
BidenCash Leaked 2.1 Million Credit Card Information
Powered by DarkMirror™
Credit card theft and the sale of credit card information are among the biggest revenue streams for threat actors on the dark web. This information is sometimes used for fraud and sometimes for larger attacks. BidenCash, which emerged in the last quarter of 2022 and leaked a large number of credit card information, shared a new leak of 2.1 million last week.
SOCRadar, in its reports on the e-commerce and finance industries, has given extensive coverage of how credit card information is captured and for what purposes it is used. According to research, it was revealed that more than 17 million credit card information was put up for sale in just the first eight months of 2022.
Here are other noteworthy dark web incidents from last week.
Receive a Free Dark Web Report for Your Organization:
2.1 Million Credit Card Details Leaked by BidenCash Underground Marketplace
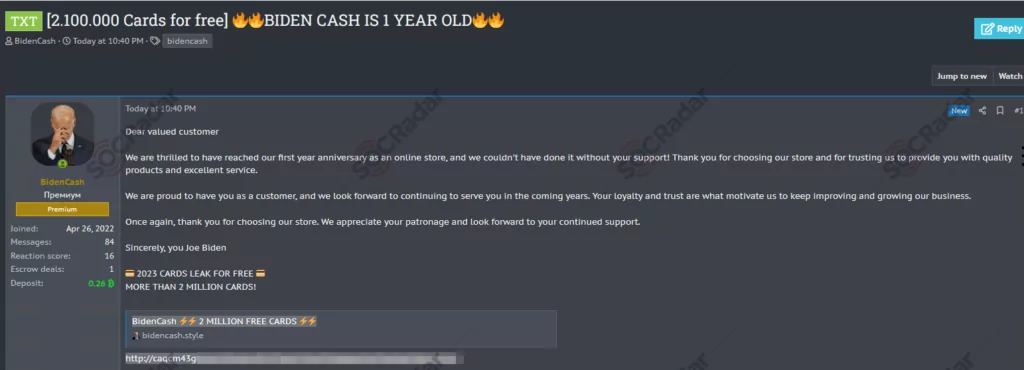
On February 28, SOCRadar found a post on a hacker forum dominated by Russian threat actors. In the post, sent by BidenCash, approximately 2.1 million credit card details were leaked.
When the SOCRadar dark web team analyzed the data set shared by BidenCash, credit card information belonging to multiple countries, such as Turkey, the US, Mexico, China, the UK, Canada, Italy, and France, was detected. The data set included credit card numbers, expiration dates, CVV codes, names, surnames, bank names, card types, addresses, email addresses, and phone numbers. It is known that illegal platforms aim to gain more members by sharing their data for free for advertising purposes during specific periods.
Employee Database of Activision Has Been Leaked
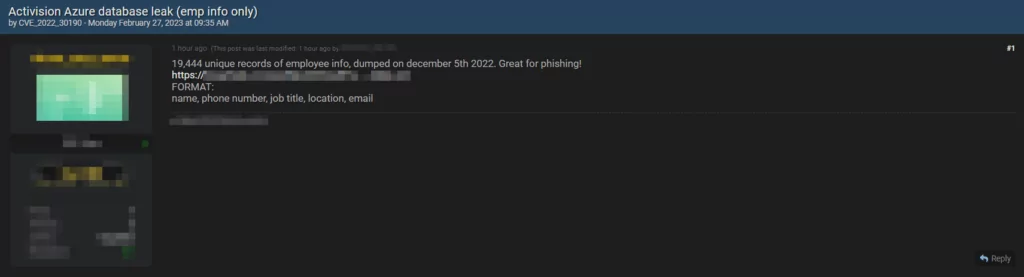
American game publisher Activision disclosed in December 2022 that it had suffered a data breach. SOCRadar dark web team detected a new post on a hacker forum in which threat actors claimed to have stolen employee information from the company’s Azure database. The perpetrators posted the stolen data, including full names, phone numbers, job titles, locations, and email addresses, of alleged Activision employees on a hacking forum. While the authenticity of the data is yet to be confirmed, the incident highlights the potential risks of cyber threats like phishing faced by companies and their employees.
New Data Breach Victim of Snatch: Ingenico
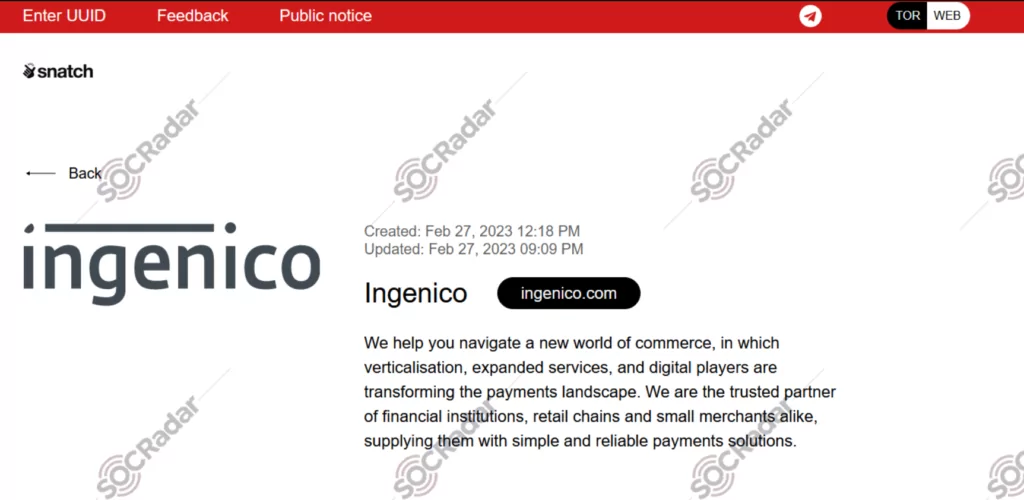
SOCRadar found a new post about Ingenico on the website belonging to the Snatch group. The Snatch threat actor claimed to have compromised sensitive data belonging to Ingenico. As evidence, they included four images in their post as examples of the data they obtained. The threat actor claims access to admin credentials, network, and VPN plans.
New Ransomware Victim of Play: City of Oakland
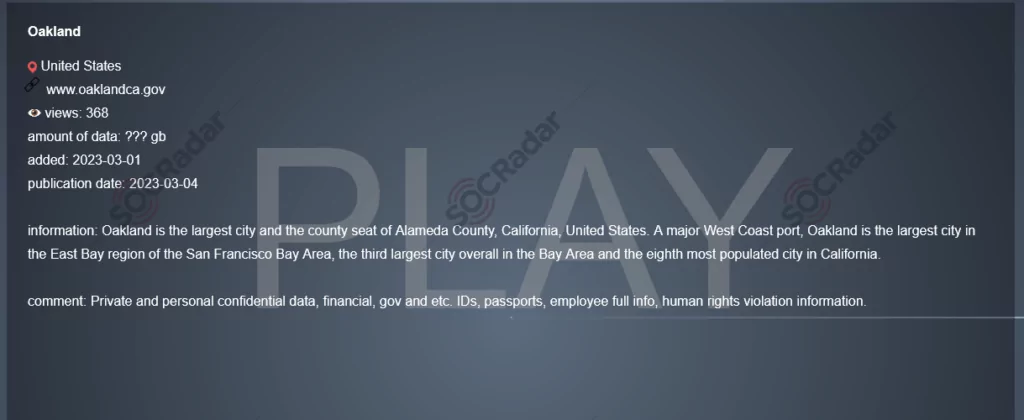
SOCRadar dark web researcher found a post that the Play ransomware group claimed responsibility for the cyberattack on the City of Oakland.
The City of Oakland has experienced IT disruptions since February 15 due to a cyberattack for which the Play ransomware gang has claimed responsibility. According to the threat actors, they have gained access to confidential data, including financial and government documents, identity papers, passports, personal employee information, and evidence of human rights violations. The Play ransomware gang reportedly stole these documents while breaching the City of Oakland’s networks. They are now using them to coerce the city’s administration to comply with their demands and pay the ransom.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































