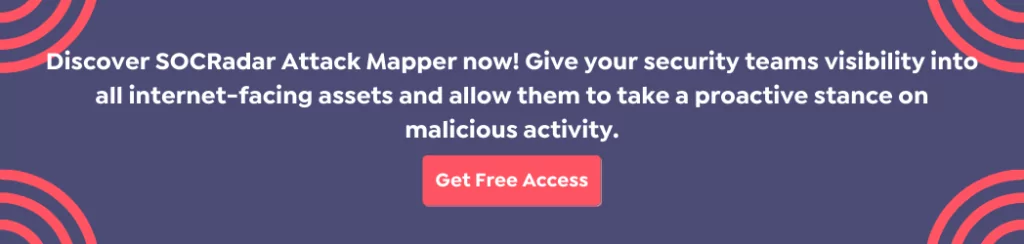
New Version of Raccoon Stealer Released
The new version of Raccoon Stealer has been released. The first version was first seen in 2019 and served as MaaS (malware-as-a-service.) The malware ceased operations on March 25, following the death of one of its key developers in the Russia-Ukraine war.
The new version of Raccoon Stealer has been reintroduced with an announcement on the Telegram channel. Claiming in the announcement that the new version is “much faster and more convenient,” the threat actors stated that the malware is “fully automated” and that operations can be carried out “with just a few mouse clicks.”

What Features Are In The New Version Of Raccoon Stealer?
According to the threat actors’ statement, Raccoon Stealer is now a malware with both loader and stealer functions and focuses on cryptocurrency wallets.
All the features are:
- Lists installed applications and identify those using credentials: browsers, crypto wallets, emails, etc.
- Steals passwords, cookies, and credit cards from identified applications.
- Targets desktop cryptocurrency wallets and wallet extensions like Electrum, Electrum-LTC, Ethereum, MeraMask Wallet, ElectronCash, Atomic, Jaxx, Binance, and TronLink.
- Stores the stolen data in RAM for later sending to the threat actor’s command and control center.
- Runs on both 32-bit and 64-bit operating systems.
- Extracts files from all disks, install executables (cmd, dll, exe), emulates, and downloads other executables.
- Captures screenshots and records keystrokes.
- Exploits fingerprint systems using Windows Registry and WinApi functions.
How is it Working?
According to Sekoia’s analysis, the new version of Raccoon Stealer is written in C/C++ using WinApi. The malware can download legitimate third-party DLL files from the C2 server. The configuration of C2 servers and string expressions goes through RC4 encryption and Base64 encoding.
An example attack scenario for the new version of Racoon Stealer is as follows:
- Loads DLL files dynamically.
- Establishes a run-time dynamic connection with WinApi functions.
- Performs Base64 decoding and RC4 decryption of string data.
- Performs deobfuscation for C2 servers.
- Performs mutex and user authorization checks.
- Performs fingerprinting and data spoofing.
- Retrieves configuration settings from the C2 server.
- Downloads malware and installs legitimate third-party DLL files.
- Collects information such as CPU, RAM, OS version, screenshot, system information, browsers, and crypto-wallets from the infected device.
- Sends the collected information to the C2 server.
- Cleans files created by the malware.
The data collected by Racoon Stealer is sent to the C2 server in a file via a POST request as a new request for each new data. Security researchers have determined that the malware does not use defense evasion techniques such as anti-analysis and obfuscation.
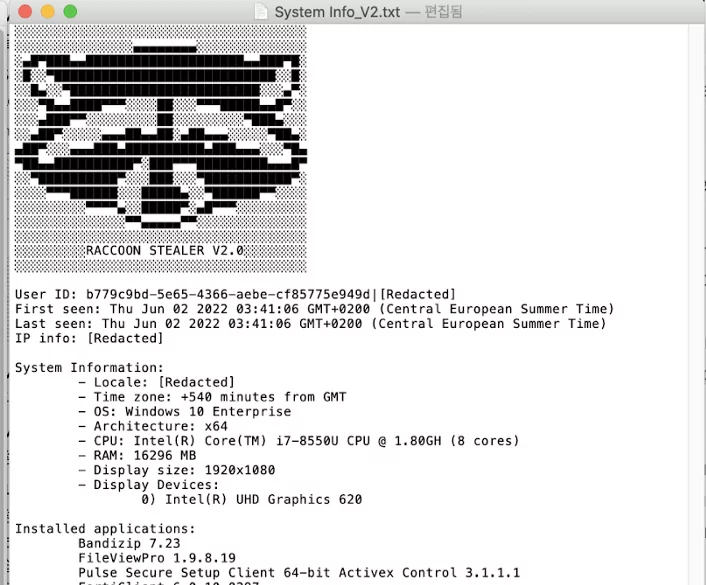
Network Communication
Raccoon Stealer uses a Tor-based C2 server to perform data extortion. Each executable of the malware is linked to client-specific signatures.
The malware sends a POST request to the C2 server containing the machine ID, username, and configuration ID. The server responds with the malware configuration:
- Application to target
- URLs containing legitimate third-party DLLs
- Tokens used for data extraction
- File grabber configuration
After examining the samples of the new version of Raccoon Stealer, cyber security researchers revealed that although many changes have been made to the malware, the main working logic has not changed much.
Considering the unfinished coding and functions such as analysis interruption compared to the first version, Raccoon Stealer is expected to be upgraded regularly in the future.
MITRE ATT&CK TTPs
|
Tactic |
Technique |
Description |
|
Defense Evasion |
T1140 – Deobfuscate/Decode Files or Information |
Decodes strings and the C2 configuration in the malware using RC4 and base64. |
|
Defense Evasion |
T1027 – Obfuscated Files or Information |
Uses RC4-encrypted strings. |
|
Credential Access |
T1539 – Steal Web Session Cookie |
Harvests cookies from popular browsers. |
|
Credential Access |
T1555.003 – Credentials from Password Stores: Credentials from Web Browsers |
Collects passwords from popular browsers. |
|
Discovery |
T1083 – File and Directory Discovery |
Lists files and directories to grab files through all disks. |
|
Discovery |
T1057 – Process Discovery |
Lists the currently running processes on the system. |
|
Discovery |
T1012 – Query Registry |
Queries the Windows Registry key at HKLMSOFTWAREMicrosoftCryptographyMachineGuid to retrieve the MachineGuid value. |
|
Discovery |
T1518 – Software Discovery |
Lists all installed software for the infected machine, by querying the Windows Registry key at HKLMSOFTWAREMicrosoftWindowsCurrentVersionuninstall |
|
Discovery |
T1082 – System Information Discovery |
Collects OS version, host architecture, CPU information, RAM capacity and display device information. |
|
Discovery |
T1614 – System Time Discovery |
Collects the time zone information from the system. |
|
Collection |
T1119 – Automated Collection |
Scans the disks and automatically collects files. |
|
Collection |
T1005 – Data from Local System |
Collects credentials of cryptocurrency wallets from the local system. |
|
Collection |
T1113 – Screen Capture |
Captures a screenshot of the victim’s desktop. |
|
Command and Control |
T1071.001 – Application Layer Protocol: Web Protocols |
Uses HTTP for C2 communications. |
|
Command and Control |
T1041 – Exfiltration Over C2 Channel |
Exfiltrates data over the C2 channel. |
|
Command and Control |
T1105 – Ingress Tool Transfer |
Downloads legitimate third-party DLLs for data collection onto compromised hosts. |
|
Execution |
T1106 – Native API |
Has the ability to launch files using ShellExecuteW. |
|
Defense Evasion |
T1055.001 – Process Injection: Dynamic-link Library Injection |
Has the ability to load DLLs via LoadLibraryW and GetProcAddress. |
|
Defense Evasion |
T1407 – Download New Code at Runtime |
Downloads its next stage from a remote host. |
Raccoon Stealer IoCs
SHA256 (Raccoon Stealer v2)
- 03a8531989aeeec1befecbba4f3ee218309306224bd22b7e52104537e32bacd6
- 056a3022c5e70d112e82844d1101e1a591b02960ae0609f06e9930a3f3bd6efa
- 084754ed1f495ee48a0bfe70b6b5c33ed17bfa129ad03356356ff3a5bf3c46f0
- 0adc96946d9806969375212cfd5012f93cb205c1008b935f6886ba0ffe7fe262
- 0bc3aa6b692b3873dfdd6942fb0eaba7aab391f1d154df80be1193aa792df0c2
- 0fb5b0562e81ae2a89f61b25cca023adf7f370fe049508c96c6bcf898a63e4d7
- 20ca741b731753f1bc981bfceb747dc8f4afb2aeb8694de63114a53d23812161
- 2c7563c76c710a3988c14b8246fd8864c37c08b723b0a24e0f4aa876cc5f73c8
- 40daa898f98206806ad3ff78f63409d509922e0c482684cf4f180faac8cac273
- 494df1513b13c70b1472282b80bdf1a9399ae0d16a90275a5c9fe7cfda6afd0d
- 502f0a6587cf2d084e98f5edc12192e1ca37515bdf7364511415d615be2e6aa7
- 516c81438ac269de2b632fb1c59f4e36c3d714e0929a969ec971430d2d63ac4e
- 567bd8dd69485d8f79edad514e54c085af1490dcc5461a01ee79e57e138b9b10
- 59d74f7e172a2ee14e5e43b9704ac95428b28741f1dbadbf5c9279dd37a11f86
- 61d8e542a34f41b5675daf924a6c21322f0a6aaad9a888b23357c85d29a8f87a
- 6697604c88f0fbb05a6848915d1800eb9a77b607e834c6a01e2bf4a076955a91
- 672fea64c92edc4d937d3132577b65813738bfddeab6a6b3ef35e6fa4b987009
- 6dfd4a12437cf38a4ecdb24891dbff464602fcbe435cf6c15a643637d7f4e1b0
- 6e5d7b8bc69145a2b65b4be1a2d66a8dbc579e54c09660c4070c5667192864bf
- 6e7e69cd1c9b24f6a36870ec5ae6c31c69022fb48d3fdf59bcda5c1528bc9c04
- 6f4e7b117124a1b5a27dfd9a7a3e03b46e84000a992e1029f0cfb62bb77fc3f3
- 7503d528db92b909ad05d65379e6aae008dfaa3664bcac252d34d7a9f25b2db9
- 7c09a54191495c699c04be9e0e2d97cf91d9c4346a37ad751416a2db52636de2
- 83fd32cace2c2f243a713f93918dafd5458af296d55edd293cf5b8b927466dc7
- 9014f5d4a597cdec4ec2d10bf73883b4f0106f62c9938a8c6a59e506b1203e2b
- 909875959dd07c5aeb345d5f93e662329866e862eb8bb18d0727aa4d9c72e6eb
- 99834c9981535b584040fef84af159e5e584927aac4a6a57001ba5ecf1e869c4
- 9d66a6a6823aea1b923f0c200dfecb1ae70839d955e11a3f85184b8e0b16c6f8
- 9e5035f075d6aef29ad158c591adf669324a17442c575c6946c5a7f279705f47
- a25fd13894644550fa9ca60a046813031e5189d4abe4bbd68ed9e6dcfc85d698
- a988a4f3652eaa34b874080da1cbb70223bac6760e318064f4f23b69bf823330
- ab3d8c58a33fd90eca17dc079eb05469bbe535b16eb653810f134df888e230ce
- ae46253a19c9e846c405b3926655efead40d8f873fef008f896019f34d486dfe
- b7104e1420fbcdd4a78b02069f32d4882d38203dcb5f73509b60cc1567dac437
- c6f111e1b32229232af8af25d714ef8f77e30bbc122c0600076bb42cbe46e22b
- c7ee80a9387a941d13738ab069f8f055e14ea8bdb12403a81e0166b098fce032
- cddc1e15fcfcb29cfcb3631f1d478640d228fd9ea38c01d347833567970d04e3
- ce29b09c57bdd0df33b7d45abe0047952fc009dbc1b5b43351aa6dad751ba262
- d2831378b440b653984e58ba82bd670f30eca0e4f23f14c248c50780883d32c3
- e2b87b9ea8bb2bf835cb064845ff863253f3eedb4a88122598eee52c9579b203
- f051b93953919cbf673b16ba995a3c1aa58e59dcc256b9eaf1cdd2f6b3c7dfd2
- f6d5c0f3f6c5cd498b605e06c6bf49a66c7cbbedf3480cb3a95229b4dc91e81d
- F97835279804b62e667211706cce813179e2571634880770862a5f759fa17c11
For other IoCs, please check sekoia.io Community GitHub.
IoCs (May 2021)
SHA256
- 012e382049b88808e2d0b26e016dc189f608deea9b6cc993ce24a57c99dd93d1
- 18c27b85f26566dd782171e00ea5b5872546b23526cca0ebb185caca35fdec93
- 24499fbfd8a2b2663899841f3cf424b60d60c26351b5d491fd475adf9e301256
- 3c5120a6e894b64924dc44f3cdc0da65f277b32870f73019cefeacf492663c0e
- 40175d0027919244b6b56fe5276c44aba846d532501e562da37831403c9ed44e
- 624b7ae8befcf91dbf768d9703147ac8f9bd46b08ffe14a75c77e88736bf07d0
- 75c3a83073d9b15d4f47308b5d688f1ec07422419e3bd54e78f6ef8683d42e5c
- 8815b21c44c22aec31f7fa6e69dcb83a60c572f8365ff02b5c6f12154e01a4c2
- 97e95e99fd499ec45a7c1d8683d5731ce5e7a8fb8b710622e578cd169a00d8d9
- a2420c7f0c7bf5d3c0893aff6b7440a09c0531632434d2bbb6f8ed98b04317b9
- bfb37c9adc809e880f56dd10898b5425242330d6e2fa69e014a98e6dc18ce416
- caf3eca514de58e215b5e9f568f748293be64a3c82e15c2f905903cd9bfacc1c
- de7ccff53ca27db1ed1e3e0d0df07f2e3364ec6b7e60622dc7726cba56831eb7
Domains
telete[.]in
telecut[.]in
tgraph[.]io
tttttt[.]me
telegram[.]cat
telegram[.]services
tlgr[.]org
xn--r1a[.]click (т[.]click)
xn--r1a[.]link (т[.]link)
xn--r1a[.]live(т[.]live)
xn--r1a[.]site (т[.]site)
xn--r1a[.]website (т[.]website)
IP Addresses
195.201.225[.]248
95.216.186[.]40
URLs
hxxps://telete[.]in/jiocacossa
hxxps://tttttt[.]me/kokajakprozak
hxxps://tttttt[.]me/antitantief3
hxxps://telete[.]in/baudemars
hxxps://telete[.]in/bpa1010100102
hxxps://tttttt[.]me/brikitiki
hxxps://tttttt[.]me/ch0koalpengold