
Dark Strom’s Android RAT, Sales of Financial Data and UK RDP Access, SiegedSec’s Government Breach
The SOCRadar Dark Web Team unveils a fresh wave of illicit activities as the relentless pace of dark web threats persists. Recognized threat actors have made significant moves: SiegedSec claims access to sensitive government data, and the Dark Strom team markets an updated hacking tool for Android on their Telegram channel. Noteworthy events also involve sales of access and compromised data, particularly financial information. Let’s delve into the latest digest of the Week in Dark Web and uncover more about these findings.
Find out if your data has been exposed.
Dark Strom Team Markets Craxs Rat V 6.7
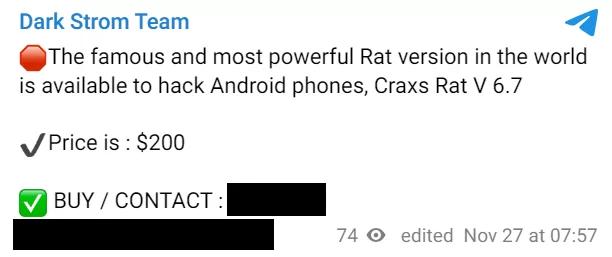
The notorious hacker group Dark Strom, known for its involvement in the Israel-Palestine cyber conflict, has announced that it is selling the latest version of its Android hacking tool, Craxs Rat V 6.7, on Telegram. Priced at $200, this tool is claimed to be among the “most powerful” in the world for hacking Android phones. Dark Strom’s activities also took place in recent ongoing cyber conflict, and there are also recent updates on GitHub with the name of Craxs Rat highlighting the evolving threat landscape.
Spanish Real Estate Leads Data Sale
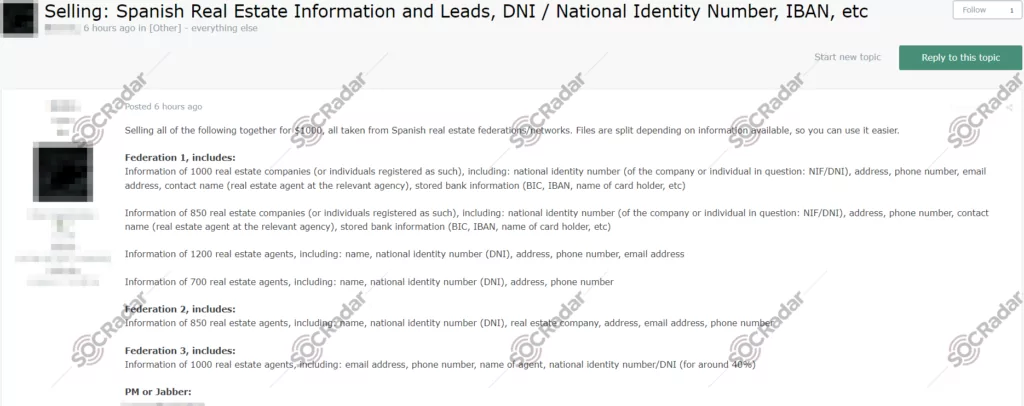
A significant alleged sale of real estate leads data in Spain has been detected. The seller offers comprehensive information on real estate companies and agents, including personal and banking details sourced from various Spanish real estate federations. This extensive collection of data is being sold for $1,000. It allegedly includes sensitive information such as national identity numbers, addresses, and stored bank information, posing a serious risk to privacy and financial security.
2,800 Credit Cards on Sale
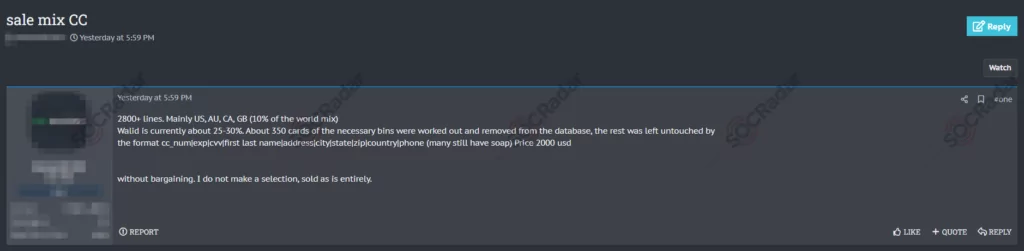
A new sale of 2,800 credit cards, mainly from the US, Australia, Canada, and the UK, has been observed. The seller claims a validity rate of 25-30% and is offering the entire database for $2,000. This database allegedly includes detailed information such as card numbers, expiration dates, CVVs, and cardholders’ personal details. The sale highlights the ongoing issue of credit card data breaches and the illicit trade of financial information.
Unauthorized RDP Access to a UK Software Company
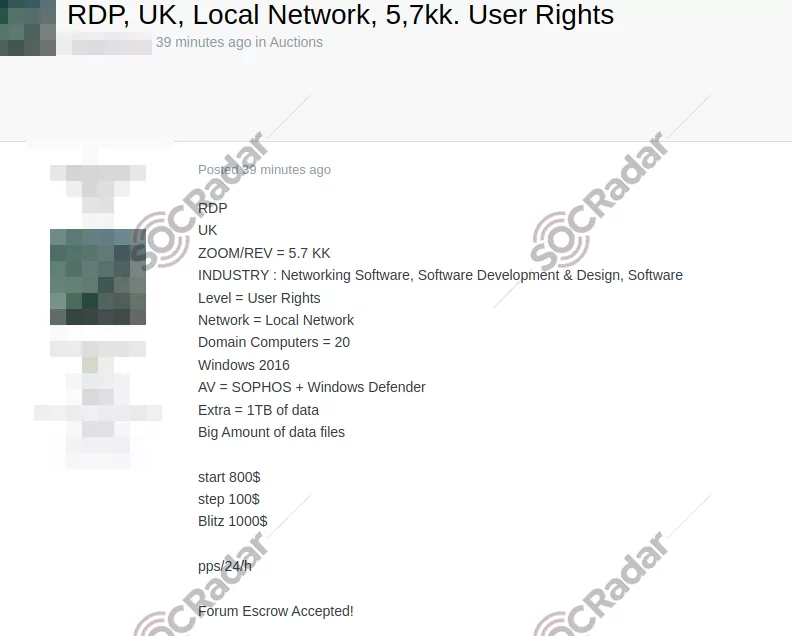
Unauthorized RDP access to a British software company is currently up for sale. The alleged access includes user rights to a local network with 20 domain computers running Windows 2016 and protected by Sophos and Windows Defender. The seller is starting bids at $800, with the potential to reach $1,000. This breach signifies a severe threat to the company’s network security and exposes a significant amount of data and internal resources.
SiegedSec Claims Breach of Hendersonville, NC Government Data
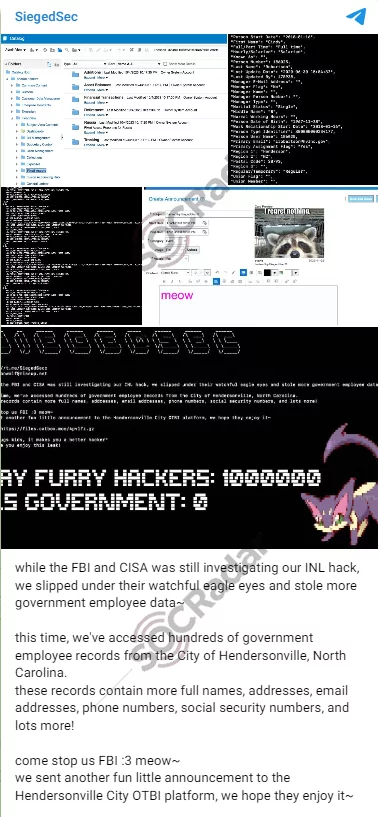
SiegedSec, a hacktivist group known for its breach of the Idaho National Laboratory, claims to have accessed sensitive data from Hendersonville, North Carolina. The group alleges obtaining government employees’ personal information, including social security numbers. This claim underlines the increasing trend of cyber-attacks targeting government entities and raises concerns over the potential implications for identity theft and national security. The group’s methods and motivations continue to pose unique challenges in cybersecurity defense strategies.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































