
Cisco Zero-Day Vulnerability Exploited by LockBit and Akira (CVE-2023-20269)
Cisco recently issued an advisory regarding a zero-day vulnerability, CVE-2023-20269, in its Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) products.
The zero-day vulnerability has been exploited in the wild, with reports indicating that two notorious ransomware groups, LockBit and Akira, are among those responsible for its exploitation.
A blog post by Cisco, published in late August, confirms that the Akira ransomware group has been targeting Cisco VPNs since March 2023. Furthermore, the LockBit ransomware group has also been implicated in attacks against Cisco systems.
Researchers have noted that threat actors primarily target organizations and systems that do not set Multi-Factor Authentication (MFA) for their VPN users.
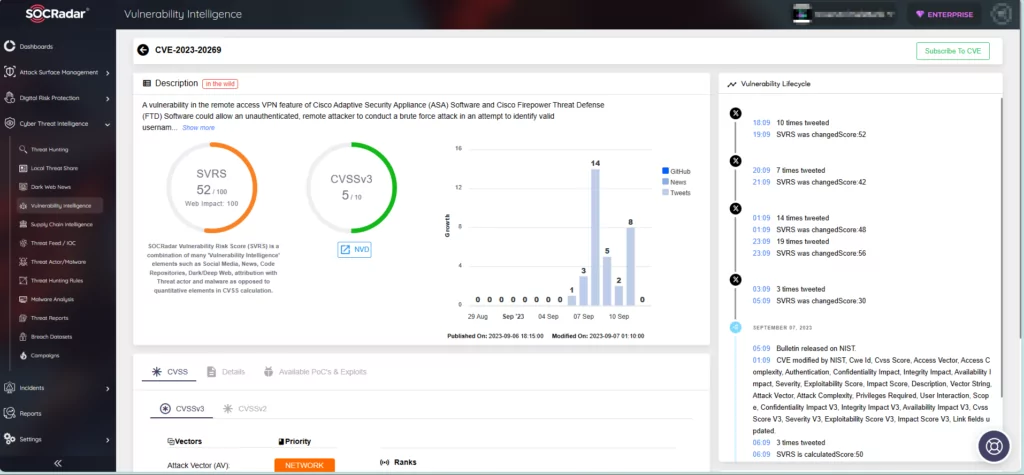
What is the Cisco Vulnerability About? (CVE-2023-20269)
CVE-2023-20269 (CVSS score by Cisco: 5.0, Medium severity) is an unauthorized access vulnerability in Cisco ASA and FTD, affecting the remote access VPN feature.
According to Cisco, the vulnerability is caused by improper separation of authentication, authorization, and accounting (AAA) between the remote access VPN feature and HTTPS management, as well as site-to-site VPN features.
To exploit CVE-2023-20269, a remote, unauthenticated attacker can either brute-force usernames and passwords for the vulnerable system, or use valid credentials to establish a clientless SSL VPN session with an unauthorized user.
For successful exploitation, the vulnerable system must contain at least one user with a password in the local database, or the HTTPS management authentication must point to a valid AAA server. Additionally, either SSL VPN or IKEv2 VPN must be enabled on at least one interface, and the DfltGrpPolicy group policy must include the clientless SSL VPN protocol.
For further information about how the zero-day vulnerability works, refer to Cisco’s advisory.
Which Products and Versions Are Affected?
The zero-day vulnerability specifically impacts the Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software. Vulnerable versions of Cisco’s Adaptive Security Appliance (ASA) encompass 9.16 and prior. In order to launch attacks on the ASA and FTD, an attacker must meet the previously mentioned requirements.
The products that are known to not be affected by the zero-day vulnerability are Firepower Management Center (FMC) software, FXOS, IOS, IOS XE, IOS XR, and NX-OS software.
Are Patches Available for the Cisco Zero-Day Vulnerability?
Cisco has provided a range of workarounds to assist in preventing exploitation attempts until a patch is available. You can access the workarounds here. The vendor has also shared indicators of compromise related to the exploitation of the zero-day vulnerability, which can assist in identifying successful exploit attempts on user devices.
Google Chrome Zero-Day Abused in the Wild (CVE-2023-4863)
Another zero-day vulnerability affects Google Chrome, which has been reported to be exploited in the wild.
The vulnerability, CVE-2023-4863, is a heap buffer overflow issue in the WebP image format that could allow arbitrary code execution or a crash. Google has decided to not provide further information about the zero-day vulnerability until the majority of users have applied the updates.
Chrome users are advised to update to version 116.0.5845.187 for Mac and Linux devices, and 116.0.5845.187/.188 for Windows devices to avoid the exploitation of the vulnerability.
For further information, refer to Google’s advisory.
Stay Proactive Against Vulnerabilities with SOCRadar
Maintaining a proactive stance against potential vulnerabilities and threats is of utmost importance. With SOCRadar’s capabilities in Vulnerability Intelligence and External Attack Surface Management, businesses can assess and address potential threats before they cause any harm, ensuring the security of their digital assets.
Enter the world of proactive cybersecurity with SOCRadar’s Free Edition and stay ahead of emerging threats.



































