Top 5 Underground Hacker Forums That are Accessible via Your Web Browsers such as Google Chrome, Firefox, and Internet Explorer
!!!FOR RESEARCH AND EDUCATIONAL PURPOSES!!!
With computer and information technology becoming more ubiquitous, cybersecurity has become a grand societal challenge. Today, malicious hackers commit numerous large-scale, advanced attacks on industry and government organizations. These cyber-attacks cost the global economy over $450 billion annually. Cyber Threat Intelligence (CTI) to enable effective cybersecurity decisions, has emerged as a viable approach to mitigate this concern.
Hacker community platforms carefully conceal themselves and employ numerous anti-crawling measures that prevent automated, large-scale data collection. These barriers force many researchers to manual collection efforts.
Hacker forums are the most common and largest platforms for hackers to share hacking resources. Hackers use these message boards to post messages within threads of conversations related to hacking tools, techniques, and malicious source code
SOCRadar is on a mission to find exposed data on the dark web. SOCRadar Labs is a free service to create a report on your company, whether your data has been exposed to the dark web and threat actors. By searching below, you can access SOCRadar Labs immediately and get a dark web report for free!
Receive a Free Deep Web Report for Your Organization
1. xss.is
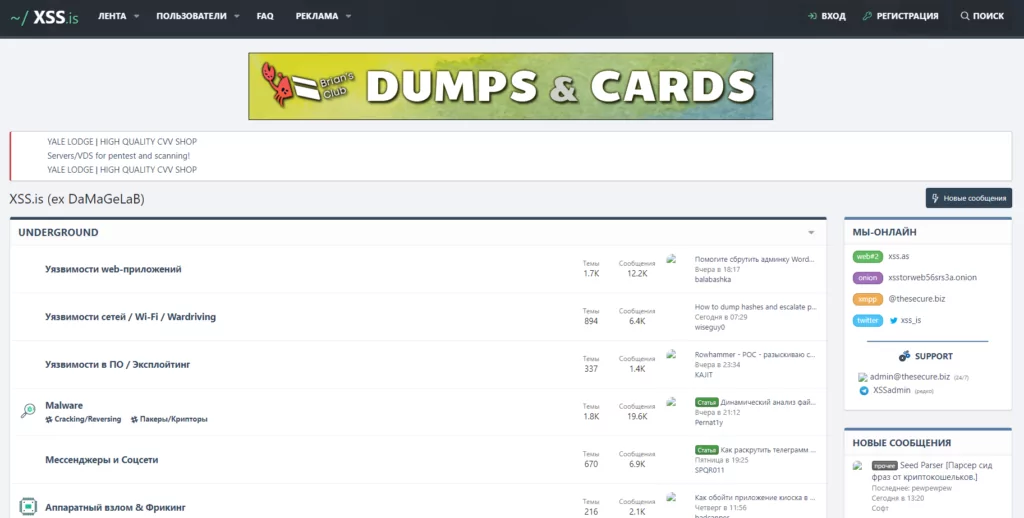
xss.is was previously known as damagelab.org (stylized as DaMaGeLaB), and was one of the first and most popular Russian-language forums, dating back to at least 2013. Following the arrest of one of its administrators in 2017, the site rebranded as xss.is and relaunched in September 2018. It derives its name from cross-site scripting, a type of security vulnerability in web applications used to bypass access controls. It is a popular Russian language forum, hosting discussion topics including hacking, programming, and technology, as well as a marketplace section in which users can make direct sales of mostly digital products.
2. raidforums.com
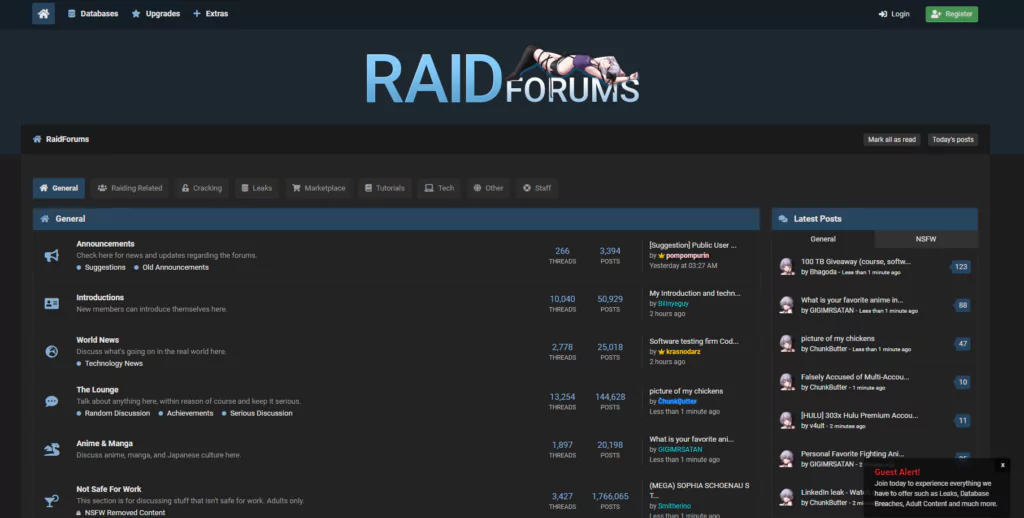
RaidForums was established in March 2015. Most of the forum’s early posts contain either links encouraging other users to raid or videos documenting successful raids carried out. RaidForums began to gain popularity the following year as a place for users to post leaked information such as hacked combolists and even entire databases, with an official or verified Database thread updated regularly by the site’s owner. The volume of high-profile leaks available to view and purchase on RaidForums has gained it mainstream and social media attention in recent years, with several Change.org petitions being created aimed at shutting down the site due to its promotion of “raiding, DDoS and database theft” with “intent to harass and attack people”. An example of RaidForums social media controversy is the campaign waged by its members against popular IRL streamer Ice Poseidon, involving bomb threats and repeated swatting (in which a serious crime alleged to have been committed by the victim is reported to authorities, usually resulting in the arrival of a SWAT team or police at the victim’s residence; swatting has resulted in a victim’s death at least once). RaidForums is a very popular forum hosting discussions on topics including Raiding, Leaks, and Tutorials. It also has a Marketplace section for trading goods, mainly dehashed combolists.
3. hackforums.net
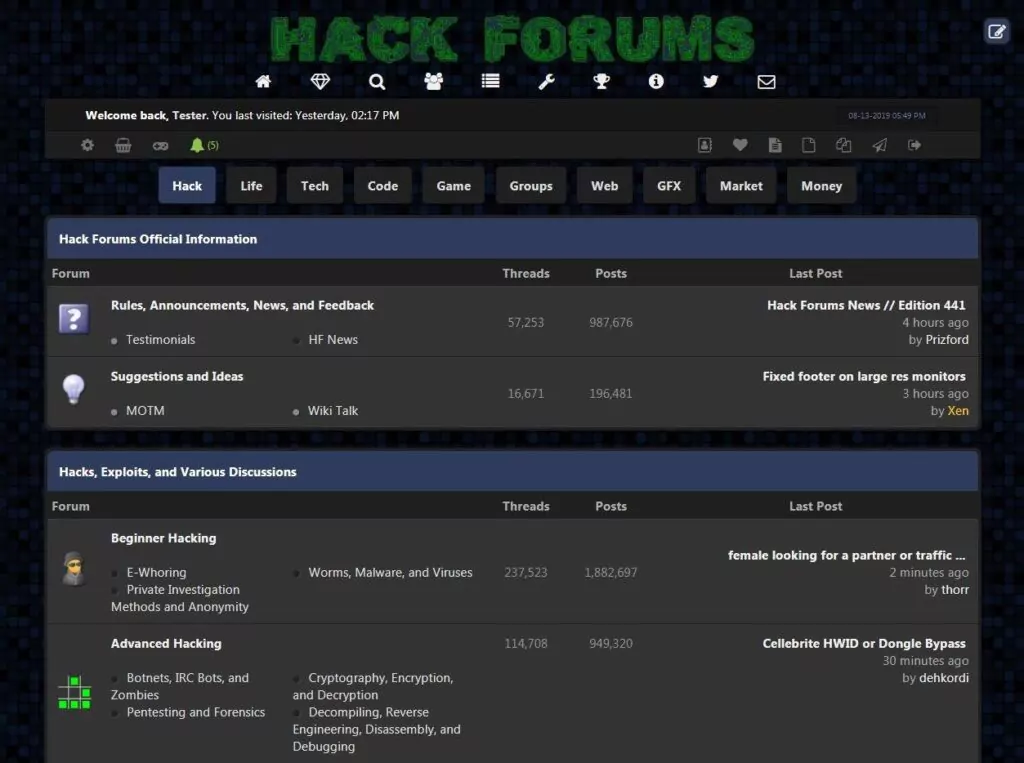
The site has been widely reported as facilitating criminal activity, such as the case of Zachary Shames, who in 2013 sold a keylogger that was used to steal personal information. The forum caters mostly to a young audience who are curious and occasionally malicious but still learning.
4. exploit.in
Exploit.in was established in 2005, making it a long-running hacking forum. It is a Russian hacker forum and news site accessible via standard browsers. Discussion on the forum focuses largely on sharing exploits and vulnerabilities within computer systems, for purposes of hacking, from which its name is derived. exploit.in also functions as a marketplace where users can buy and sell digital products such as malware.
5. evilzone.org
Evilzone is a community of hackers and crackers. Many coders, professional hackers take part in this forum and within an hour you will get an answer to your questions. To reduce the number of Noobs registering in the forum, you need to “find” a registration key. This key can be found by completing one of the several challenges. The best way to get Registration Key is to connect the IRC server using Icechat or another IRC client.
How to Know if Your Organizations’ Sensitive or Personal Data Available via Hacker Forums?
SOCRadar 7×24 monitoring of malicious activities targeting your organization
SOCRadar provides a thorough Surface&Dark & Deep Web Monitoring solution that enables organizations to identify and mitigate threats across the surface, deep, and dark web. Using our unparalleled reconnaissance capacities and threat analysis, we deliver actionable intelligence to help you proactively secure your organization. The fusion of automated external cyber intelligence with a dedicated analyst team enables SOC teams to take control of the outer world beyond their perimeters.
- Proactively Identify Threats: Empower the inevitable part of your cyber defense mechanisms with the ability to identify and neutralize threats at the very beginning of the cyber kill chain.
- Enhance Your Threat Hunting Capability:Uncover the dark web which notably presents a challenging landscape for threat hunting due to its anonymous nature and basic difficulties in forcing regulations.
- Get Proactive against a Variety of Malicious Activities:Continuously monitor the common forums with many sub-forums split into different categories which are well-divided for the trading of a broad variety of malicious activities such as botnets, malware, data dumps, exploits, hacking as-a-service, remote access, and PII trading