
Sales of bfBot Stealer & Knight Ransomware Source Code, Dior Vulnerabilities, Passport Leaks, and More
The SOCRadar Dark Web Team exposed alarming sales, from ransomware source codes to leaked passports. Knight 3.0 ransomware’s source code, Dior vulnerabilities, passport leaks, and bfBot Stealer are among the critical discoveries of last week.
With security breaches ranging from luxury brands to passport data, the digital underworld’s threats intensify, urging robust defenses and heightened vigilance.
Receive a Free Dark Web Report for Your Organization:
Source Code of Knight Ransomware is on Sale
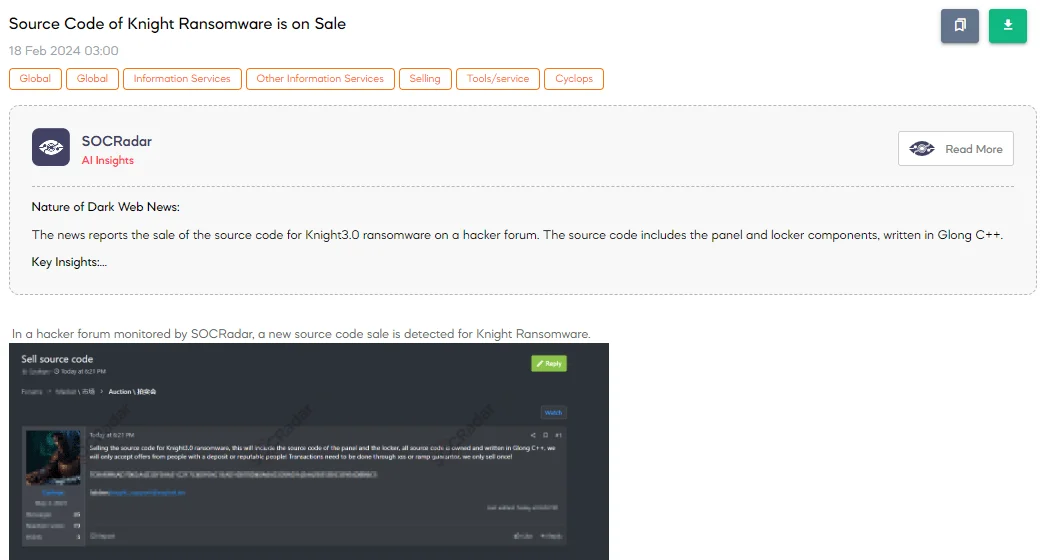
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to be selling the source code for Knight 3.0 ransomware. This ransomware package includes the control panel and the encryption (“locker”) mechanism. The threat actor states that the entire source code is proprietary, written in a language referred to as “Glong C++,” which may be a typographical error or slang for a version of C++.
The condition for sale is quite strict, with the seller requiring potential buyers to either make a deposit or have a reputable standing in the community. Furthermore, transactions are to be conducted through trusted intermediaries on deep/dark web forums like XSS or RAMP, indicating a preference for security and anonymity in the sale process. The seller also emphasizes that the source code will be sold only once, suggesting an attempt to maintain the exclusivity and potentially high value of the ransomware.
Vulnerabilities of Dior are on Sale
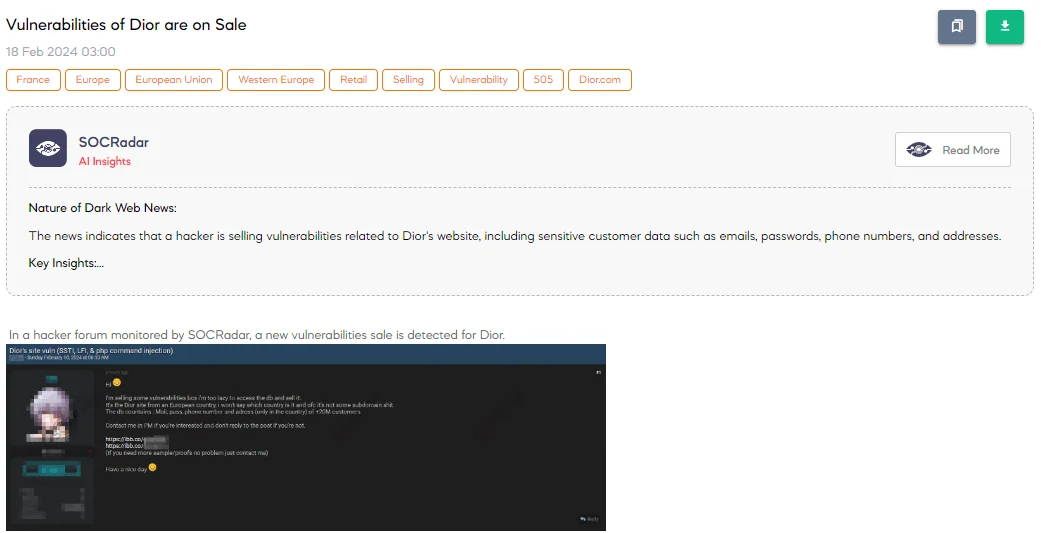
SOCRadar Dark Web Team has uncovered a post on a hacker forum where a threat actor claims to be selling vulnerabilities for Dior, the renowned French luxury fashion brand, specifically targeting an unnamed European country’s main site rather than any subdomains. The seller claims to possess vulnerabilities that could potentially allow access to Dior’s database, which reportedly contains personal data of over 20 million customers, including emails, passwords, phone numbers, and addresses (limited to the country of the affected Dior site). The threat actor is offering these vulnerabilities for sale, stating a preference for Private Messaging (PM) for those interested and discouraging public responses to the post.
The fact that the threat actor chooses to sell these vulnerabilities instead of directly exploiting them for access to the database suggests a potentially broader risk landscape where multiple threat actors could buy this information and exploit it in various malicious ways, from targeted phishing attacks to identity theft.
Passports of Citizens of Many Countries are Leaked
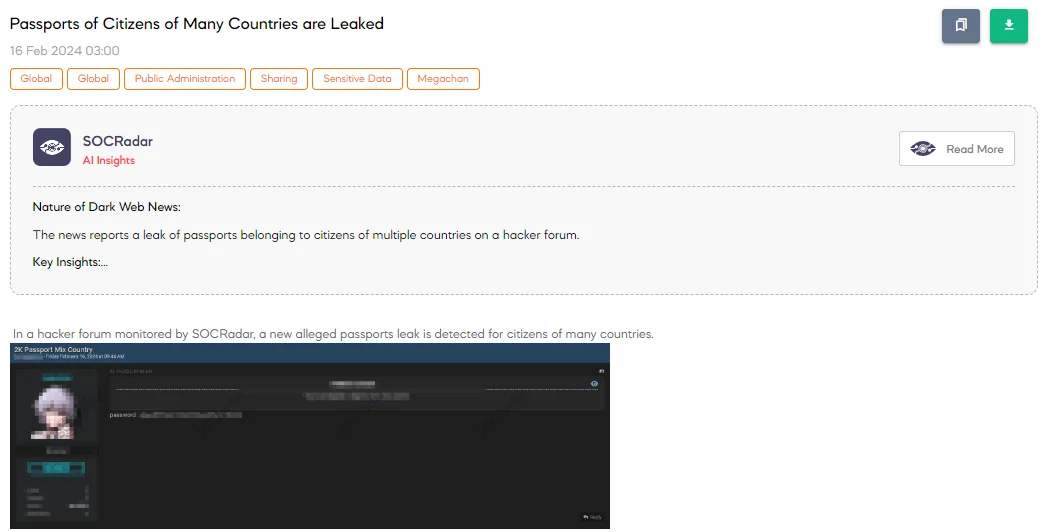
The SOCRadar Dark Web Team has discovered a post on a hacker forum where a threat actor is claiming to have accessed and is distributing passports from citizens of multiple countries. The leak reportedly includes around 2,000 passports and is being offered without charge. This situation represents a severe privacy breach, exposing individuals to potential risks of identity theft, fraud, and other malicious uses of their personal information.
bfBot Stealer Service Sale is Detected
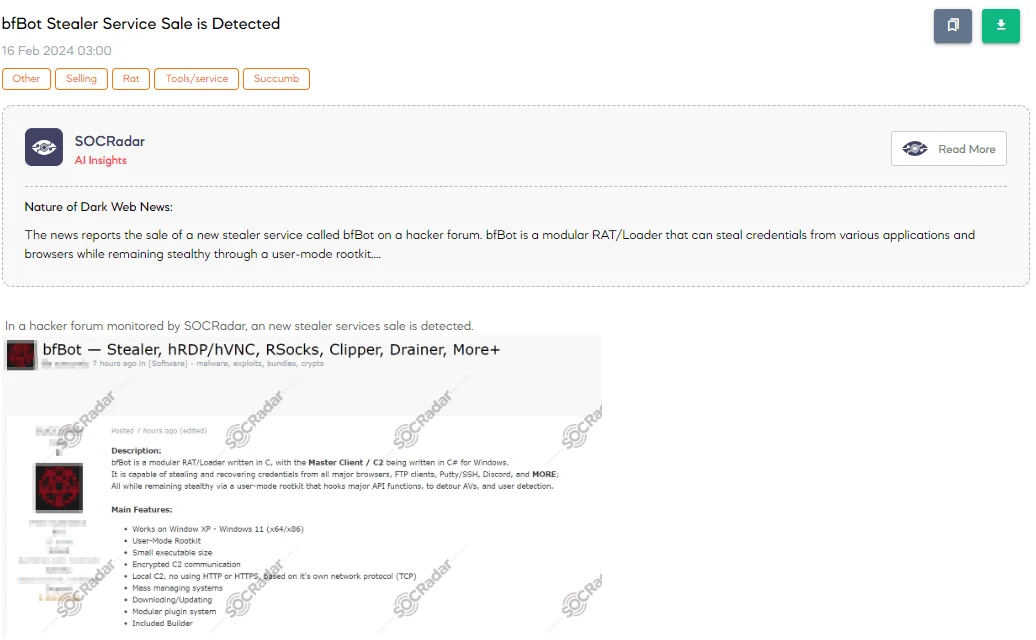
On February 16, a SOCRadar Dark Web Analyst detected a sale for a malicious tool named bfBot on a hacker forum, advertised by a threat actor. Claimed features of bfBot include its design as a modular Remote Access Trojan (RAT)/Loader with stealth capabilities, targeting Windows systems from XP through Windows 11. It’s engineered to steal credentials from major browsers, FTP clients, and applications like Discord and Putty/SSH, leveraging a user-mode rootkit to evade antivirus detection.
The tool supports encrypted Command and Control (C2) communication and includes a variety of modules for extended functionalities such as virtual network computing (hVNC/hRDP), reverse proxy, and more.BfBot, offered at $500, poses a significant security threat with its claimed capabilities, emphasizing the importance of robust defenses against such sophisticated malware.
Unauthorized RDP Access Sale is Detected for a German Commercial Company
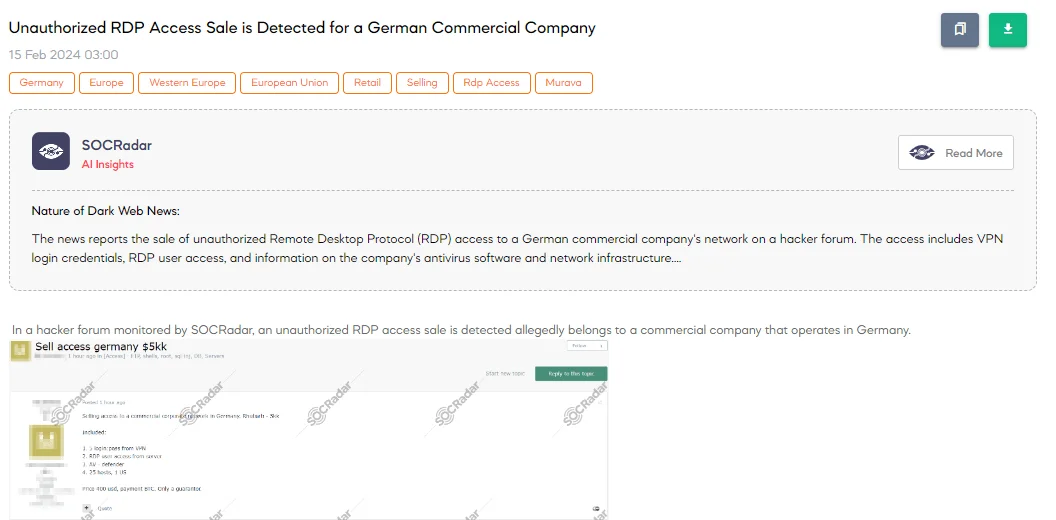
A SOCRadar Dark Web Analyst has detected a post on a hacker forum where a threat actor is claiming the sale of unauthorized RDP access to a German commercial company’s network. Offered at $400 in Bitcoin, the access includes credentials for five VPNs, Remote Desktop Protocol (RDP) user access, and involvement of 25 hosts, including one in the US, with Windows Defender noted as the antivirus solution.
Unauthorized VPN Access Sale is Detected for a South Korean Company
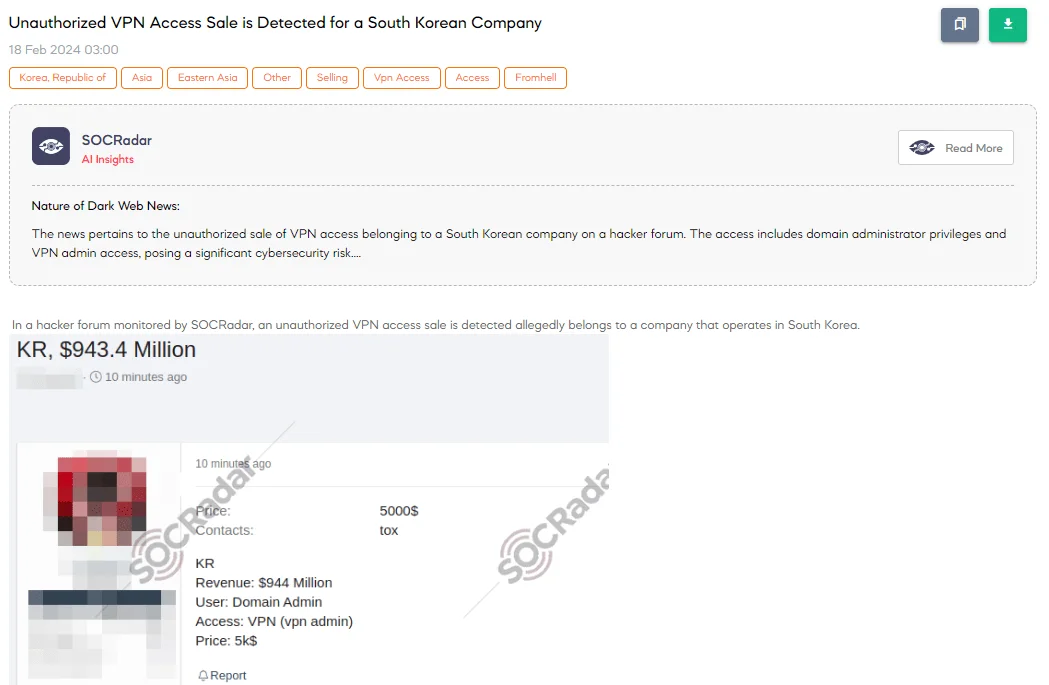
The SOCRadar Dark Web Team came across a post on a hacker forum where a threat actor is claiming to sell unauthorized VPN access that allegedly belongs to a South Korean company. The company in question is reported to have a revenue of $944 million, indicating it is a significant player in its industry. The access being sold provides VPN administrator privileges, suggesting the buyer would gain extensive control over the company’s network. The asking price for this unauthorized access is set at $5,000, and the seller has chosen Tox for communication, a platform known for its secure, encrypted messaging services.
8K OWA Accesses are on Sale
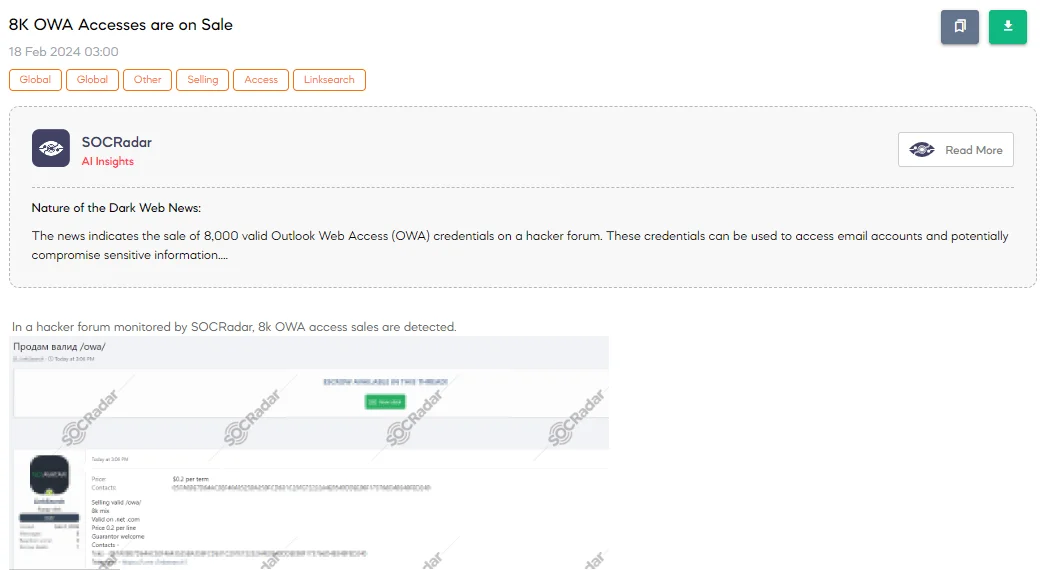
The SOCRadar Dark Web Team has uncovered a claim on a hacker forum where a threat actor is advertising the sale of 8,000 Outlook Web Access (OWA) credentials. These credentials are described as a mixed batch, presumably valid across various domains, mentioned explicitly as “.net” and “.com.” The pricing set by the threat actor is notably low, at $0.2 per credential, suggesting a bulk sale aimed at attracting buyers looking for mass access to email accounts for potentially malicious purposes.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































