
Chain Reactions: Footprints of Major Supply Chain Attacks
In today’s interconnected digital ecosystem, supply chain attacks have emerged as one of the most potent threats. A supply chain attack occurs when threat actors target organizations by focusing on weaker links in their supply chain. The aim is to access source codes, build processes, or update mechanisms by infecting legitimate apps to distribute malware. As witnessed recently in 2023 with high-profile threat actors such as CL0P Ransomware leveraging a zero-day vulnerability in MOVEit Transfer to conduct ransomware attacks, these can have cascading effects, compromising not just one entity but potentially thousands of organizations that rely on a single compromised component.
The importance of understanding and mitigating supply chain attacks cannot be overstated. As global networks face continuous and unforeseen disruptions due to these cyber-attacks, professionals, and organizations at large must revise their strategies and defenses. The risks are not just about data breaches; they extend to tarnished brand reputations, financial losses, and in some cases, national security implications. According to Comparitech, since 2020, around 229 million customers and 221 thousand packages have been affected by supply chain attacks.
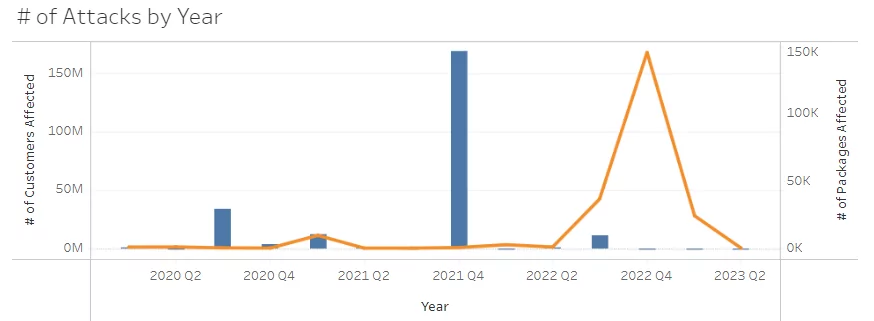
Blue bar: # of Customers Affected
Orange Line: # of Packages Affected
SOCRadar Threat Intelligence is at the forefront of providing solutions to combat these evolving threats. Its Extended Threat Intelligence solution offers a holistic approach to preparing for supply chain attacks. SOCRadar tracks the latest hacked companies and provides vendor intelligence to inform on the potential impact of the latest news can have on the scene. Additionally, it provides supply chain reports for multiple companies that have a big role in the supply chain.
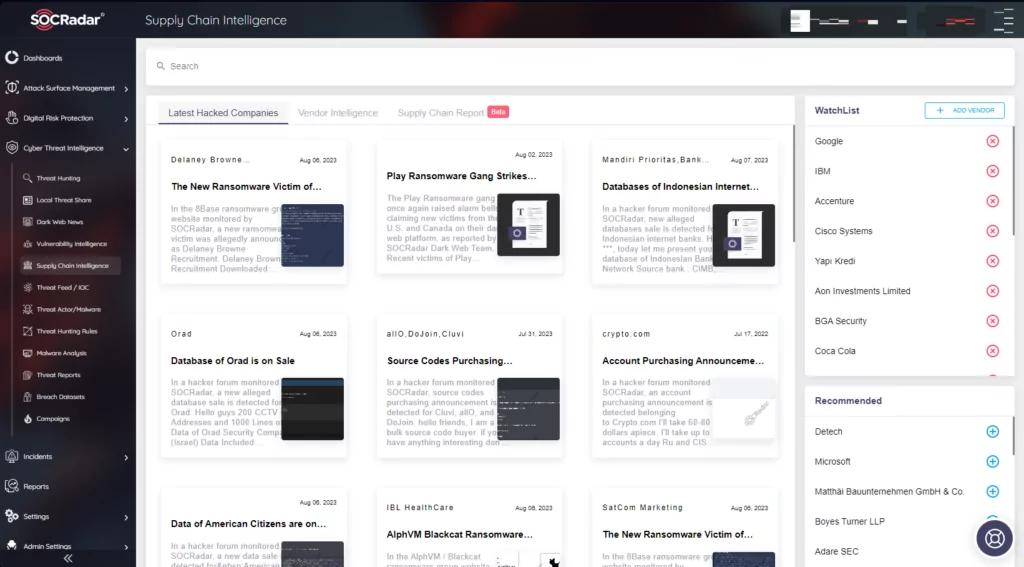
In this blog post, we will list and briefly explain some of the most important supply chain attacks that have occurred since the start of 2023. It will be a continuous effort, so keep an eye on this page in the future.
Ivanti EPMM: Multiple Vulnerabilities Lead to Supply Chain Issue
July 2023
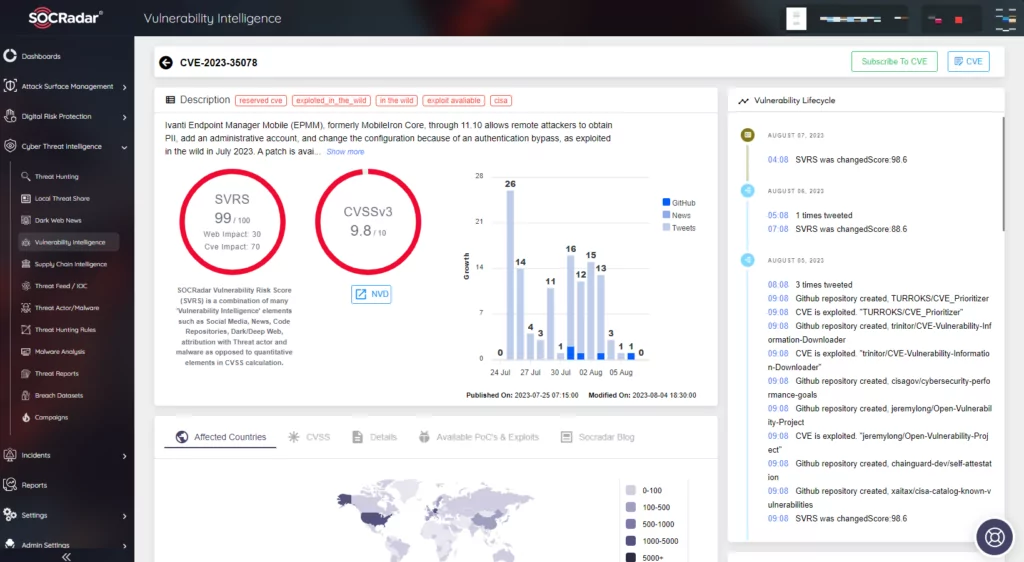
In July 2023, Ivanti faced a critical zero-day vulnerability (CVE-2023-35078) in its Endpoint Manager Mobile (EPMM), previously known as MobileIron Core. This flaw allowed unauthorized remote access, potentially exposing user data. The first victim was the Norwegian National Security Authority (NSM). They confirmed that attackers breached a software platform used by 12 ministries in the country by exploiting the zero-day vulnerability. The exact threat actors remain unidentified, but the compromised systems raised concerns over potential access to sensitive data. The events did not stop there, and consecutive vulnerabilities were discovered as well, which are CVE-2023-35081 and CVE-2023-35082.
To explore more on the subject, you can check the SOCRadar blog post here.
MOVEit Transfer: Clop’s Relentless Attacks Hit Near 600 Organizations
June 2023
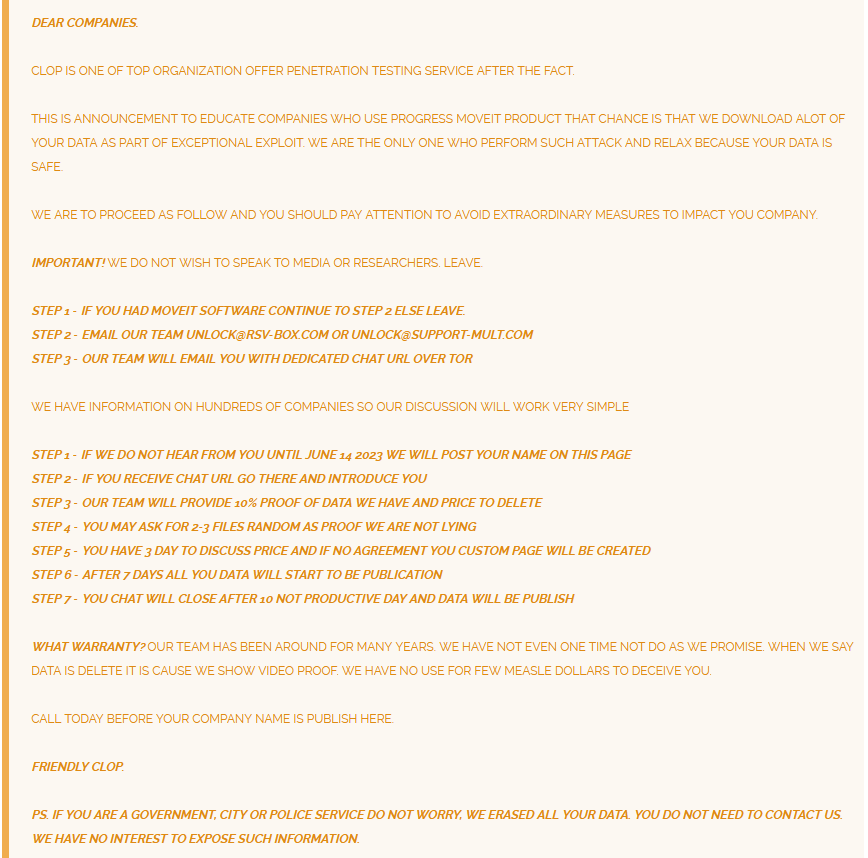
In June 2023, CL0P hit the cyber scene with a zero-day on MOVEit Transfer (CVE-2023-34362). MOVEit Transfer is a managed file transfer software developed by Progress. The vulnerability allowed attackers to execute remote code and steal data from targeted organizations using SQL injection. The notorious CL0P Ransomware group leveraged this vulnerability to launch a series of attacks. Among the victims of Cl0p’s MOVEit Transfer campaign were major entities such as Gen Digital, the parent company of Avast, Norton, AVG, and Avira, as well as PwC, Ernst & Young, and Medibank. Another vulnerability followed the first one, CVE-2023-35036. Since the first report, 595 organizations and more than 30 million individuals have been affected by CL0P’s actions.
To explore more on the subject, you can check the SOCRadar blog post here.
SmoothOperator Supply Chain Attack via 3CX Desktop App
March 2023
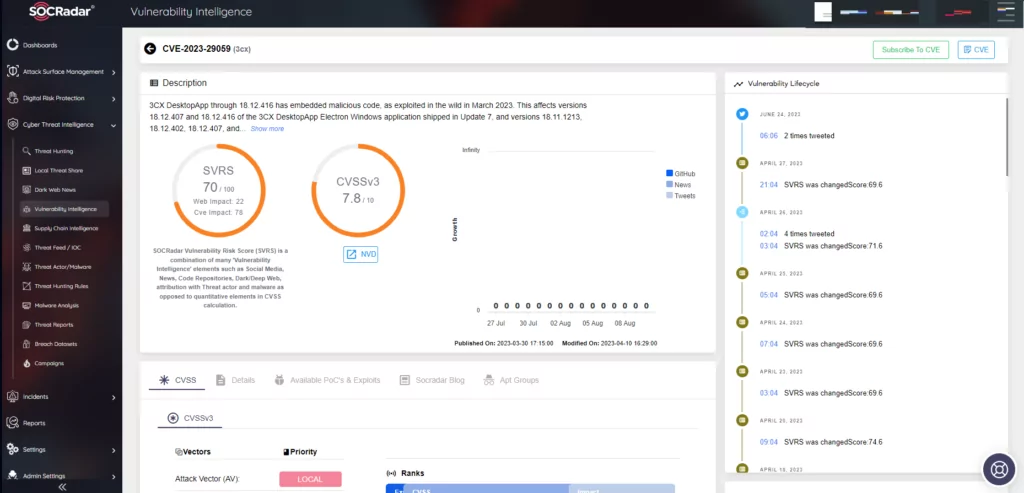
The “SmoothOperator” supply chain attack specifically targeted the 3CX Voice Over Internet Protocol (VoIP) desktop client. The vulnerability has been tagged as CVE-2023-29059 On April 11, 2023, 3CX confirmed that a North Korean hacking group was responsible for the attack. Mandiant’s investigation linked the attack to UNC4736, a group with ties to North Korea. The attackers compromised the 3CX systems using a malware strain named TAXHAUL (or TxRLoader), which subsequently deployed another malware downloader called Coldcat. In addition to this, macOS systems were also targeted, getting infected with a backdoor malware named Simplesea.
To explore more on the subject, you can check the SOCRadar blog post here.
GoAnywhere MFT Supply Chain Issue Contributed to Surge in Ransomware Attacks
March 2023
In February 2023, a critical zero-day vulnerability was identified in the GoAnywhere MFT (Managed File Transfer) product by Fortra, tracked as CVE-2023-0669, which leads to remote code execution. The notorious CL0P ransomware group, known for its history of targeting the healthcare industry, was a primary actor leveraging this vulnerability. Its exploitation in March led to a staggering 91% increase in ransomware attacks that month compared to February. Among the victims was Brightline, a pediatric mental health provider, which confirmed a data breach affecting over 780,000 patients due to the CL0P group’s exploitation of the compromised GoAnywhere MFT service.
To explore the subject more, you can check the SOCRadar blog post here.
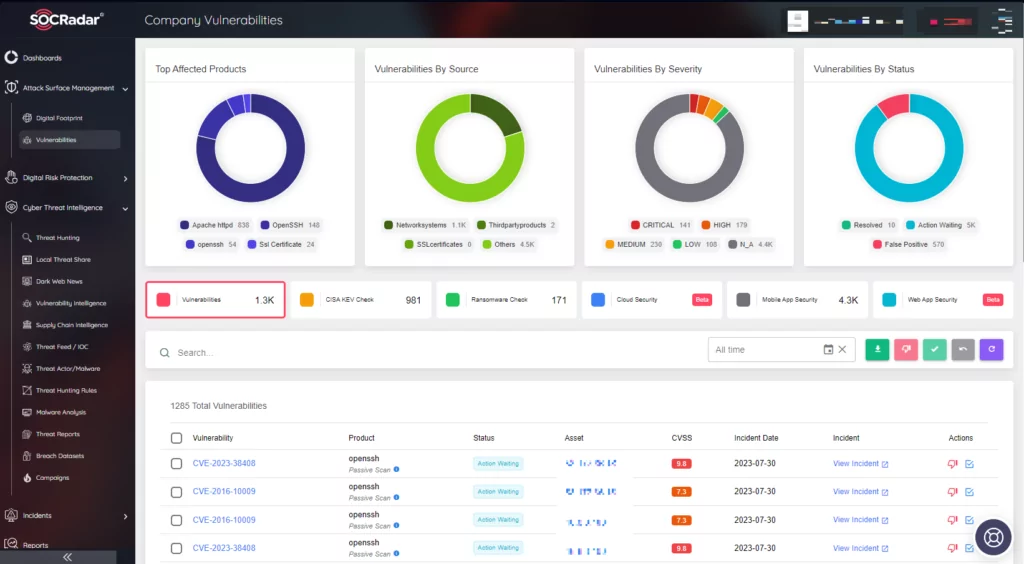
- SOCRadar’s External Attack Surface Management (EASM) offers a comprehensive solution for organizations to proactively identify, monitor, and mitigate potential threats in the digital realm. By continuously scanning and mapping an organization’s digital footprint SOCRadar’s EASM provides real-time insights into exposed assets, vulnerabilities, and potential threats. With SOCRadar’s EASM, organizations can fortify their defenses if vulnerabilities such as the above-mentioned are present in their environment.
Conclusion
The digital landscape has evolved rapidly, and with it, the sophistication and frequency of cyberattacks have surged, especially in the realm of supply chain compromises. No organization, regardless of its size or stature, is immune to supply chain attakcs. These incidents underscore the critical need for robust cybersecurity measures and proactive threat intelligence.
At this juncture, SOCRadar emerges as a beacon of hope. With its advanced threat intelligence capabilities, SOCRadar offers organizations a proactive approach to identifying potential threats before they escalate. By continuously monitoring the digital footprint of businesses, SOCRadar ensures that vulnerabilities are spotted and addressed promptly. Moreover, with real-time alerts, businesses can stay one step ahead of potential attackers, ensuring their digital assets remain uncompromised.
In this ever-evolving cyber landscape, staying informed and prepared is no longer a luxury but a necessity. And with partners like SOCRadar, businesses can navigate this challenging terrain with confidence, ensuring their operations remain secure and resilient against the ever-looming threat of supply chain attacks.



































