
Threat Actors Exploit Atlassian Confluence RCE Flaw to Install Crypto Miners
Unpatched Atlassian Confluence Server instances are vulnerable to a critical RCE flaw. The flaw, tracked as CVE-2022-26134 (CVSS score: 9.8), is actively exploited by hackers for crypto mining purposes.
The vulnerability, once exploited, could result in various attack scenarios, such as code injection, complete domain takeover, data theft, and the distribution of remote access trojans (RAT) or ransomware.
Operations Carried Out by Shell Script
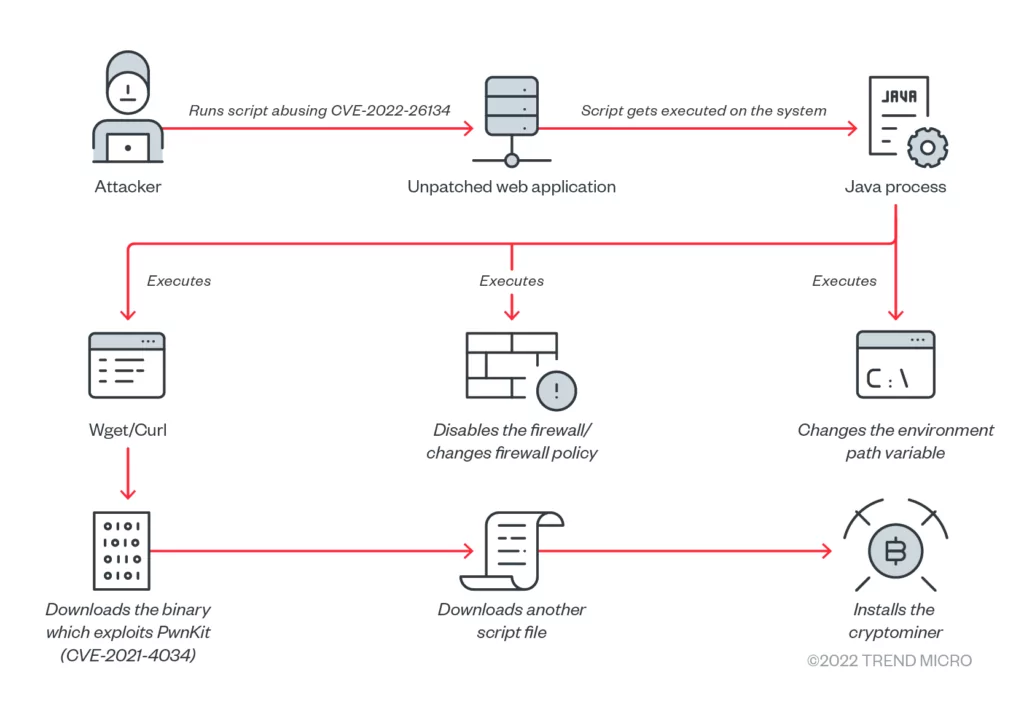
When the target PC executes the exploit payload, the malware downloads the ro.sh/ap.sh shell script file. The following list of actions is performed by this shell script:
- The /tmp and /dev/shm paths are added to the path variable by the script.
- From the C&C server, the script downloads and installs its own curl binary file.
- It flushes all firewall rules and disables iptables or switches the firewall policy action to ACCEPT.
- The script downloads the ap.sh shell script for the following steps, while the binary file ko exploits the PwnKit flaw to escalate the privilege to the root user.
- The ap.sh script downloads the hezb miner malware, ends several processes belonging to rival coin miners, disables cloud service provider agents, and moves laterally.
The ap.sh script checks to see if the active process has hezb. If it cannot be located, the script downloads the binary file for the system architecture (such as sys.x86_64), renames it to “hezb,” and then uses port 4545 to connect to its C&C server, which is located at 106[.]252[.]252[.]226.
The discoveries are consistent with similar exploitation attempts that Lacework, Microsoft, Sophos, and Akamai announced in June.

Recommendations
Numerous businesses have been identified as being actively exploited by CVE-2022-26134. Over 75,000 clients utilize Confluence’s collaboration tool for business and work operations, which suggests that if their systems are not fixed, many different industries could be exposed to attacks.
In June, Atlassian released a security advisory that detailed fixes and mitigation methods for the Confluence vulnerability.
Atlassian advises patching the vulnerability as soon as possible to prevent future attacks.
IoCs
URLs:
- hxxp://202.28.229.174/ap[.]txt
- hxxp://202.28.229.174/kthmimu[.]txt
- hxxp://202.28.229.174/sys[.]x86_64
- hxxp://202.28.229.174/ko
- hxxp://202.28.229.174/ldr[.]sh
- hxxp://202.28.229.174/ap[.]sh
- hxxp://202.28.229[.]174/curl
- hxxp://202.28.229[.]174/kik
SHA256:
- aaa4aaa14e351350fccbda72d442995a65bd1bb8281d97d1153401e31365a3
- 4dcae1bddfc3e2cb98eae84e86fb58ec14ea6ef00778ac5974c4ec526d3da31f
- F13e48658426307d9d1434b50fa0493f566ed1f31d6e88bb4ac2ae12ec31ef1f
IPs:
- 202.28.229.174
- 199.247.0.216
- 106.251.252.226:4545
TTPs
|
ID |
Technique |
|
T1190 |
Exploit Public-Facing Application |
|
T1574.007 |
Hijack Execution Flow: Path Interception by PATH Environment Variable |
|
T1222.002 |
File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification |
|
T1564.001 |
Hide Artifacts: Hidden Files and Directories |
|
T1518 |
Software Discovery |
|
T1562.004 |
Impair Defenses: Disable or Modify System Firewall |
|
T1070.004 |
Indicator Removal on Host: File Deletion |
|
T1053.003 |
Scheduled Task/Job: Cron |
|
T1496 |
Resource Hijacking |
|
T1082 |
System Information Discovery |
|
T1018 |
Remote System Discovery |
|
T1021.004 |
Remote Services: SSH |


































