
What Do You Need To Know About Atlassian Confluence RCE Vulnerability?
After it was disclosed that the RCE vulnerability with the code CVE-2022-26134, which affects Atlassian Confluence and Data Center servers, was exploited by multiple threat actors, detailed analyzes of the exploit continue to be published.
First, when the vulnerability shared by Veloxity is successfully exploited, it can allow attackers to RCE, create new admin accounts, and take over the server.
Atlassian announced that it had released patches for the affected versions with the vulnerability shared publicly. In this article, we compiled the Atlassian Confluence vulnerability questions.
1. How Does Confluence Vulnerability Work?

The Atlassian Confluence vulnerability can be exploited through OGNL injection, which enables the evaluation of a widely used framework (Apache Struts) for web-based Java projects. Thus, unauthenticated attackers can RCE. According to Veloxity’s analysis, threat actors could exploit this vulnerability to make web requests on the Confluence server system and take control of the entire system.
According to the analysis, a malicious actor initiates a single exploit attempt on Confluence server systems and loads a file into memory. Thus, it ensures that it has a web shell that it can interact with through requests it sends later.
The attack allows threat actors to re-exploit and executes commands without the need for a backdoor.
2. Which Products Affected by This Vulnerability?
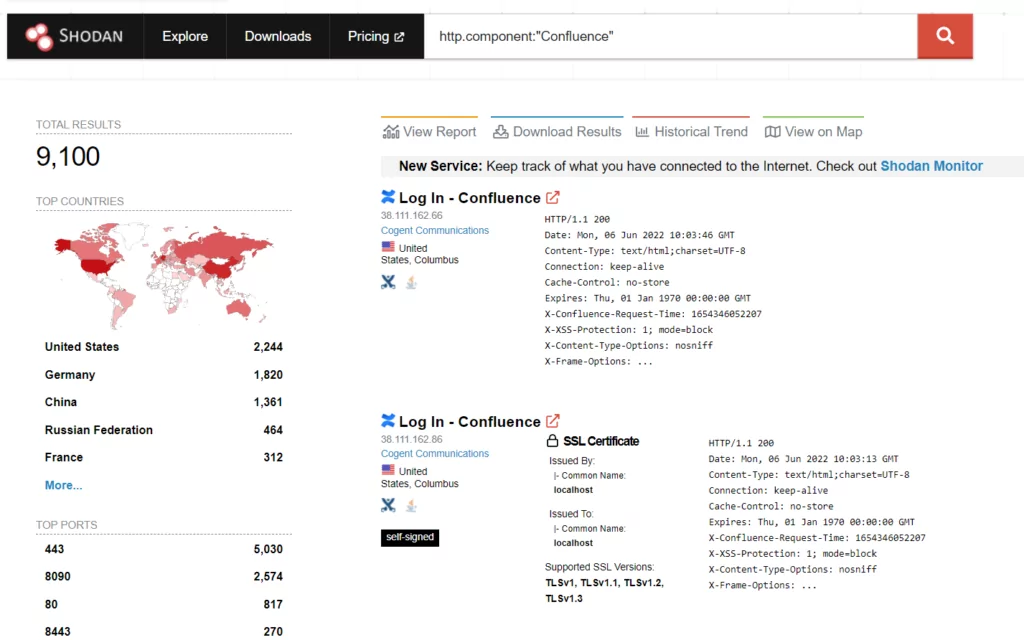
According to Atlassian’s security advisory, the vulnerability affects all Confluence Server and Data Center versions after version 1.3.0. This indicates that all products currently in use are vulnerable to CVE-2022-26134.
The affected versions are:
- 7.4.0
- 7.4.16
- 7.13.0
- 713.6
- 7.14.0
- 7.14.2
- 7.15.0
- 7.15.1
- 7.16.0
- 7.16.3
- 7.17.0
- 7.17.3
- 7.18.0
3. How Big Are the Potential Impacts of the Vulnerability?
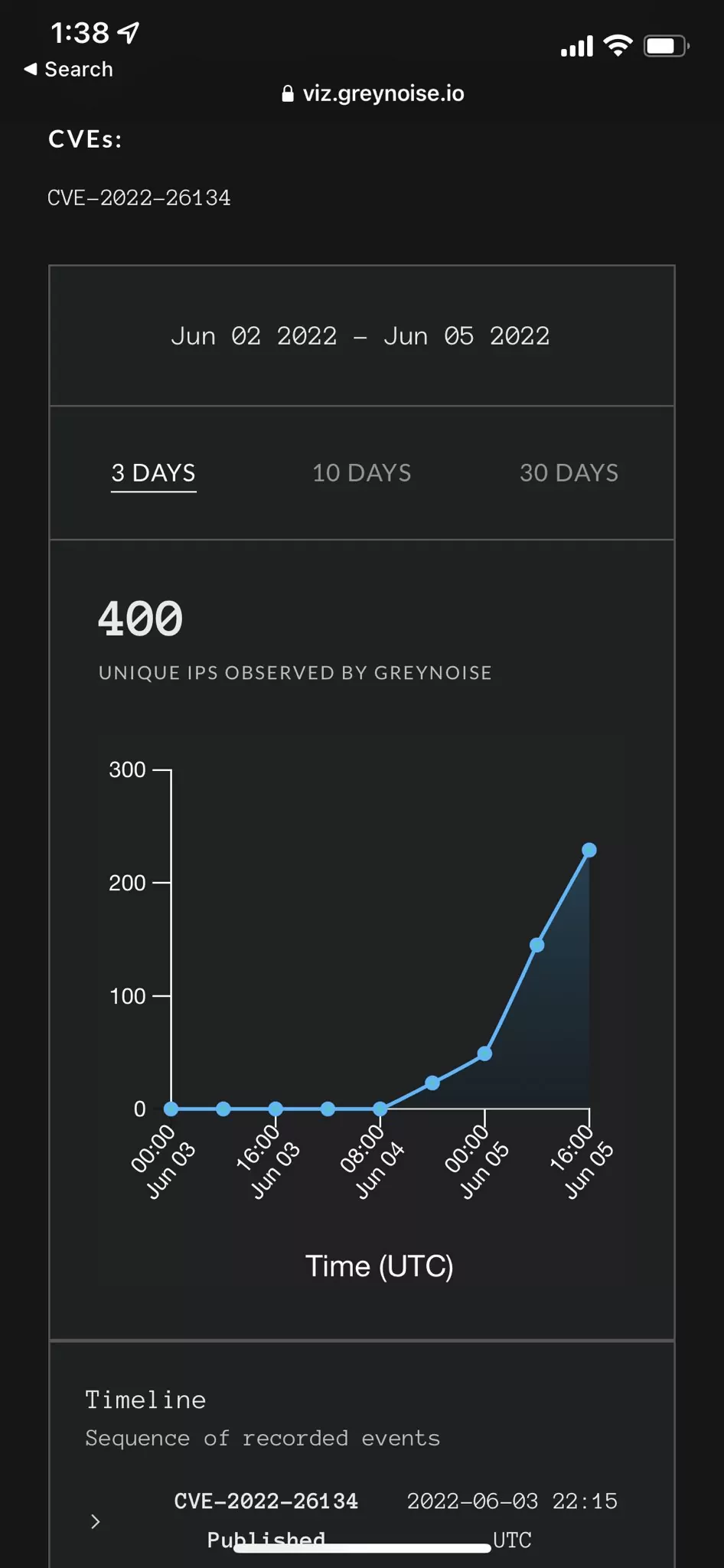
According to GreyNoise’s Andrew Morris tweets, there has been a noticeable increase in exploit attempts since the release of the PoC. In just 24 hours, the number of unique IPs interacting with or attempting to exploit the exploit increased from 28 to 400.
The dramatic increase in IP addresses raises concerns that the scope of the vulnerability may boost.
4. How to Protect? Are There Any Mitigations or Patches?
It is recommended that the official patches released to protect against the vulnerability be applied urgently. In the security advisory published by Atlassian, it is stated that there are updates covering versions 7.4.17, 7.13.7, 7.14.4, 7.15.2, 7.16.4, 7.17.4, and 7.18.1.
The same security advice also recommends mitigations for users who cannot apply patches. It’s worth noting that the mitigations only apply to Confluence versions 7.0.0 – 7.14.2 and 7.15.0 – 7.18.0.
5. How to Exploit the Confluence Vulnerability? Is There Any Example of Exploit?
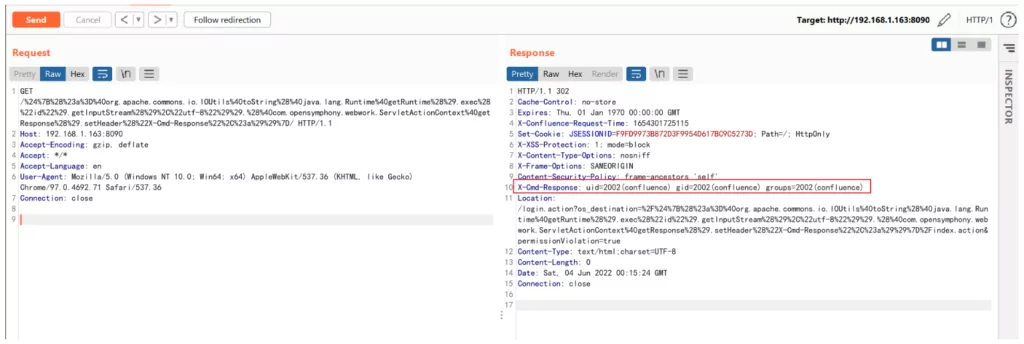
The PoC is also available to independent cybersecurity researchers about the vulnerability in Atlassian Confluence. Shared on GitHub, the exploit shows how simply leveraged the vulnerability.
Researchers underline that exploitation can be carried out in just a few steps.
- Start Confluence Server 7.13.6, it is necessary to execute the command “docker-compose up -d,”
- After starting the environment, visit “http://your-ip:8090” to load the trial installation.
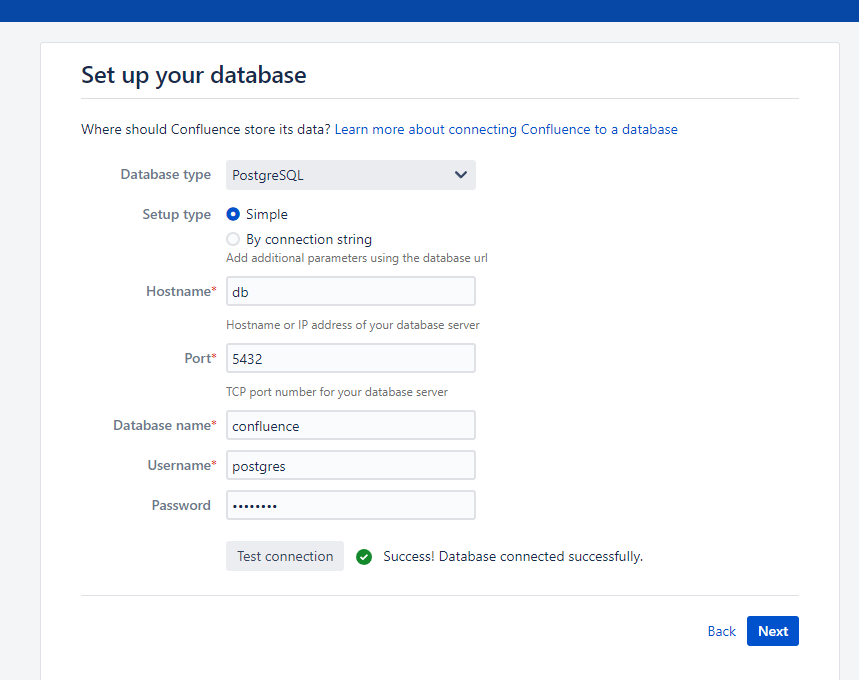
- After obtaining the Atlassian Confluence Server test certificate, it is enough to configure the database and receive the response by sending a request.
Analysis of vulnerability CVE-2022-26134 has shown the following activities:
- Code execution and creation of child processes that invoke different shells
- Overwriting of Confluence Server resources to incorporate webshell. (This file in particular: confluence root>/confluence/noop.jsp)
- Deployment of other webshells (to ensure persistence) including JSP China Chopper.
- Deployment of “Behinder” to have a memory resident webshell.
6. Are There Any IoCs that the SOC Teams Can Use?
IoCs
The following IP addresses are also indicators, used by the attacker to interact with webshell:

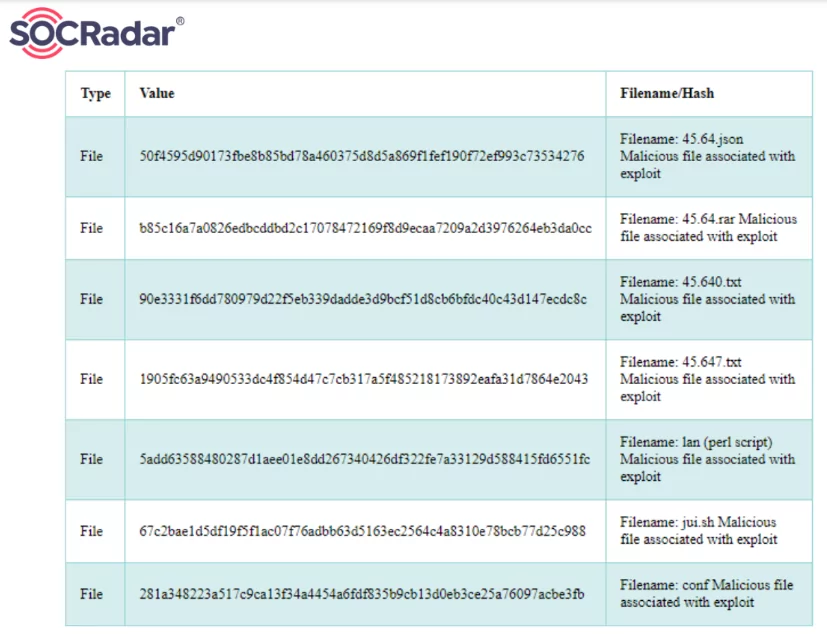
YARA Rules:
You can access the YARA rules shared by Volexity here.
How SOCRadar Can Help With Atlassian Confluence and Data Center Vulnerability
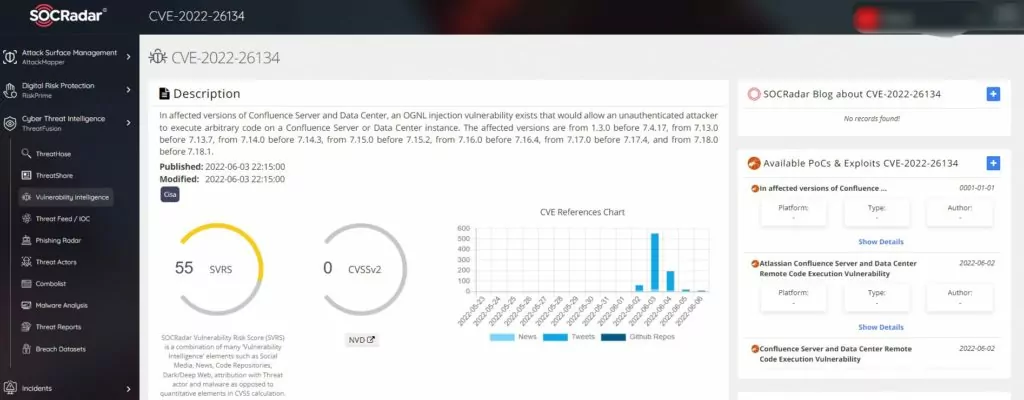
With SOCRadar’s ThreatHose module, you can view conversations about this vulnerability on the surface, deep and dark web, and if a list of vulnerable servers is shared, you can view them. You can also view the status of your Confluence servers with AttackMapper.
SOCRadar will automatically notify you if any of your servers are vulnerable.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.




































