
Python Flaw Unfixed for 15 Years: 350,000 Projects Deemed Vulnerable
A flaw in the Python tarfile module has gone unfixed for 15 years. 350,000 open-source projects are considered vulnerable.
The flaw is tracked as CVE-2007-4559; it is a directory traversal vulnerability that allows to read and write tar archives. The vulnerability was reported by Tomas Hoger in 2007.
The vulnerability exists in tarfile.extract() and tarfile.extractall() functions used by the Python tarfile package.
If the victim untars a malicious tar archive using tarfile, the flaw could enable overwriting and hijacking files on their machine. The module’s maintainer, Gustäbel, had explained how the vulnerability could affect.

Fix Attempt for the Python Module
Gustäbel added a true-by-default check_paths parameter to the TarFile.extractall() method to alert if the tar archive’s path cannot be trusted, and warned against extracting archives from untrusted sources.
However, the risk of arbitrary path traversal remains for both extract() and extractall().
How Is It Exploited?
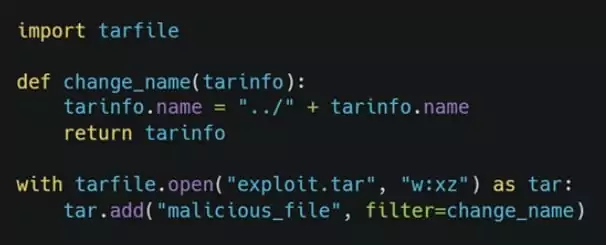
The tarfile module’s extraction functions are vulnerable to a path traversal attack that lets an attacker alter arbitrary files by appending the ‘..’ sequence to filenames in a tar archive.
The “..” sequence switches to the parent directory from the current working path.
Therefore, it is possible to instruct the tarfile module to read and edit a file’s information before adding it to the tar archive using a similar code.
Ongoing Patching Process
Kasimir Schulz, a vulnerability researcher, claims that Trellix created the free Creosote tool to check for CVE-2007-4559.
AWS, Facebook, Google, Intel, and other companies have frameworks including tarfile by default. It is also used in applications for machine learning, automation, and Docker containers.
In a blog post, Charles McFarland, a vulnerability researcher with Trellix, wrote, “Using our tools, we currently have patches for 11,005 repositories, ready for pull requests.” “Each patch will be added to a forked repository and a pull request made over time. This will help individuals and organizations become aware of the problem and give them a one-click fix.”
It is predicted that this process will continue over the coming weeks because of the size of the affected projects. By the time this is finished, around 70K projects, or 12.06% of all vulnerable projects, would have been affected.



































