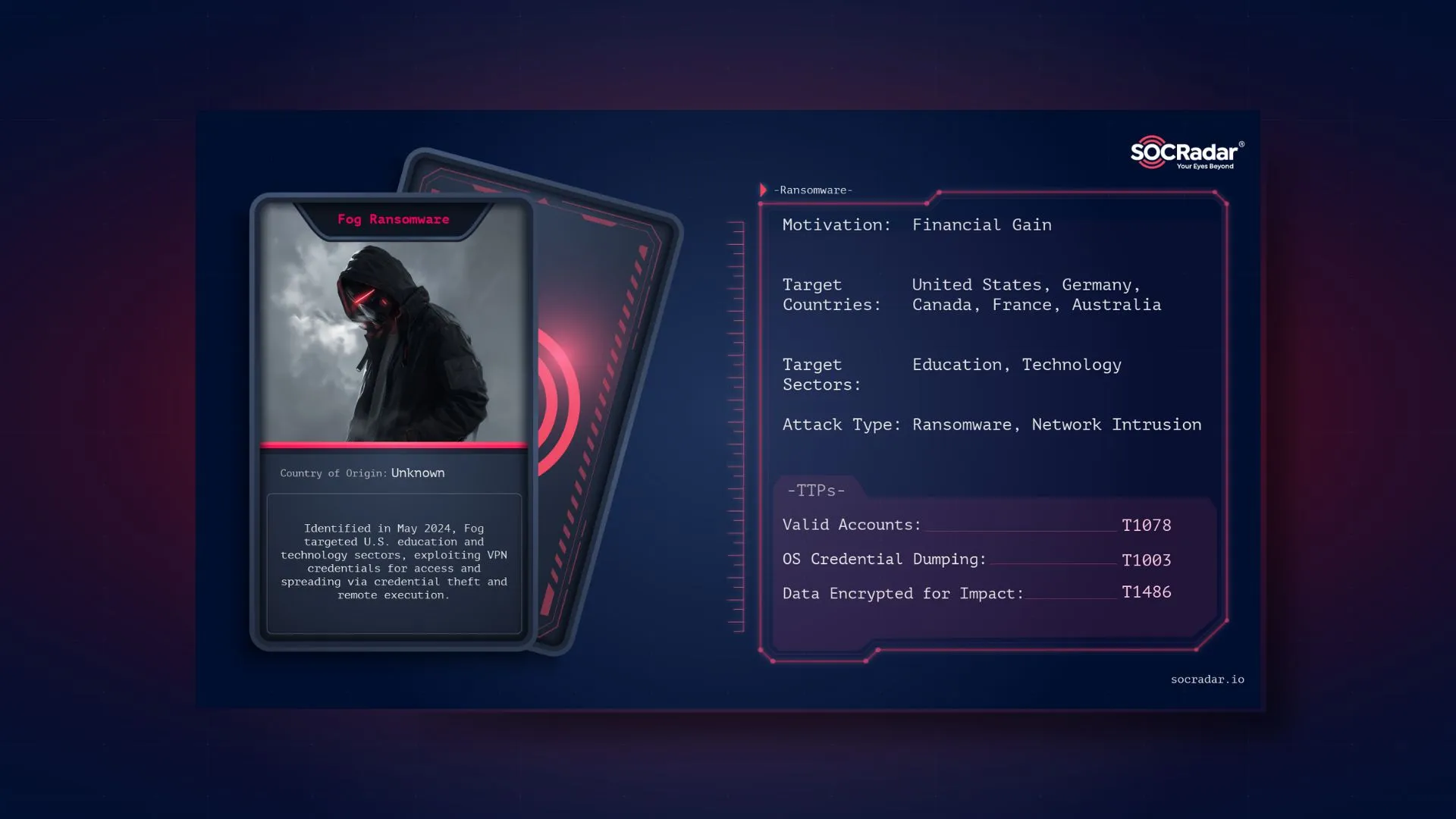
Dark Web Threat Profile: BlackMatter Ransomware Group
We continue to convey the latest news on ransomware on our blog. Cybersecurity researchers have warned of emerging ransomware groups almost every day that could pose a significant threat to businesses: BlackMatter Ransomware is one of them.
A New Face in Town: BlackMatter Ransomware
In July 2021, a new ransomware threat actor entered the stage, the BlackMatter ransomware group. The group utilizes Ransomware-as-a-Service, a model in which the threat actors use the ransomware themselves and rent it to their customers.
Analysts at SOCRadar believe that the BlackMatter group is descendants of the DarkSide ransomware group. After DarkSide’s attack on the Colonial Pipeline, which had devastating results for the US fuel sector, the DarkSide ransomware group has announced its retirement. Not long after their retirement, the BlackMatter group was discovered.
Two ransomware groups’ code and TTP similarities are another evidence that BlackMatter originates from DarkSide.
After their debut, threat actors behind the BlackMatter ransomware group have been actively looking for initial access brokers and penetration testers and inviting journalists and recovery companies to work together.
A Ransomware Gang with Principles
Even though their number one priority is money, like many other ransomware groups, the BlackMatter group is one with principles.
On their site on the Dark Web, the BlackMatter group states that their service is better than their competitors. They claim that interactions with victims are carried out with honesty and transparency, and they never attack a victim twice, always fulfilling their responsibilities.
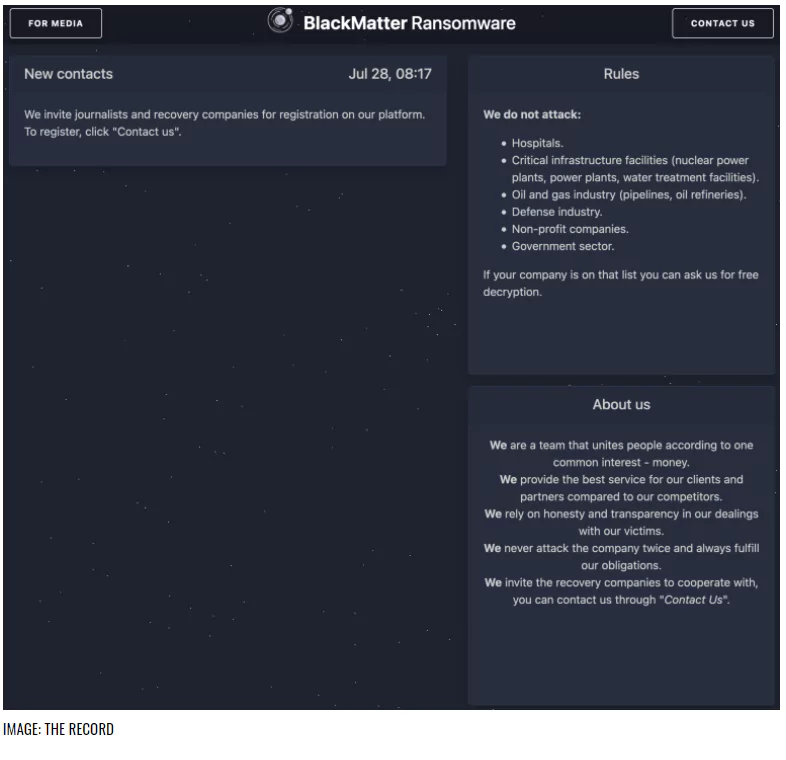
The group states they do not attack hospitals, government sectors, the defense industry, non-profit enterprises, and industries like oil and gas. All areas other than these sectors are in their scope.
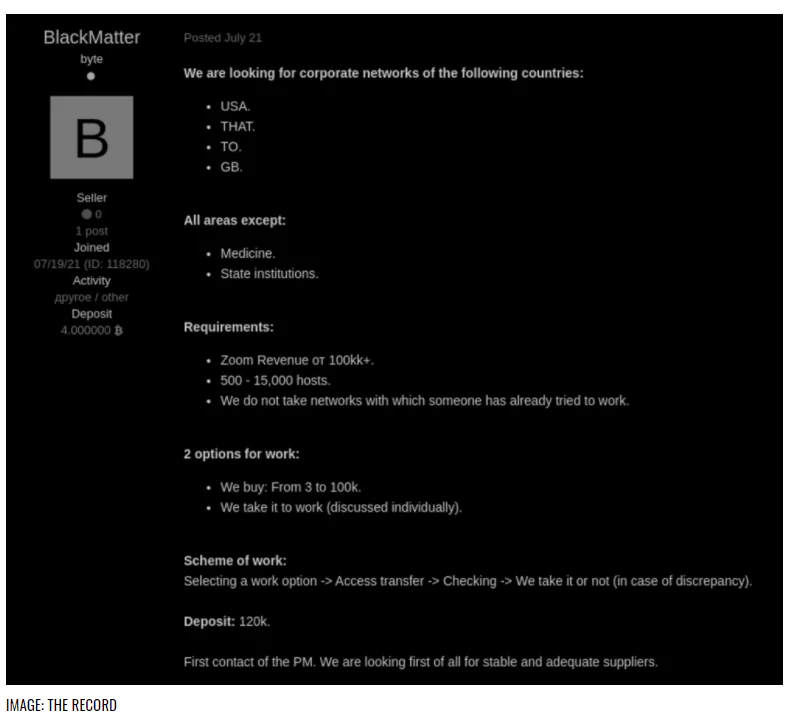
On the 21st of July, the BlackMatter group published an advertisement post on Forum Exploit. In the post, the actors reveal their targeted countries: the US, UK, Canada, and lastly, Australia. They stated that they were targeting companies with revenues of $100 million or more.
Float Like a Butterfly, Sting Like a Bee: BlackMatter’s Tactics
- BlackMatter ransomware usually exists in a .exe file and, like other ransomware, is programmed in C++. Those working in the field feel that threat actors are actively developing ransomware.
- To make analysis and debugging harder, the ransomware utilizes special tricks such as detecting the debugging mode and not executing the encryption if the system is in debugging mode.
- The ransomware also includes a check for administrator rights. If the system does not have admin rights, the ransomware uses another method to increase privileges.
- The ransomware can encrypt open documents by terminating specific processes just before the encryption begins.
- After the encryption, BlackMatter changes the victim’s wallpaper to a ransom notice, just like the DarkSide ransomware.
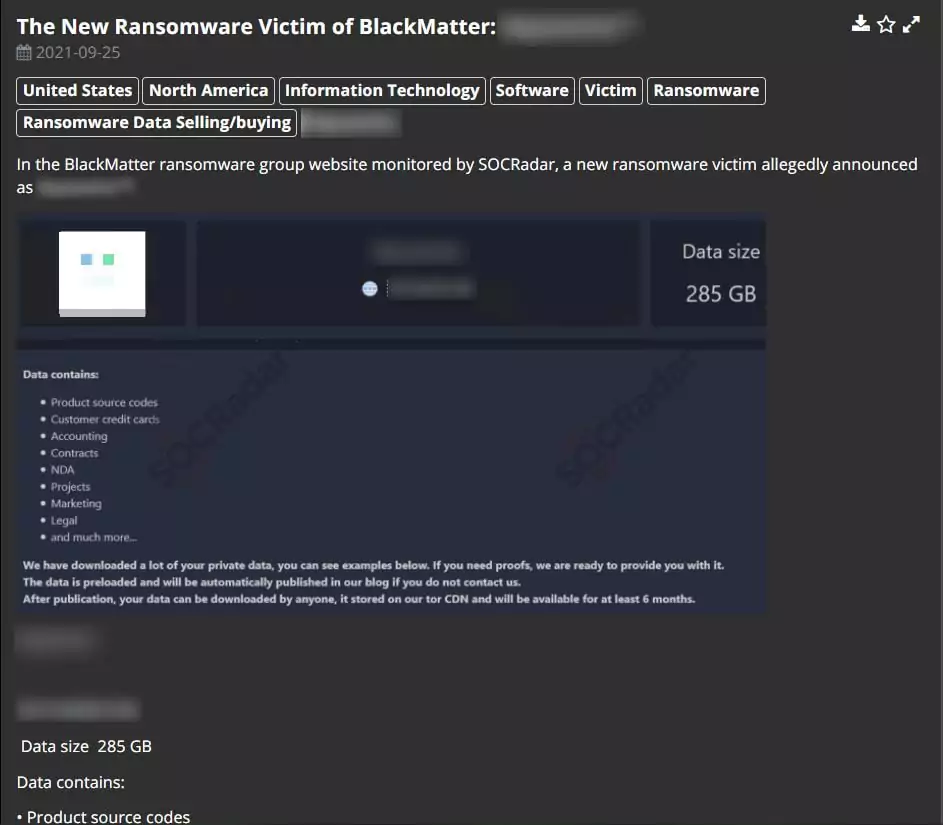
- The ransomware copies the victim’s data; if the ransom is not paid, the threat actors publish the company’s data on their Dark Web site.
SOCRadar’s DarkMirror monitors the Dark Web and provides visibility into the ransomware threats, new victims as well as leaked information.
Researchers at McAfee have compiled a list of TTP’s mapped to MITRE ATT&CK.
- T1134: Access Token Manipulation
- T1486: Data Encrypted for Impact
- T1083: File and Directory Discovery
- T1222.001: Windows File and Directory Permissions Modification
- T1562.001: Disable or Modify Tools
- T1106: Native API
- T1057: Process Discovery
- T1489: Service Stop
- T1497.001: System Checks
- T1135: Network Share Discovery
- T1082: System Information Discovery
- T1592: Gather Victim Host Information
- T1070: Valid Accounts
- T1547: Boot or Logon Autostart Execution
- T1102: Query Registry
- T1018: Remote System Discovery
- T1112: Modify Registry
References
[1]Blackmatter Group Analysis:”The Dark Side Returns”
[2]REvil Ransomware Operation as Blackmatter
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free