
Is Nginx Zero-Day RCE Vulnerability False Alarm?
On Saturday, April 9, it was announced that there was a zero-day RCE vulnerability for webserver Nginx version 1.18 in the post made from the Twitter account BlueHornet, which is associated with the group AgainstTheWest. The threat actor shared this vulnerability directly with Nginx.
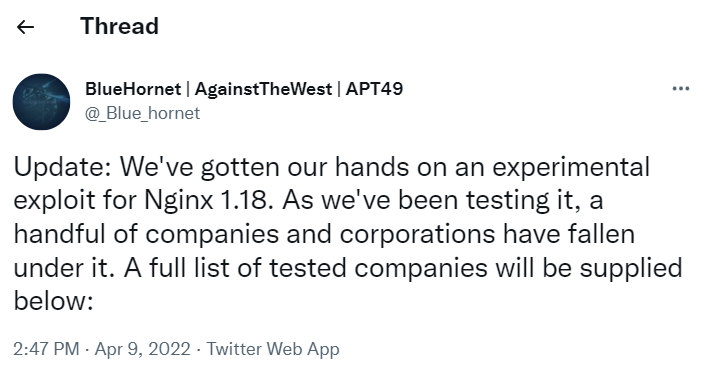
Cybersecurity researchers asked, “Is it the next Spring4Shell?” They focused on the suspicion, and this question occupied the headlines for a while. Later, conversations with the group were shared, and instructions emerged on exploiting the vulnerability.
How is Nginx Vulnerability Exploited?
In the shared conversations, BlueHornet claims that the vulnerability can be implemented in two stages. The threat actor explains that LDAP (Lightweight Directory Access Protocol) injection should be done first. It is not effective if there is an active web application firewall. LDAP has been exploited by attackers for many years.
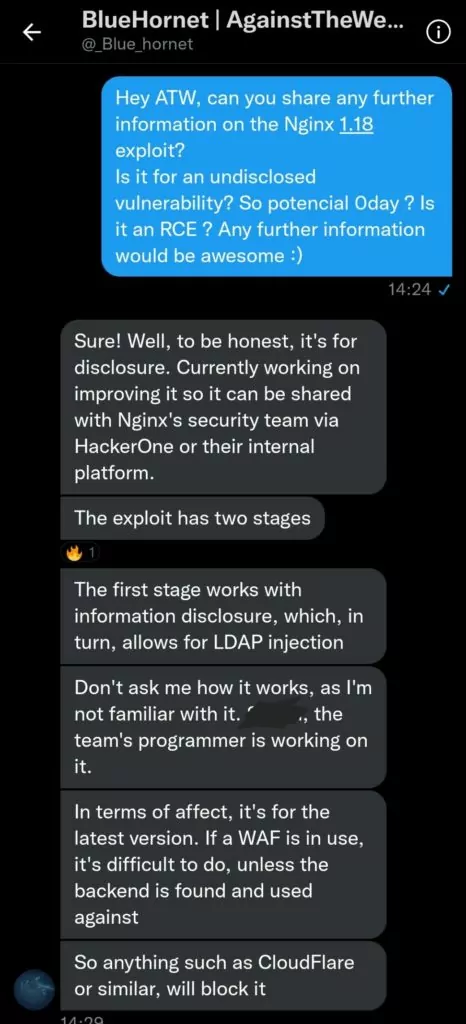
The group AgainstTheWest later shared more detailed information by opening a GitHub repository about the vulnerability, which it claims to be zero-day. Posting updates throughout Saturday and Sunday, the group claimed they had access to Atlassian and Royal Bank of Canada accounts, but no leaks were shared. In light of this information, cyber security experts explained that many conditions must come together for the vulnerability to be exploited and that it is not as critical as it was thought.
Nginx: Only LDAP Reference Implementation Affected
In its security advisory published on Monday, April 11, Nginx stated that Nginx Open Source and Nginx Plus products are not directly affected. No measures are necessary for those who do not use the reference implementation pointed out by the threat actor.
The statement noted that the vulnerability can be exploited under any of the following conditions apply:
- Using command-line parameters to configure a Python daemon
- Having unused optional configuration parameters
- LDAP authentication is tied to specific group memberships
Nginx’s security advice also includes mitigations for each situation.
Who is AgainstTheWest?
Also known as ATW, the group presents itself as hacktivists fighting against China and Russia. AgainstTheWest is known for committing many data breaches, especially those linked to the Chinese government. Among these breaches are public institutions such as the People’s Bank of China, the Ministry of Public Security of China, and China’s Ministry of Science and Technology. The group declared that it supported Ukraine in the Russia-Ukraine cyberwar.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































