
The Lifecycle of a Ransomware Attack
There are many different types of ransomware and multiple criminal gangs operating in this underworld. Once ransomware gangs assume control, they usually demand a ransom to restore the victim’s encrypted data access. The frequency of these attacks is growing, so that we devoted Cyber Security Awareness Month, which many international cyber security actors focused on, to the issue of ransomware.
SOCRadar provides a solution to help them prepare to minimize disruptions caused by ransomware with the digital tools it has developed. If you want to benefit from SOCRadar’s services effectively, it is necessary to know about each stage of a ransomware attack.
The lifecycle of a ransomware attack includes five stages. There are more sub-titles within these five steps, which can be summarized in the outline. Now let’s take a look at all of them one by one. The lifecycle here was created keeping in mind other ransomware-related content on the SOCRadar blog. It is open to improvement with each new attack.
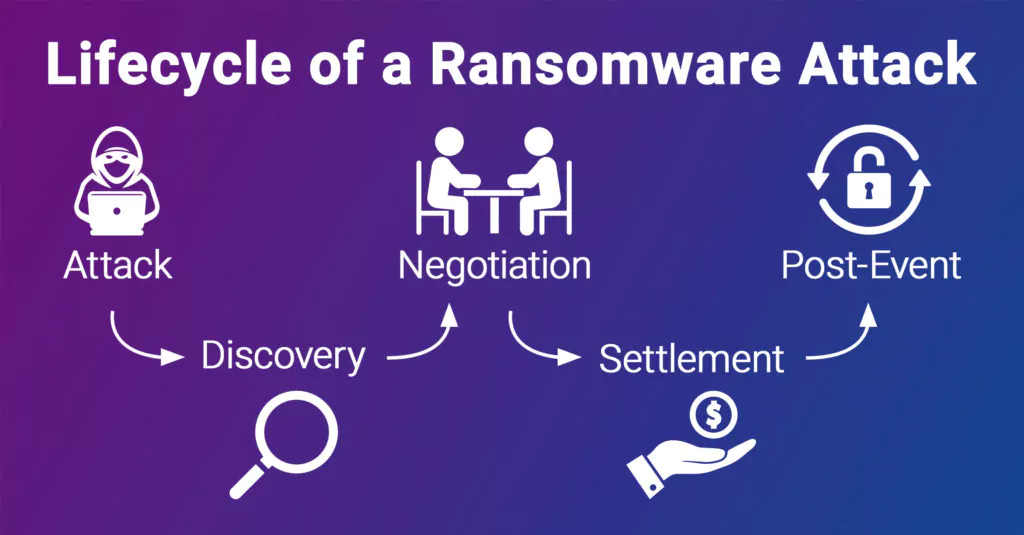
Attack: Initial Access
When the malicious ransomware files are detected, it may be too late to prevent the attack from moving forward. Probably all data will be encrypted. There is a chance to contain the attack and potentially some parts of the attack entirely. Success will depend heavily on a well-rehearsed defense-in-depth strategy and a thought-out preparatory plan explicitly designed to thwart a ransomware attack.
The online behavior of the end-user, unaware of cybersecurity, can be enough for ransomware attacks to start. This relates to phishing, BEC fraud, malspam, and by extension — ransomware and malware incidents in general since it’s ubiquitous for end-users to be the first to encounter a security incident.
It is highly recommended that end-users receive periodic training on the types of threats they may encounter, what actions they should or should not take, and how and in what manner they should do so.
Discovery: Consolidation and Preparation
Once attackers infiltrate a system, they demand a ransom for the decryption key to unlock the encrypted files. Companies often discover the attack via a flashing alert on all connected computers when they leave a ransom note emailed to an administrator, a file dumped on a server, or even a message with contact information, payment delivery time, and the consequences of unmet conditions.
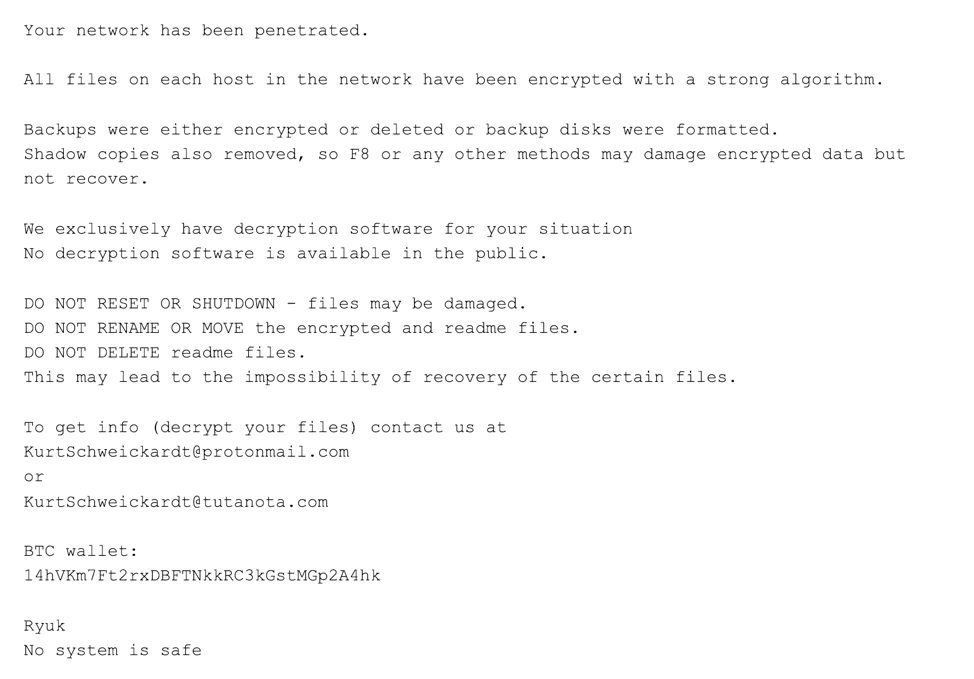
The ransomware scans and maps the locations containing those files locally and on both mapped and unmapped network-accessible systems. Many ransomware variants also look for cloud files storage repositories such as Box, Dropbox, and others. This particular stage is the first real opportunity that security analysts have to stop the ransomware kill chain.
The attacker’s goal is to access all relevant devices in the environment, including servers and workstations. To achieve this, attackers will look for a way to gain Domain Administrator privileges, control panels for security systems such as Security Information and Event Management (SIEM) or Endpoint Detection and Response (EDR), and virtualization platforms such as VMWare VCenter.
Defenses to be applied at this point are vital to limit the spread of an attacker who has gained access to the network. In this way, the attacker is prevented from accessing other systems, and the damage that may occur is limited.
These defenses help mitigate any network compromise regardless of the attackers’ end goal or how they gained initial access. However, if an attacker can achieve their goals in this phase, they will move to the impact on target phase, where destructive activity is carried out.
Impact on Target: Data Exfiltration and Destroyed Backups
Once all desired data has been exfiltrated, the attackers will seek to destroy your backups and then encrypt your data. At this point, ransom notes or lock screens are distributed to warn of a ransomware attack and often provide instructions on payment. They may also threaten further activity such as Distributed-Denial-of-Service (DDoS).
In this phase, the attacker has already achieved the access they want, and the window for detection and disruption is small. With careful analysis, you may be able to detect data being exfiltrated from your network. Unfortunately, this is often only seen after the fact by forensic investigators.
When an attacker has reached this attack phase, a robust and well-tested backup system is the most critical control. As attackers destroy backups, offline or disconnected backups are essential to recovering from the encryption.
During a complex incident, communication is key to establishing how you and your stakeholders will communicate ahead of time can pay dividends during an incident. You can learn about pre-detection methods using SOCRadar’s tools.

Negotiation and Settlement
Under normal circumstances, a company that encounters a ransomware attack will seek help from a cybersecurity expert even before confirming the attack. The company asks this professional to negotiate with the hackers. The ransom price may still be high, while hackers are waiting for price bargains. But hackers can increase the price.
The ransomware negotiation process could go like this:
- Communicating with attackers
- Obtaining proof of decryption
- Securing evidence of data theft
- Negotiate for a discount
Negotiations can be complex, and sometimes attackers may demand additional payment. Additionally, decryption tools may have bugs that skip mapped network drives or folders with long paths and unusual characters.
An investigation is crucial to determine how hackers got in, what was exposed, and whether they still have access.
After the ransom negotiations are over, companies should carefully consider the strategy behind paying or not paying the ransom. If companies agree, the payment is usually delivered via cryptocurrency such as Bitcoin, as it is more difficult to identify the payees.
What Can be Encountered After the Attack is Over?
For many companies, the settlement is just the beginning of ransomware attack costs. Companies will also have to pay to restore back-ups, rebuild systems and implement more robust cybersecurity controls to avoid future attacks.
“Advanced Endpoint Monitoring System, Restrict Remote Desktop Protocol (RDP), Regularly Update Software and Operating Systems, Implement Password Management Policies, establish and update Incident Response Plan, and Ransomware Playbook” are recommended by experts for companies to implement stricter cyber control.
Ransomware attacks are increasing day by day. To minimize the impact of attacks, companies create a proactive preparedness plan. Determining to protect and scan for strategic operational and tactical cyber threat intelligences, establish negotiation and payment rules, and external breach communications.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































