
Major Cyberattacks in Review: October 2023
In October 2023, a surge of cyber incidents underscored the persistent and evolving threats confronting organizations.
October 2023 witnessed a range of malicious activities, from large-scale data breaches to cyber warfare. Notable incidents included escalating tensions in the Israel-Palestine Conflict which reflected on the cyber realm, the alarming hack of Facebook’s official page, and a targeted cyberattack on the Royal Family’s website. Ransomware attacks continued their onslaught, with infamous actors like BlackCat and Knight making headlines. Additionally, multiple organizations faced substantial financial losses due to cyberattacks.
In this blog post, we will explore the notable cyberattacks of October 2023 to gain a comprehensive understanding of these incidents, and the evolving threat landscape.
Threat Actor Offered 815M Indian Citizens’ Data Related to ICMR COVID-19 Tests for Sale

Researchers uncovered a dark web post titled “Indian Citizen Aadhaar & Passport Database 2023” on October 9, 2023. The threat actor, operating under the alias ‘pwn0001,’ put the information of 815 million Indians for sale. This data allegedly originated from COVID-19 tests conducted by the Indian Council of Medical Research (ICMR) and consisted of various personally identifiable information (PII).
The sale also included passport details and Aadhaar card information. Aadhaar, a government initiative, assigns a unique 12-digit identity number to each Indian citizen.
Reportedly, the ICMR COVID-19 test data exceeded 90 GB in size, as indicated in the post. The data was shared in spreadsheets, with one sample containing 100,000 individuals’ PII, including Aadhaar data. Reports suggest that the samples have been authenticated, matching the ICMR’s COVID test data. However, the source of the data and whether it involved a breach of ICMR systems remains uncertain.
LastPass Data Breach Spurs $4.4M Crypto Theft from 80 Wallets

A $4.4 million cryptocurrency theft affected at least 25 people across 80 wallets on October 25, as a result of a 2022 data breach involving the password storage software LastPass. ZachXBT, a pseudonymous on-chain researcher, and MetaMask developer Taylor Monahan examined the fund movements within these compromised wallets on October 27.
According to Monahan, the victims, the majority of whom were long-time LastPass users, had stored their crypto wallet keys or seeds in LastPass. Users who suspect they may have stored their seed phrases or keys in LastPass should immediately transfer their crypto assets to a more secure platform.
Cloudflare Mitigated Thousands of HTTP DDoS Attacks with +100 RPS, Exploiting HTTP/2 Rapid Reset Vulnerability

Cloudflare reported thwarting thousands of hyper-volumetric HTTP Distributed Denial-of-Service (DDoS) attacks, with 89 exceeding 100 million requests per second (RPS). This campaign contributed to a 65% increase in HTTP DDoS attack traffic in Q3, while L3/4 DDoS attacks also rose by 14%.
The attacks stemmed from the HTTP/2 Rapid Reset vulnerability (CVE-2023-44487), discovered as part of a coordinated disclosure that exposed how attackers targeted various providers, including Amazon Web Services (AWS), Cloudflare, and Google Cloud.
Learn more about the Rapid Reset attacks in the SOCRadar blog post: ‘Rapid Reset’ DDoS Attacks Rise: October 2023 Patch Tuesday Has Arrived (CVE-2023-36563, CVE-2023-41763, CVE-2023-44487)
Alleged Airbnb Data Breach Exposed 1.2 Million Users’ Personal Information

An alleged data breach at Airbnb has exposed the personal information of 1.2 million users, and a threat actor known as ‘Sheriff’ claimed responsibility.
The sensitive data, which included names, email addresses, and other information, was listed for sale on the dark web for $7,000.
While the breach raises security concerns for users, Airbnb has not confirmed the breach or issued an official statement about it.
Ransomware Group Knight Struck US Claims Solutions (USCS): 600GB Data Exfiltrated

The Knight ransomware group (formerly known as Cyclops) allegedly executed a cyberattack against US Claims Solutions (USCS).
US Claims Solutions is an insurance company specializing in cargo and inspections, commercial loss claims, firearms appraisals, forensic inventories, and more. Reportedly, the Knight ransomware group exfiltrated over 600GB of data from the company during the attack.
Knight issued a ransom payment deadline of 308 hours and 2 minutes regarding the USCS ransomware attack.
The content of the 600GB of sensitive data exfiltrated by Knight was not disclosed. Knight threatened that if the USCS management did not respond within 2 days, they would sell or publicly release the data obtained from the ransomware attack.
Massive 23andMe Data Leak Sparked Lawsuits

In October, a hacker named “Golem” leaked 4.1 million stolen 23andMe genetic data profiles from Great Britain and Germany on BreachForums. 23andMe stated that this data was obtained through credential stuffing attacks on accounts with weak passwords or exposed credentials from previous data breaches, and there is no evidence of a security incident on their IT systems.
However, a small number of accounts that opted into the ‘DNA Relatives’ feature enabled the threat actor to scrape the data of millions of people.
The threat actors claimed that the stolen data includes genetic information on notable individuals, such as the royal family, the Rothschilds, and the Rockefellers, but it remains unverified. Some of the newly leaked data matches known and public user information, and it was previously sold on a now-shutdown hacking forum, Hydra.
The data breach led to multiple lawsuits against 23andMe, alleging a lack of information about the breach and inadequate protection of customers’ data.
Tech Giant CDW Didn’t Meet LockBit’s $80M Ransom Demand

CDW Corporation, known for providing technology solutions and services, was added to the LockBit ransomware gang’s victim list. The gang leaked the data after their $80 million ransom demand went unmet. CDW-G, a division focusing on U.S. governmental entities, was also affected. Data in the archives includes employee badges, audits, commission payouts, and other account-related information, as indicated by a researcher’s tweet.
Unlike typical ransomware attacks, LockBit did not encrypt files or employ malware, making it more of a data breach with ransom demands. This incident stands out due to the significant $80 million demand, making it one of the costliest ransom demands by a threat actor.
For more on top ransom demands, check our other blog post: Top 10 Ransomware Demands
BlackCat Ransomware Targeted QSI Banking: 5TB SQL Data Theft

The BlackCat ransomware group has targeted QSI Banking, stealing personal and SQL data in an alleged cyberattack. QSI Inc., a major NCR product reseller, faces potential exposure of sensitive data across various sectors. While the QSI Banking cyberattack hasn’t been confirmed by the company, cybersecurity researchers reported it based on a dark web announcement.
The breach, claimed by the BlackCat group, involves the exfiltration of financial, client, and work-related data, including a 5TB SQL database. Numerous banks, such as Wesbanco Bank, Stock Yards Bank, and SECU, were reportedly affected. Furthermore, this incident may be linked to the NCR corporation cyber attack claimed by BlackCat in April 2023.
Escalation of Israel-Palestine Conflict Ignited Cyber Warfare

Multiple hacker groups have joined the escalation of the Israel-Hamas conflict that was initiated in October following a major attack by the Palestinian militant group on Gaza. In response, Israel declared war on Hamas, leading to a retaliatory cycle that resulted in hundreds killed and thousands wounded on both sides.
Alongside state-sponsored actors potentially increasing cyber efforts, hacktivist groups supporting each side have heightened their cyberattacks, marking the beginning of an intensified phase in the Israel-Palestine Conflict.
Discover the cyber aspect of the Israel-Palestine conflict in our blog post: Reflections of the Israel-Palestine Conflict on the Cyber World
Official Page of Facebook Was Hacked: Security Concerns Arise

On October 6, 2023, Facebook’s official page was reportedly hacked, featuring bizarre posts demanding the release of ex-Pakistani PM Imran Khan, who was arrested in August 2023. While it is unclear if it was a prank or a genuine hack, the incident raises serious concerns about the security of Facebook accounts and pages. Social media users were surprised by unusual messages criticizing the BCCI. Facebook swiftly deleted the posts, launched an investigation, and bolstered the page’s security.
This incident highlights the potential dangers, as attackers could trick users into downloading malware or scam them, leveraging users’ trust in Facebook.
Royal.uk Website Was Hit by DDoS Attack
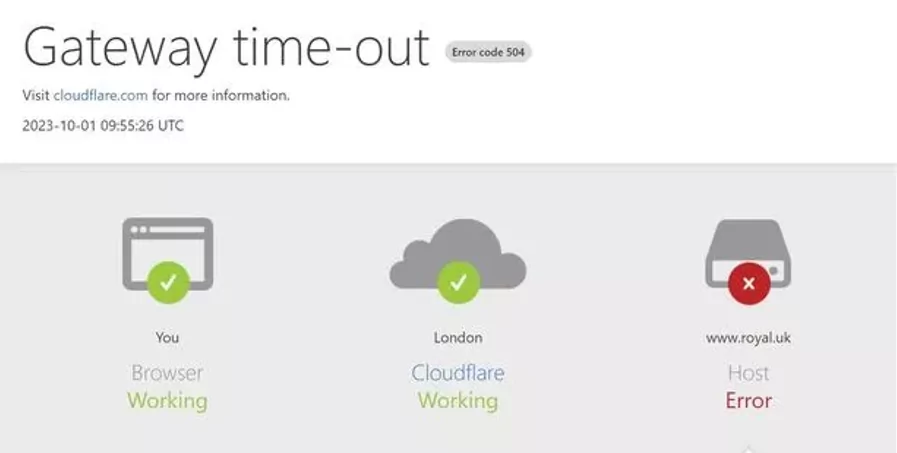
The official website of the U.K.’s royal family faced a serious threat on October 1, 2023, when it fell victim to a Distributed Denial-of-Service (DDoS) attack. Reports indicate that the ‘Royal.uk’ site was inaccessible for approximately 90 minutes, with the incident starting at 10 AM local time.
While the website was restored to full functionality shortly after the attack, ongoing security measures were in place. Russian hacktivist group Killnet has claimed responsibility for the attack on its Telegram channel, although this assertion remains unverified.
Upon the cyberattack on the Royal family website, security experts stressed the importance of robust security measures for all organizations.
Proactive Defense Against Cyber Threats with SOCRadar XTI
Empowered by advanced monitoring algorithms, SOCRadar Extended Threat Intelligence (XTI) continously tracks threat actors, malware, vulnerabilities, and associated trends to provide insights into emerging cyber threats.
With a robust blend of asset monitoring, real-time alerts, and a steady flow of actionable intelligence through the SOCRadar platform, organizations can effectively fortify themselves against threat actors seeking to exploit vulnerabilities, thereby elevating their cybersecurity defenses to unprecedented levels.
Sign up for the Freemium to remain watchful against future threats.



































