
Zero-Day Vulnerabilities in Citrix Netscaler ADC and Gateway & Google Chrome: CVE-2023-6548, CVE-2023-6549, and CVE-2024-0519
[Update] January 18, 2024: “CISA Lists Zero-Day Vulnerabilities in Netscaler ADC and Gateway, and Chrome on KEV Catalog”
Citrix has recently issued a warning to its customers, advising them to patch Netscaler ADC and Gateway appliances promptly to prevent the exploitation of two zero-day vulnerabilities, CVE-2023-6548 and CVE-2023-6549.
These zero-day vulnerabilities have the potential to lead to Remote Code Execution (RCE) and Denial-of-Service (DoS) attacks. The advisory mentions that these vulnerabilities only impact customer-managed NetScaler appliances, with no action required for customers of Citrix-managed cloud services or Citrix-managed Adaptive Authentication.
Here are the details of the vulnerabilities:
- CVE-2023-6548 (CVSS Score: 5,5) is an RCE vulnerability on the management interface. However, successful exploitation demands an authentication, with a low privileged account, and the ability to access NSIP, CLIP, or SNIP with management interface access.
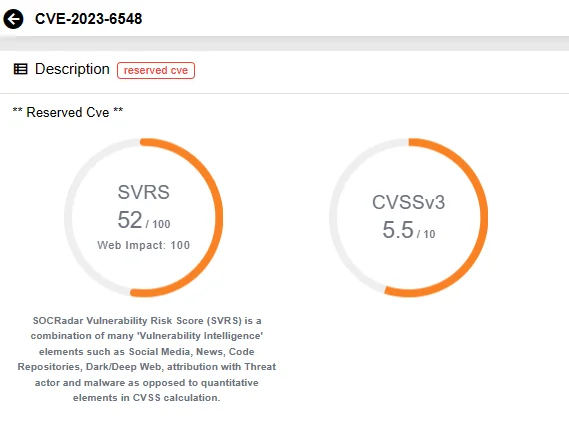
SOCRadar Vulnerability Intelligence: CVE-2023-6548
- CVE-2023-6549 (CVSS Score: 8,2) is a Denial of Service (DoS) vulnerability. For its exploitation to be successful, the appliance must be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy), OR AAA virtual server.
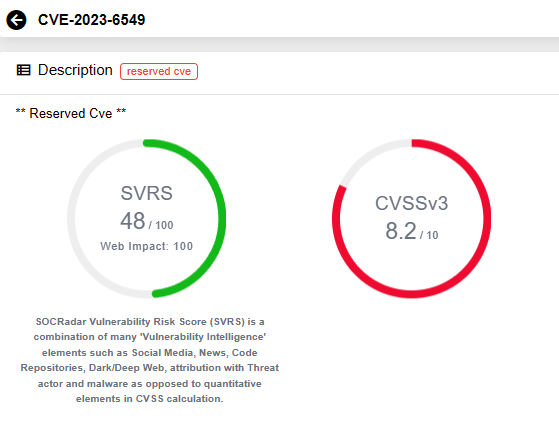
SOCRadar Vulnerability Intelligence: CVE-2023-6549
Citrix has observed exploits on unpatched instances and strongly urges affected customers of NetScaler ADC and Gateway to promptly install the relevant updated versions.
Leverage SOCRadar’s Vulnerability Intelligence to stay informed about the latest updates and trends on identified vulnerabilities, including exploits and mentions. You can glimpse into the capabilities of SOCRadar’s Vulnerability Intelligence with CVE Radar, a free feature on SOCRadar Labs.
CVE Radar from SOCRadar Labs
What Are the Affected Netscaler ADC and Gateway Versions?
The zero-day vulnerabilities impact the following versions of Netscaler ADC and Gateway appliances:
- NetScaler ADC and NetScaler Gateway 14.1 before 14.1-12.35
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-51.15
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.21
- NetScaler ADC 13.1-FIPS before 13.1-37.176
- NetScaler ADC 12.1-FIPS before 12.1-55.302
- NetScaler ADC 12.1-NDcPP before 12.1-55.302
To mitigate the factors contributing to the exploitation of these vulnerabilities, if immediate updating is not feasible, it is strongly advised to segregate the network traffic to the appliance’s management interface from the normal network traffic. Additionally, Citrix recommends not exposing the management interface to the internet.
According to Shadowserver, over 1,200 Netscaler management interfaces are accessible on the internet. Implementing the mentioned security practices and preventing exposure of the appliances to the internet could significantly reduce the risk of exploitation.
Visit the Citrix advisory for more information on the zero-day vulnerabilities and guidance on updating.
Google Issued an Urgent Update to Fix a Chrome Zero-Day Vulnerability: CVE-2024-0519
Google has released an urgent Chrome browser update to address a zero-day vulnerability, as well as two other high-severity security vulnerabilities.
The zero-day vulnerability, tracked as CVE-2024-0519, affects the Chrome browser and is described as an out-of-bounds memory access issue in V8 JavaScript engine.
The vulnerability affects V8 in Google Chrome prior to 120.0.6099.224, indicating a high severity issue. Although it has not yet been assigned a CVSS score on NVD, it is described that it could allow a remote attacker to potentially exploit heap corruption via a crafted HTML page.
Other than the fact that the vulnerability was reported anonymously and exploited, Google provided no additional information about it in order to save time for patching.
The two other vulnerabilities in the Chrome security update, CVE-2024-0517 and CVE-2024-0518, are ‘Out-of-Bounds Write’ and ‘Type Confusion’ vulnerabilities in V8, respectively.
For more information, visit the advisory here.
CISA Lists Zero-Day Vulnerabilities in Netscaler ADC and Gateway, and Chrome on KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has included the three zero-day vulnerabilities, CVE-2023-6548 and CVE-2023-6549 affecting Citrix’s Netscaler ADC and Gateway appliances, as well as CVE-2024-0519 affecting Google’s Chrome browser, in its Known Exploited Vulnerabilities (KEV) Catalog.
The agency emphasizes that these vulnerabilities are common attack vectors and present substantial risks to the federal enterprise. Organizations are urged to address the Netscaler Buffer Overflow vulnerability (CVE-2023-6549) and the Chrome vulnerability (CVE-2024-0519) by the deadline of February 7, 2024, whereas the Netscaler CVE-2023-6548 zero-day requires immediate attention; organizations are expected to complete patching CVE-2023-6548 within a week, by January 24, 2024.




































