RCEs in FortiOS SSL VPN, ‘shim’; Latest Ivanti Flaw Possibly Exploited (CVE-2024-21762, CVE-2023-40547, CVE-2024-22024)
[Update] March 20, 2024: “Technical Documentation and Detailed Exploit Code on CVE-2024-21762”
[Update] March 18, 2024: “PoC Exploit for FortiOS SSL VPN Vulnerability (CVE-2024-21762) Emerges on a Hacker Forum”
[Update] March 11, 2024: “Nearly 150,000 FortiOS Devices Are Vulnerable to CVE-2024-21762”
[Update] February 16, 2024: “Scanning Activity Detected for CVE-2024-22024 in Ivanti; Thousands of Instances Are Still Vulnerable”
Fortinet has revealed a new critical Remote Code Execution (RCE) vulnerability in FortiOS SSL VPN, cautioning about potential exploitation in ongoing attacks.
Tracked as CVE-2024-21762 (CVSS: 9.6), the critical vulnerability is an out-of-bounds write issue in FortiOS. It enables unauthenticated attackers to execute RCE through maliciously crafted requests.
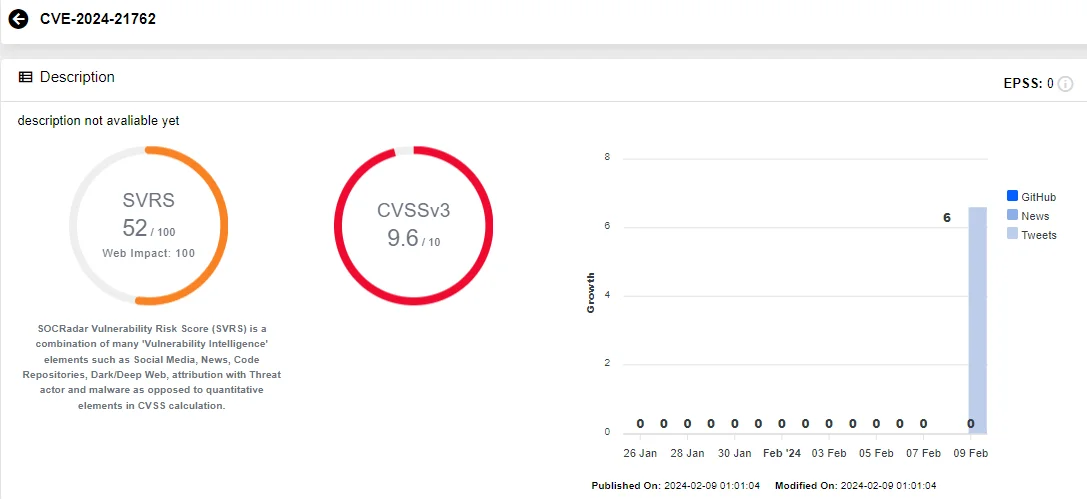
SOCRadar Vulnerability Card for CVE-2024-21762
The affected FortiOS versions include:
- FortiOS 7.6
- FortiOS 7.4
- FortiOS 7.2
- FortiOS 7.0
- FortiOS 6.4
- FortiOS 6.2
- FortiOS 6.0
Fortinet advises upgrading to the latest versions listed in the advisory to patch the FortiOS SSL VPN vulnerability. If unable to apply patches immediately, as a mitigation method, you can disable SSL VPN on FortiOS devices.
According to a Shodan search, over 310,000 Fortigate firewalls are accessible from the Internet.
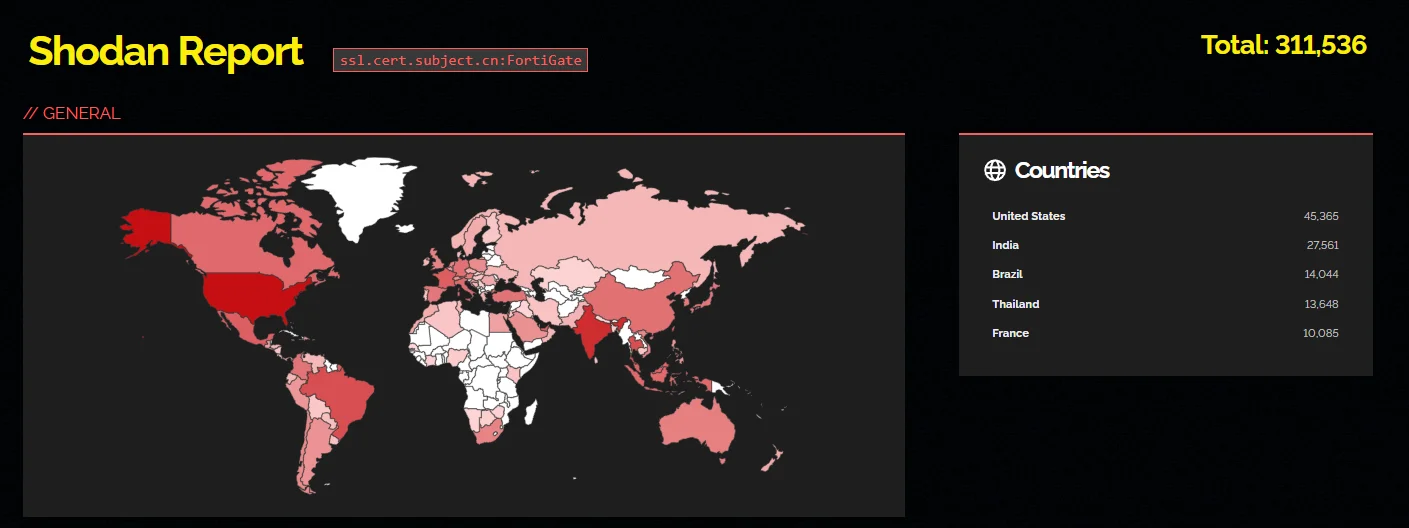
Shodan search on exposed Fortigate firewalls
In addition to CVE-2024-21762, Fortinet disclosed another critical vulnerability, CVE-2024-23113 (CVSS: 9.8), although it has not been reported as exploited in the wild.
With SOCRadar’s Vulnerability Intelligence, you can track hacker trends and access detailed information on identified vulnerabilities, as well as view if a particular vulnerability has an associated exploit detected.
Concerningly, Fortinet recently revealed that Chinese state-sponsored threat actors, known as Volt Typhoon, target FortiOS vulnerabilities to deploy custom malware. CISA has also issued guides to mitigate the impact of this threat group. Following recommended measures to mitigate vulnerabilities in such popular products, which are also targeted by specific threat actors, holds great importance.
*CISA included the FortiOS vulnerability CVE-2024-21762 in its Known Exploited Vulnerabilities (KEV) Catalog, citing active exploitation. The agency emphasizes that such vulnerabilities are common targets for attackers, posing significant risks to the federal enterprise. Organizations are urged to patch the vulnerability by February 16, 2024, to mitigate potential threats.
Nearly 150,000 FortiOS Devices Are Vulnerable to CVE-2024-21762
The Shadowserver Foundation recently revealed enhancements to its scans for FortiOS/FortiProxy, leading to the discovery of almost 150,000 devices vulnerable to CVE-2024-21762. The Foundation made this announcement on X, highlighting the widespread exposure to this vulnerability.
The scan results revealed a significant number of vulnerable instances in the United States, with over 24,600 identified. This is the highest number of any country. Following the United States, India and Brazil have the next highest numbers, with 7,713 and 4,934 vulnerable instances respectively.
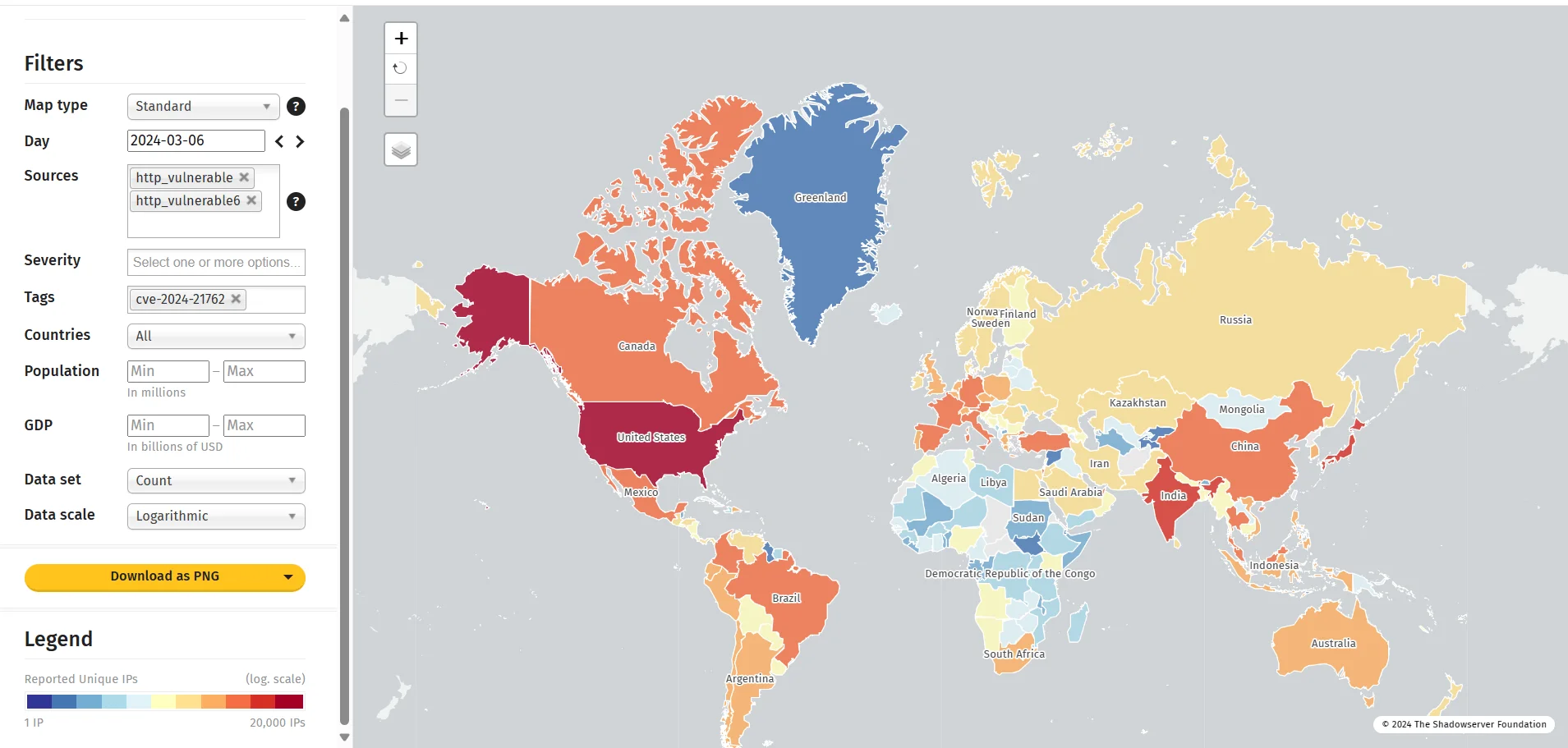
Scan of instances vulnerable to CVE-2024-21762 (Shadowserver)
It is important to note that the actual number of vulnerable devices might be somewhat lower. This is because the scan targets vulnerable versions of FortiOS/FortiProxy, but some administrators may have implemented mitigating measures to protect against CVE-2024-21762 instead of updating to a newer version.
PoC Exploit for FortiOS SSL VPN Vulnerability (CVE-2024-21762) Emerges on a Hacker Forum
SOCRadar has discovered that a threat actor shared a Proof-of-Concept (PoC) exploit for the FortiOS SSL VPN vulnerability, CVE-2024-21762, on a hacking forum.
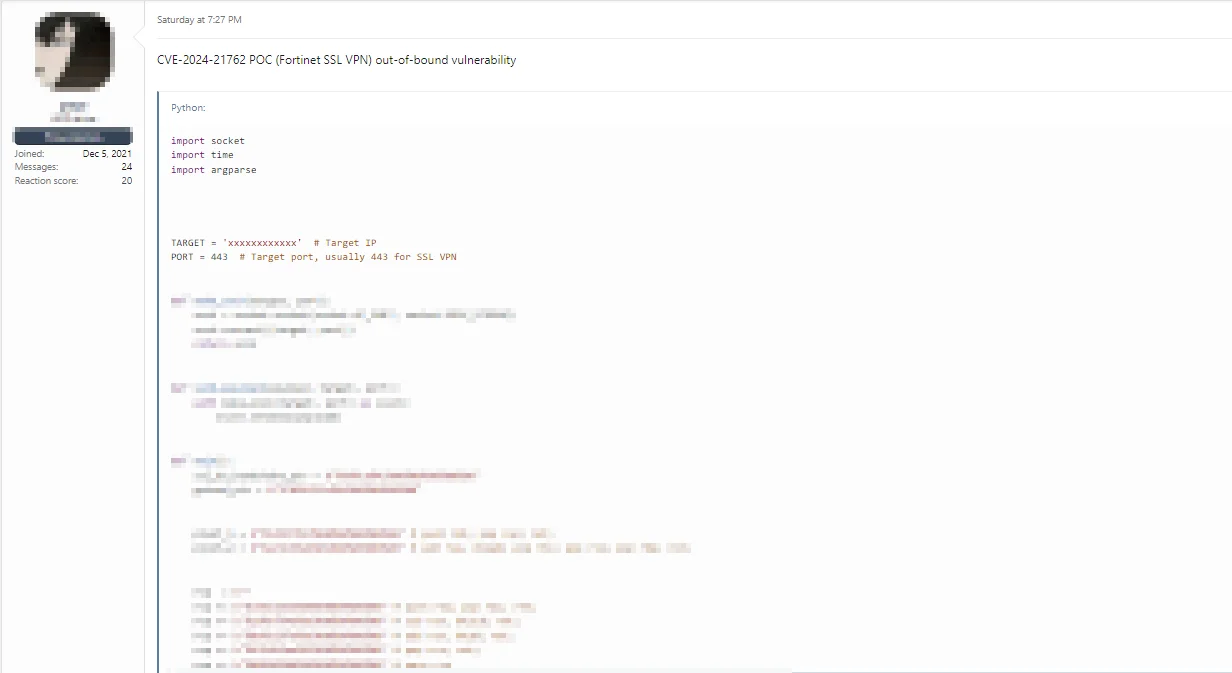
A threat actor on a hacker forum shared an exploit for CVE-2024-21762 on March 16, 2024.
The PoC script establishes a foundation for interacting with a target system via a socket connection in order to send crafted payloads. As previously warned, exploitation of this critical out-of-bounds write vulnerability could lead to Remote Code Execution (RCE) attacks.
In February, CISA included the vulnerability in its KEV Catalog due to active exploitation. The fact that threat actors have started sharing a PoC across underground forums heightens the risk, attracting more threat actors and equipping them with the means to exploit CVE-2024-21762.
Exploits shared across dark web hacker forums quickly evolve into potent weapons, fueling cybercrime. Learn more about the dangers of shared exploits and discover the top vulnerabilities that attracted threat actors: Top 10 Vulnerabilities on the Dark Web in 2023.
Technical Documentation and Detailed Exploit Code on CVE-2024-21762
An official Proof-of-Concept (PoC) exploit code for the FortiOS SSL VPN vulnerability, CVE-2024-21762, is now available with detailed technical documentation.
Security researcher and pentester Dylan Pindur dug into the vulnerability, clarifying its intricacies through patch diffing. He cited CVE-2024-21762 as another example of a significant memory corruption vulnerability in a network/security appliance, which is a recurring issue for FortiGate. Pindur stated that while mitigations exist, timely implementation is critical.
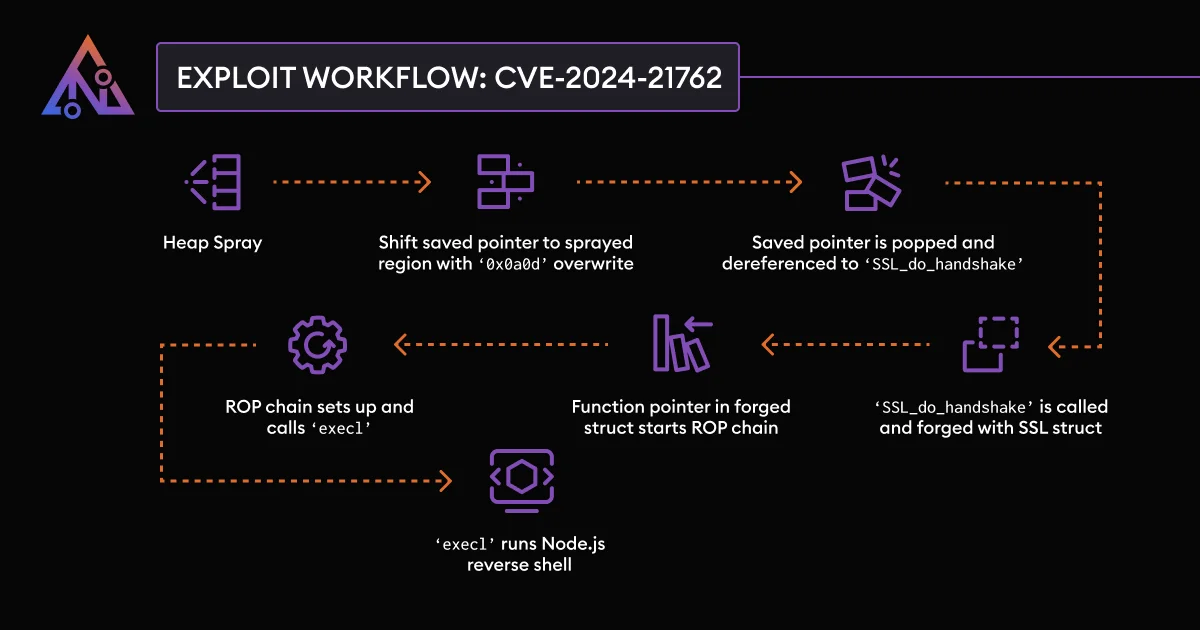
Exploit workflow of the CVE-2024-21762 vulnerability. See its technical analysis here.
A PoC exploit in the form of a Python script is provided on GitHub, based on the researcher’s technical analysis. The script configures several pointers and ROP gadgets to generate a payload that eventually executes arbitrary code.
While defenders gain additional insights with the release of a technical documentation and an official exploit code, threat actors gain additional resources to exploit the vulnerability. To safeguard FortiOS SSL VPN instances, it is strongly recommended that you apply the necessary security patches. A Nuclei template for detection is available and can be useful if you suspect your instance is vulnerable to CVE-2024-21762.
Shim Security Update for Critical Vulnerabilities Affecting Secure Boot on Linux
The maintainers of shim addressed six vulnerabilities, including a critical flaw that could potentially lead to Remote Code Execution (RCE) under specific circumstances.
In the context of Secure Boot on Linux, “shim” refers to a pre-bootloader program that works with Secure Boot firmware on UEFI systems. Most Linux distributions use it in the boot process; it allows trusted bootloaders and kernel modules to be loaded and executed if they are not included in the Secure Boot database. The shim verifies the signatures of these components to ensure their integrity and authenticity during boot.
It is frequently used when either the bootloader or the operating system kernel lacks a signature recognized by the UEFI firmware. The shim, signed with a key trusted by the firmware, enables the loading and execution of an unsigned bootloader or kernel.
The critical vulnerability tracked as CVE-2023-40547 (CVSS score: 9.8) resides in HTTP boot support and could lead to Secure Boot bypass.
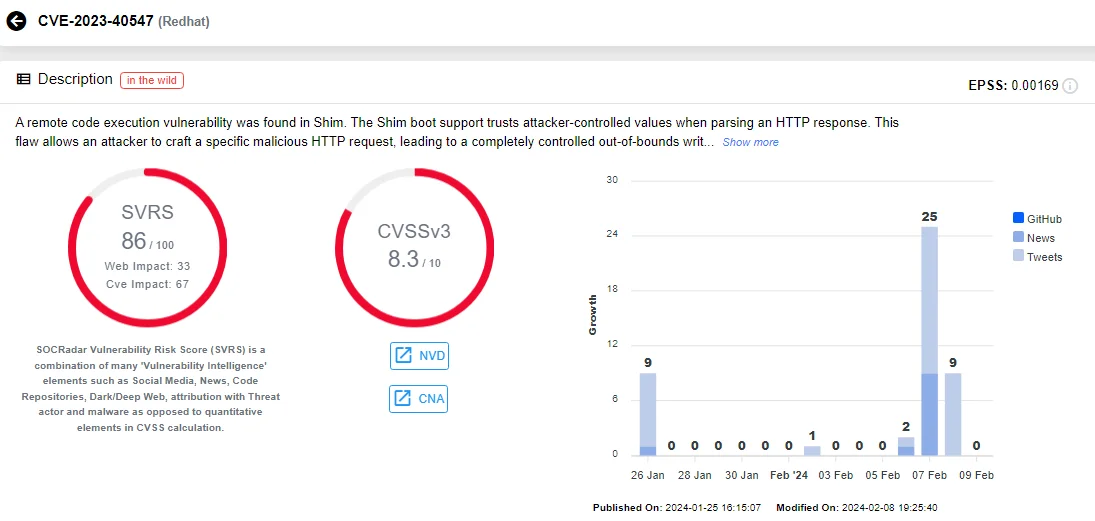
SOCRadar Vulnerability Card for CVE-2023-40547
The vulnerability occurs because the shim boot support trusts attacker-controlled values when parsing an HTTP response. This allows an attacker to craft a specific malicious HTTP request, leading to an out-of-bounds write that can result in a complete system compromise.
The critical vulnerability, discovered by Bill Demirkapi from MSRC, is warned to impact every Linux boot loader signed in the past decade.
Possible Attack Scenarios
Attackers can conduct a Man-in-the-Middle (MiTM) attack, intercepting HTTP traffic between victims and servers during HTTP boot file serving, as highlighted by researchers. This exploit can occur from any network segment between the victim and the legitimate server.
In another tactic, attackers with privileges can manipulate EFI Variables or the EFI partition using a live Linux USB stick. By altering the boot order, they can load a remote and vulnerable shim on the system, enabling the privileged code execution from the remote server without disabling Secure Boot.
Furthermore, attackers on the same network can manipulate PXE to chain-load a vulnerable shim bootloader, which could provide privileged access and bypass kernel and OS controls.
The maintainers of shim addressed the critical CVE-2023-40547 vulnerability alongside CVE-2023-40546, CVE-2023-40548, CVE-2023-40549, CVE-2023-40550, and CVE-2023-40551 with the release of shim version 15.8.
Ivanti Discloses Critical XXE Vulnerability, CVE-2024-22024: Urgent Patching Required
Ivanti has disclosed another vulnerability, found during their investigation into issues affecting Ivanti Connect Secure, Ivanti Policy Secure, and ZTA gateways, urging immediate patching from users.
The latest vulnerability, CVE-2024-22024, rated with a CVSS score of 8.3, is an XML External Entity (XXE) vulnerability in the SAML component, impacting Ivanti products’ versions 9.x and 22.x. Successful exploitation can grant attackers access to restricted resources without authentication.
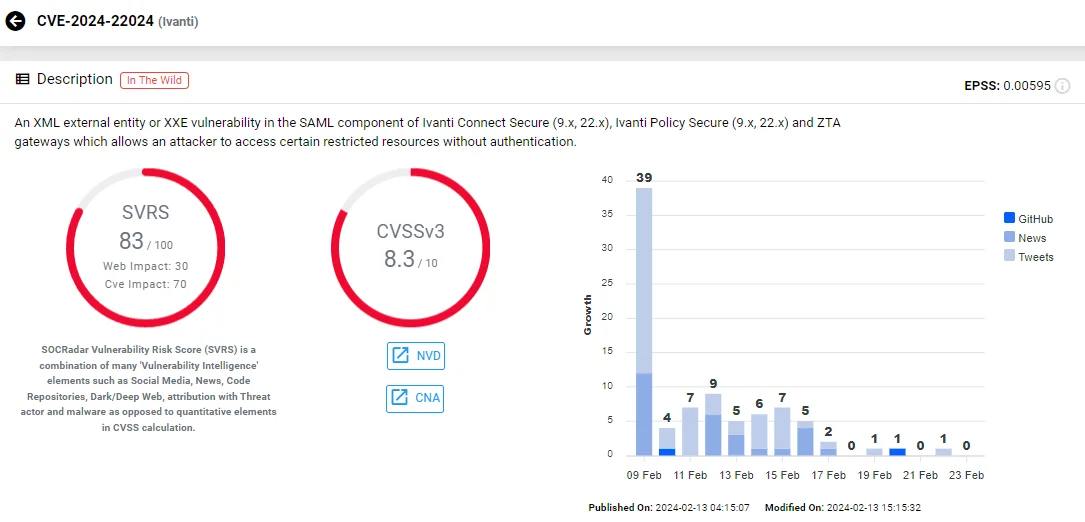
SOCRadar Vulnerability Card for CVE-2024-22024
While Ivanti reports there is no evidence of exploitation, it also emphasizes the need for prompt action to ensure protection.
Despite Ivanti’s advisory, some of the security community claims the new vulnerability (CVE-2024-22024) is exploited, reflecting their concerns on platforms such as X (formerly Twitter) and Mastodon.
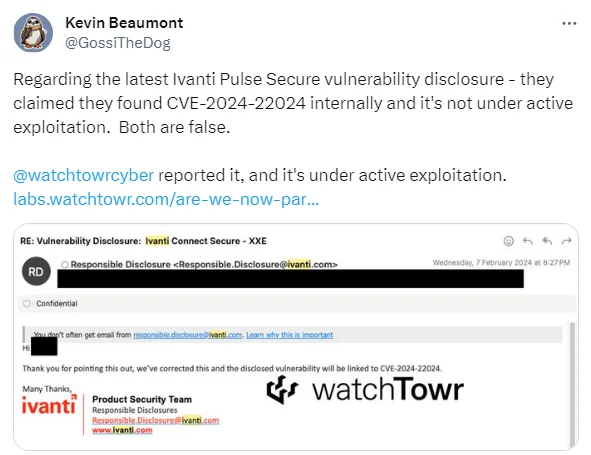
The vulnerability is reportedly under active exploitation (X)
Another Twitter user suggests monitoring Ivanti Pulse outgoing connections in DNS, firewall, proxy, and other logs. They have shared Indicators of Compromise (IOCs) to detect compromise. Breached Ivanti Pulse appliances reportedly send DNS queries to the following domains:
- *[.]oastify[.]com – DNS query type A
- *[.]burptest[.]tssrt[.]de – DNS query type A
- 255[.]255[.]255[.]255[.]in-addr[.]arpa – Type PTR
Last week, two other vulnerabilities were found, with one identified as CVE-2024-21893 being exploited in attacks on Ivanti customers, including government agencies globally. The vulnerabilities prompted CISA to direct all U.S. federal civilian agencies to disconnect Ivanti Connect Secure and Policy Secure products within 48 hours.
For more details, refer to our blog post: Vulnerability in Ivanti Connect Secure, Policy Secure, and Neurons for ZTA Exploited (CVE-2024-21888, CVE-2024-21893)
Scanning Activity Detected for CVE-2024-22024 in Ivanti; Thousands of Instances Are Still Vulnerable
A February 14 report revealed that scanning activity targeting the CVE-2024-22024 vulnerability in Ivanti has shot up. Many instances remain unpatched against this vulnerability, making them vulnerable to potential threat actors who seem interested in exploiting it.
Since the first PoC exploit for the vulnerability was published on February 9, researchers have observed an increase in scanning activity, peaking on February 11 and declining in subsequent days. Researchers reported that the activity on this specific date originated from 11 countries and 80 different IP addresses, and involved 240,000 requests.
Added to that, Shadowserver tweeted that they improved their scans and discovered approximately 3,900 instances of unpatched Ivanti Connect Secure VPNs that are still vulnerable to CVE-2024-22024.
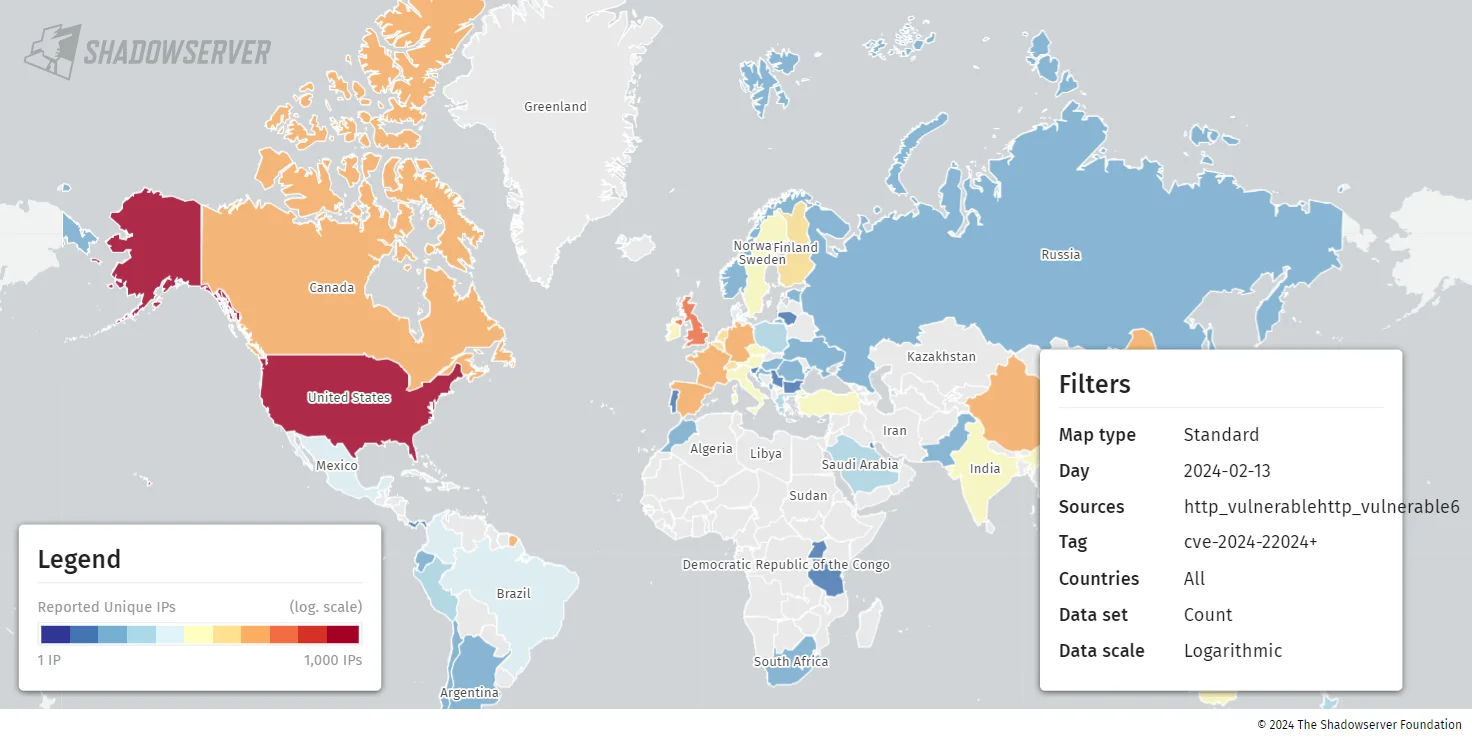
Map of instances that are still vulnerable to CVE-2024-22024 (Shadowserver)
Researcher Yutaka Sejiyama (@nekono_naha) highlighted the vulnerability’s patch status on X (Twitter), including the top 20 countries with the most Ivanti/Pulse Secure instances, as well as the number of instances that have been patched.
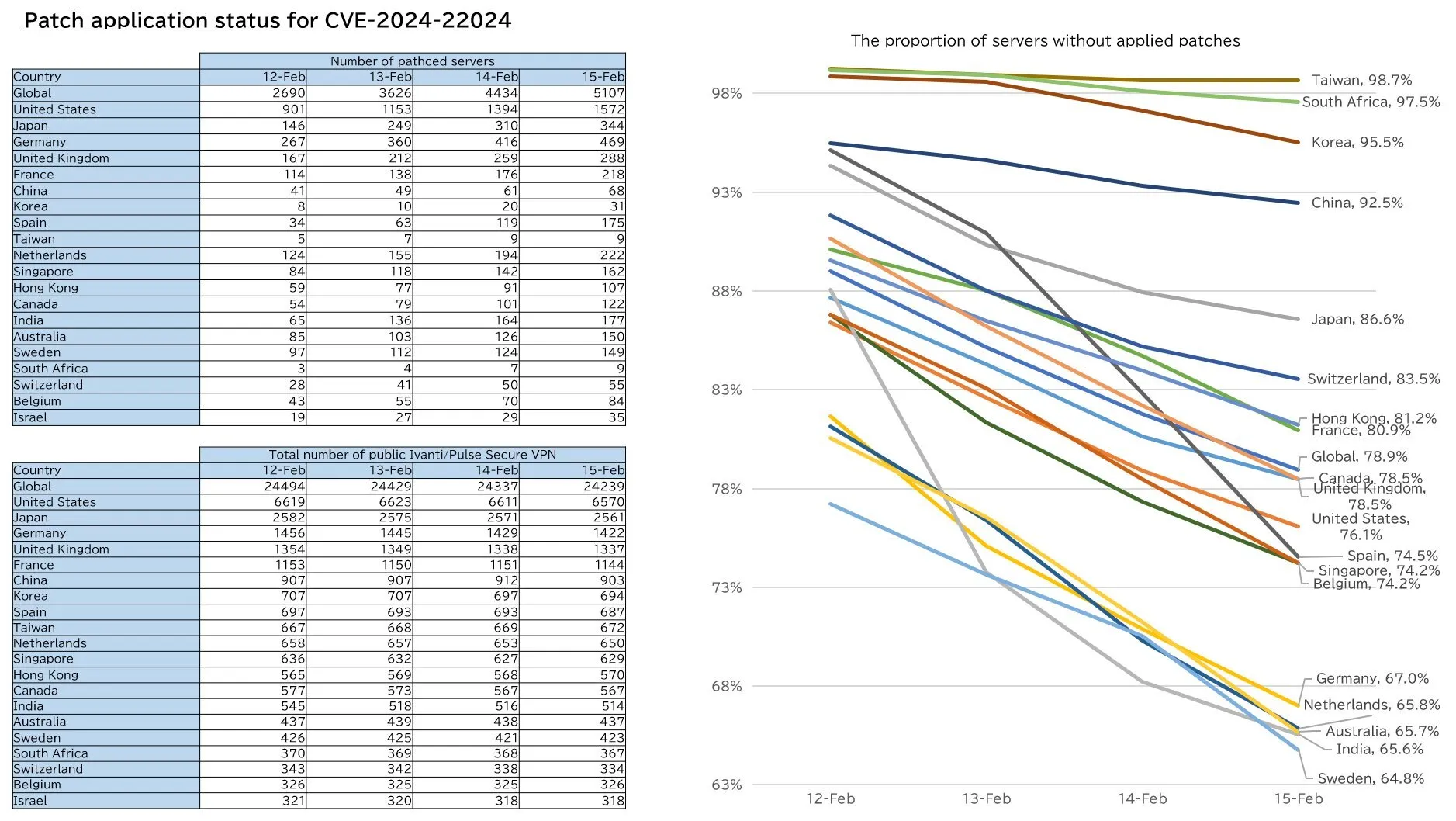
The vulnerability is reportedly under active exploitation (X)