
Sensitive Data of 65,000+ Entities in 111 Countries Leaked due to a Single Misconfigured Data Bucket
SOCRadar has detected that sensitive data of 65,000 entities became public because of a misconfigured server. The leak includes Proof-of-Execution (PoE) and Statement of Work (SoW) documents, user information, product orders/offers, project details, PII (Personally Identifiable Information) data, and documents that may reveal intellectual property.
SOCRadar’s built-in Cloud Security Module monitors public buckets to detect any information exposure of customer data. Among many discovered public buckets, six large ones contained information for more than 150,000 companies in 123 different countries. The leaks are collectively dubbed BlueBleed by SOCRadar to better track the intelligence around it. While this article covers the largest one of the BlueBleed leaks (BlueBleed Part I), we will publish our analysis for other buckets owned by different organizations as we complete our investigation on them.
Read our second blog post about BlueBleed to learn more about this leak.
“BlueBleed leaks include critical data such as project details, signed customer documents, and customer emails. The exposed data, if parsed properly, enable threat actors to create elaborate attacks against the companies at risk of BlueBleed. Even though most of the data consists of RAW files of databases, the threat actors certainly have enough resources to parse and process the data. To level the playfield, companies need consolidated cybersecurity solutions, such as SOCRadar, that combine attack surface management, digital risk protection services, and cyber threat intelligence.“
Huzeyfe Onal | CEO and Co-Founder
SOCRadar
What is BlueBleed?
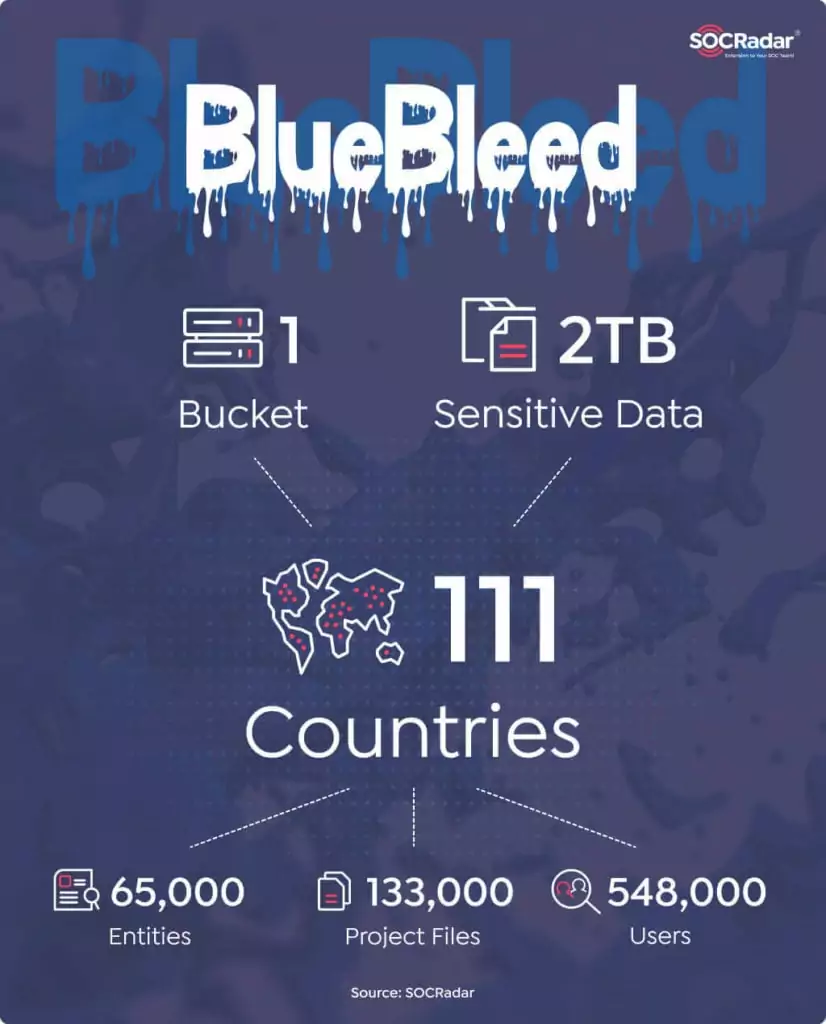
The term “BlueBleed” was coined by Can Yoleri, a Threat and Vulnerability Researcher at SOCRadar, referring to the sensitive information leaked by six misconfigured buckets collectively. The first part of the collection is due to a misconfigured Azure Blob Storage. It can be considered one of the most significant B2B leaks, affecting more than 65,000 entities in 111 countries with sensitive data inside a single Bucket.
“Surely this is not the first time a misconfigured server has exposed sensitive information, and it will not be the last. However, with vital leaked data belonging to tens of thousands of entities, BlueBleed is one of the largest B2B leaks in recent years.“
Can Yoleri | Vulnerability and Threat Researcher – Primary Investigator of BlueBleed
SOCRadar
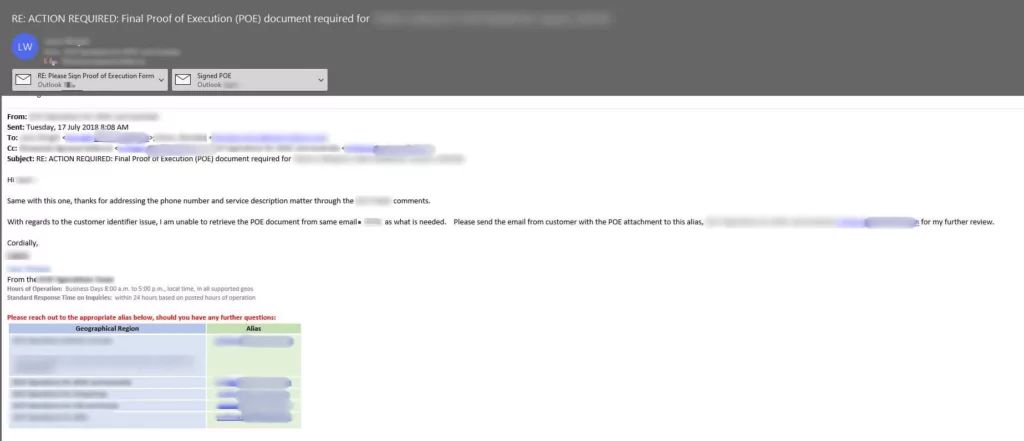
Threat actors who may have accessed the bucket may use this information in different forms for extortion, blackmailing, creating social engineering tactics with the help of exposed information, or simply selling the information to the highest bidder on the dark web and Telegram channels.
How did SOCRadar Discover BlueBleed Part I?
SOCRadar, an Extended Threat Intelligence platform, continuously monitors the surface web, deep web, and darknet for vulnerabilities and data leaks. BlueBleed Part I is discovered as the result of such monitoring. On September 24, 2022, SOCRadar’s built-in Cloud Security Module detected a misconfigured Azure Blob Storage maintained by Microsoft containing sensitive data from a high-profile cloud provider.
“SOCRadar Cloud Security Module constantly scans applications (Bucket, Storage, Apps …) to discover possible misconfigurations and security vulnerabilities in all environments open to the Internet, including all cloud environments. In case of detecting a publicly available bucket that contains confidential or sensitive data, SOCRadar sends alarms to the owner to take necessary precautions. SOCRadar’s in-house developed algorithms and AI/ML enable the platform to detect sensitive data after analyzing the scanned resources. For SOCRadar customers, an alert is automatically created and sent for the Incident Management process to launch.”
Ahmet Kurukose | CTO and Co-Founder
SOCRadar
After the initial detection, SOCRadar researchers investigated a storage area in the bucket where SQLServer backups are stored. Further investigations on the backups led SOCRadar researchers to discover links between the misconfigured bucket and other Azure Blob Storages. A thorough investigation revealed that the sensitive data of tens of thousands of companies was exposed to the public due to this misconfiguration. The amount and scale of the leaked data make it the most significant B2B data leak in the recent history of cybersecurity.
SOCRadar Security Team informed the bucket’s owner, Microsoft, about the leak and notified SOCRadar customers affected by the leak. Microsoft rapidly responded to the SOCRadar’s alerts and reconfigured the bucket to make it private within several hours. Microsoft and SOCRadar collaborated on investigating the leak and successfully mitigated the risk of exposure. The bucket is no longer publicly accessible.
SOCRadar provides a free service where companies can search their company names to see if they are impacted by any of the BlueBleed leaks.
SOCRadar Free Edition can help you find out if your data has been exposed in Bluebleed or other cyberattacks in seconds. Click on the link below and register for SOCRadar Free Edition!
What is the Content of BlueBleed Part I?
As a result of our investigations on the misconfigured server, SQLServer databases, and other files, SOCRadar researchers discovered publicly available 2.4 TB of data containing sensitive information belonging to Microsoft. The exposed data include files dated from 2017 to August 2022.
According to our analysis, the leak, dubbed BlueBleed Part I, consists of critical data belonging to more than 65,000 companies from 111 countries. SOCRadar researchers have discovered more than 335,000 emails, 133,000 projects, and 548,000 exposed users within the leaks so far.
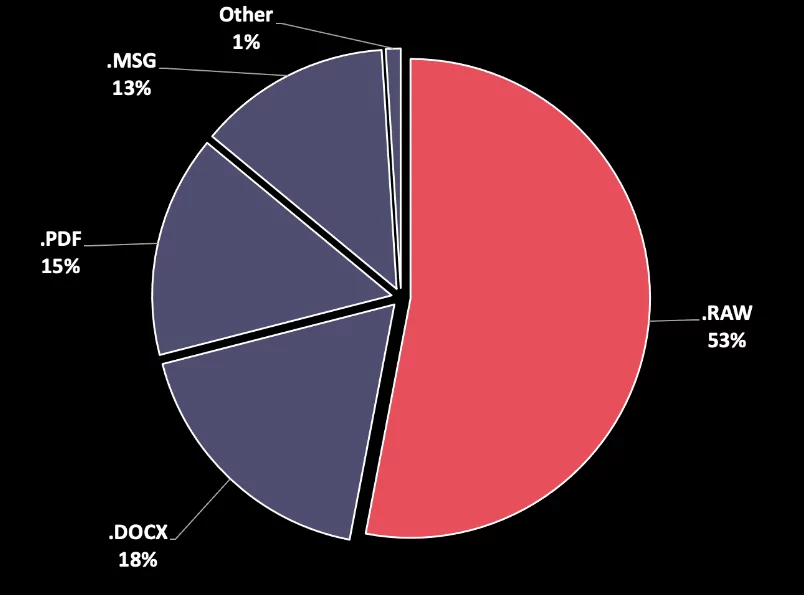
The exposed files in the misconfigured bucket include;
- POE documents,
- SOW documents,
- Invoices,
- Product orders,
- Product offers,
- Project details,
- Signed customer documents,
- POC (Proof of Concept) works,
- Customer emails (as well as .EML files),
- Customer product price list and customer stocks,
- Internal comments for customers (High risk etc.),
- Sales strategies,
- Customer asset documents, and
- Partner ecosystem details.
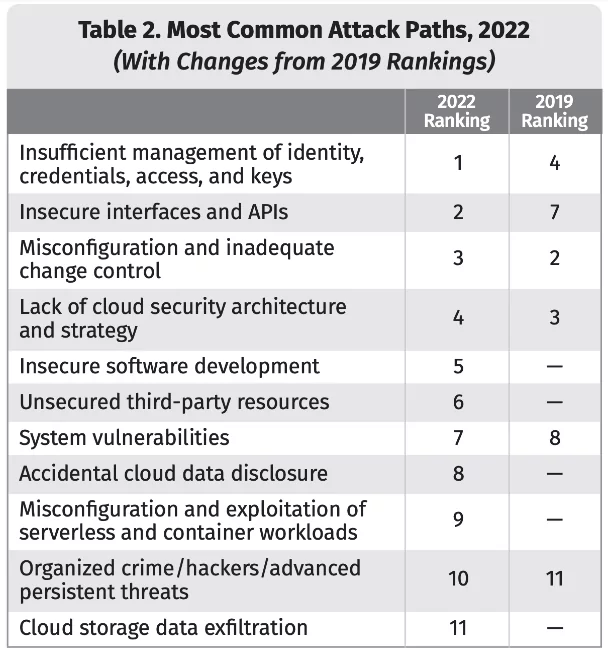
How to Prevent Data Leaks due to Misconfigured Servers?
Misconfigured servers are one of the top reasons for data leaks. According to the SANS 2022 Top New Attacks and Threat Report, cloud storage data exfiltration has become one of the most common attack paths in 2022.
Threat actors constantly scan public storage buckets for sensitive data. They have the resources and means to automate the scanning with advanced tools. Companies should proactively monitor such cyber risks with automated security tools.
- Map out your attack surface to easily manage and control external-facing endpoints.
- Apply your shared responsibility model
- Bring identity and access solutions to all your environments
- A shared access signature token should be used for providing controlled and timed access to your blob containers.
- Encrypt your data at rest
- Enforce accepted cloud security policies – Zero Trust approach
- Fortify your endpoints to prevent breaches.
- Monitor your attack surface to detect any external assets open to the public, which may contain sensitive data about your company and your customers.
“Companies must monitor their external facing assets and bucket configurations with automated tools such as Attack Surface Management (ASM) solutions. ASM solutions will notify companies when a configuration setting has changed to public. However, monitoring the attacks surface for a company is insufficient to prevent incidents like BlueBleed, considering the misconfigured bucket belongs to a cloud service provider. Thus, it should be backed up with cyber threat intelligence (CTI) solutions to be alerted in case of data leaks due to misconfigured servers. Solutions that combine ASM and CTI, such as SOCRadar, can consolidate the efforts to prevent such incidents.”
Ensar Seker | CISO
SOCRadar
How Can SOCRadar Help?
When a data leak occurs due to a third-party provider, advanced threat intelligence solutions enable companies to understand and be alerted if their information is exposed due to services taken from the third-party provider. SOCRadar offers big threat-share data search with its Free Edition, where users can search, in a secure environment, digital assets (IP addresses, domains, etc.), hashes, or any keyword mentioned in the dark web and darknet websites without any subscription or providing personal data.

SOCRadar’s Threat Hunting module enables users to
- Get up-to-date data feeds about data leaks, cybersecurity news, IoC/feed data, and deep web information.
- Search for assets (domain, IP address), suspicious IP address, or a domain used by a specific threat actor, information in the IRC, Telegram, Discord, and ICQ channels used by adversaries,
- Execute threat hunting on a common threat-share platform,
- Get trends about threat actors such as APT (Advanced Persistent Threat) groups and their tactics, techniques, and procedures (TTPs) that can be used with the MITRE ATT&CK framework.
- Integrate threat intelligence with SOAR (Security Orchestration, Automation, and Response), firewall, SIEM (Security Information and Event Management), and EDR (Endpoint Detection and Response).
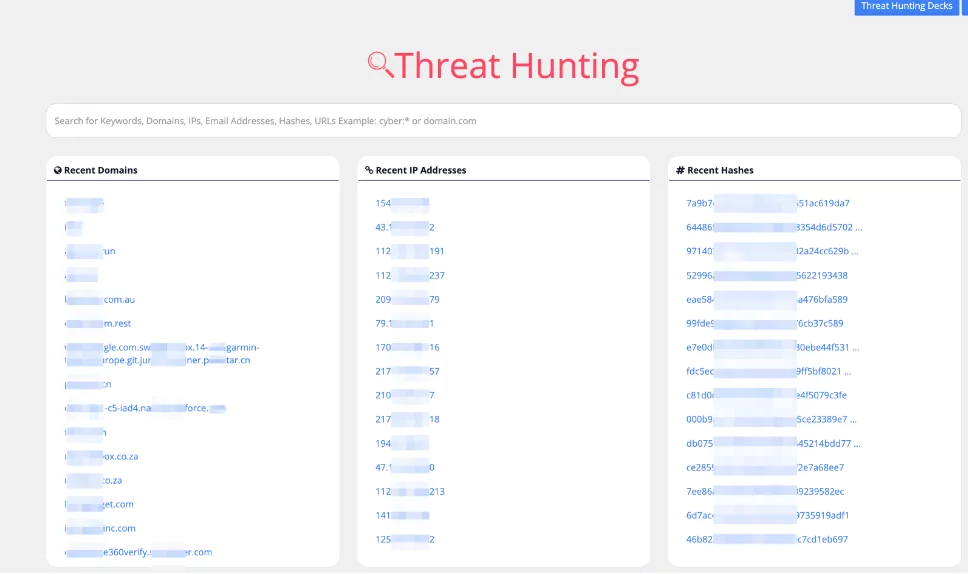
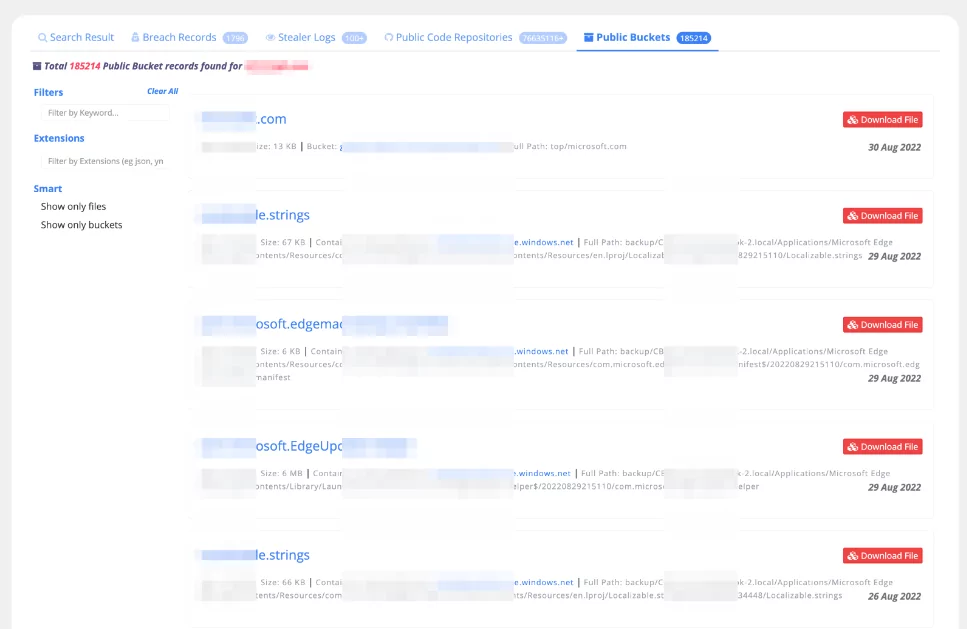
SOCRadar Free Edition has many more modules like Threat Hunting that helps your organization to strengthen Cyber Threat Intelligence abilities. Even in the free edition, you can find many features that will guide you on strategic, tactical, and technical topics. Click here to register for SOCRadar Free Edition!
Please reach us at bluebleed@socradar.io to receive more information about BlueBleed leaks.



































