
TeamCity Authentication Bypass Flaw: CVE-2023-42793
[Update] December 14, 2023: See the subheading: “CISA Alerts on APT29 Exploiting TeamCity Vulnerability, CVE-2023-42793.”
[Update] October 6, 2023: A PoC exploit for the TeamCity vulnerability has surfaced. Further details are in the blog post.
In recent cyber news, a critical security flaw has been unearthed in JetBrains TeamCity. With the trend of growing software vulnerabilities, it is essential for organizations to stay ahead of potential threats. This vulnerability, identified as CVE-2023-42793, has caught the attention of the cybersecurity community due to its severity and potential impact.
This flaw was initially discovered and reported by the adept team at Sonar. For those unfamiliar with TeamCity, it is a product from JetBrains and serves as a robust solution for continuous integration and deployment (CI/CD). Yet, like all software, it’s not immune to vulnerabilities.
Details of the Vulnerability
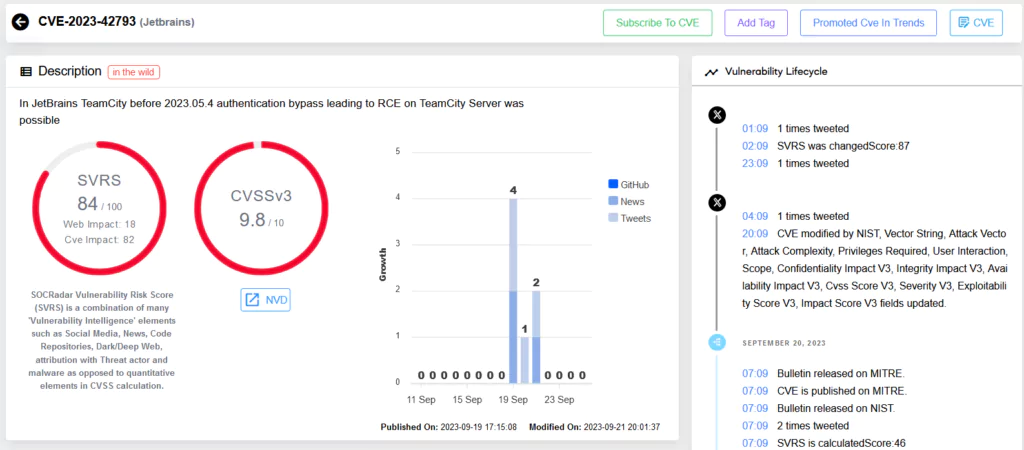
The criticality of this flaw lies in its potential. It allows an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication. This bypass paves the way for a remote code execution (RCE) attack, allowing attackers to gain administrative control of the TeamCity server. The gravity of this vulnerability is reflected in its CVSS score of 9.8, indicating its high-risk nature.
Affected Versions and Mitigations
All on-premises versions of TeamCity are susceptible to this vulnerability. Thankfully, JetBrains acted promptly, releasing a fix in version 2023.05.4. It’s crucial for organizations using TeamCity On-Premises to upgrade their servers to this version, ensuring the security of their systems.
However, JetBrains has provided a security patch plugin in scenarios where an immediate upgrade isn’t feasible. This plugin, compatible with TeamCity 8.0 and above, specifically targets and patches the RCE vulnerability. But it’s worth noting that this is a temporary fix. Upgrading the server to the latest version is recommended for a holistic security solution.
Safety First: Precautionary Measures
For servers that are publicly accessible, if upgrading or applying the patch isn’t immediately feasible, a best practice would be to temporarily restrict its accessibility. This would be prudent to prevent potential exploitation until mitigation measures are in place.
CISA Alerts on APT29 Exploiting TeamCity Vulnerability, CVE-2023-42793
Since September 2023, the APT29 group, linked to Russia’s Foreign Intelligence Service (SVR), has actively targeted TeamCity servers, exploiting CVE-2023-42793, as warned by CISA and authoring agencies.
To bring attention to Russia’s activities, CISA and the agencies have released details of the SVR’s recent compromise through a new advisory. The advisory includes actionable IOCs, TTPs, and other pertinent information, providing organizations with essential intelligence for conducting thorough investigations to secure their networks.
CISA states that in this newly attributed operation, the group continues its trend of targeting technology companies. By exploiting CVE-2023-42793, the SVR specifically targets the networks of software developers. The SVR has been observed using this initial access to escalate privileges, move laterally, deploy additional backdoors, and establish persistent access to the compromised networks.
The advisory also notes that the SVR has not yet moved into customer networks following the intrusions. However, the operation appears to be in a preparatory phase, and the risk could escalate in the future. It is further highlighted that having access to these networks provides the SVR with opportunities to set up hard-to-detect C2 infrastructure.
Significantly, the same vulnerability was exploited by Lazarus and affiliated groups. In October, Microsoft disclosed that Lazarus and Andariel, North Korean state-backed hacking groups, were backdooring victims’ networks using CVE-2023-42793.
PoC Exploit is Available for TeamCity Authentication Bypass Vulnerability (CVE-2023-42793)
A Proof-of-Concept exploit (PoC) is now available for the TeamCity authentication bypass vulnerability, CVE-2023-42793. This PoC emerged in a Russian Telegram channel which actively shares posts related to penetration testing and PoCs for documented vulnerabilities.
The issue revolves around a specific method in the software and an interceptor framework. CVE-2023-42793 allows unauthorized users to manipulate incoming HTTP requests, bypass authentication checks, and gain admin tokens.
With the admin token, attackers can create users with admin privileges. Additionally, the vulnerability can be exploited to achieve Remote Code Execution (RCE) by enabling debug mode and executing commands.
In the Telegram post, the channel admin pointed out that the interceptor allows modifying incoming HTTP requests; thereby, any incoming HTTP request with a /**/RPC2 path avoids authentication checks.
The RPC2 authentication token used in this attack is an important indicator of compromise in context of the TeamCity vulnerability, showing that there is malicious activity. Attackers may attempt to cover their tracks by deleting or renaming the token after exploitation.
The Larger Picture: SOCRadar Vulnerability Intelligence
The discovery of such vulnerabilities underscores the importance of proactive cybersecurity measures. Tools like SOCRadar’s Vulnerability Intelligence can serve as the first line of defense, providing real-time insights into emerging threats. By staying informed, organizations can take timely action, ensuring their infrastructure remains secure.
Conclusion
The digital landscape is ever-evolving, with new vulnerabilities emerging daily. Staying ahead requires diligence, swift action, and the right tools. With platforms like SOCRadar’s Vulnerability Intelligence, organizations are better equipped to face these challenges head-on, ensuring a safer digital future for all.



































