
Mirai Variant MooBot Targets RCE Vulnerabilities in D-Link Routers
MooBot botnet is back for new attacks. The variant of the Mirai malware started a new campaign last month to exploit critical vulnerabilities (CVSS 9.8) in D-Link routers.
MooBot was first identified in December 2021, when it exploits a vulnerability in Hikvision cameras to spread across many devices to build itself a DDoS army. The malware has changed targets, now targeting vulnerable D-Link routers.
Which Vulnerabilities Does MooBot Exploit?
MooBot exploits several old and new vulnerabilities to hack into the routers:
CVE-2022-26258 and CVE-2022-28958 are remote code execution vulnerabilities found in D-Link routers. The vulnerabilities are exploited by writing unknown input in place of “value” and “Device Name” in /lan.asp and shareport.php files.
The botnet malware also exploits old vulnerabilities. CVE-2018-6530 exists in soap.cgi and allows a remote attacker to inject commands into OS. CVE-2018-6530 is discovered to exist in a series of configurations within D-link routers. The oldest exploited vulnerability in the MooBot campaign is CVE-2015-2051, which lets an attacker execute arbitrary commands and is exploited through GetDeviceSettings in the HNAP interface.
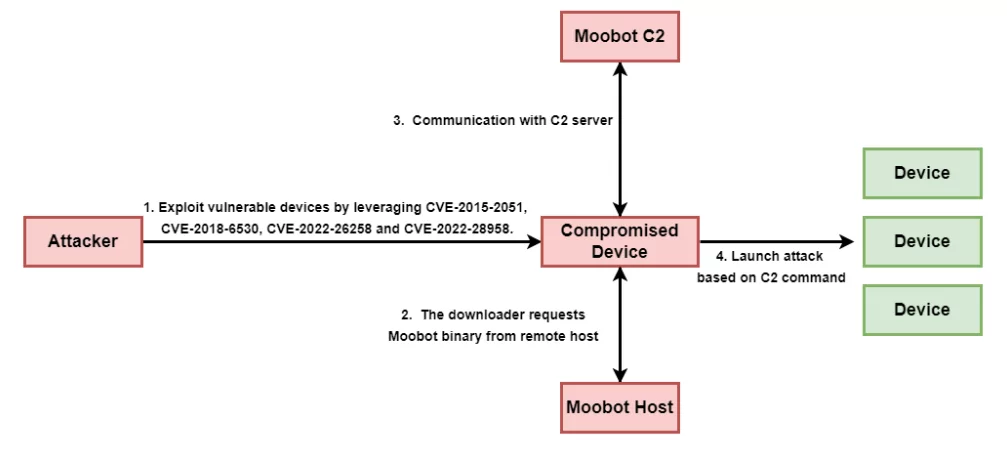
Following the malware’s decoding of the configuration’s hardcoded address, the newly captured routers are registered on the threat actor’s C2 server. The C2 addresses listed in Unit 42’s report and those in Fortinet’s analysis are different, which is significant because it suggests that the threat actor’s infrastructure has been updated.
Depending on the objectives of MooBot’s operators, the captured routers participate in targeted DDoS attacks against different targets.
The power of the botnet is rented to anyone interested in disrupting websites and online services since threat actors typically sell DDoS services to others.
Internet speed drops, slowness, overheated routers, and mysterious DNS configuration changes are indicators of botnet infections and may be experienced by users of hacked D-Link equipment.
Recommendations
The easiest approach to prevent MooBot and other botnet attacks is to update your D-Link router’s firmware whenever an update becomes available.
D-Link has issued security firmware updates to fix the mentioned vulnerabilities.
To block remote access to the admin panel, you should configure any outdated or unsupported hardware you use.
Suppose you believe you may have already been compromised. In that case, you should reset the device using the associated physical button, change your admin password and install the most recent vendor security updates.
MooBot IoCs
C2 Server:
- vpn.komaru[.]today
Malware Host:
- hxxp://159.203.15[.]179/wget[.]sh
- hxxp://159.203.15[.]179/wget[.]sh3
- hxxp://159.203.15[.]179/mips
- hxxp://159.203.15[.]179/mipsel
- hxxp://159.203.15[.]179/arm
- hxxp://159.203.15[.]179/arm5
- hxxp://159.203.15[.]179/arm6
- hxxp://159.203.15[.]179/arm7
- hxxp://159.203.15[.]179/sh4
- hxxp://159.203.15[.]179/arc
- hxxp://159.203.15[.]179/sparc
- hxxp://159.203.15[.]179/x86_64
- hxxp://159.203.15[.]179/i686
- hxxp://159.203.15[.]179/i586
Shell Script Downloader (SHA256):
- rt: B7EE57A42C6A4545AC6D6C29E1075FA1628E1D09B8C1572C848A70112D4C90A1
- wget[.]sh: 46BB6E2F80B6CB96FF7D0F78B3BDBC496B69EB7F22CE15EFCAA275F07CFAE075
Samples (SHA256):
- 36DCAF547C212B6228CA5A45A3F3A778271FBAF8E198EDE305D801BC98893D5A
- 88B858B1411992509B0F2997877402D8BD9E378E4E21EFE024D61E25B29DAA08
- D7564C7E6F606EC3A04BE3AC63FDEF2FDE49D3014776C1FB527C3B2E3086EBAB
- 72153E51EA461452263DBB8F658BDDC8FB82902E538C2F7146C8666192893258
- 7123B2DE979D85615C35FCA99FA40E0B5FBCA25F2C7654B083808653C9E4D616
- CC3E92C52BBCF56CCFFB6F6E2942A676B3103F74397C46A21697B7D9C0448BE6
- 188BCE5483A9BDC618E0EE9F3C961FF5356009572738AB703057857E8477A36B
- 4567979788B37FBED6EEDA02B3C15FAFE3E0A226EE541D7A0027C31FF05578E2
- 06FC99956BD2AFCEEBBCD157C71908F8CE9DDC81A830CBE86A2A3F4FF79DA5F4
- 4BFF052C7FBF3F7AD025D7DBAB8BD985B6CAC79381EB3F8616BEF98FCB01D871
- 3B12ABA8C92A15EF2A917F7C03A5216342E7D2626B025523C62308FC799B0737
You can find all IoCs here.



































