
What is External Attack Surface Management?
The attack surface is all hardware, software and cloud assets accessible from the internet that processes or stores data. All exposed IT assets, from servers to APIs, are part of the attack surface, whether or not there are any known vulnerabilities. Millions of these assets appear on the Internet every day and are completely beyond the scope of firewall and endpoint protection services.
The attack surface is divided into four groups; “Known Assets, Unknown Assets, Mimic Assets, 3rd Party Assets.”
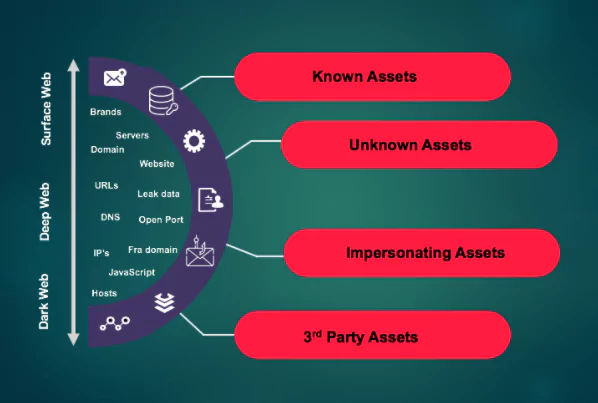
Why is Attack Surface Management Important?
Attack surface management is important as it helps prevent and mitigate risks from:
- IoT and IT assets
- Vulnerable and outdated software
- Large-scale attacks against your industry
- Unknown Open Source Software (OSS)
- Targeted cyber attacks against your organization
- Human errors and omissions such as phishing and data leaks
- Intellectual property infringement
- Vendor-managed assets
Timely identification of digital assets is essential if you want to have a robust threat intelligence network. Timely identification of assets can greatly reduce the risk of data breaches and data leaks. Any vulnerable point in the organization is all it takes for an attacker to launch a cyberattack.
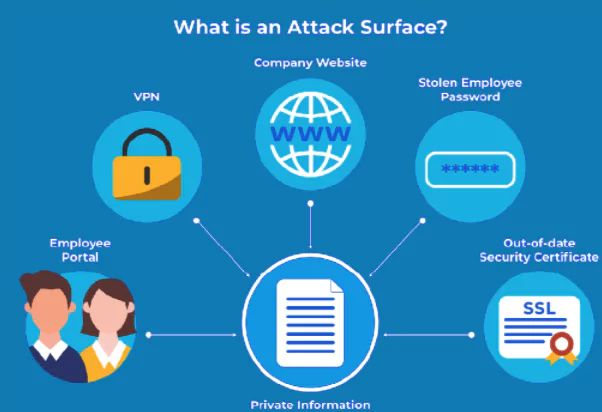
What is an External Attack Surface?
The External Attack Surface, also known as a “Digital Attack Surface”, is the entirety of an organization’s internet-facing assets and associated attack vectors that can be exploited during an attack.
Servers, domain names, SSL certificates, operating systems, IoT devices, security devices, IP blocks are all IT (Information technology) assets of the organization.
These assets may be located on-premises, in the cloud, or from third-party vendors. While organizations often define the “attack surface” very narrowly, threat actors do not view the attack surface in the same way.
Threat actors want to access assets located on-premises, in the cloud, or third parties. Therefore, the best way to protect the organization; to see through the eyes of a threat actor, to see, understand, and manage all the ways that can reach the organization.
How Does External Attack Surface Management Work?
The attack surface cannot be protected until all the assets the attackers are exposed to are visible. Organizations should view attack surfaces as threat actors – adopting an outside-in and an external attack surface management perspective.
External attack surface management refers to the processes and technology required to discover extroverted assets and effectively manage their vulnerabilities. Examples include servers, credentials, and incorrect cloud configuration that can be exploited by attackers.
Threat actors seek the path of least resistance to enter the organization. They examine and test the attack surface almost continuously until they find a path that provides little resistance. Organizations also need to explore the entire IT ecosystem using an external attack surface perspective.
External attack surface management requires organizations to continually discover, assess and prioritize the risk of all attack surfaces and remediate them.
What are the Key Elements for External Attack Surface Management and Protection?
- Digital footprint discovery: The first step for external attack surface management is to identify all of the organization’s assets that are exposed to the internet. Like websites, IPs, domains, SSL certificates, and cloud services. Companies have many assets that they do not know or forget, as well as assets that they know and manage. Any asset that is forgotten or not configured for security poses a risk to companies.
- Asset inventory and classification: It is important to understand exactly which business unit, subsidiary, or third-party vendor each asset disclosed belongs to and how it is networked. Creating an accurately classified inventory is essential for responsible individuals who want quick access to the assets they manage.
- Evaluation: After discovering the assets in your IT ecosystem, it is necessary to evaluate them for risks. Attackers need only one opportunity. These; misconfigured assets, network architecture flaws, data vulnerabilities, authentication and encryption weaknesses, or any other risk, including common vulnerabilities and CVEs. Detect them on the external attack surface using multiple security testing techniques and then correlate the results to identify attack vectors that threat actors can use.
- Prioritization: Risks on the external attack surface must be prioritized. Prioritizing makes it possible to know where to focus first. Without prioritization, it is nearly impossible to manage the volume of security issues and alerts organizations face. The goal is to reduce false positives and increase the productivity of the team. Correcting risks such as misconfigurations, open ports, and unpatched vulnerabilities in an order of urgency, severity, and risk is vital to achieving this goal.
- Continuous security monitoring/Fixing – Needs improvement: The assets of organizations are increasing and being updated day by day. As the digital asset inventory grows, it is difficult to keep track of updated assets. In addition, there are many 3rd party applications running on assets, and security vulnerabilities that can be easily exploited are published in these applications every day. Therefore, it is necessary to ensure 24/7 monitoring of digital assets for newly discovered vulnerabilities and misconfigurations.
Refinement is critical to attack surface protection, so making remediation functional is an essential element of effective external attack surface management.
Often IT operations teams are tasked with improvement. To accelerate remediation workflows, security teams must provide remediation guidance and actionable evidence for each identified risk. This allows operations teams to make corrections with little or no additional research.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































