
Highlights from SOCRadar Cyberwatch September Webinar
The first of SOCRadar’s Cyberwatch webinar series took place yesterday. Cyberwatch September, which covers significant cyber incidents, emerging threat actors, the most exploited vulnerabilities, and major cyberattacks worldwide, aims to provide actionable intelligence to cyber security researchers every month and share SOCRadar’s insights with the cyber security community.
This blog will highlight some of the headlines from SOCRadar Cyberwatch September. Follow us on Linkedin to register for our webinars right on time.
Most Q2 Attacks Targeted Old Microsoft Vulnerabilities
Threat actors are always trying new ways to achieve their goals. The method they use most is to exploit a vulnerability. In this way, they can obtain initial access to the system. Although new vulnerabilities or zero-days make organizations’ infrastructures vulnerable, threat actors often choose to leverage unpatched old vulnerabilities as well.
These old vulnerabilities, forgotten over time, are unfortunately only remembered when an attack scenario occurs. In this sense, it may be important to highlight that attackers most exploited old Microsoft vulnerabilities in the second quarter of 2022.
In the table below, you can see the four most commonly used vulnerabilities in attacks.
|
Vulnerability |
Attacked users in Q2 2022 |
Dynamics of attacked users, % Q2 2022 vs Q1 2022 |
|
4,886 |
696% |
|
|
60,132 |
59% |
|
|
140,623 |
5% |
|
|
345,827 |
3% |
How to Mitigate?
- Provide your SOC team access to the latest threat intelligence (TI) that helps detect and prevent attacks early – before the attackers can achieve their goals.
- Receive relevant and up-to-date information on threats to be aware of and the TTPs used by attackers
- Use a security solution that provides vulnerability management components. This component monitors suspicious actions of applications and blocks the execution of malicious files.
- Use Endpoint Detection and Response (EDR) solutions.
Phishing Landscape
Threat actors exploit many of the vulnerabilities mentioned above through phishing campaigns. That’s why we’ve dedicated the next topic to Cyberwatch September on phishing.
Looking deeply into the phishing campaigns in the first quarter of 2022, it is striking that attackers continue using social engineering techniques such as vhishing to deceive their victims. We see that phishing methods such as voice phone calls, mail spoofing, and typosquatting are used in a hybrid way.
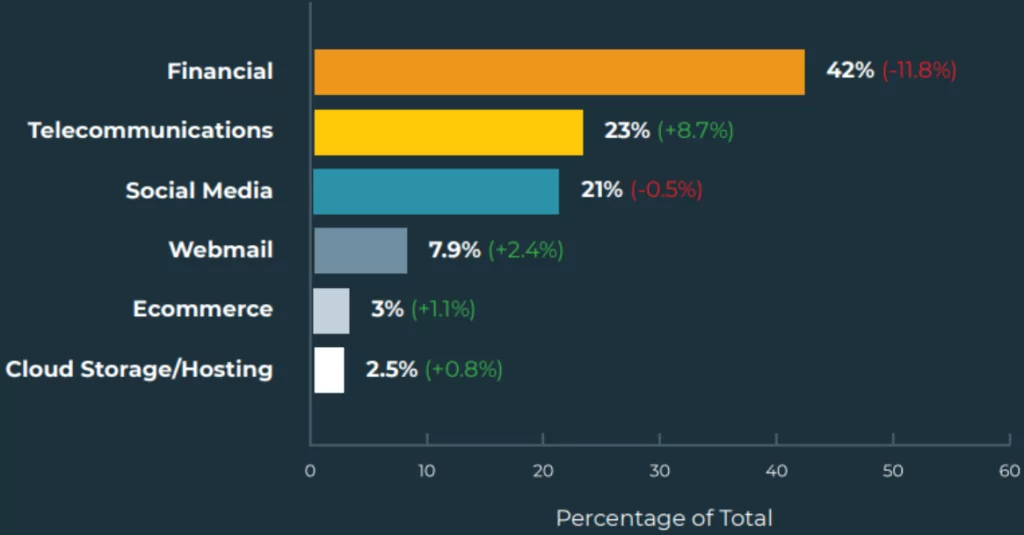
Financial services remained the primary target of threat actors in Q2 2022, as they always have been, albeit with a reduction in attacks. What comes as a surprise is that the telecommunications industry is in second place in a significant way.
Follow our Cyberwatch Webinar Series to learn more about cyber incidents and stay up to date with what’s happening on the dark web!
See you in October!


































