What You Need to Know About the Alleged Sony Breach
The RansomedVC group has announced that it successfully breached Sony, the renowned Japanese multinational electronics giant. The group claims to have infiltrated all of Sony’s systems in their victim listing, posted both on its clearnet and dark web platforms.
Taking a departure from the typical ransomware approach of encrypting the victim’s files and issuing ransom demands, RansomedVC has chosen a straightforward extortion strategy and declared its intention to directly sell the stolen data.
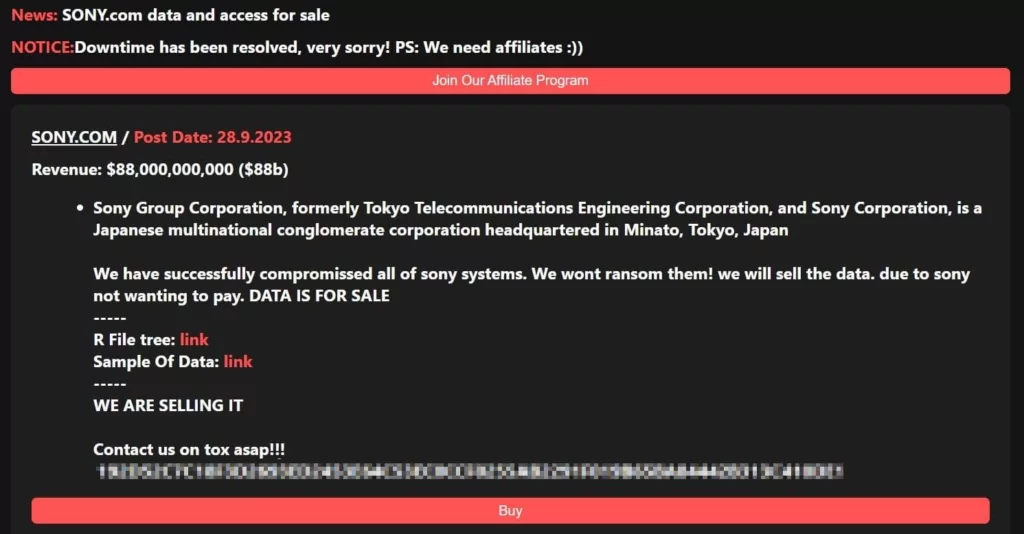
“We have successfully compromissed all of sony systems. We wont ransom them! we will sell the data. due to sony not wanting to pay. DATA IS FOR SALE,” the ransomware group noted in their post.
A file tree of the entire leak is also available in the post as a form of proof. Although the stolen data is claimed to be “all of Sony systems,” this file tree contains fewer than 6,000 files.
The content includes screenshots of an internal login page, a PowerPoint presentation from Sony’s Quality Assurance Division detailing testbench information, numerous Java files, build log files, and some HTML files. It is reported that many of these files feature Japanese characters.
RansomedVC has not specified a price for the data. Instead, they have provided contact details for the Tox messaging service, Telegram, and email, along with a post date of September 28 (currently September 26 on the group’s TOR site). The initial post date may indicate when the ransomware group intends to release all the data.
Threat Actor Claims the Sony Breach to Be False
With no official announcement from Sony, another threat actor has taken to a cybercriminal forum to debunk RansomedVC’s hack, releasing all the content that the ransomware group has claimed to possess. This individual, who goes by the alias “MajorNelson,” labeled the ransomware group as “scammers.” They asserted that RansomedVC has lied about the Sony leak as a means to gain influence.
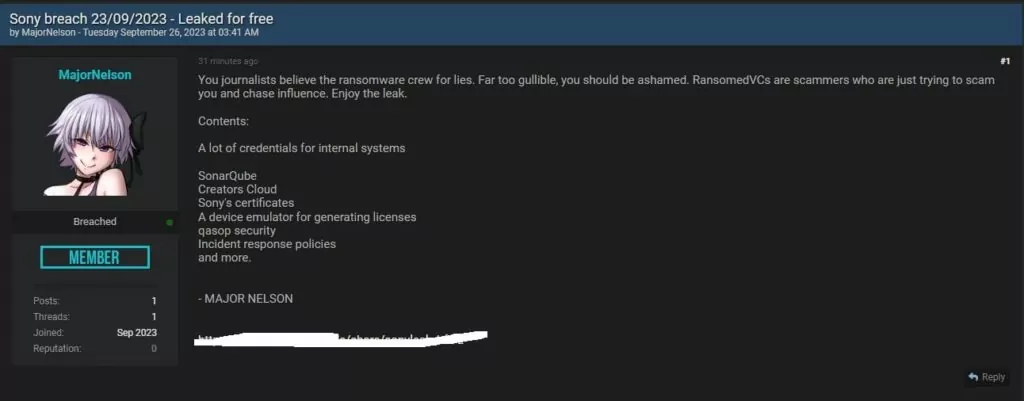
The post lists the following as contents of the leak:
- A lot of credentials for internal systems
- SonarQube
- Creators Cloud
- Sony’s certificates
- A device emulator for generating licenses
- qasop security
- Incident response policies
- and more.
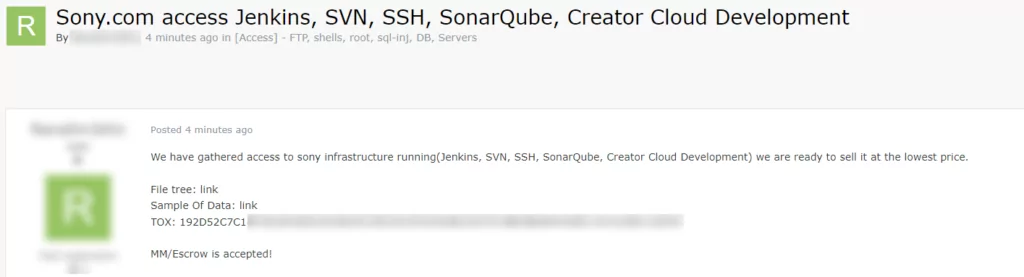
A RansomedVC threat actor had also shared a post on a hacker forum, where they claimed to have gained access to “Sony’s infrastructure running Jenkins, SVN, SSH, SonarQube, and Creator Cloud Development.” The Tox chat ID provided in the forum post matches the one on the victim listing.
RansomedVC (aka Ransomed.vc) is a relatively novel group in the threat landscape, having officially started its operations in 2023. To learn more about the group and its operations, visit our other blog post:
On the Horizon: Ransomed.vc Ransomware Group Spotted in the Wild
Truth Behind the Sony Breach
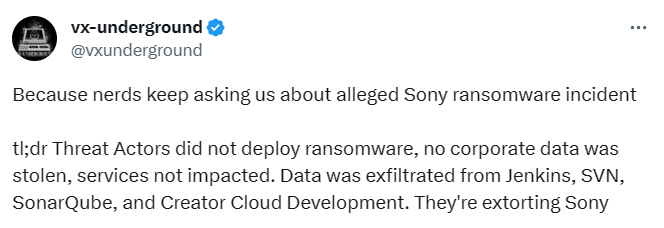
In a Tweet, vx-underground provided a summary of the entire incident. They noted that no corporate data had been stolen. Instead, data was exfiltrated from Jenkins, SVN, SonarQube, and Creator Cloud Development. This suggests that the threat actor might be bluffing, corroborating the point made in the previously mentioned dark web forum post.
Sony’s global popularity and expansive user base make it an attractive target for threat actors. Before RansomedVC’s hack claim, a notorious gang, the Clop ransomware, had targeted the company as part of the MOVEit campaign.
The compromise of credentials and data may not necessarily stem from a zero-day vulnerability within a single software but rather from potential misconfigurations within Sony’s environment. Additionally, gaining access to external-facing servers is likely a less formidable challenge than achieving full access to a corporate network.
In summary, while it appears that not all of Sony’s systems have fallen victim to compromise, uncertainty remains regarding whether the threat actors managed to exfiltrate critical data, and if so, the extent and nature of the pilfered data. The true confirmation of the hack’s authenticity hinges on the awaited announcement from Sony.
How Can SOCRadar Help?
SOCRadar utilizes automated data collection, classification, and AI-driven analysis from diverse sources spanning the surface, deep, and dark web. Through these processes, we ensure that you receive continuous updates regarding cyber threats.
Through vigilant dark web monitoring, SOCRadar promptly notifies you when your organization’s data surfaces on the black market, enabling swift and informed decision-making against data leaks.
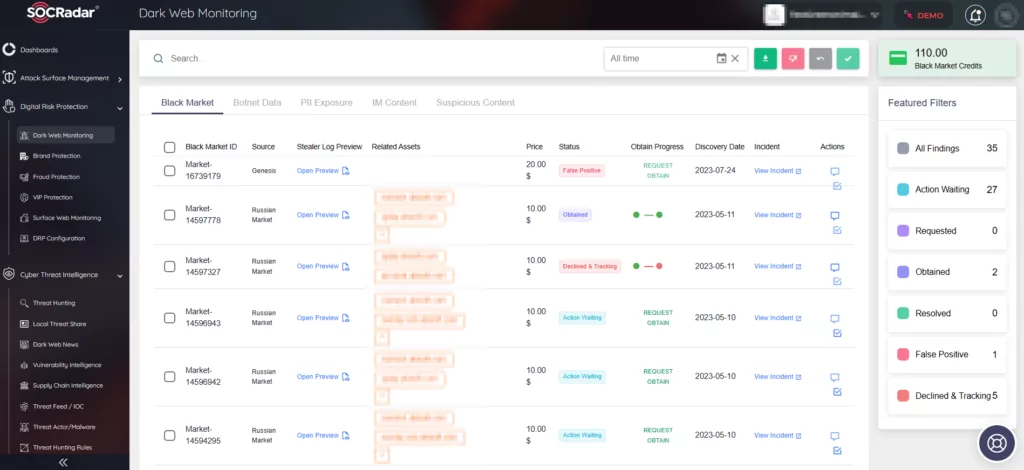
Furthermore, on the platform, you can search for specific threat actors and malware to access comprehensive insights, arming yourself with the critical intelligence to bolster your organization’s defenses. The platform comprises various information on threat actors and malware, including their targeted vulnerabilities, affiliations, and indicators of compromise.