
Zero-Days (CVE-2023-26077, CVE-2023-26078) in Atera Windows Installers
Recent revelations have exposed critical zero-day vulnerabilities in Atera Windows installers. Cyber attackers could potentially use these loopholes to launch privilege escalation attacks. To understand the severity of these vulnerabilities, it is crucial to unpack the characteristics of these zero-day exploits and how they may impact users of the Atera remote monitoring and management software.
Atera Installer Vulnerabilities
The flaws in the Atera installers, discovered by Mandiant on February 28, 2023, have been assigned the identifiers CVE-2023-26077 and CVE-2023-26078. These vulnerabilities are profoundly concerning as they expose users to a local privilege escalation attack, a form of security exploit that allows attackers to increase their privileges within a system, often leading to complete control over the targeted system.
In the context of the Atera installers, both vulnerabilities reside in the Microsoft Software Installer (MSI) installer’s repair functionality, potentially allowing operations to be triggered from a high-privileged system context (NT AUTHORITYSYSTEM), even when initiated by a standard user. This situation presents a potential security risk if not properly managed.
Exploring the Privilege Escalation Attacks
The first vulnerability, CVE-2023-26077, exposes the Atera Agent to a privilege escalation attack that can be exploited through DLL hijacking. DLL (Dynamic-Link Library) hijacking is a technique that takes advantage of how some Windows applications search and load DLL files. By replacing a legitimate DLL with a malicious one, an attacker could execute arbitrary code with elevated privileges.
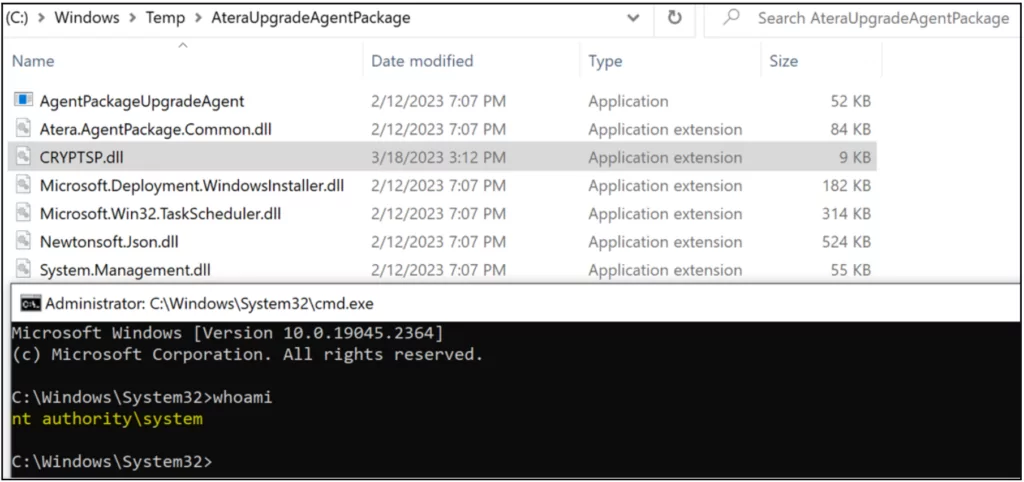
In the case of Atera, a misconfigured repair functionality makes the software susceptible to such an attack. The software attempts to load a DLL from a folder where standard users have written permissions, presenting an opportunity for an attacker to replace the DLL with a malicious version. Successful exploitation of this flaw could result in obtaining a Command Prompt as the high-privileged system user, NT AUTHORITYSYSTEM.
Execution of System Commands
CVE-2023-26078, the second vulnerability, deals with a scenario where system commands are executed, triggering the Windows Console Host (conhost[.]exe) as a child process. When executed with elevated privileges, this could open up a command window, which an attacker could use to perform a local privilege escalation attack.
When the repair functionality runs system commands that spawn conhost[.]exe as a child process, it opens a command window, which an attacker could hijack. By rapidly interacting with the window, an attacker could freeze it, gaining access to hyperlinks that can be used to open a web browser as NT AUTHORITYSYSTEM.
Kaspersky has documented instances where the aforementioned vulnerabilities have been manipulated by malicious actors. These threat actors have cleverly utilized Outlook tasks, messages, or calendar events as tools for their harmful intentions.
Protective Measures and Updates
In response to these critical vulnerabilities, Atera has released updates for its software. CVE-2023-26077 was remediated in version 1.8.3.7, while CVE-2023-26078 was addressed in version 1.8.4.9. The updates include hardening certain folders to prevent standard users from writing files to them, which effectively blocks the possibility of a DLL hijacking attack.
Despite these updates, organizations must understand that vulnerabilities in software are a constant risk. Developers must thoroughly review their custom actions to prevent hijacking privileged operations, especially those triggered by MSI repairs. Similarly, developers must be cautious when using system commands that spawn conhost[.]exe as a child process, as this could temporarily open a command window that attackers could hijack.
Leveraging SOCRadar for Enhanced Cybersecurity
While staying vigilant is crucial, companies must also equip themselves with robust cybersecurity tools that preemptively identify vulnerabilities and security risks. This is where SOCRadar comes in. By utilizing SOCRadar’s Vulnerability Intelligence and External Attack Surface Management, organizations can identify vulnerabilities and understand their attack surface better.
The Vulnerability Intelligence service allows organizations to track known vulnerabilities, exploit publications, and zero-day vulnerabilities. In turn, this can help businesses act quickly in remediating potential threats. On the other hand, the External Attack Surface Management tool can help organizations map, monitor, and manage their digital footprint, further enhancing their cybersecurity defenses.
In the rapidly evolving cybersecurity world, organizations must stay one step ahead. By understanding the potential risks and equipping themselves with effective cybersecurity tools like those offered by SOCRadar, they can fortify their defenses against future cyber threats.

































