Threat Actors Stole LastPass Source Code Through a Compromised Developer Account
On 25th August, LastPass announced a breach and stated that its source code was stolen, along with some technical information. The incident happened two weeks ago, and the password management company only recently confirmed it.
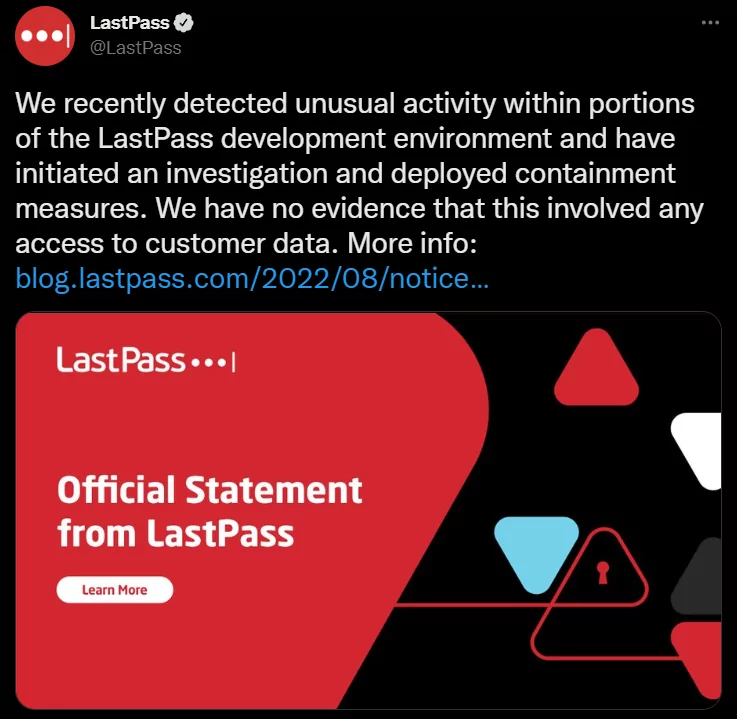
Threat actors used a compromised developer account as an entry point for the attack. There is no proof that customer data or vaults have been compromised during the breach. Passwords are kept in encrypted vaults that are only decrypted with a user’s master password, which the company claimed was unaffected by the breach.
In the advisory, company stated that they “have deployed containment and mitigation measures.”
LastPass Has Been Targeted Before
LastPass has over 80,000 business customers and is a well-known password management service. In the past years, attackers tried various ways to breach the company. In 2021, attackers gained access to a user’s master password through a credential stuffing attack, and in 2015 users were advised to change passwords upon a network breach; there also was a RedLine malware campaign targeted to steal master passwords in 2020.
Additional Words From the CEO
CEO of LastPass, Karim Toubba, added: “We have determined that an unauthorized party gained access to portions of the LastPass development environment through a single compromised developer account and took portions of source code and some proprietary LastPass technical information. Our products and services are operating normally.”.
How to Prevent Risks
Customers do not need to take any specific action, but cybersecurity experts advises using best practices during setup and configuration, which include:
- Set a unique and strong master password. It should not be reused elsewhere.
- Enable multi-factor authentication. It prevents attacks even if the user’s password is stolen.
- Pair new devices with the LastPass account and set up the service’s authenticator app.