
Why Do Organizations Need IAM?
Identity and access management (IAM) is a discipline to ensure that the right people and job roles (identities) can access the tools they need in the organization. The enterprises can control employee apps without logging into every app as administrators by identity management and access systems.
Identity and access management systems allow the organization to address a variety of identities, including individuals, software, and hardware like robotics and IoT devices. According to Gartner, by 2024, 30% of large enterprises will newly implement identity-proofing tools to address common weaknesses in workforce identity life cycle processes.
How Does IAM Work?
Identity and access management solutions commonly perform two tasks:
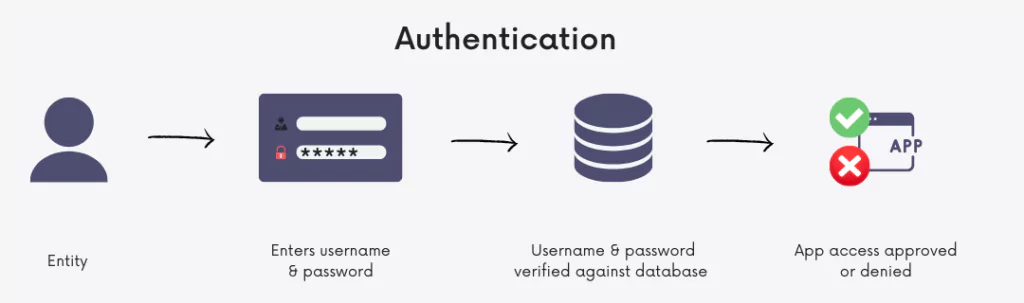
- Firstly, IAM confirms that the user, software, or hardware is who they say they are byauthenticating their credentials against a database.
IAM cloud identity tools are much more secure and flexible than traditional username and password solutions.
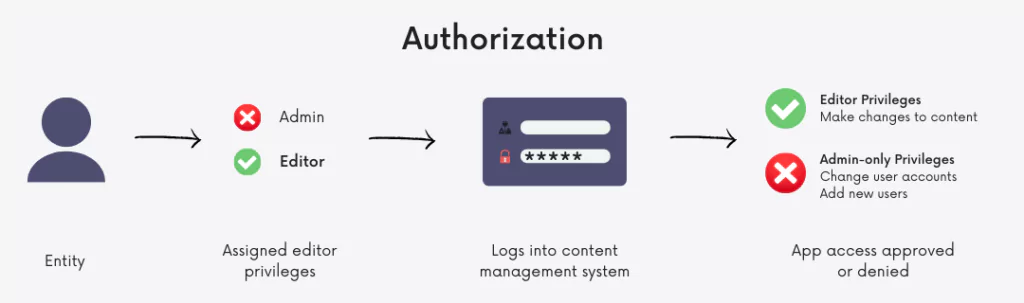
- Secondly, identity and access management systems only allow the appropriate level of access. IAM allows for narrow slices of entry to be portioned out, such as editor, viewer, and commenter in a content management system instead of a username and password allowing access to an entire software suite.
Why Do Organizations Need IAM?
IAM helps organizations to improve online security and increase employee productivity. Traditional security often fails at one point – the password. If a user’s password is breached or, worse, the email address for their password recovers, the organization becomes vulnerable to attacks. IAM services narrow vulnerable points and promote them by catching mistakes when they’re made.
Once an enterprise logs on to their leading IAM portal, their employees no longer have to bother about having the correct password or access level to perform their tasks. Not only does each employee get access to the precise suite of tools for their job, but their access can also be managed as a group or role instead of individually, decreasing the workload on your IT experts.
Threat Intelligence Approach to IAM
Digital transformation and increasing reliance on remote work across various vertical markets are driving the demand for new proactive approaches to IAM. External threat intelligence and digital risk protection capabilities like compromised credentials detection can enhance the existing solutions to prevent Account Takeover (ATO) attacks.
Threat actors usually post the stolen credentials through public data breaches and stealer malware logs for sale. Monitoring these posts across underground markets can be exhausting for security analysts. However, an automated solution like SOCRadar can help automate this process and gain real-time insights.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































