
Threats to Financial Institutions on the Rise
Financial institutions, especially banks, are always one of the significant targets of threat actors. The number of cyber threats against financial institutions that appeared on the darknet and the deep web has increased in 2021. SOCRadar has released a report that summarizes cyber threats in the financial sector during the Q3 period.
The SOCRadar team monitored more than 10,000 deep web posts, thousands of chatters on hacker channels, ransomware attacks targeting financial institutions, banking trojans in the wild, DDoS threats, vulnerabilities, and supply-chain threats for financial institutions.
To achieve this objective, they steal and sell sensitive data or choose extortion by holding the data encrypted with ransomware, threatening data sharing, or executing DDoS attacks. Exploiting vulnerabilities on the supply chain is also an effective method for threat actors to gain access.
You can read the full report by clicking here.
Cyber Threats on the Rise in the Financial Sector
SOCRadar Research Team monitored around ten thousand posts and shares on darknet/deep web forums and hacker channels on different mediums.
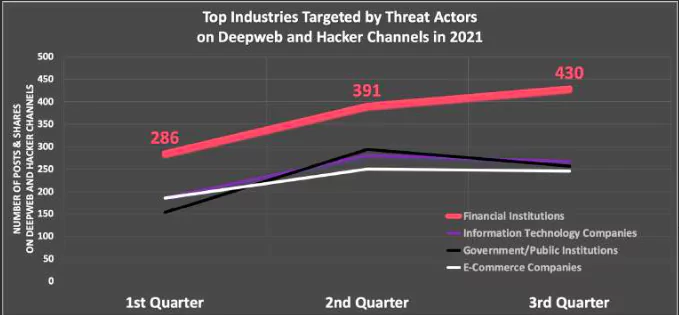
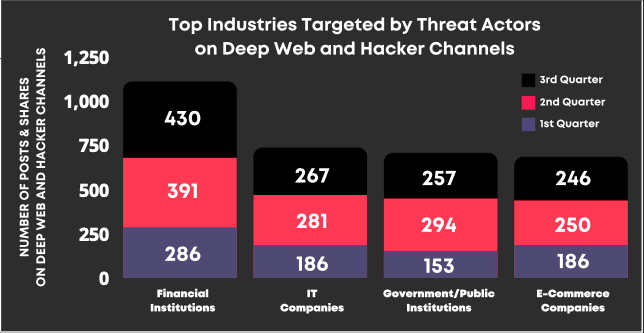
Finance is the top industry targeted by threat actors for the total number of posts and shares on deep web and hacker channels. It is followed by IT firms, government/public institutions, and e-commerce companies.
Most Targeted Countries
Concerning the deep web post and hacker channel shares targeting financial institutions, the most targeted countries in the first three quarters of 2021 are;
- USA
- UK
- India
- Italy
- Russia
- Germany
- Australia
- Brazil
- Canada
- France
- Turkey
- Spain
- Iran
One of the report’s highlights is around 50 ransomware attacks, Lockbit 2.0 is the ransomware group targeting financial institutions most. Various ransomware groups targeted financial institutions in 2021. Lockbit 2.0, Avaddon, Conti, ReVIL, and Cl0p are the head runners.
Also, state-sponsored Advanced Persistent Groups (APTs) and financially motivated threat actors are more organized groups in cyberspace targeting several industries, including finance, with sophisticated attacks. 14.6 million credit card information is sold on the black market so far in 2021, and the spread of banking trojans is on the rise.
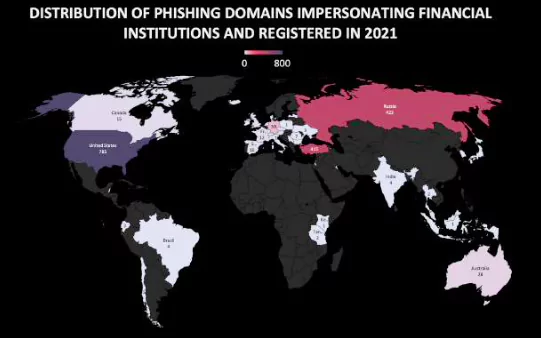
After describing malware targeting banks and their customers in the report, another vital title, phishing domains impersonating financial institutions, is mentioned.
Phishing Domains Impersonating Financial Institutions
SOCRadar detected more than 2,300 phishing domains impersonating financial institutions registered in 2021. Threat actors use phishing domains to lure customers and employees into stealing their credentials and accessing the company systems.
While threat actors prefer free registrars to register these phishing domains, they also might get an SSL/TLS certificate to convince the victims about the website’s legitimacy. Seeing the HTTPS at the beginning of the URL with an excellent padlock sign next to it gives a false sense of security to the users.
SOCRadar discovered that almost 60% of the phishing domains impersonating financial institutions have a valid SSL certificate. It is a very high ratio not observed in phishing domains impersonating companies in other industries.
Top countries targeted by these phishing domains include;
- United States
- Russia
- Turkey
- Germany
- Australia
Top 5 Software Vulnerabilities Exploited by Threat Actors
Different threat actors, from APT groups to ransomware operators, from initial access brokers to average hackers, actively exploit software vulnerabilities. Companies disclosing the service version in use are always on the radar of cybercriminals to see whether the service has critical exploitable vulnerabilities or not.
In 2021, some critical 0-day vulnerabilities will be exploited by threat actors to attack companies in many industries, including financial institutions. In the report, the top 5 critical vulnerabilities widely used by threat actors this year so far are also listed.
1) MS Exchange Server ProxyLogon and ProxyShell Vulnerabilities (ProxyLogon Vulnerabilities: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 & ProxyShell Vulnerabilities: CVE-2021-34473, CVE-2021-34523, CVE-2021-31207)
2) Microsoft MSHTML Remote Code Execution Vulnerability (CVE-2021-40444)
3) Windows NTLM PetitPotam Vulnerability (CVE-2021-36942)
4) Windows Print Spooler PrintNightmare Vulnerability (CVE-2021-34527)
5) VMWare vCenter Server Vulnerability (CVE-2021-22005)

Recent Major Cyber Attacks Targeting Financial Institutions
In 2021, the deep web was filled with threat actors sharing or selling data that belonged to financial institutions. Also, the SOCRadar analyst team has listed some major claims by threat actors in the threat landscape report.
Mellat Bank: In May, SOCRadar detected a threat actor selling a database allegedly belonging to an Iranian bank. The database includes sensitive information of 30 million citizens of Iran.
Bank of China: In this particular post published in October, threat actors claim that they worked on this attack for two months to gain access to the bank’s internal assets. They allegedly obtained source codes for all project software deployed by the Bank of China.
Banorte: In August, a threat actor posted a sale of a Mexican bank’s database. A hacker group called Bandito Gang allegedly breached the database that contains 6.5 million records. The threat actor also shared sample data that consists of 150 thousand lines.
Banco Pichincha: In July, on a hacker forum monitored by SOCRadar, threat actors claimed that they have 120 million bank records allegedly belonging to Banco Pichincha of Ecuador.
Chase Bank: Some leaks are just because of technical errors or some misconfiguration. On August 17, Chase Bank admitted to having a technical bug on its online banking website and app that allowed accidental customer banking information to other customers. Chase Bank sent a notice to its customers on the following days.
Recommendations
In the last part of the report, some recommendations are offered by SOCRadar against the increasing number of cyber threats. These are listed as follows;
- Keeping Track of the Vulnerabilities on Digital Assets: There are particular vulnerabilities and sometimes zero-days that threat actors exploit. SOCRadar discovers almost all digital assets and their vulnerabilities. SOCRadar’s External Attack Surface Mapper tracks and updates assets and their vulnerabilities.
- Identifying and Monitoring Threat Actors: Many organized threat actors like APTs have signature Tactics, Techniques, and Procedures (TTP). Some of them are only active and specific regions and sectors. Monitoring the threat landscape and threat actors will make defenses stronger. SOCRadar’s threat intelligence threat feeds, IOCs, IOAs can help to give the proactive readiness that everybody needs.
- Phishing Control: Social engineering and phishing are the starting attack vectors for many cyber attacks. In addition to all company’s training for not untrusted links and email attachments without verifying their authenticity, SOCRadar can discover impersonating and typo-squatting domains which could be used for phishing campaigns against all customers and employees.
- Dark Web and Deep Web Awareness: Threat actors often find their way into systems by purchasing credentials or intelligence from dark and deep web forums and chatter channels. SOCRadar monitors these channels and creates alarms and incidents for anything related to companies.
You can read the full report by clicking here.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































