
489 Million Instagram Accounts Scraped and Listed for Sale on Dark Web
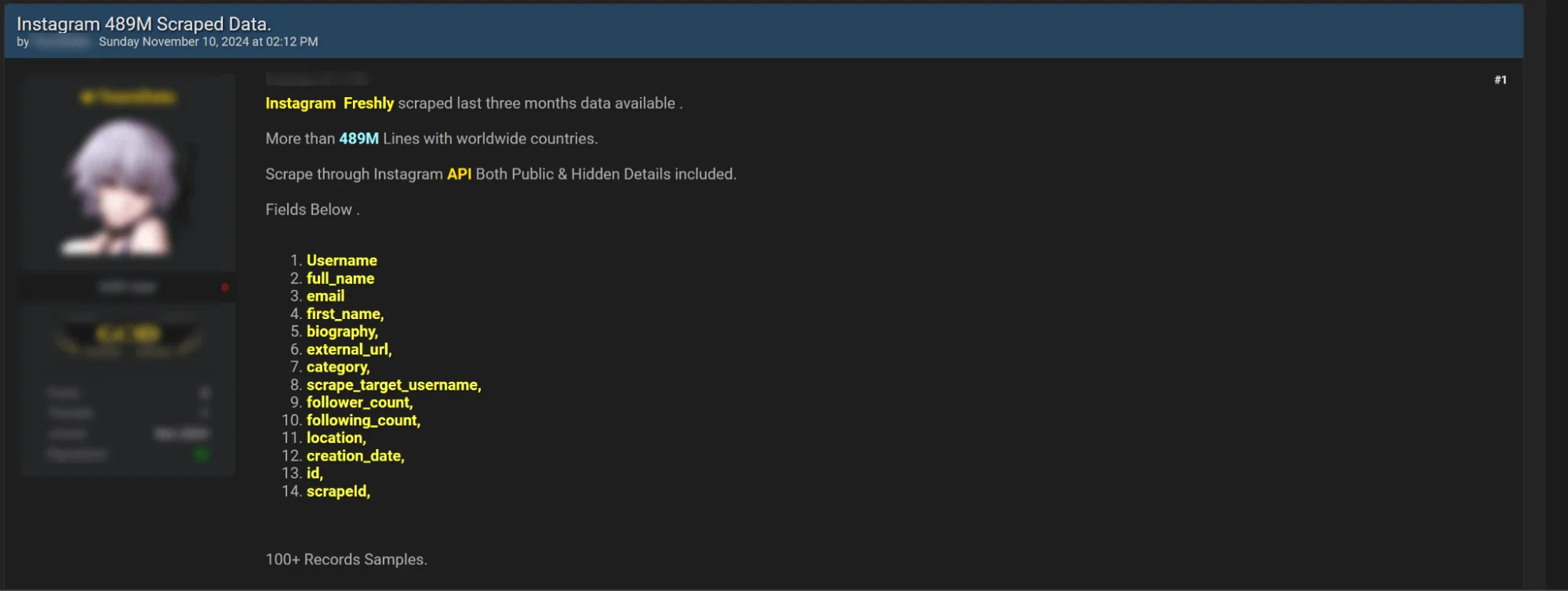
A recent post on a Dark Web hacker forum has sparked widespread concern, with a threat actor claiming to possess a massive dataset containing the personal details of Instagram users. The dataset allegedly has over 489 million records.
Allegedly obtained within the last three months, this dataset is said to include both public and hidden information, suggesting that the actor may have exploited Instagram’s API to access sensitive user data.
The post has gained attention across the cybersecurity community, with many questioning the potential privacy impacts on Instagram users worldwide. The dataset is described as containing “worldwide coverage,” with users from numerous countries included.
A threat actor claims to have scraped Instagram
What Happened?
A threat actor on a popular Dark Web forum recently made headlines by claiming they had scraped a massive dataset containing over 489 million Instagram user records.
The actor, who shared this post on November 10, 2024, stated that the data was collected over the past three months through the Instagram API, reportedly accessing both public and hidden details. This scraping activity has raised concerns that the actor may have taken advantage of weaknesses in Instagram’s systems to acquire sensitive user information at scale.
In the post, the threat actor shared details about the data fields included in the scrape. The dataset is said to contain a wide range of user information, including:
- Username
- Full name
- Email address
- First name
- Biography
- External URL
- Account category (e.g., business, influencer)
- Targeted username for the scrape
- Follower and following counts
- Location information
- Account creation date
- User ID and scrape ID
This dataset reportedly covers users from around the world, making it a broad and potentially valuable resource for those looking to exploit personal information.
To back up their claims, the threat actor provided a sample of over 100 records, offering a glimpse into the details they’ve allegedly obtained. This sample reportedly includes email addresses and location data, alongside the usual public information such as usernames and follower counts. Such a mix of public and potentially private information could expose Instagram users to numerous security and privacy threats.
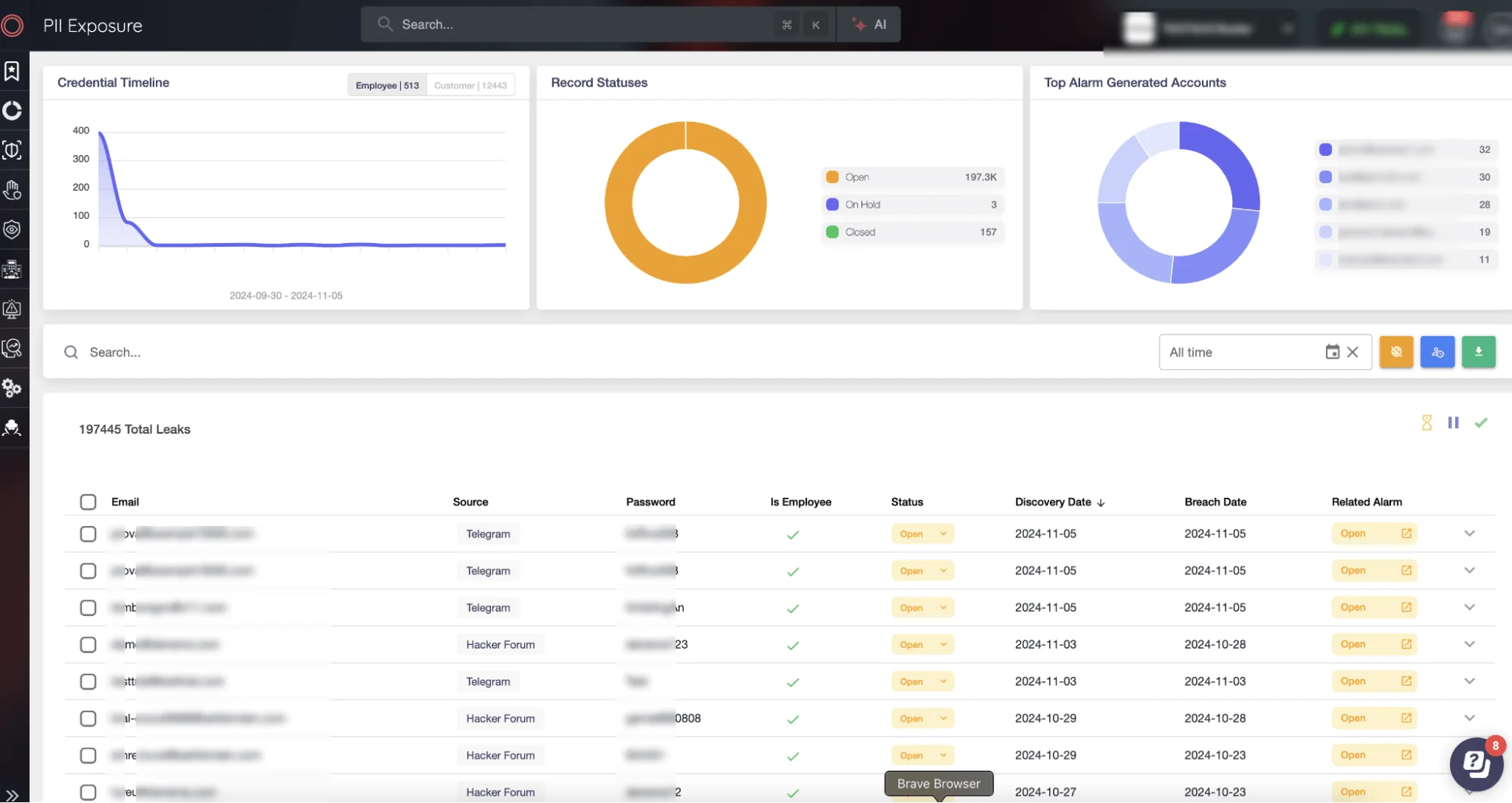
In scenarios like this, where sensitive user data is disclosed on Dark Web forums, SOCRadar Advanced Dark Web Monitoring becomes a critical tool for organizations aiming to safeguard their digital environment. This monitoring service empowers companies with real-time insights into Dark Web threats, actively tracking exposed Personally Identifiable Information (PII), identifying threat actors, and monitoring suspicious activities that could escalate into severe security incidents if left unchecked.
SOCRadar Dark Web Monitoring
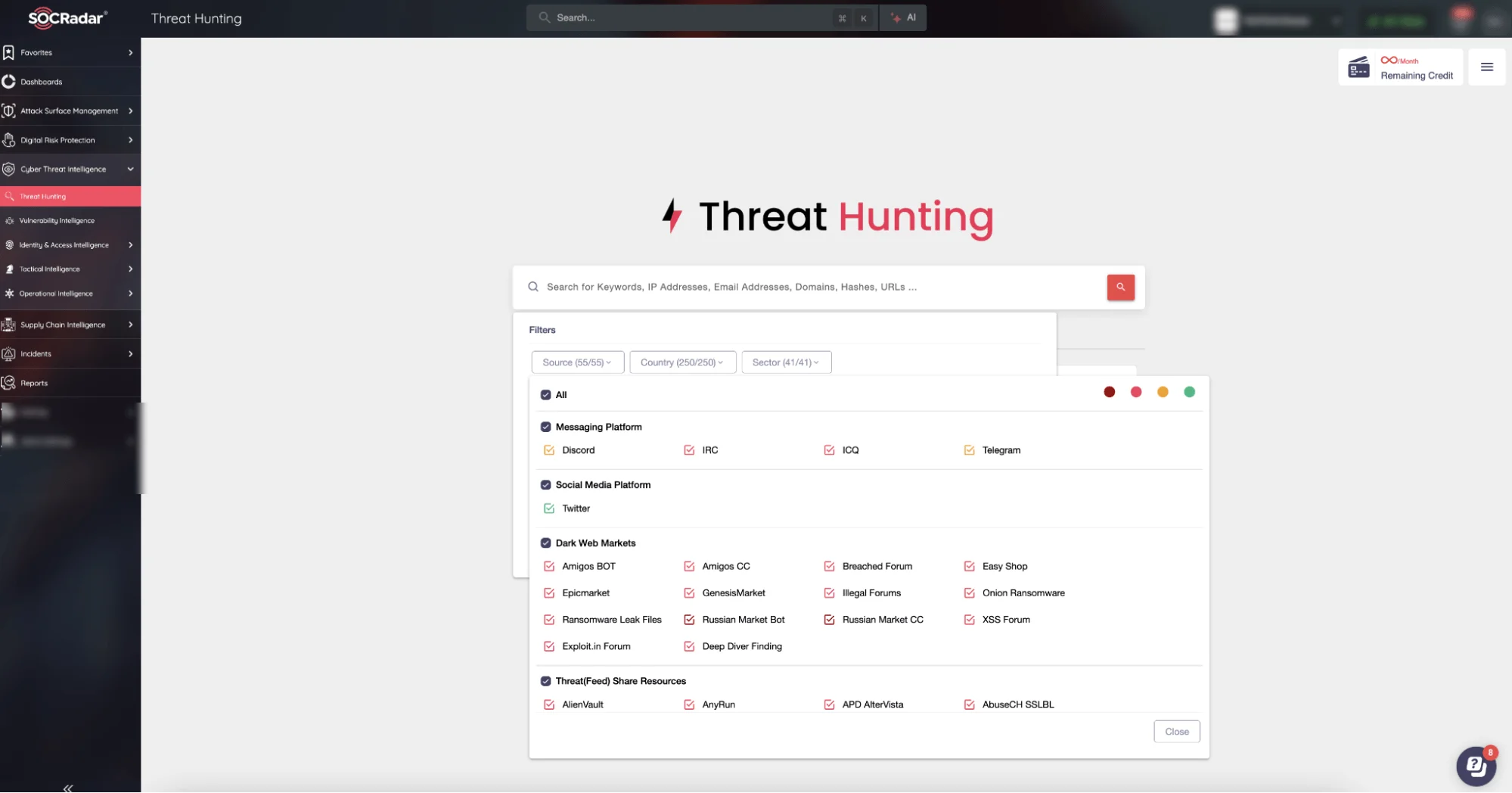
Complementing these insights, the Dark Web Search Engine of the SOCRadar Threat Hunting module offers a precise navigation tool for delving into the hidden areas of the Dark Web. By using advanced algorithms and customized news feeds, it delivers targeted threat intelligence, enabling organizations to detect and neutralize emerging risks before they pose a direct threat to the organization’s perimeter.
SOCRadar Threat Hunting
Together, these tools facilitate a proactive approach to Dark Web monitoring, helping to secure data and maintain organizational integrity in an ever-evolving threat landscape.
What Does the Data Leak Mean for Instagram Users?
If authentic, this data leak could pose significant risks for Instagram users around the world. With details like usernames, full names, email addresses, follower counts, and locations reportedly included, cybercriminals could exploit this information for a variety of malicious purposes.

AI illustration for phishing by DALL-E
The leaked Instagram data could potentially expose users to:
- Social Engineering Attacks: Cybercriminals may use the email addresses, names, and locations in phishing schemes or impersonation attacks. With such specific data, attackers could easily craft convincing messages or scenarios to trick users into sharing more personal information or clicking on malicious links.
- Account Takeovers and Impersonations: For accounts with sensitive information or high follower counts, cybercriminals could attempt to take over accounts using techniques such as SIM swapping. Once an account is compromised, it could be misused for further scams, such as cryptocurrency fraud or impersonation scams targeting followers.
- Increased Risk of Scams and Fraud: The threat actor may also sell the data to other criminals interested in using it for various fraudulent schemes. Cybercriminals can exploit high-profile or business accounts for brand impersonation, crypto scams, or even Business Email Compromise (BEC) fraud.
- Invasion of Privacy: For some users, especially those who haven’t publicly shared their email addresses or other details, this exposure could represent a major privacy violation. Individuals who assumed their personal information was private may now face harassment, unsolicited contact, or worse.
The availability of both public and hidden data fields makes this dataset especially valuable to cybercriminals. Access to private details like email addresses and location data offers opportunities to exploit these profiles in ways that were not previously possible with just public information.
Who is the Threat Actor Behind the Instagram Data Leak?
The threat actor responsible for this alleged Instagram data leak recently emerged on the Dark Web forum, joining on November 6, 2024, and has since upgraded their account to a paid membership. This upgrade likely reflects an attempt to build credibility within the forum and signal a more serious intent to potential buyers. The actor’s post, which claims access to over 489 million Instagram user records, serves as a bold sales pitch on one of the Dark Web’s popular marketplaces for stolen data.
In the post, the threat actor withheld specific pricing information but did respond to a forum comment by stating, “Full DB at $5k but negotiable and broad range countries prices are different for example you want to have the data from specific countries.” This suggests that the actor may be willing to negotiate based on specific buyer needs, such as filtering data by country. By offering these flexible options, the actor may be attempting to appeal to a range of cybercriminals with different motivations and target regions.
How Can Instagram Users and Organizations Protect Themselves?
This data leak, if verified, highlights the critical need for both individual users and organizations to take proactive measures against potential security threats. While Instagram users cannot control every aspect of how their data is handled, there are steps they can take to mitigate risks:
- Enable Two-Factor Authentication (2FA): Users should activate 2FA on their Instagram accounts to add an extra layer of protection. This measure helps prevent unauthorized access, even if attackers have certain personal details.
- Be Cautious of Phishing Attempts: With email addresses and other details potentially exposed, users should be vigilant about any suspicious messages or emails. Phishing attempts may try to exploit this data to trick users into revealing even more sensitive information.
- Regularly Monitor Account Activity: Users should periodically review their account activity for unusual logins or unauthorized actions. Early detection can prevent further harm if an account is at risk.



































