC 2 require organizations to manage all identities securely. Unmonitored NHIs can lead to compliance violations.
The OWASP Non-Human Identities Top 10
To address these risks, the OWASP project has identified the Non-Human Identities Top 10 security concerns for 2025 (OWASP NHI Top 10):
- Excessive Privileges: NHIs often have more access than needed, increasing attack surfaces.
- Hardcoded Secrets: API keys and credentials stored in code or repositories are easy targets for attackers.
- Lack of Lifecycle Management: NHIs frequently remain active long after they are no longer needed.
- Poor Logging and Monitoring: Many organizations do not track NHI activity, making it difficult to detect misuse.
- Weak Authentication and Authorization Controls: NHIs often bypass strong authentication policies applied to human users.
- Unverified Third-Party Integrations: External applications with access to NHIs may introduce security vulnerabilities.
- Orphaned NHIs: Accounts and keys that remain active after associated services are retired create security risks.
- Inadequate Segmentation: Lack of proper network and access segmentation allows attackers to move laterally using compromised NHIs.
- Over-Reliance on Static Credentials: Many NHIs rely on static credentials rather than more secure authentication methods.
- Insufficient Policy Enforcement: Weak policies for NHI governance lead to compliance and security gaps.
The list highlights the most critical security risks associated with Non-Human Identities (NHIs) in application development.
The list was created using OWASP’s Risk Rating Methodology, which evaluates risks based on factors like exploitability, prevalence, detectability, and impact. It draws from real-world breaches, surveys, and CVE databases to ensure accuracy and relevance.
To maintain consistency, the ranking assumes that organizations are already vulnerable to these risks and that attackers have sufficient knowledge to exploit them. It also considers the worst-case impact scenario, widespread prevalence of security weaknesses, and how difficult they are to detect.
Best Practices for Securing Non-Human Identities
As NHIs become integral to development pipelines and organizations continue adopting emerging technologies, understanding and mitigating the risks associated with them is already vital and will only become more critical over time. The increasing reliance on APIs, microservices, and automation tools elevates the need for robust security measures to ensure that these non-human actors do not become points of vulnerability.
To mitigate the risks associated with NHIs, organizations should adopt a proactive security approach:
- Implement Least Privilege Access: Ensure NHIs are granted only the minimum permissions necessary to perform their tasks. Limiting access reduces the impact of a compromised NHI and helps prevent the exploitation of over-provisioned identities.
- Use Secrets Management Solutions: Securely store API keys, tokens, and credentials using vault-based solutions. Proper management of secrets ensures that sensitive information is not exposed and can be rotated regularly, reducing the risk of unauthorized access.
- Automate Identity Lifecycle Management: Regularly review and deactivate NHIs that are no longer in use. This reduces the attack surface by eliminating inactive or obsolete identities that may still possess sensitive access.
- Enable Monitoring and Logging: Track and analyze NHI activity to detect anomalies and potential threats. By maintaining detailed logs and setting up alerts, security teams can quickly identify suspicious behavior and respond in real-time.
- Apply Strong Authentication Methods: Where possible, use certificate-based authentication or rotating credentials instead of static keys. This adds an additional layer of security, making it more difficult for attackers to impersonate NHIs.
- Leverage Attack Surface Management Tools: As part of a comprehensive security strategy, organizations should consider using solutions like SOCRadar’s Attack Surface Management to continuously discover, monitor, and protect all digital assets, including those tied to NHIs. By providing visibility into the external-facing infrastructure and identifying vulnerabilities in real-time, SOCRadar helps organizations mitigate risks associated with exposed NHIs and ensure a more secure digital environment.
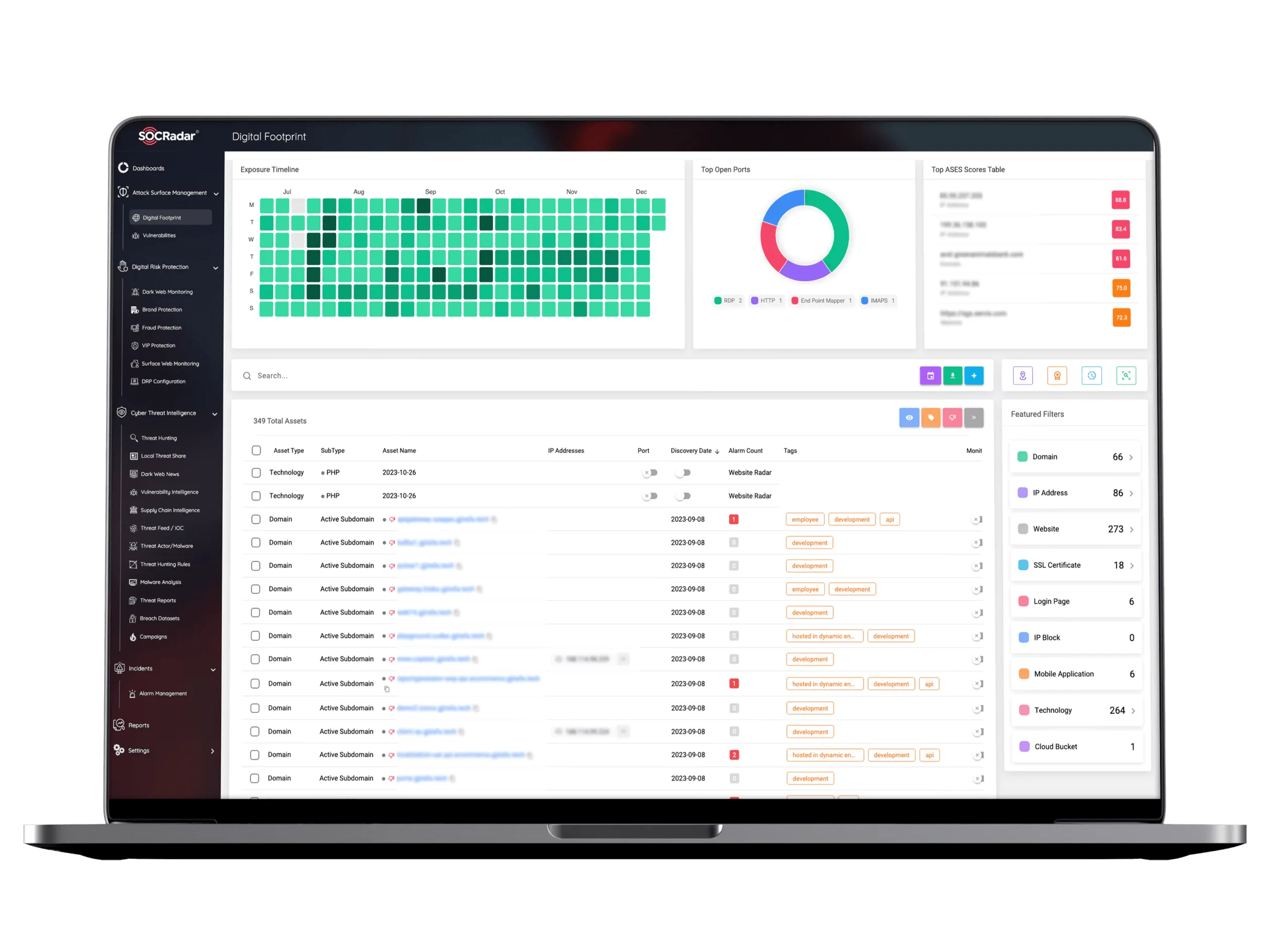
Thanks to SOCRadar’s EASM advanced continuous monitoring algorithms, you gain enhanced visibility and context for your current and future attack surface without manually providing your asset inventory.
By incorporating these best practices into their security frameworks, organizations can minimize the risks associated with NHIs and maintain a strong defense posture as their digital environments grow and evolve.
In Summary
As organizations increasingly rely on non-human identities (NHIs) such as service accounts, APIs, and automation scripts, understanding and addressing the security risks associated with them is paramount. NHIs are proliferating at an alarming rate, outnumbering human identities by a significant margin, and their lack of traditional security controls makes them vulnerable to exploitation. Attackers are keenly aware of these weaknesses, targeting mismanaged credentials, excessive privileges, and unmonitored activities to infiltrate systems undetected.
To mitigate these risks, businesses must adopt a proactive and comprehensive approach to NHI security. By implementing best practices such as least privilege access, secure secrets management, regular lifecycle reviews, and strong authentication methods, organizations can significantly reduce their attack surface.




































