‘Rapid Reset’ DDoS Attacks Rise: October 2023 Patch Tuesday Has Arrived (CVE-2023-36563, CVE-2023-41763, CVE-2023-44487)
[Update] October 12, 2023: “Python Script to Detect Rapid Reset Vulnerability is Available on GitHub”
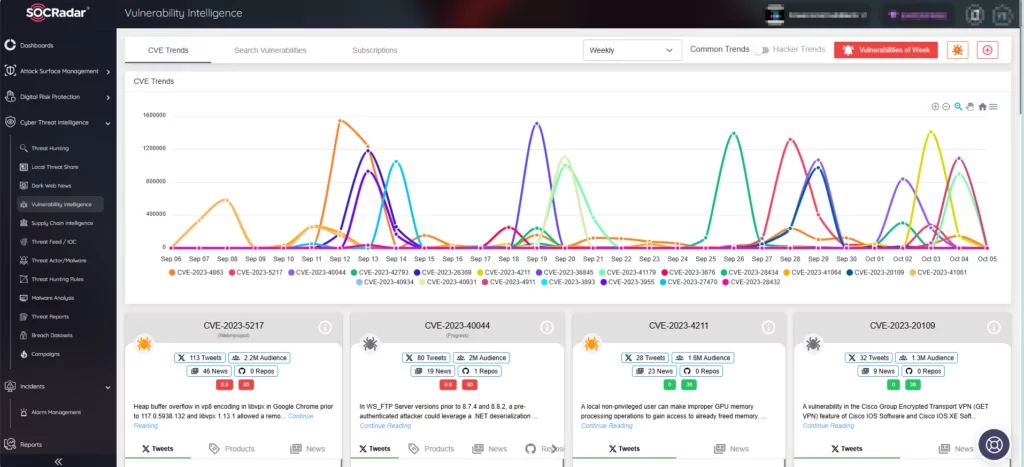
Microsoft has just released its October 2023 Patch Tuesday, which addresses a total of 103 security vulnerabilities. Among these, 12 have been rated as critical, and there are three zero-day vulnerabilities currently being actively exploited. One of these zero-day vulnerabilities relates to Rapid Reset DDoS attacks, which have recently emerged as a significant issue.
The October 2023 Patch Tuesday includes the following vulnerability types:
- 45 Remote Code Execution (RCE) Vulnerabilities
- 26 Elevation of Privilege (EoP) Vulnerabilities
- 16 Denial of Service (DoS) Vulnerabilities
- 12 Information Disclosure Vulnerabilities
- 3 Security Feature Bypass Vulnerabilities
- 1 Cross-Site Scripting (XSS) Vulnerability
We will spotlight the addressed vulnerabilities, outline the risks associated with zero-day exploits, and guide organizations on protecting their systems.
Actively Exploited Zero-Day Vulnerabilities: CVE-2023-36563, CVE-2023-41763, and CVE-2023-44487
This month’s Patch Tuesday addresses three actively exploited zero-day vulnerabilities:
CVE-2023-36563 (CVSS Score: 6.5): This vulnerability, an information disclosure flaw in WordPad, has the potential to expose NTLM hashes upon exploitation. There are two methods by which this vulnerability can be exploited. The first method involves an attacker persuading a local user to open a specially crafted malicious file, using social engineering. The second method of exploitation entails running a specially crafted application capable of exploiting the vulnerability and assuming control over an affected system.
For more information and mitigation methods related to this vulnerability, refer to this link.
CVE-2023-41763 (CVSS Score: 5.3): An attacker could make a specially crafted network call, directed at the target Skype for Business server. This could lead to the parsing of an HTTP request to an arbitrary address, potentially revealing IP addresses and/or port numbers. If successfully exploited, the vulnerability would enable the attacker to access certain sensitive information, and in specific instances, the exposed information could grant access to internal networks.
The third zero-day vulnerability, tracked as CVE-2023-44487, was disclosed as a non-Microsoft CVE, and you can find its details in the following section.
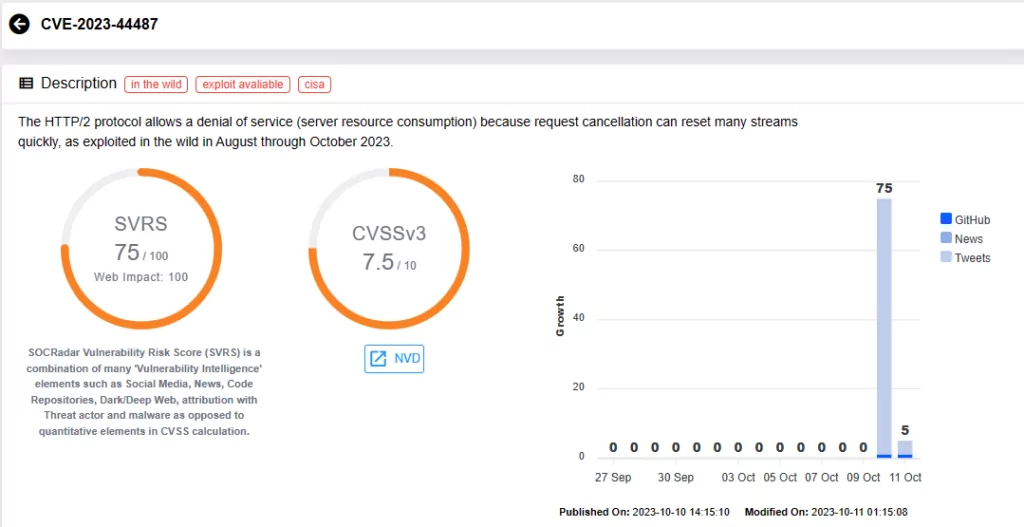
Zero-Day Vulnerability in HTTP/2: ‘Rapid Reset’ (CVE-2023-44487)
CVE-2023-44487 (CVSS Score: 7.5): Published as a non-Microsoft CVE, this vulnerability impacts any internet exposed HTTP/2 endpoints, leading to a Denial-of-Service situation caused by server resource consumption. This occurs as request cancellation can swiftly reset numerous streams.
The vulnerability is also known as ‘Rapid Reset’, and it has been actively exploited in the wild between August and October 2023.
While Microsoft’s advisory does not offer extensive details about this vulnerability, it does include some workarounds:
- Disable the HTTP/2 protocol on your web server by using the Registry Editor
- Include a protocols setting for each Kestrel endpoint to limit your application to HTTP1.1
Furthermore, Microsoft detailed the Rapid Reset attack scheme in a blog post and presented several other mitigation methods.
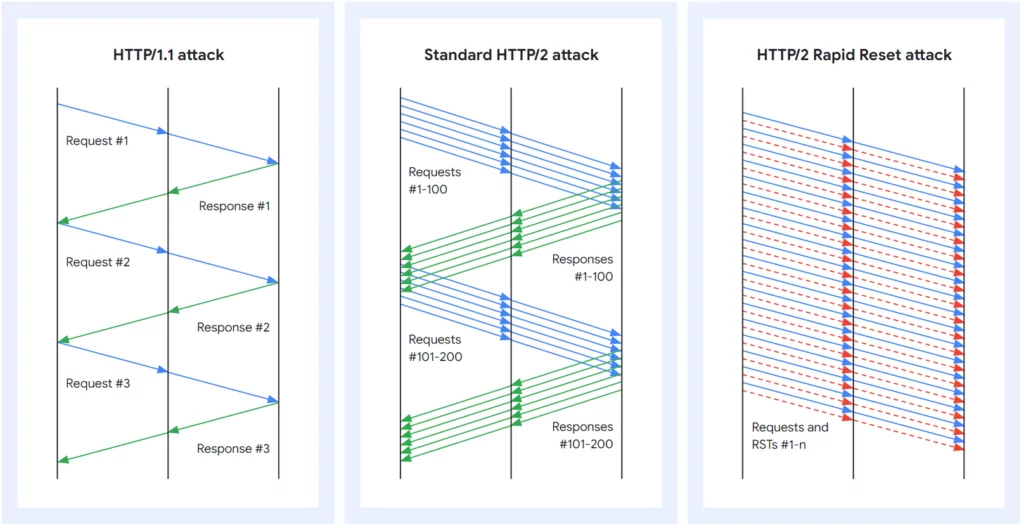
How Does the Rapid Reset Attack Work?
The attack involves sending a set number of HTTP requests using HEADERS followed by RST_STREAM, and repeating this sequence to create substantial traffic on the targeted HTTP/2 servers. Attackers pack multiple HEADERS and RST_STREAM frames within a single connection, leading to a significant surge in requests per second and increased CPU usage on the servers. This heightened load can eventually lead to resource exhaustion, resulting in a DDoS attack.
This attack is termed ‘Rapid Reset’ because it capitalizes on the endpoint’s ability to promptly issue a RST_STREAM frame right after sending a request frame. This process initiates the server’s work and then swiftly resets the request, effectively canceling it while keeping the HTTP/2 connection open.
Microsoft emphasizes that this HTTP DDoS activity primarily targets layer 7, rather than layer 3 or 4. Therefore, adopting protective measures against layer 7 DDoS attacks is also recommended.
Variants of Rapid Reset Attacks
Google has observed various Rapid Reset attack variants after the initial DDoS attacks. It is reported that, while not as efficient as the original version, these variants can still outperform standard HTTP/2 DDoS attacks.
The first variant opens a batch of streams, waits, cancels them, and quickly opens another batch. This approach can bypass mitigation strategies reliant on the rate of inbound RST_STREAM frames. However, it does not maximize connection usage, requiring strict rate-limiting for effective mitigation.
The second variant ditches stream cancellations entirely. Instead, it attempts to open more concurrent streams than the server allows, keeping the request pipeline full.
Google notes that the current HTTP/2 RFC (RFC 9113, a specification that defines an extension to the HTTP/2 protocol) suggests that attempting to open too many streams should only invalidate the exceeding streams, not the entire connection, making non-cancelling attacks possible.
CISA Urges Organizations to Secure Against Rapid Reset Attacks
The Cybersecurity & Infrastructure Security Agency (CISA) has issued an advisory to warn organizations about CVE-2023-44487. The agency advises organizations offering HTTP/2 services to apply available patches, consider configuration adjustments, and implement other mitigations.
CISA’s advisory lists several informative reports which also include mitigation measures aimed at helping organizations safeguard against the exploitation of CVE-2023-44487 in Rapid Reset DDoS attacks.
For more information, visit CISA’s advisory.
Python Script to Detect Rapid Reset Vulnerability is Available on GitHub
A Python script to scan for the Rapid Reset vulnerability is now available on GitHub. This tool performs non-invasive checks to determine if a website is vulnerable to CVE-2023-44487.
The tool assesses whether a web server accepts HTTP/2 requests by attempting to establish a connection stream and subsequently reset it. If the web server allows both the creation and resetting of the connection stream, it is considered vulnerable. In cases where the server only accepts HTTP/2 requests but the stream connection fails, it may still be vulnerable if server-side capabilities are enabled.
The script’s final output includes the vulnerability status. You can find the script on GitHub.
What are the Critical Vulnerabilities Addressed in October 2023 Patch Tuesday?
As part of the October 2023 Patch Tuesday update, Microsoft has released a total of 12 critical vulnerabilities, all of which are RCE vulnerabilities. Nine of these vulnerabilities impact the Windows Layer 2 Tunneling Protocol; see the CVE identifiers below:
- CVE-2023-38166
- CVE-2023-41765
- CVE-2023-41767
- CVE-2023-41768
- CVE-2023-41769
- CVE-2023-41770
- CVE-2023-41771
- CVE-2023-41773
- CVE-2023-41774
Two of the other critical CVEs, CVE-2023-35349 and CVE-2023-36697, have been assigned to vulnerabilities in Microsoft Message Queuing (MSMQ).
CVE-2023-35349 (CVSS Score: 9.8): While the advisory does not provide specific details about its attack vector, it requires MSMQ to be enabled for a system to be vulnerable to this vulnerability. To check for susceptibility, verify if a service named Message Queuing is running, and confirm that TCP port 1801 is actively listening on the machine.
CVE-2023-36697 (CVSS Score: 6.8): Exploiting this vulnerability successfully enables a remote, authenticated domain user to execute arbitrary code on the target server. The attacker must persuade a user on the target machine to connect to a malicious server or compromise a legitimate MSMQ server host and manipulate it into functioning as a malicious server. As it demands valid domain credentials and user interaction on the target machine, the CVSS score is lower for this vulnerability.
The final critical vulnerability identifier pertains to a container escape issue affecting Microsoft Virtual Trusted Platform Module (vTPM).
CVE-2023-36718 (CVSS Score: 7.8): This vulnerability impacts vTPM. Successful exploitation can result in an escape from a contained execution environment. To exploit this, the attacker must first gain access to the vulnerable VM. The advisory notes that exploitation of CVE-2023-36718 is possible when authenticated as a guest mode user.
We highly recommend promptly applying patches to safeguard your environment and enhance your security stance. For additional details on the vulnerabilities addressed in this update, refer to Microsoft’s Release Note.
Address Vulnerabilities with SOCRadar
In the evolving cyber landscape, SOCRadar is dedicated to assisting you in overcoming security challenges, preserving the integrity of your systems, data, and reputation. SOCRadar’s Vulnerability Intelligence and External Attack Surface Management solutions offer the means to promptly identify, assess, and mitigate vulnerabilities.
On SOCRadar’s Company Vulnerabilities page within Attack Surface Management, you can access essential information on vulnerabilities that affect your assets. By integrating SOCRadar into your security strategy, you can strengthen your defense mechanisms and stay ahead of emerging threats.
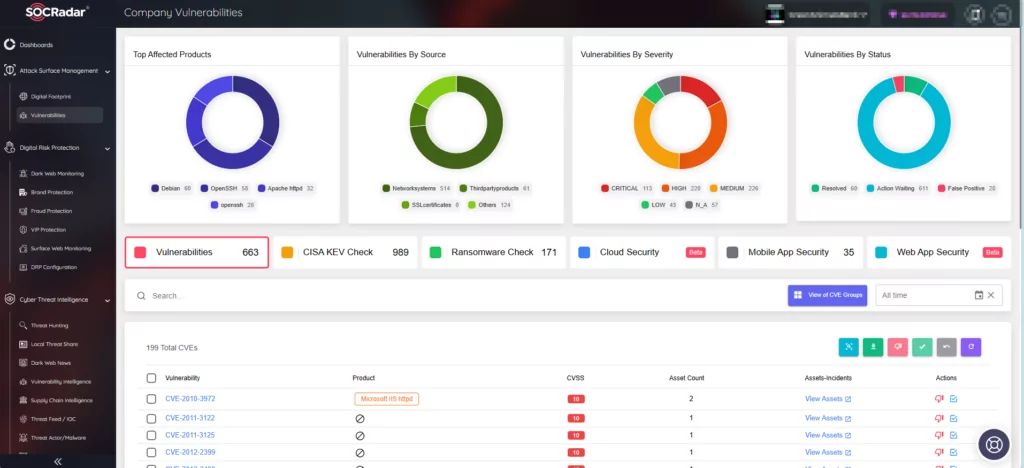
SOCRadar’s Vulnerability Intelligence enhances security measures by continuously tracking security vulnerabilities. You can utilize this module to search for vulnerabilities, access detailed information about them, and monitor associated activities, including hacker trends.