
Black Basta Ransomware Victim Knauf Forced to Stop Their Services
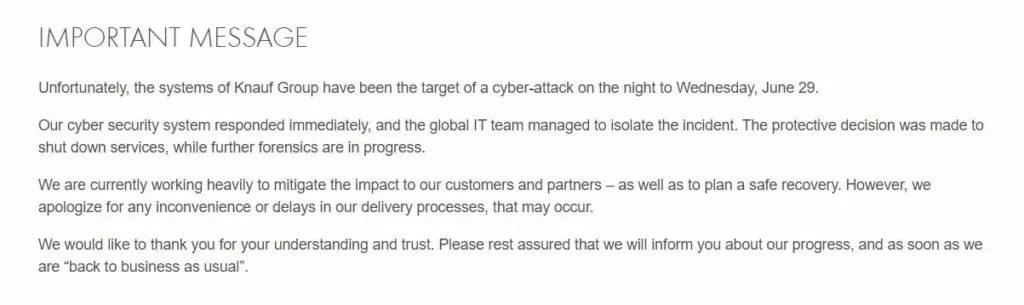
Construction materials manufacturer Knauf announced it was the target of a cyberattack by the Black Basta ransomware. The company declared that some of its operations were interrupted due to the attack, and the IT team closed all IT systems to control the situation.
In the statement published on its website, Knauf announced that the attack took place on the night of June 29 and that they continue to work to mitigate the effects of the attack as soon as possible.
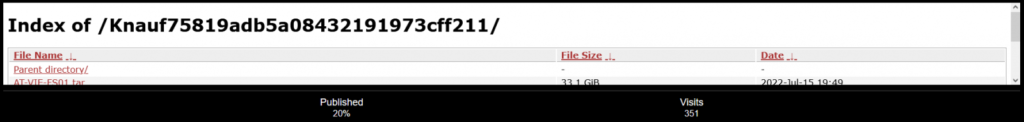
20% of Stolen Knauf Data Made Public
The Black Basta ransomware group added Knauf to its victim list on July 16, then shared 20% of the leaked data. After Knauf’s announcement, the allegations of threat actors became certain. Among the data shared by Black Basta are user information, sensitive data about employees, ID scans, and product documents.
Security researchers detected that the leaked data has been accessed by 400 profiles so far, and Black Basta aims to negotiate ransom using the double extortion technique.
Black Basta Attacks Affected Nearly 50 Organizations
Cybersecurity researchers state that they first spotted the Black Basta ransomware group in April 2022. Studies about threat actors show that victims are selected from organizations operating in different industries in countries such as the US, UK, India, Canada, Australia, New Zealand, and the United Arab Emirates.
Although it has been active for a few months, Black Basta has negatively affected around 50 organizations with its attacks. Thus, threat analysts think that it is rebranded version of Conti.
Black Basta uses the double extortion technique to get ransom from its victims. Attackers steal data before encrypting the victim’s data. They then strengthen their trump by threatening to share this data.
Recent Victims of Black Basta
Black Basta ransomware came to the fore last month with its Linux-based version targeting VMware ESXi servers in addition to Microsoft systems.
They used Qakbot, also known as Qbot, in some attacks to steal data, upload payloads, and move laterally on systems.
Black Basta ransomware can evade detection by installing an object that disables antivirus software such as Windows Defender on compromised domain controllers.
While making a backup is not the definitive solution for data recovery, it is highly recommended for organizations. To avoid such threats, the company’s devices must be protected with the most up-to-date security solutions, and the attack surface must be managed effectively.
Black Basta IoCs
Domain:
aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd[.]onion
MD5:
3f400f30415941348af21d515a2fc6a3
SHA256:
5d2204f3a20e163120f52a2e3595db19890050b2faa96c6cba6b094b0a52b0aa
7883f01096db9bcf090c2317749b6873036c27ba92451b212b8645770e1f0b8a
ae7c868713e1d02b4db60128c651eb1e3f6a33c02544cc4cb57c3aa6c6581b6e
17205c43189c22dfcb278f5cc45c2562f622b0b6280dcd43cc1d3c274095eb90
a54fef5fe2af58f5bd75c3af44f1fba22b721f34406c5963b19c5376ab278cd1
1d040540c3c2ed8f73e04c578e7fb96d0b47d858bbb67e9b39ec2f4674b04250
2967e1d97d32605fc5ace49a10828800fbbefcc1e010f6004a9c88ef3ecdad88
f088e6944b2632bb7c93fa3c7ba1707914c05c00f9491e033f78a709d65d7cff
SHA1:
bd0bf9c987288ca434221d7d81c54a47e913600a
Detection Names:
Avast: (Win32:Malware-gen)
Combo Cleaner: (Gen:Heur.Ransom.REntS.Gen.1)
ESET-NOD32: (Win32/Filecoder.OKW)
Kaspersky: (HEUR:Trojan.Win32.DelShad.gen)
Microsoft: (Trojan:Win32/Sabsik.FL.B!ml)
DrWeb: Trojan.DelShadows.20
BitDefender: Gen:Heur.Ransom.REntS.Gen.1
Malwarebytes: Malware.AI.3879235874
Rising: Ransom.Agent!8.6B7 (CLOUD)
Tencent: Win32.Trojan.Filecoder.Lmay
TrendMicro: TROJ_GEN. R002H09DP22
IPs and URLs
24[.]178[.]196[.]44:2222
37[.]186[.]54[.]185:995
39[.]44[.]144[.]182:995
45[.]63[.]1[.]88:443
46[.]176[.]222[.]241:995
47[.]23[.]89[.]126:995
72[.]12[.]115[.]15:22
72[.]76[.]94[.]52:443
72[.]252[.]157[.]37:995
72[.]252[.]157[.]212:990
73[.]67[.]152[.]122:2222
75[.]99[.]168[.]46:61201
103[.]246[.]242[.]230:443
113[.]89[.]5[.]177:995
148[.]0[.]57[.]82:443
167[.]86[.]165[.]191:443
173[.]174[.]216[.]185:443
180[.]129[.]20[.]53:995
190[.]252[.]242[.]214:443
217[.]128[.]122[.]16:2222
elblogdeloscachanillas[.]com[.]mx/S3sY8RQ10/Ophn[.]png
lalualex[.]com/ApUUBp1ccd/Ophn[.]png
lizety[.]com/mJYvpo2xhx/Ophn[.]png



































