Business Email Compromise (BEC) Attacks: A Sneaky Threat to Organizations
The pandemic has brought about radical changes in business models. Alongside digital transformation, the increased efficiency and profitability have also altered the landscape of potential threats that organizations may face. Today, with over 60% of businesses worldwide adopting remote or hybrid work models, most internal and external communications rely on the trust relationship of digital channels, particularly corporate email addresses.
Business Email Compromise (BEC) attacks exploit this trust relationship, allowing attackers to gain financial benefits or initiate malicious activities as the first step of initial access. Attackers leverage basic information about a company’s hierarchy gathered from open sources prior to BEC attacks. These attacks can take the form of a message resembling an email sent by the company’s CEO, requesting urgent fund transfers from employees. Alternatively, they may involve requests for purchasing gift cards from executive assistants to reward diligent employees, as we will discuss further in the information below.
BEC attacks can also target the relationships between organizations and vendors in their supply chain. By impersonating an email from a participant in the supply chain, attackers can request the modification of invoice details in your company’s finance department, replacing them with the attacker’s account information. They can also demand transfers of funds to accounts under their control using fake invoices. Furthermore, as we will elaborate on in the following information, BEC attacks can lead to the introduction of malicious software into your organization’s information system through email attachments.
An alarming example demonstrating that BEC attacks can target any type of organization is the case of Puerto Rico’s government, which suffered millions of dollars in financial losses. As a result of an attacker gaining control over an email address associated with the Puerto Rico Retirement System, many victims, including the Puerto Rico Department of Industry and Development and Puerto Rico Tourism Companies, were persuaded by the attackers to make multimillion-dollar transfers. Numerous institutions fell into the trap set by emails sent on behalf of the Puerto Rico Retirement System, requesting changes to account numbers for future premium payments.
A Rising Trend: Business Email Compromise (BEC) Attacks
According to the FBI’s annual cybercrime reports, Business Email Compromise (BEC) attacks accounted for 20,373 complaints in 2018, which increased to 23,775 in 2019, then decreased to 19,369 in 2020, and rose again to 21,832 in 2022. These data indicate a 7.2% increase in BEC attacks over the past four years.
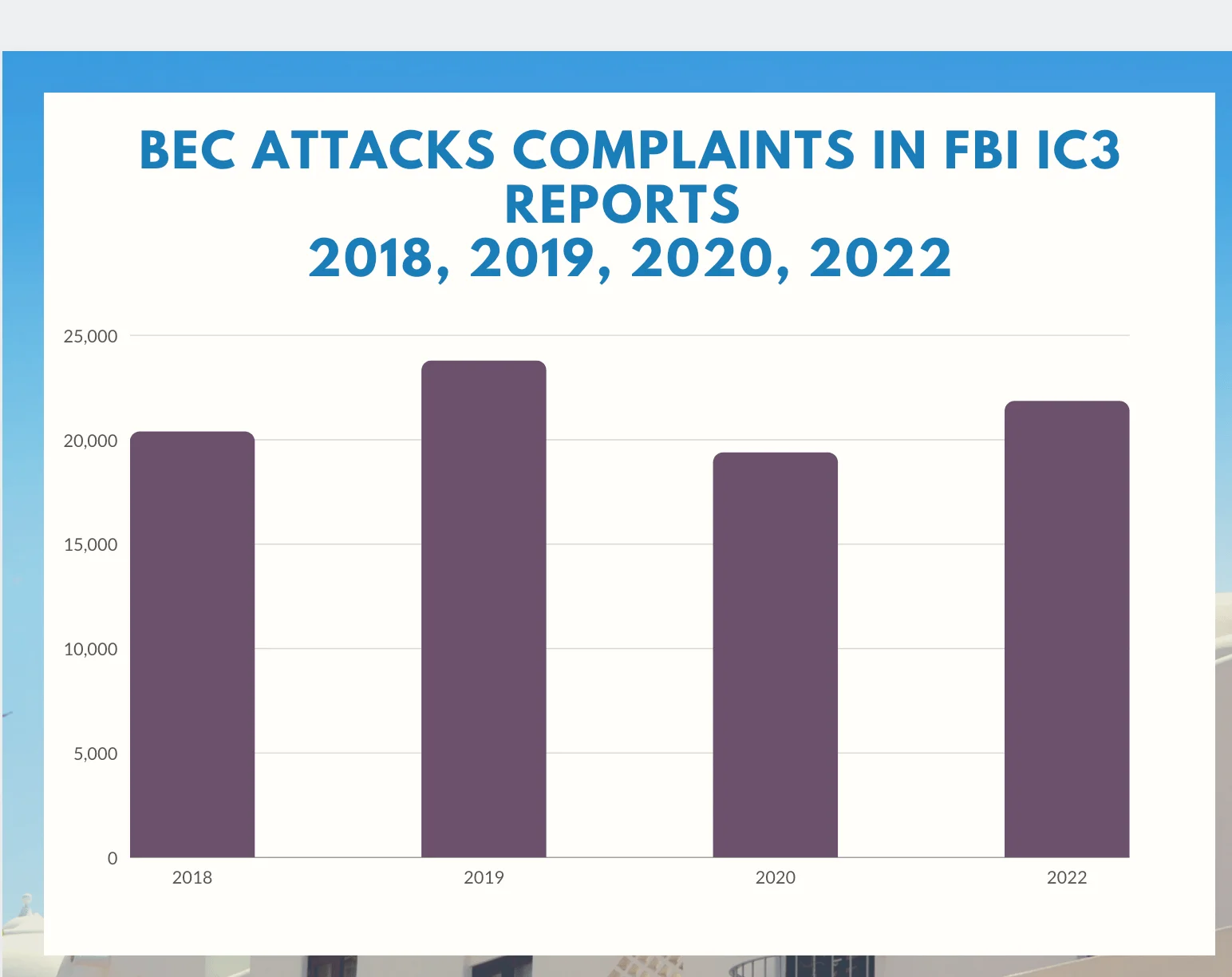
FBI IC3 Annual Reports, BEC Attacks, 2018, 2019, 2020, 2022
Despite the lack of an astronomical increase in reported BEC attack cases, the techniques employed by attackers have become more sophisticated, and the demanded amounts have significantly increased in parallel with the post-pandemic digitalization and adoption of remote work models. The losses due to BEC attacks rose from $1.2 billion in 2018 to $1.7 billion in 2019, $1.8 billion in 2020, and $2.7 billion in 2022. These figures show a 125% increase in BEC attacks over the past four years.
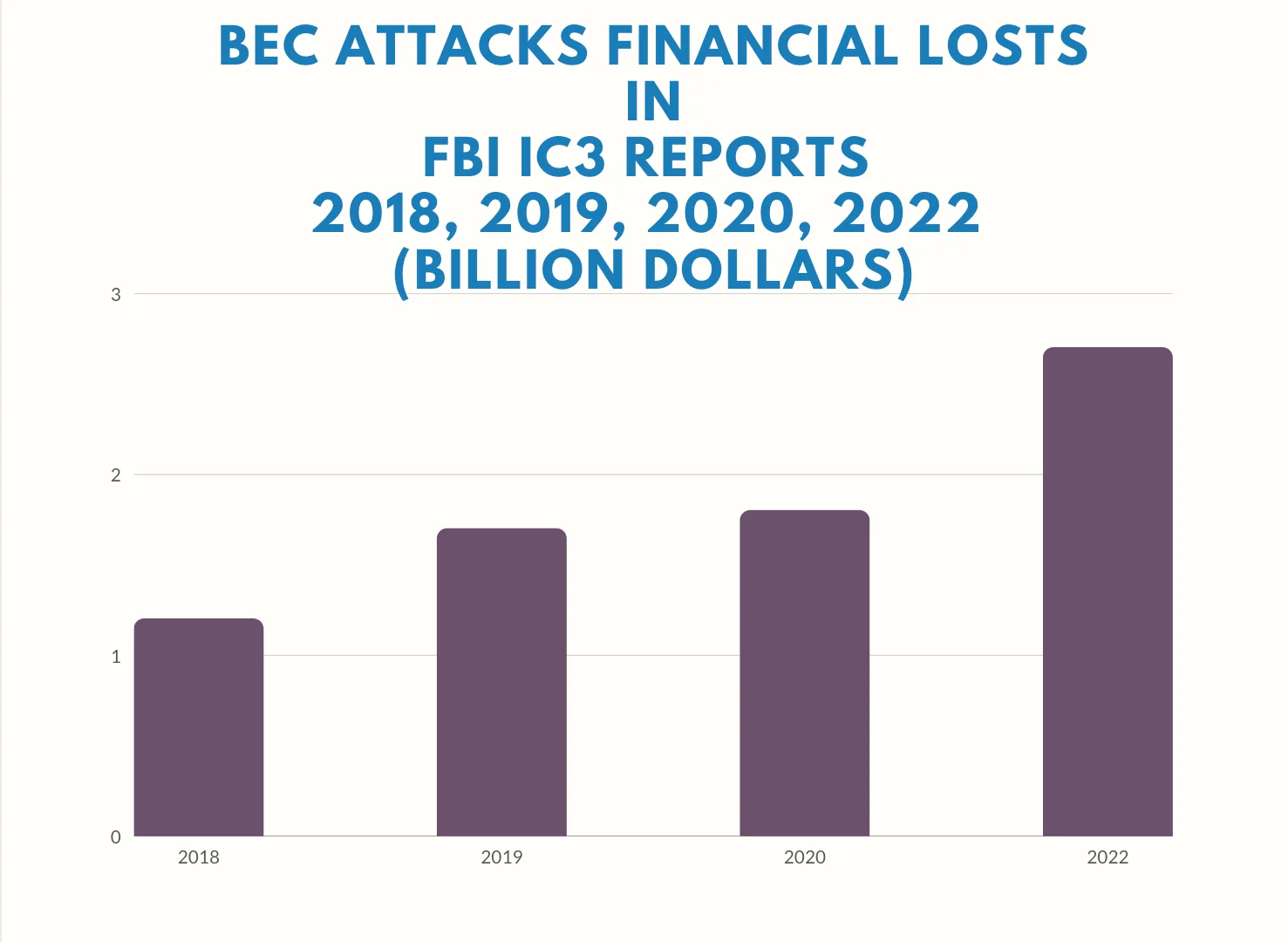
FBI IC3 Annual Reports, BEC Attacks, 2018, 2019, 2020, 2022
The Weakest Link in the Chain: Humans
While many sophisticated security solutions focus on email attachments and malicious file extensions, company employees can fall victim to plain text emails written in simple language.
According to the 2023 Email Security Report by Abnormal Security, over 98% of employees fail to report BEC email attacks. The same study reveals that entry-level employees respond to text-based BEC emails in 78% of reported incidents, particularly in sales and marketing departments.
Another noteworthy finding from Verizon’s 2023 DBIR report is that Business Email Compromise (BEC) attacks stand out in over 67% of all cases where data breaches occur after an initial compromise.
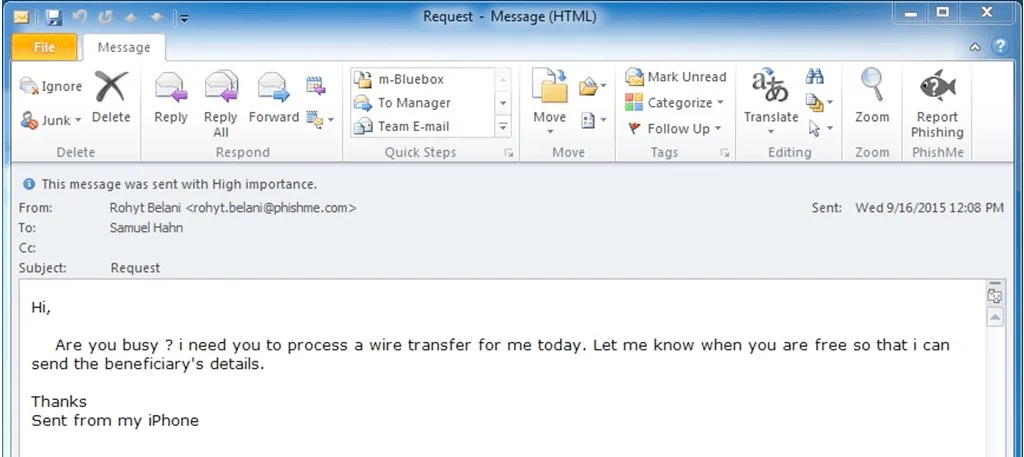
An example of a malicious email sent by an attacker on behalf of a company CEO.
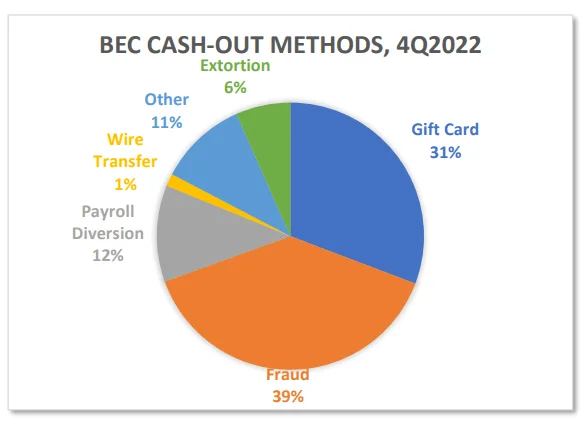
BEC Cashout Methods
In response to the proactive approach of security teams, attackers are complicating their attacks. In their primitive form, Business Email Compromise (BEC) attacks consisted of attackers hacking or spoofing business or personal email, then sending wire transfers or requesting gift cards to fraudulent bank accounts. Nowadays, fraudsters are reaching their goal more discreetly and faster by demanding that their victims send money to their cryptocurrency accounts.
According to the Phishing Activity Trends Report 4th Quarter 2022 published by APWG, while the rate of attackers requesting gift cards as a payment method remained at 31%, advance fee fraud scams outperformed gift card requests, the most popular payment method, with 39%.
BEC attacks against the Food & Agriculture sector have been added to the sophisticated attack methods of the attackers. For this purpose, on December 15, 2022, the Federal Bureau of Investigation (FBI), the Food and Drug Administration’s Office of Criminal Investigation (FDA OCI), and the US Department of Agriculture (USDA) released the Joint Cybersecurity Advisory (CSA) to provides mitigation recommendations to help reduce the risk of financial loss and possible food contamination resulting from these recent attacks.
In this method of attack on the Food & Agriculture industry, fraudsters impersonate employees of legitimate companies using fake emails and domain names and order large quantities of food products. The victim companies fulfill this order and ship the products, but they do not receive any payment in return.
Manipulating Emotions: The Key Strategy in Business Email Compromise (BEC) Attacks
In Business Email Compromise (BEC) attacks, attackers capitalize on the victim’s emotional responses as part of their strategy, exploiting their emotional state for malicious purposes.
- Trust and Urgency
They manipulate the victim’s trust by impersonating high-ranking individuals like the CEO or reputable organizations. Simultaneously, they apply time pressure to create a sense of urgency, coercing the victim into making hasty and potentially detrimental decisions.
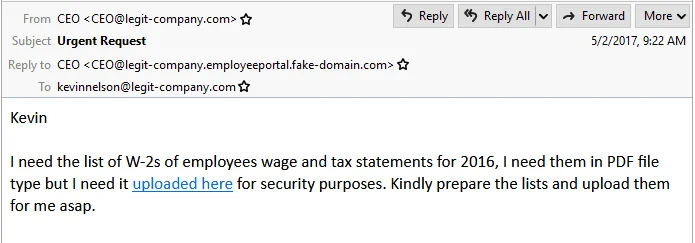
Source: Trustwave
- Fear and Anxiety
Attackers aim to induce anxiety and fear in their victims. They exploit victims’ emotional responses by utilizing tactics such as issuing threats of legal repercussions or financial losses.
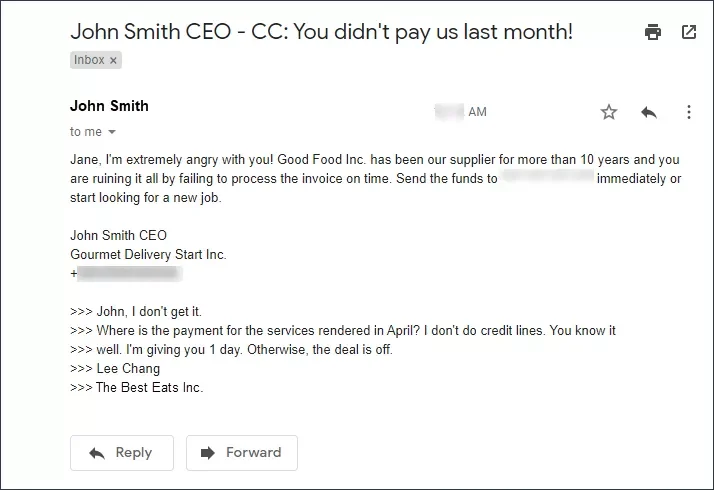
Source: Clario
- Curiosity
Attackers exploit their victims’ curiosity by using tactics such as emphasizing that the victim is an important person, offering special opportunities or advantages, providing access to private information, etc. Thus, they motivate them to perform the actions they want.
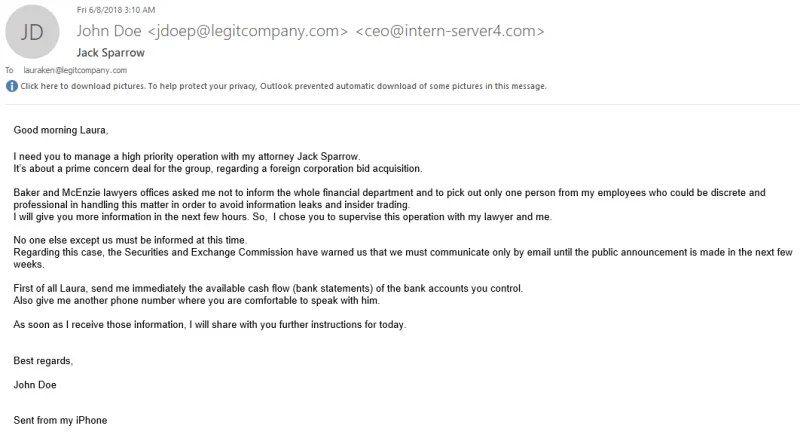
Source: Trustwave
- Helpfulness
Attackers exploit the willingness of their victims to help or cooperate, often by impersonating an employee within a company, to manipulate their sense of helpfulness.
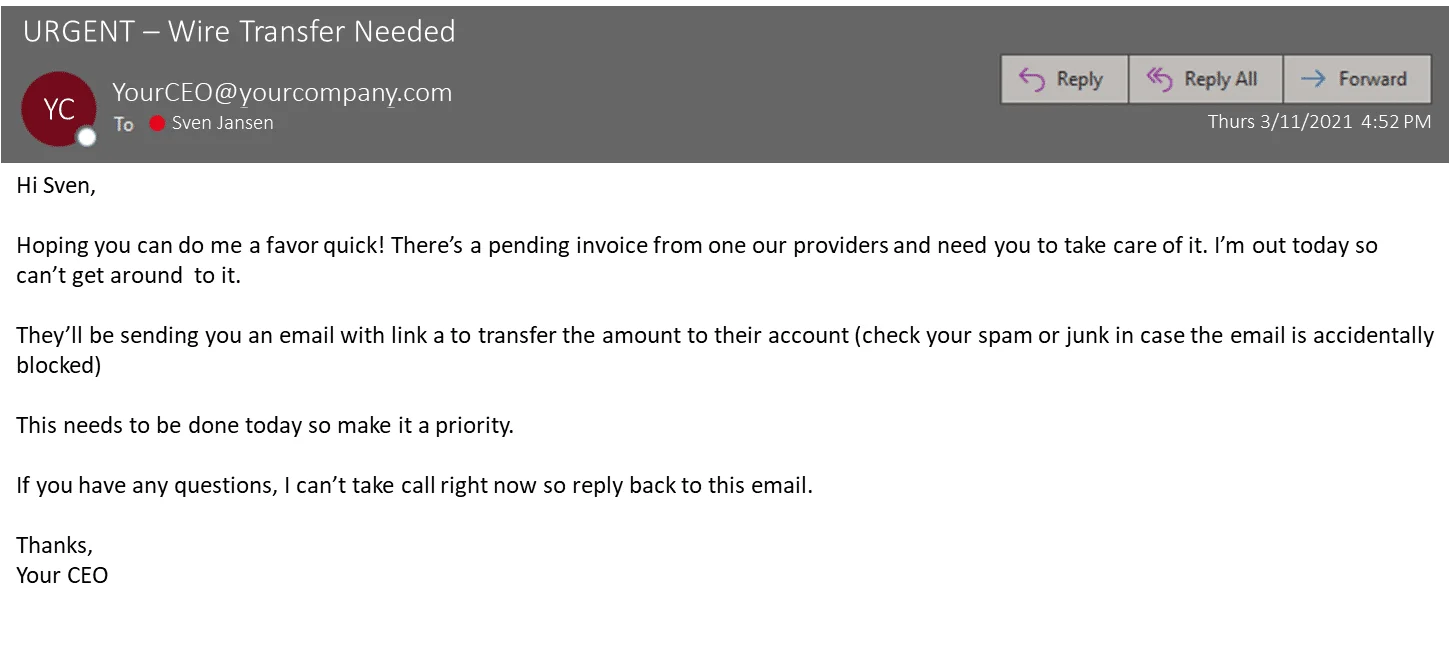
Source: Magnet Forensics
By targeting these emotional responses, attackers distract victims, influence their decision-making processes, and manipulate them to make wrong decisions. Therefore, sensitivity and carefulness are an important factor in preventing BEC attacks.
Preventing Business Email Compromise (BEC) Attacks: A Multilayered Approach
To counter and prevent Business Email Compromise (BEC) attacks effectively, organizations can implement multiple layers of protection. Here are some recommended measures:
- Email Authentication Protocols: Implement Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC) protocols to authenticate email senders and prevent spoofing.
- Brand Indicators for Message Identification (BIMI): Incorporate BIMI policies to enhance email security and validate the authenticity of emails using verified logos and indicators.
- Employee Awareness Training: Conduct regular training sessions to educate employees about BEC attacks, including the recognition of common red flags, such as urgent requests for fund transfers, unusual sender addresses, and grammatical errors in email messages. In the context of BEC attacks, if you are not a very specific target for the attacker, the attackers’ rushed style, language, and spelling errors can draw attention as details that give away the attempted attack. With the proliferation of artificial intelligence language models, it should not be forgotten that attackers can prepare emails of professional quality that are indistinguishable from reality in any language and for any organization. Moreover, advanced AI language models can mimic the person, tone, and writing style to be used in the attack based on publicly available writing samples and speech patterns, enabling them to craft more convincing email messages.
- Robust Password Policies: Encourage employees to use strong, unique passwords for their email accounts, enable Two-Factor Authentication (2FA), and use password managers whenever possible.
- Vendor and Supplier Due Diligence: Implement a rigorous vetting process for suppliers and vendors, verifying their security measures and ensuring their adherence to industry standards.
- Policy, procedure, and Incident Response Plan: Develop a comprehensive incident response plan that includes specific procedures for handling suspected BEC attacks, including reporting incidents, communicating with financial institutions, and involving law enforcement if necessary. Having a secure email policy and procedure is essential for organizations to combat BEC attacks effectively. It establishes guidelines for employees to follow, emphasizing the importance of caution and verification when dealing with suspicious emails. The policy outlines steps to handle suspected BEC attacks, including reporting incidents, preserving evidence, and escalating to the appropriate channels. It also addresses secure communication practices, such as email encryption and strong passwords. By incorporating these measures into a comprehensive incident response plan, organizations can mitigate the impact of BEC attacks and reduce the risk of future occurrences.
By implementing these measures, organizations can significantly reduce their vulnerability to BEC attacks and strengthen their overall cybersecurity posture. Remember, maintaining a high level of vigilance and continuously educating employees about emerging threats is crucial for staying one step ahead of attackers.
How does threat intelligence help organizations tackle BEC attacks?
Threat intelligence plays a vital role in helping organizations tackle Business Email Compromise (BEC) attacks effectively. By incorporating threat intelligence into their cybersecurity strategies, organizations gain valuable insights into the latest tactics, techniques, and Indicators of Compromise (IoCs) used by attackers in BEC attacks. Here’s how threat intelligence can assist organizations in countering BEC attacks:
- Early Detection: Threat intelligence sources, such as cybersecurity research firms, government agencies, and information sharing platforms, continuously monitor and analyze emerging threats, including BEC attack trends. By subscribing to these intelligence feeds, organizations can receive timely alerts and updates about new attack vectors, compromised email addresses, or phishing campaigns related to BEC attacks. This early warning enables organizations to proactively identify and respond to potential threats before they can cause significant damage.
- Behavioral Analysis: Threat intelligence can provide behavioral analysis of BEC attacks, helping organizations understand the techniques employed by attackers. This analysis includes identifying patterns in email content, metadata, sender behavior, and social engineering tactics commonly used in BEC attacks. Armed with this knowledge, organizations can train employees to recognize these behavioral patterns and respond appropriately, such as verifying requests through alternative communication channels or double-checking email addresses before initiating any financial transactions.
- Collaboration and Information Sharing: Threat intelligence promotes collaboration and information sharing among organizations facing similar threats. Industry-specific forums, cybersecurity communities, and threat intelligence platforms enable organizations to share insights, experiences, and best practices for countering BEC attacks. By participating in these collaborative efforts, organizations can enhance their understanding of the threat landscape, receive real-time updates, and benefit from collective defense strategies.
You are not alone, power your organization’s security posture with SOCRadar’s Extended Threat Intelligence
The AI-powered Digital Risk Protection service provided by SOCRadar analyzes millions of domain names to detect phishing domains created for your brand and entire business network. It identifies domain registrations that mimic your organization’s name or owned brands and instantly notify users. With SOCRadar, security teams can initiate the takedown process of domain names impersonating the organization or its brands with just one click, without additional legal or procedural obligations.
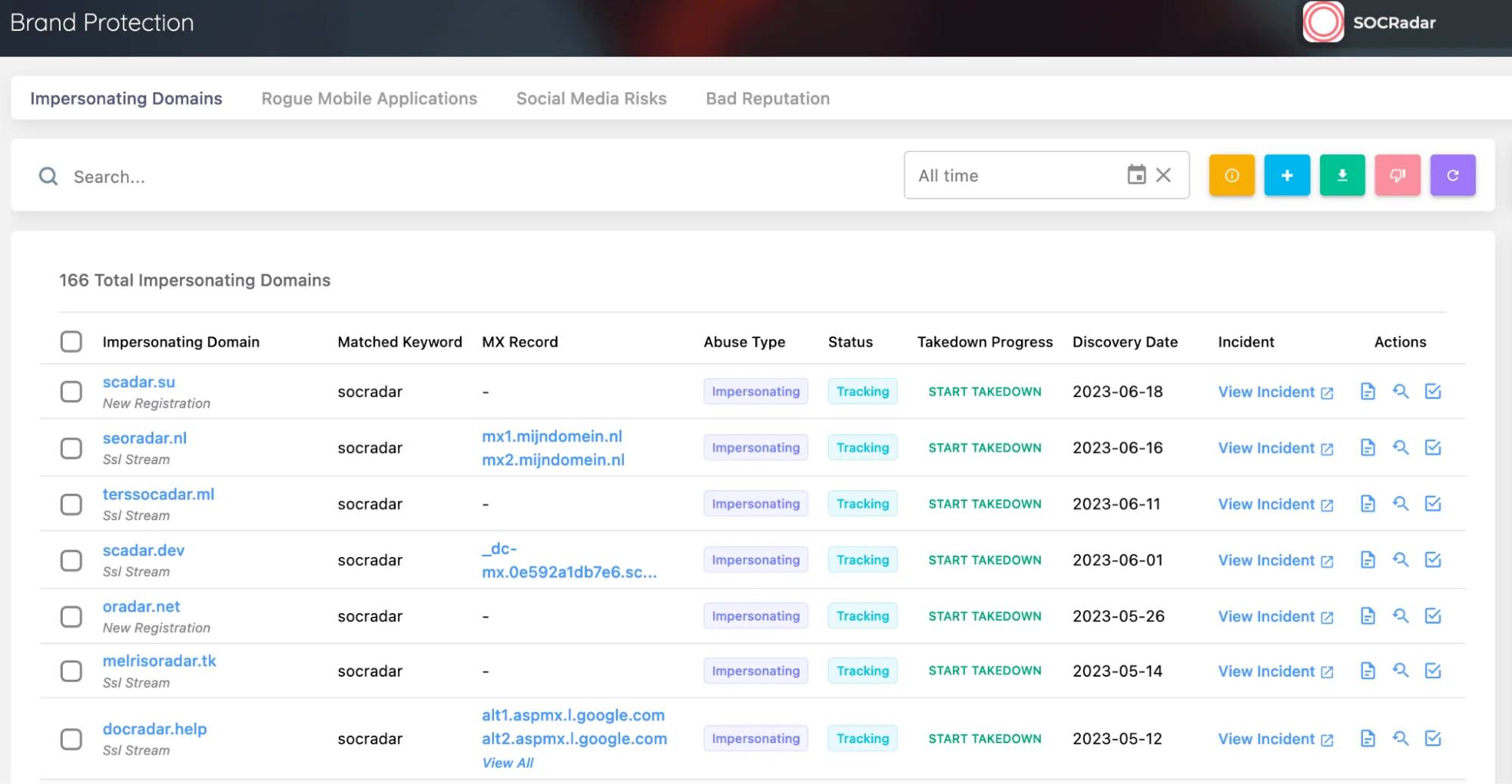
SOCRadar’s Brand Protection
Additionally, real-time alerts ensure that you are informed before your domain names and SSL/TLS certificates expire, allowing you to ensure the security of your digital assets. SOCRadar closely monitors domain names taken by phishing attackers in the DNS records of these emails, particularly changes in MX records, and instantly notifies you of any modifications.
With the SOCRadar Breach Database module, you can check if any of your employees or business partners’ information is exposed in disclosure lists through the platform and quickly initiate password changes in case of exposure.
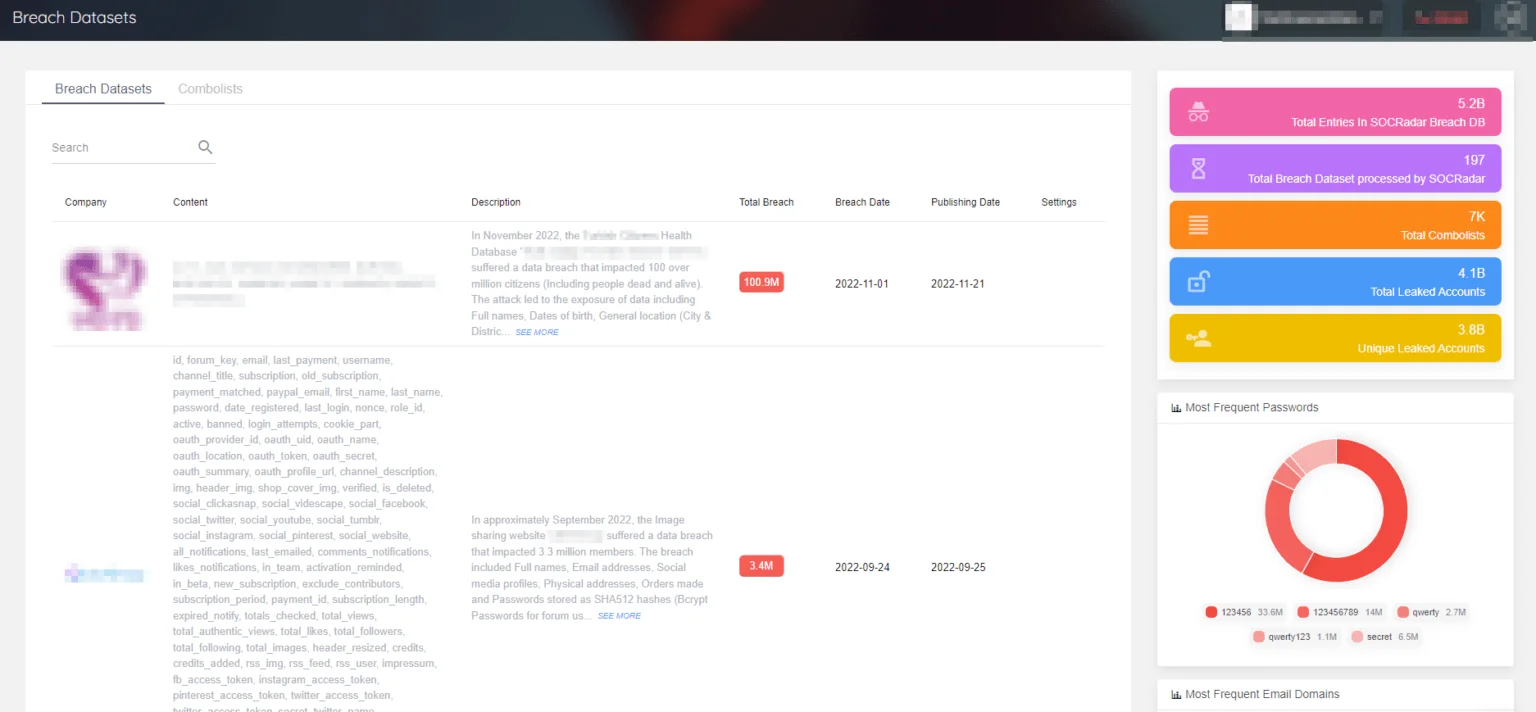
Breach Datasets on the SOCRadar platform
Through SOCRadar’s Supply Chain Intelligence module, you can monitor and alert your employees to be cautious of emails from suppliers that have been hacked or subjected to data breaches.
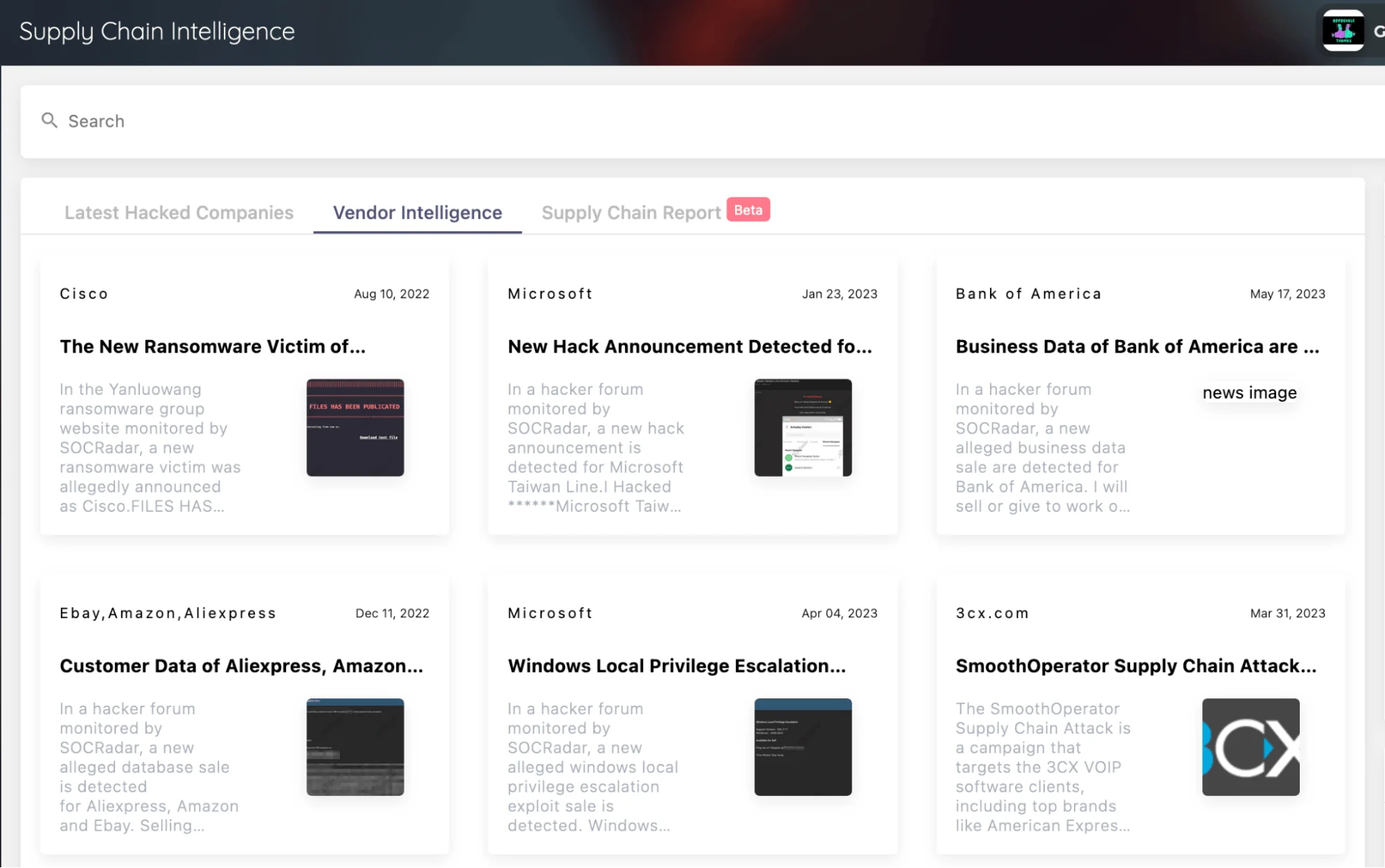
SOCRadar Supply Chain Intelligence module
Threat actors primarily target your organization’s CEO, CFO, and other key executives. SOCRadar closely monitors and instantly notifies you of any personal data disclosures related to your organization’s key personnel. You can check if the information of your critical employees is present in disclosure lists through the SOCRadar platform, enabling you to stay one step ahead of attackers.
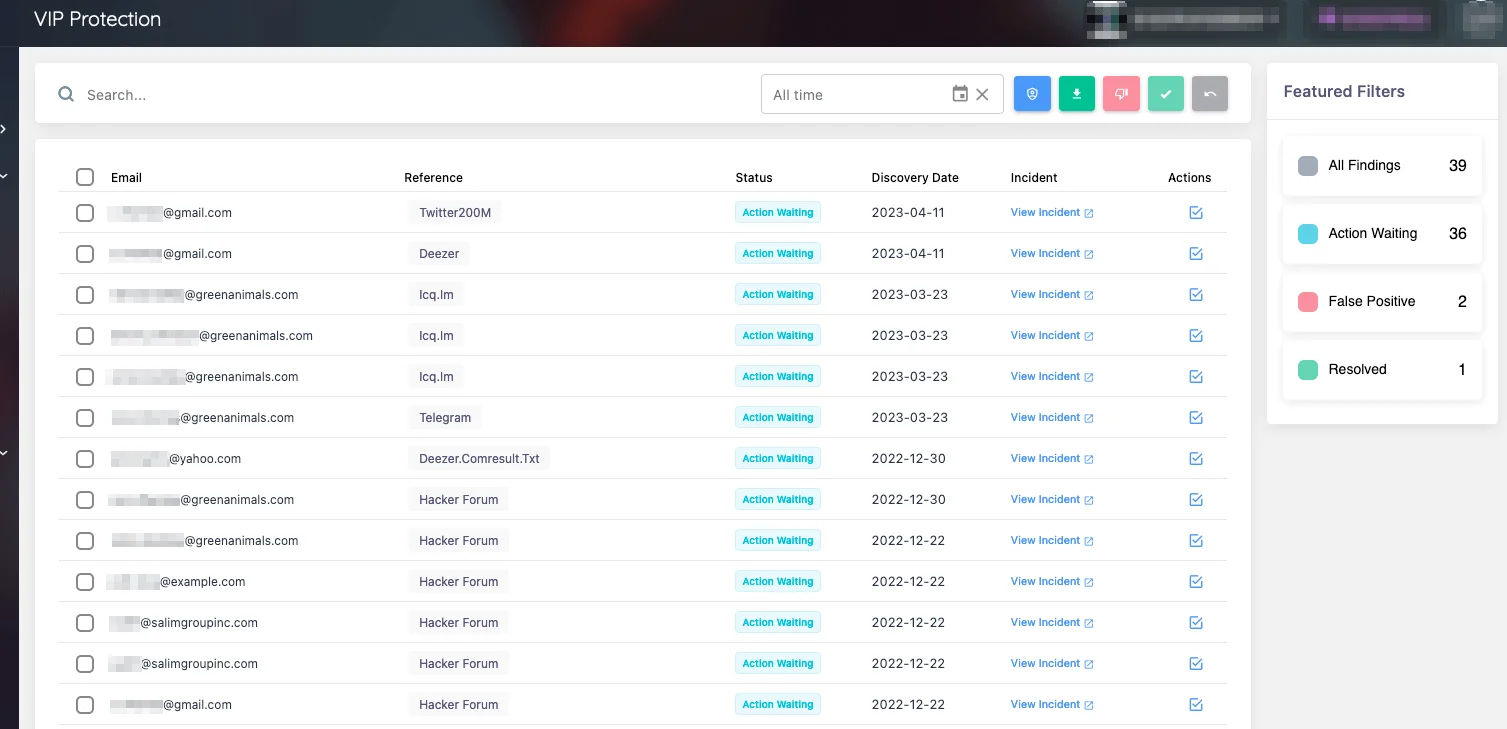
SOCRadar’s VIP Protection
SOCRadar, XTI module performs SPF and DMARC validation on your MX-registered domains, mitigating email spoofing techniques and enhancing email security measures.
In summary, threat intelligence serves as a critical resource for organizations to stay ahead of BEC attacks. By leveraging timely and relevant information, organizations can enhance their detection capabilities, fortify their defenses, and empower employees to make informed decisions when encountering suspicious emails or requests.