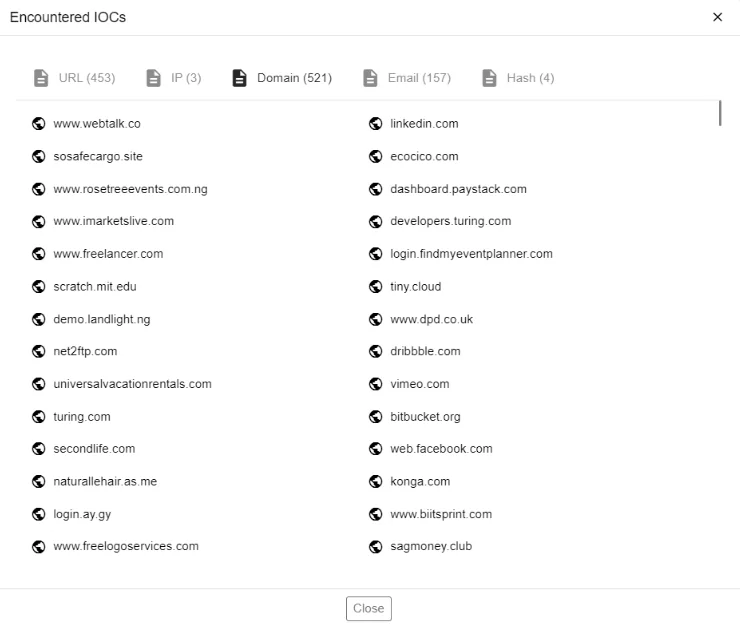
Newly Unsealed Indictment Charges the Operator of Raccoon Infostealer
On Tuesday, October 25th, 2022, a federal grand jury indictment charges a Ukrainian national, Mark Sokolovsky, 26, also known as Photix, raccoonstealer, and black21jack77777, for his role in operating an international malware operation known as Raccoon Infostealer.
Mark Sokolovsky, presently detained in the Netherlands after the United States requested his extradition, has been charged with stealing sensitive data, including emails, passwords, and financial data, from more than 2 million people worldwide.
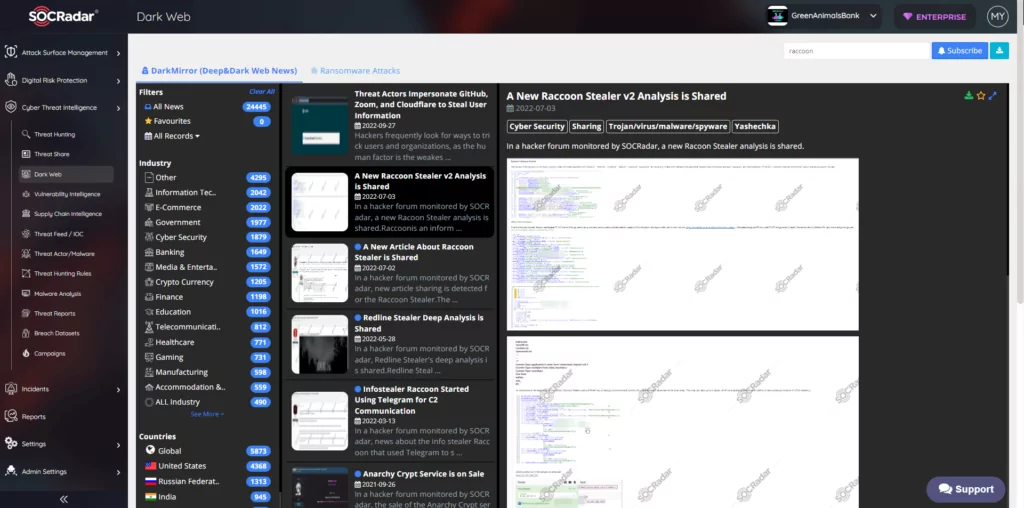
(Source: SOCRadar)
Raccoon Infostealer worked as a malware-as-a-service or “MaaS.” For about $200 per month in cryptocurrency, users who deployed Raccoon Infostealer to steal data from victims rented access to the infostealer malware. These individuals installed the malware on the devices of unwary victims using a variety of tricks, including email phishing. Then, Raccoon Infostealer would steal log-in information, financial data, and other private information from victims` computers. Stolen data was sold to other people on cybercrime forums or used to commit financial crimes.
Capabilities of Raccoon Infostealer
Cybersecurity researchers first observed the Raccoon Infostealer in the wild in April 2019. Since then, it has been capable of stealing private information from almost 60 programs, including 29 different Chromium-based browsers, Mozilla-based programs, and cryptocurrency wallets from Exodus and Jaxx. The malware may also take screenshots because it is written in C++. Raccoon uninstalls and removes any traces of itself after stealing all the relevant data from an infected PC. Raccoon Infostealer, also known as “Racealer,” was popular because of its low price (USD$75 per week and $200 per month) and its rich features. While the malware lacked sophistication, it had many methods and features for stealing data from popular browsers, email clients, and cryptocurrency wallets. Raccoon Infostealer was mainly delivered using either exploit kits or phishing campaigns.
What Should You Do?
The FBI estimates that this malware took more than 50 million different private data items from millions of victims worldwide. After Dutch police arrested Sokolovsky in March 2022, the current version of Raccoon Infostealer was taken offline by the FBI with the help of law enforcement in Italy and the Netherlands. These numbers might increase as the US continues the investigation because the FBI doesn’t think it has all the stolen data.
A website, raccoon.ic3.gov, developed by the FBI, can be used to find out if you have been a victim of Raccoon Infostealer. You can visit the website to determine if your email address is connected to any of the data now held by the United States. FBI’s Internet Crime Report Center (IC3) encourages victims to file a thorough complaint and describe any harm incurred due to their information being stolen. You can use this page to complete a complaint form: Internet Crime Complaint Center(IC3) | File a Complaint.
You can find the announcement from the United States Department of Justice at this link: https://www.justice.gov/usao-wdtx/pr/newly-unsealed-indictment-charges-ukrainian-national-international-cybercrime-operation
Protection & Prevention Tips
- Use a powerful anti-malware program to protect your systems against malware infections.
- Activate your browser’s pop-up blocker against threats from malvertising.
- Do not download free software from untrusted sources.
- Always keep your operating system and other critical software up to date.
- Prevent the loss of your important data by making regular backups.
- Be wary of emails from an unknown or unreliable sender, and do not open attachments.
- Use the most up-to-date anti-virus software on all your devices.
How can SOCRadar Help?
On top of providing you with a live list of your assets and another live list of vulnerabilities and zero-days on these assets, SOCRadar brings you related dark web intelligence about you and your domain. You can learn about the latest version of Raccoon Stealer and its TTPs here.
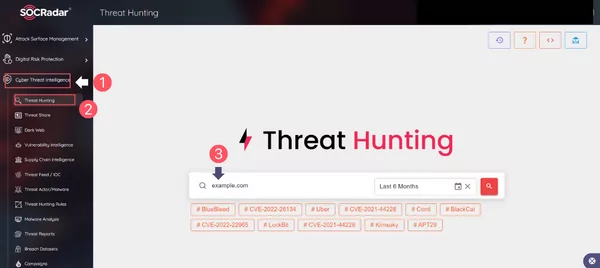
You could use the Threat Hunting feature in the Cyber Threat Intelligence (CTI) module of the SOCRadar Platform as follows:
1. Click the Cyber Threat Intelligence suite on the left menu of the SOCRadar Platform.
2. Click the Threat Hunting module in the Cyber Threat Intelligence.
3. Enter your domain or email in the search bar, as shown below.
4. Click on the Stealer Logs tab.
5. Click on the eye button for details.
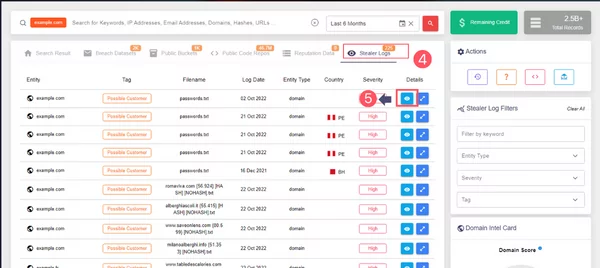
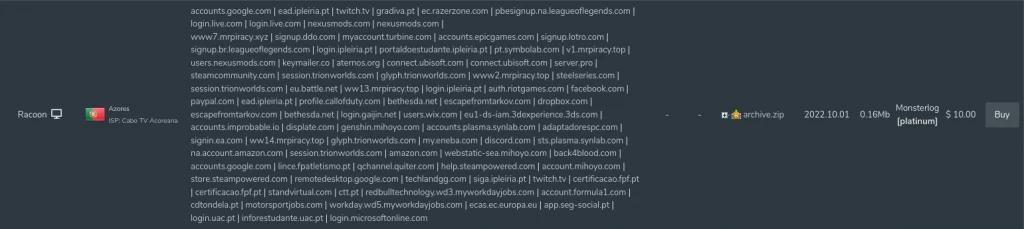
6. Example content of a single Stealer Log entry.