
Why Threat Intelligence is So Effective for Vulnerability Prioritization?
Any day of the week there might seem to be a new vulnerability. There are more than 8,000 vulnerabilities annually. 80% of attacks originate from vulnerabilities. It is almost impossible for IT teams to keep up with patching vulnerabilities without proper intelligence. On average, companies spend 1.4 million USD annually on programs related to vulnerability management, an expansion of an average of 282.750 USD from 2018 where organizations spend an average of 1.16 million USD.
An earlier analysis by the Ponemon Institute showed an average of 139 hours spent on vulnerabilities a week.
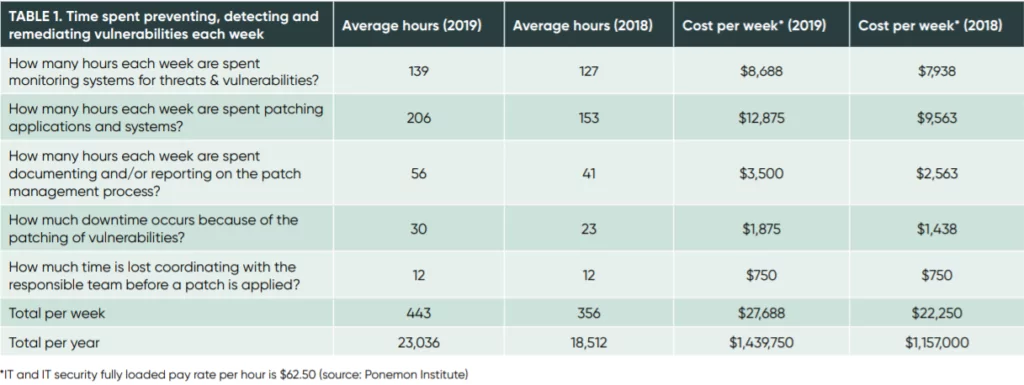
Organizations’ patching process is under greater pressure because they have less time to patch vulnerabilities before being attacked. Vulnerability patching is delayed because of a lack of resources, no common view of applications and assets and no ability to take critical applications and systems off-line so they can be patched quickly.
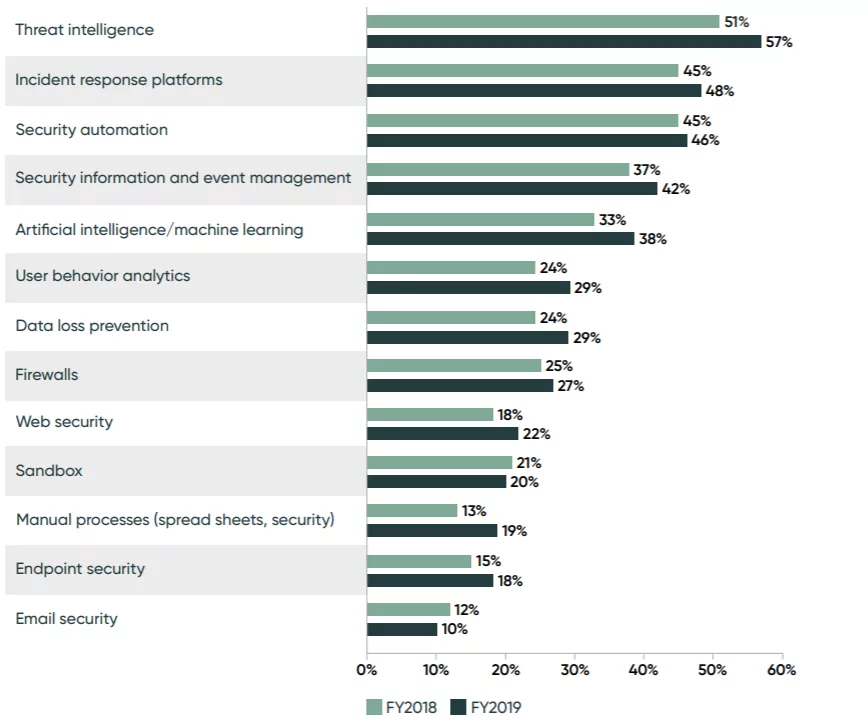
Threat intelligence is at the top of the list as a tool to respond for improving vulnerability response as shown in figure-1.
What is vulnerability?
CVE defines a vulnerability as ; weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact to confidentiality, integrity, or availability. Mitigation of the vulnerabilities in this context typically involves coding changes, but could also include specification changes or even specification deprecations (e.g., removal of affected protocols or functionality in their entirety).
What is vulnerability intelligence?
Vulnerability intelligence is collecting and contextualizing OSINT data about IT vulnerabilities and exploits.
What are the sources of vulnerability intelligence?
- Information security sites like vendor blogs, official disclosure information on vulnerabilities, and security news sites.
- Social media, where link sharing provides jumping-off points for uncovering useful intelligence
- Code repositories such as GitHub, which yield insights into the development of proof-of-concept code for exploiting vulnerabilities
- Paste sites such as Pastebin and Ghostbin (which are sometimes wrongly defined as dark web sources) that often house lists of exploitable vulnerabilities
- The dark web, composed of communities and marketplaces with a barrier to entry, where exploits are developed, shared, and sold
- Forums with no barrier to entry or requirement to be using specific software, where threat actors exchange information on vulnerabilities and exploits
- Technical feeds that deliver data streams of potentially malicious indicators, which add useful contexts
What are CVE (Common Vulnerabilities and Exposures), The Common Vulnerability Scoring System (CVSS) and NVD (National Vulnerability Database)?
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that’s been assigned a CVE ID number
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to a threat.
The NVD is the U.S. government repository of standards-based vulnerability management data represented using the Security Content Automation Protocol (SCAP). This data enables automation of vulnerability management, security measurement, and compliance. The NVD includes databases of security checklist references, security-related software flaws, misconfigurations, product names, and impact metrics.
How to prioritize vulnerabilities?
The Common Vulnerability Scoring System (CVSS) provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity. The numerical score can then be translated into a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize their vulnerability management processes.
The CVSS analyses the origin, time, effect, and environmental metrics of a vulnerability to understand how difficult an exploit is to achieve and the harm it will do if the attacker succeeds
The CVSS has continued to evolve over the years with new and updated versions as the community works to improve the scoring system.
CVSS score may not be the best guide when prioritizing the vulnerabilities. Usually, organizations need to consider 2 things;
- Likelihood of exploitation: How likely is it that the specific vulnerability you’re analyzing will be taken advantage of by a hacker, a malicious user, malware, or some other threat?
- Impact if exploited: How detrimental would it be if the vulnerability you’re analyzing were exploited?
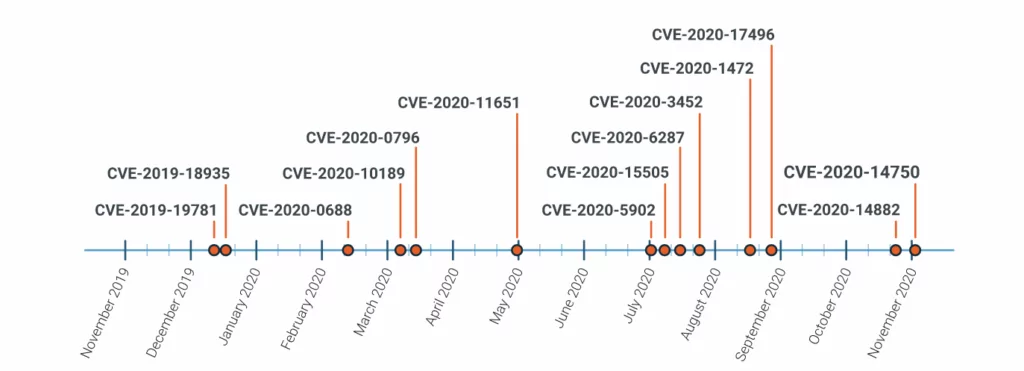
What are the top vulnerabilities in 2020?
Citrix NetScaler and Telerik UI were discovered at the beginning of 2020. Zoho ManageEngine and SaltStack Salt followed while the second half of the year was punctuated by internet-scale exploitation of severe vulnerabilities in F5 BIG-IP, Microsoft NetLogon Remote Protocol, and Oracle WebLogic Server. The combination of an authentication bypass and a remote code execution flaw in MobileIron’s Mobile Device Management (MDM) solution also offered a glimpse at how mobile device management software may prove a potent attack vector in the future, even after the remote workforce has begun to transition back to the office.
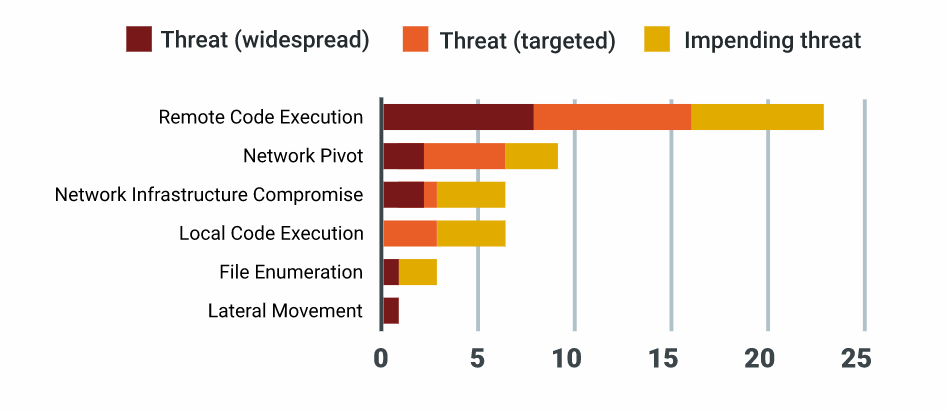
What are the top attack utilities in 2020?
- Remote code execution (RCE): Code execution on a remote target. Typically refers to the ability to execute a payload on a target system (e.g., obtain a shell session). Aids in credential stealing, data exfiltration, and so on.
- Network pivot: The ability to pivot from an external network to an internal network, most often by exploiting internet-facing systems such as VPNs, firewalls, routers, and other gateway devices. A network pivot gives an attacker visibility into both internal and external traffic and aids in data exfiltration, traffic sniffing, and further attacks within the target network.
- Network infrastructure compromise: Compromise of networked infrastructures, such as a network management system or backup system, that may give an attacker access to everything managed by that software. Vulnerabilities in virtualization, automation, and/or device management infrastructure all fall into this category.
- Local code execution: The ability to run code locally on a system to which the attacker already has some access. Most commonly used to escalate privileges (e.g., by executing code as the user running the vulnerable application).
- File enumeration: The ability to enumerate files on a target. File reads do not give an attacker a path to code execution by themselves but instead function as primitives that allow attackers to gather the information that enables a secondary part of an exploit chain (e.g., remote code execution). Can aid in turning a post-authentication vulnerability into a pre-authentication vulnerability.
Which measurements should be taken for vulnerabilities?
Following measurements should be taken in order to create an effective defense against vulnerabilities.
- Patch early and as often as possible.
- Defense-in-depth is more efficient than just patching.
- Keep an up-to-date inventory list that emphasizes assets or products that sit on the perimeter and/or may be used as pivot points for external attackers to gain access to the internal network.
- Use a Cyber Threat Intelligence platform.
Does SOCRadar provide Vulnerability Intelligence?
SOCRadar is a real-time tool for monitoring vulnerabilities and their remediation and it gives the best vulnerability intelligence available. So you can prioritize your vulnerabilities based on actionable intelligence. SOCRadar also provides; .
- Real-time alert for major vulnerability (Zero-day, critical patch, etc.)
- Real-time alert for new exploits.
- 100% SaaS solution, available 24/7/365
- Weekly newsletters
- Data collection from different OSINT sources
- Most popular and critical CVEs
- Relevant and timely intelligence information
- Automated vulnerability detection
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.

































