
What is New in the MITRE ATT&CK Framework v12 and v13?
New threat actors are emerging on the dark web daily, and cybercrimes are increasing exponentially. According to some research insights, the cost of cybercrime is estimated to reach $8 trillion in 2023 and $10.5 trillion by 2025. One important reason for this situation is that cyber attackers constantly update and improve the malware used in attacks and change their tactics and methods. No matter how much endeavor is made for cyber defense, it is not possible to keep up with the speed of cyber attackers. However, in this cat-and-mouse game, essential frameworks, databases, and tools can help security teams on the defensive and offensive sides.
One of the most popular is the MITRE ATT&CK Framework, which offers a comprehensive, systematic, and actionable way to understand attacker behaviors, and you can access it as open source and follow the TTPs (Tactics, Techniques, and Procedures) of threat actors. The MITRE ATT&CK framework has become the universal dictionary of TTPs, in large part due to contributions from security analysts and researchers around the globe.
Thanks to this framework, you can get the answers to some critical questions listed below:
- What are the different stages of a cyberattack?
- What are the common TTPs used by cyber threat actors?
- Which security controls or detection mechanisms can help mitigation and detection phases?
- How can you improve your Digital Forensics & Incident Response (DFIR) procedures?
- What are the potential indicators of compromise (IoCs)?
- What are the recommended best practices for detection and prevention?
- How can you use it to align your security operations and threat intelligence efforts?
- How can you categorize and analyze the techniques or sub-techniques of threat actors?
Let’s look at the prominent and useful features of the newest version of this framework, the latest version 13 of which was announced on April 25, 2023.
What is MITRE ATT&CK Framework?
The cybersecurity industry and academic researchers have adopted the MITRE ATT&CK Framework, a comprehensive knowledge base of malicious behaviors of cyber threat actors such as APTs and their tactics and techniques. The Framework comprises a wealth of knowledge based on real-world observations, which stands for Adversarial Tactics, Techniques, and Common Knowledge. It includes detailed descriptions of these groups’ observed tactics (the technical objectives they’re trying to achieve), techniques (the methods they use), and procedures (specific implementations of techniques), commonly called TTPs. Its broad range of sectoral applications includes threat intelligence, threat detection & hunting, and incident response.
All information captured in the ATT&CK database comes from publicly available data and reports thanks to community contributions such as threat researchers and security teams in the channels experiencing or analyzing cyber attacks daily. It also provides one of the most practical and centralized references to threat groups in the open-source domain.
Furthermore, the Software page in ATT&CK includes an extensive list of 585 entries of software APTs known to exploit. In this context, the term software is used broadly and primarily consists of malware.
There are three main ATT&CK matrices to follow iterations:
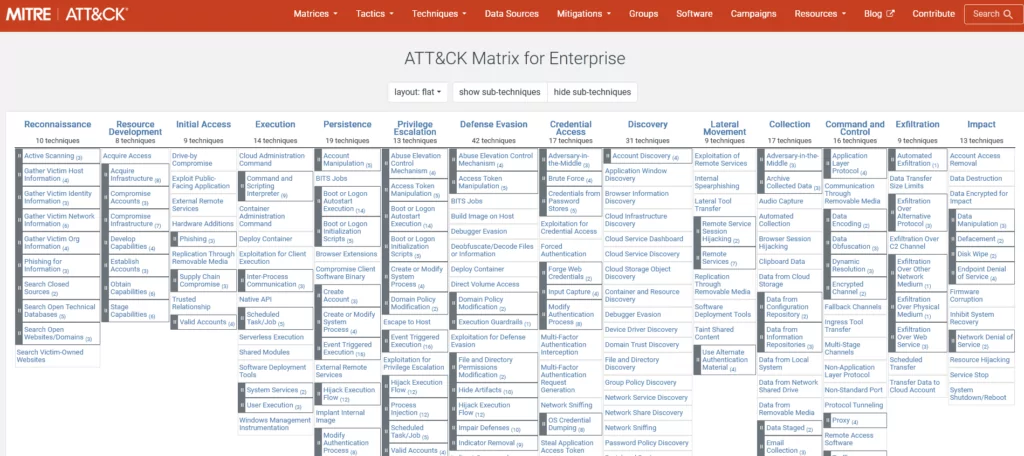
Enterprise: The MITRE ATT&CK Matrix for Enterprise focus on information involving Windows, macOS, Linux, PRE, Azure AD, Office 365, Google Workspace, SaaS, IaaS, Network, and Container Technologies with over 200 techniques across multiple stages of an attack lifecycle.
Mobile: The MITRE ATT&CK Matrix for Mobile concentrates on techniques involving Android and iOS devices and network-based effects.
ICS: The MITRE ATT&CK Matrix for ICS (Industrial Control Systems) covers industrial process controls and their associated systems in critical infrastructure sectors like energy production.
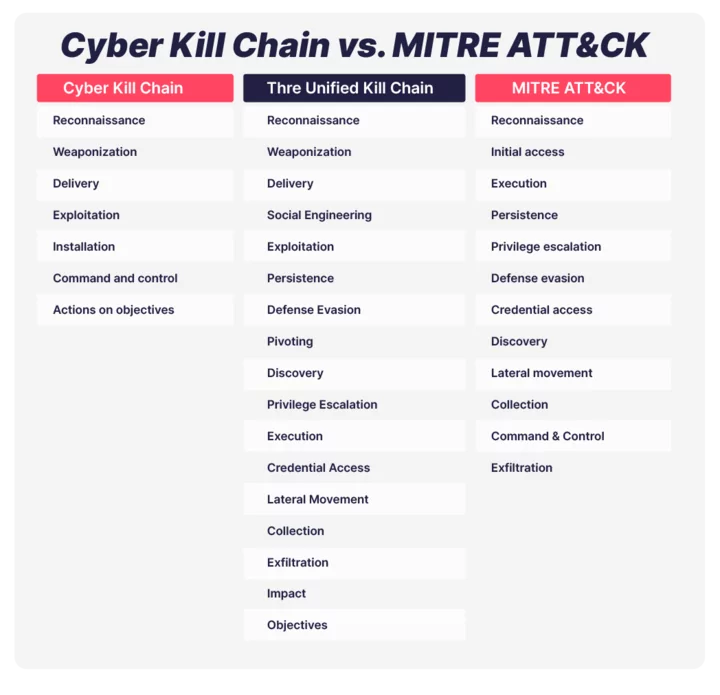
MITRE ATT&CK vs. Cyber Kill Chain
Although both MITRE ATT&CK and Cyber Kill Chain used similar phases or tactics, their main differences exist. While Cyber Kill Chain is great for non-practitioners about a particular attack, which has a clearly defined linear sequence of phases and covers only high-level tactics (goals or phases) of an attack, the ATT&CK framework goes a step further than the Cyber Kill Chain by expanding the attackers’ high-level goals to 14 different tactics and a matrix of intrusion techniques that are not only confined to a specific order of operations but also contain a more profound scope of knowledge and granular details about cyberattacks such as attack TTPs, and links to industry advisories.
The Unified Kill Chain focuses on both Lockheed Martin-Cyber Kill Chain and MITRE ATT&CK. It takes from all of these frameworks and proposes 3 high-level steps attackers take:
1- Initial Foothold
2- Network Propagation
3- Action on Objectives
Such three high-level steps of an attack are even easier to understand for non-technical staff. Each high-level tactic then dives into the techniques in detail.
What are the Benefits of MITRE ATT&CK Framework?
The MITRE ATT&CK offers a useful framework for security teams, including blue teams, red teams, and purple teams’ members such as incident responders, CTI analysts, penetration testers, SOC analysts, and so on.
The MITRE ATT&CK framework can help an organization in several ways. Let’s list the main applicable benefits of adopting ATT&CK:
1– Adversary Emulation and Attack Simulation: Adversary emulation is a type of red team process that mimics a known threat and the attacker’s behavior to an organization by blending in threat intelligence to define what actions and behaviors the red team uses. It also offers the capability to test your organization’s resilience against advanced malicious threats in a situation known as assumed hacking.
ATT&CK can help offensive teams to create adversary behavior emulation scenarios for testing during Red Team and Purple Team exercises. MITRE also created Adversary Emulation Plans, whose purpose of this activity is to allow security teams to test and emulate their defense architecture more effectively by enabling red teams to model adversary behavior more actively, as described by ATT&CK.
CALDERA is also a cybersecurity platform devised to easily automate adversary emulation, help manual red teams, and automate incident response. It is actively built on the MITRE ATT&CK Framework as a research project.
2- Enrichment Threat Intelligence: The MITRE ATT&CK Framework serves as a practical resource for security teams, empowering them to better understand and defend organizations against cyber threats. Security teams can gain intelligence about potential threats targeting their business and stay abreast of the latest improvements in cybersecurity through this framework. The framework provides insights into attacker tactics and techniques that help security teams prioritize their defenses based on real-world threat intelligence.
3- Improvement DFIR (Digital Forensics & Incident Response) capabilities and Threat Hunting: Integrating the MITRE ATT&CK Framework into incident response processes allows security teams to quickly identify tactics and techniques employed during an attack and can help security teams identify patterns in attacker behavior. ATT&CK TTPs can be used to achieve multiple different attack goals; the primary focus is understanding the TTPs the attackers use and how to detect intrusions and mitigate them.
Analysts can create mappings of MITRE ATT&CK to malware families and techniques observed in their environment. Thereafter, they can craft search queries to help with threat-hunting and detection efforts. The ATTACK matrix can also be used to create playbooks for various types of attacks. These playbooks can help incident response teams rapidly identify and respond to attacks and to train the staff.
4- Effective Prioritization of Security Controls: The framework’s focus on specific adversary behaviors allows organizations to prioritize implementing or improving security controls that address these behaviors directly. By identifying the most impactful behaviors, and possible gaps in the defense, security teams can prioritize hunting, detection, and response based on observable threat behaviors rather than reactional requests from stakeholders.
5- Facilitating Stakeholder Communication: The standardized terminology used within the MITRE ATT&CK Matrix facilitates clear communication among different stakeholders. Beyond indicators of compromise (IoCs), ATT&CK can allow the defenders to visualize threat behaviors in a digestible way to show what TTPs are observed and impacting an organization versus what stakeholders expect or want to focus on.
6- Benchmarking Cybersecurity Maturity Levels: The MITRE ATT&CK Evaluations program allows corporations to evaluate their security products via the framework as a benchmarking tool for assessing an organization’s security posture. Purple Teams can add their own test cases using dynamic MITRE ATT&CK Heatmap as a Threat Resistance Metric and make it a repository for security tests. This can help to create a baseline for defense success and provide benchmarks on scores. Purple Teams can establish quantifiable measurements of how well your defensive capabilities prevent and detect attack patterns.
7- Enhanced Security Awareness Training: The framework’s detailed information and real-world examples from the matrix on attack techniques can be incorporated into security awareness training programs to raise employee awareness, recognize potential threats, and follow best practices pertaining to sensitive and personal data. A bundle of training resources designed to help users understand and apply the framework effectively.
How Can You Access and Work with ATT&CK Data?
It is possible to work with the data provided by ATT&CK in several ways. The 5 important ways and methods you can use for your organization are listed below.
1- Structured Threat Information Expression (STIX) is a language and serialization format used to exchange Cyber Threat Intelligence (CTI). The ATT&CK dataset is available in STIX 2.0 and STIX 2.1. Other presentations of this dataset, including the ATT&CK Navigator and this website, are built from the STIX data.
2- Excel spreadsheets representing the ATT&CK dataset. These spreadsheets are built from the STIX dataset and provide a more human-accessible view into the knowledge base while also supporting basic querying/filtering capabilities.
3- The ATT&CK Navigator is a web-based tool for annotating and exploring ATT&CK matrices. It can be used to visualize defensive coverage, blue/red team planning, the frequency of detected techniques, and so on. ATT&CK Navigator is a tool that takes the headache out of using a spreadsheet or other tool to analyze threats, evaluate your defenses, plan attack simulations, compare various elements that ATT&CK tracks, and more.
4- The ATT&CK Workbench is an application allowing users to explore, create, annotate, and share extensions of the ATT&CK knowledge base.
5- ATT&CK provides a variety of Python tools for accessing, querying, and processing the ATT&CK dataset. These scripts can be useful utilities or serve as examples of how to work with ATT&CK programmatically.
What are the New Features of Version 12 and 13?
ATT&CK released (v12) updates related to Techniques, Groups, and Software for Enterprise and Mobile in October 2022. The main changes in ATT&CK v12 were the addition of detections to ATT&CK for ICS and Campaigns pages. This version 12 of ATT&CK for Enterprise contains 14 Tactics, 193 Techniques, 401 Sub-techniques, 135 Groups, 14 Campaigns, and 718 Pieces of Software.
Version 13 includes a new, more human-readable changelog showing what changed in updated ATT&CK objects and also a new machine-readable JSON changelog, whose format is described in ATT&CK’s GitHub. The terminology used in these release notes has also been updated to better describe the changes to various ATT&CK objects. This version of ATT&CK for Enterprise contains 14 tactics, 196 techniques, 411 sub-techniques, 138 groups, 22 campaigns, and 740 pieces of software.
The ATT&CK Sync project facilitates upgrades to new versions of MITRE ATT&CK by providing detailed change logs in both human and machine-readable formats. Use the form to access the changelog depending on the version you are now using and the version you wish to upgrade to.
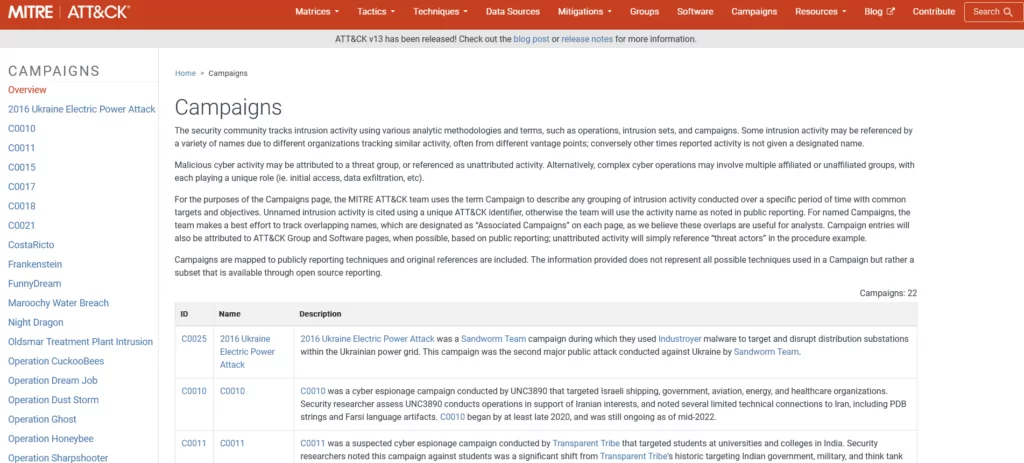
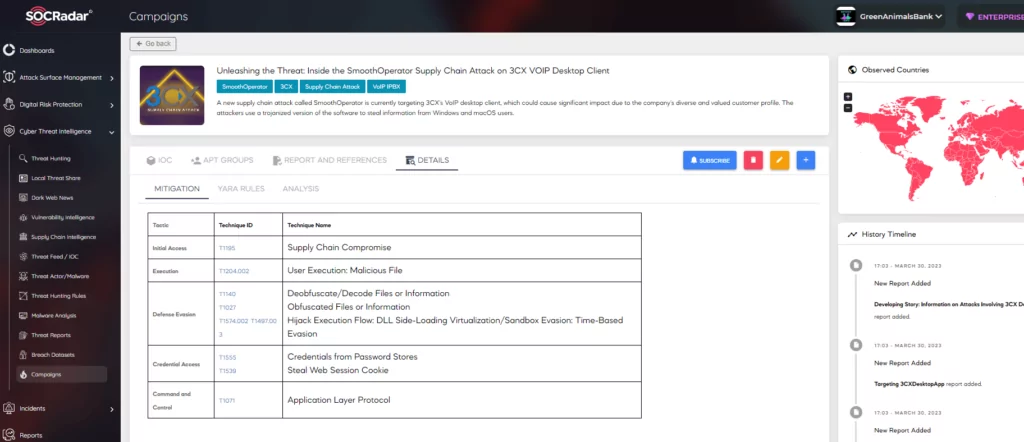
Campaigns Page
One of the more significant changes you can expect this year is the introduction of Campaigns. We can define campaigns as a grouping of intrusion activity performed over a specific period with common targets and objectives; this type of activity may or may not be directly and individually linked to a specific threat actor.
As seen in the figure below, the Campaigns page visually aligns with the Groups and Software pages, and the v12 release featured an addition of a new “Campaigns” button on the main page for easy access.
There are two key changes to Group and Software pages as they relate to Campaigns. Techniques and corresponding procedure examples mapped to a Group Campaign will carry over to the associated Group page. Campaigns table added to associated Group and Software pages, so ATT&CK users can easily reference Campaign ID numbers, Names (when applicable), and the Campaign description.
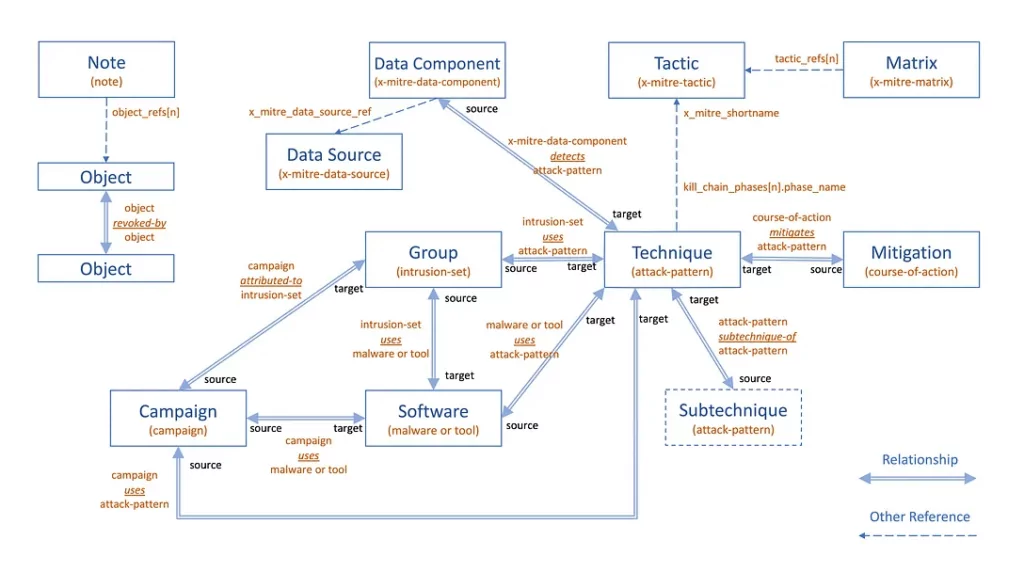
The diagram below represents how all the moving objects work together, with the new additions of the Campaign object type and the relationships between Campaigns and the other objects.
In addition, the SOCRadar Campaign page is designed in line with the MITRE Campaign motivation and serves the customers. The campaign page, which is enriched with dark web and surface intelligence information about recent campaigns, contains a series of attack activities that may be active at certain periods of time, have been successful in their targets, and continue to spread.
Consequently, you can follow these types of real-world threat risks, which are spread over the entire cyberspace, and find out which threat actors the campaigns are associated with, which common TTPs they use, the IoCs identified, and the countries and sectors targeted by the campaigns on SOCRadar Campaign page and support your security posture by gaining actionable insights.
How Can We Use ATT&CK for CTI?
Cyber Threat Intelligence is vital to an organization’s capability to protect itself against modern threats. The MITRE ATT&CK framework provides a common language that allows organizations to build, compare, and analyze threat intelligence. It can be used to help analyze information about the cyber threat landscape and inform decisions based on that analysis.
The ATT&CK framework can also help an organization get actionable threat intelligence itself. Using the intelligence information provided within the framework, an organization can identify behaviors and the tools, techniques, and procedures (TTPs) used by active threat groups and determine whether their existing defensive methods are capable of detecting and responding to attacks by these adversaries.
From the CTI point of view, ATT&CK Framework is more suitable for institutions looking to enrich threat intelligence information and go deep with specific advanced tactics, techniques, and procedures (TTPs). Security teams can better understand the cyber attackers’ modus operandi and improve more targeted defenses.
Real-world Use Case Scenarios
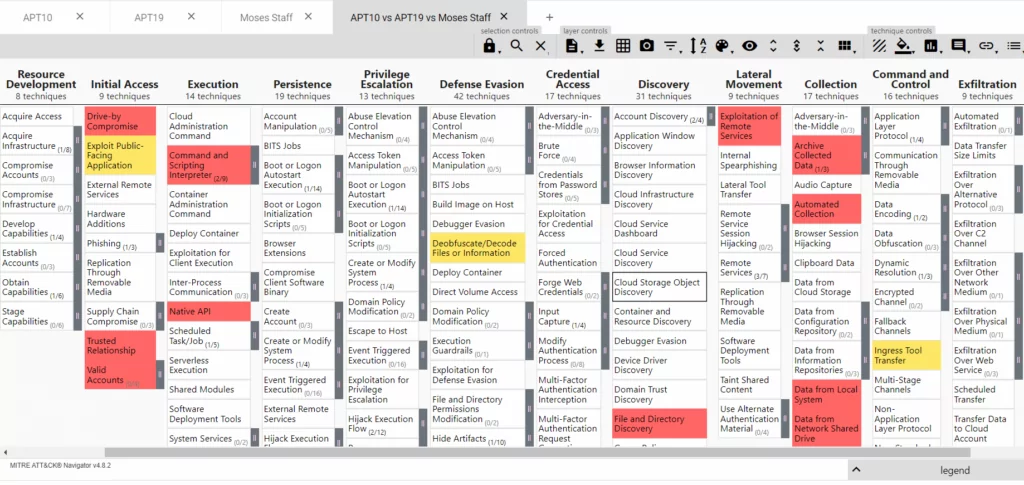
ATT&CK Framework can be used depending on your organization’s specific needs and goals. Let’s consider a real use case scenario for threat intelligence. For this process, you can use the MITRE ATT&CK Navigator mentioned and explained in the section above. For instance, you are carrying on a business in finance and want to get information about threat actors specifically targeting your sector. You can type “finance” from the MITRE home page and choose three threat actors from the pages that appear first, such as APT10, APT19, and Moses Staff. You want to see the TTPs of these threat actors under a single roof and also discover the tactics and techniques they use in common and where they exploit differently, you can realize much more than this described scenario using this framework and even export the output for further analysis.
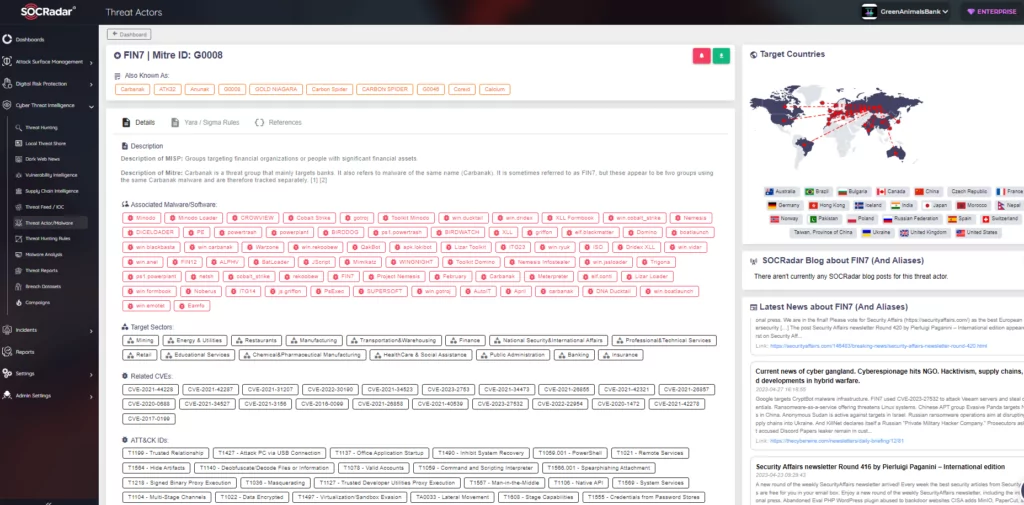
For example, you have gained intelligence that threat actors specially select their victims and focus on their targets on a country and sector basis. SOCRadar Threat Actor Tracking provides intelligence information enriched with the knowledge obtained from the MITRE ATT&CK database about existing TTPs, which can be much more crucial than easily replaceable IOCs, to dynamically understand and track cyber adversaries. Through automated data collection, classification, and AI-powered analysis of hundreds of sources on the surface, deep and dark web, SOCRadar can alert you to the activities of APT groups, helping you identify use cases to effectively detect and prevent malicious attempts.
Conclusion
MITRE ATT&CK is a highly specified and cross-referenced repository of information about adversary groups and their known behaviors; used tactics, techniques, and procedures; specific components of their activities; and both legitimate and malicious software and tools they employed in their attacks. Organized from an attacker’s point of view, MITRE ATT&CK stands apart from other defense-oriented and risk-based threat modeling and lifecycle models. This makes it an invaluable tool for helping organizations gain insight into attacker behavior so they can develop their own defense strategies.
The general characteristics of the framework have enabled analysts to verify open-source reporting and better understand the nature of threat actors. It has also allowed researchers to document and communicate threat behaviors, prioritize detections, and improve defense more effectively. By standardizing how we identify and classify threat behaviors, actionable intelligence can be more easily communicated to a variety of stakeholders.
Cyber Threat Intelligence (CTI) is a continuous process that necessitates the use of text classification techniques for retrieving TTP-oriented information. ATT&CK is valuable for security teams seeking to keep up with the latest threats and enhance their CTI capabilities.
SOCRadar actively utilizes MITRE ATT&CK to track cyber actors that are constantly emerging with a new name and forms, to identify common patterns in the methods of changing and transforming TTPs and threat actors. Thus, it empowers security teams to proactively detect and prevent attacks and keep their digital assets safe from cyber threats. ATT&CK is also used for further threat analysis and adversarial TTP classification in utilizing the framework for linking adversary techniques to vulnerabilities. Many studies link CTI reports with ATT&CK matrices to create effective mitigation strategies. It has been observed that many research papers in this field utilize ATT&CK to improve CTI. However, there is a lack of investigation into how insights gained from CTI research can be used to enhance ATT&CK itself.



































