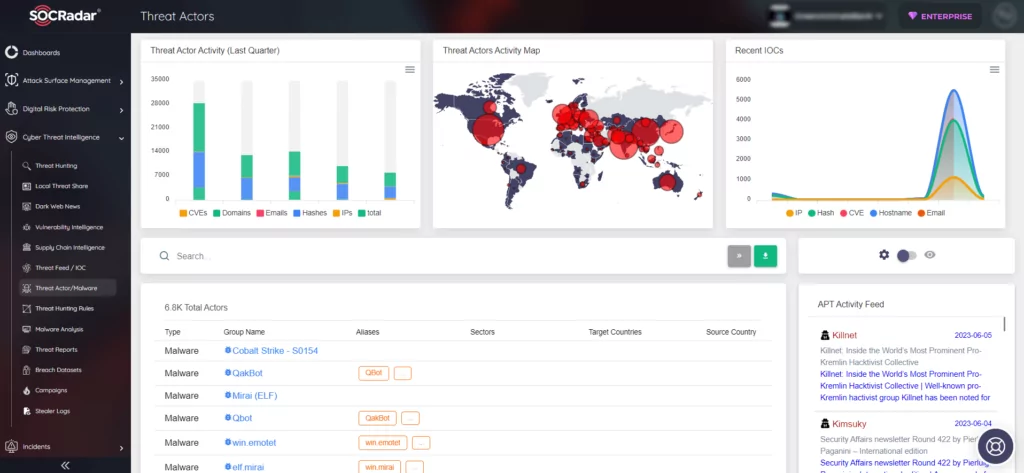
Cyclops Ransomware: Cross-Platform Threat with RaaS and Advanced Features
[Update] August 7, 2023: After officially rebranding as Knight, Cyclops has shared their new stealer named “Knight stealer” on a hacking forum. See more under: “Cyclops Advertises the New Knight Stealer.”
[Update] August 3, 2023: Cyclops ransomware has undergone a rebranding, now operating under the name “Knight.” Added under the subheading “Cyclops Ransomware Operation Rebrands with v2.0: Knight Ransomware.”
[Update] July 27, 2023: Added the subheading: “Cyclops Ransomware Operation Rebrands with v2.0: Knight Ransomware.”
Researchers have recently discovered a new ransomware developer named Cyclops group. This group takes pride in creating ransomware that can infect three significant platforms: Windows, Linux, and macOS. They offer ransomware utilities as a service, which is referred to as Ransomware-as-a-Service (RaaS).
Alongside the ransomware service, the group has shared a separate binary with the specific purpose of stealing sensitive data, including infected computer names and various processes.
The Cyclops group actively promotes their offerings on hacker forums and seeks a share of the profits from users who use their malware.
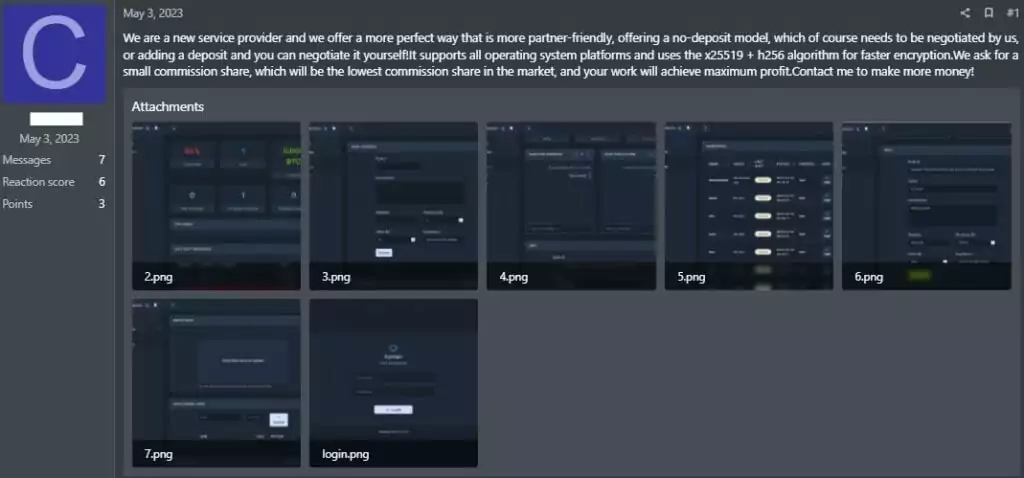
Offerings of the Cyclops Ransomware & Stealer
Cyclops has a dedicated panel for distributing their ransomware across Windows, Linux, and MacOS operating systems. This panel has separate binaries for the additional stealer component, catering specifically to Linux and Windows.
The Windows stealer extracts system information and creates password-protected zip files containing targeted files.
The Linux stealer performs a similar function, creating password-protected zip files in the /tmp directory.
The website also operates similarly to a bank. It has a financial section allows Cyclops attackers to withdraw the ransom payments they receive. The developers of Cyclops actively address any issues that arise on this platform and reward valuable feedback.
The Windows Ransomware Binary of Cyclops
Researchers of Uptycs analyzed the Cyclops ransomware binaries and discovered a builder binary and a readme.txt file in the extracted archive file.
The threat actor provided a builder ID for creating a ransom payload called locker[.]exe, which is designed to infect both local and networked machines. The text file that comes with it contains instructions for running the payload with and without command line arguments, as shown below:
locker[.]exe
run without command line arguments.
lock all disk(local and network)
locker[.]exe -m local
only local disk
locker[.]exe -m net
only network disk
locker[.]exe -p path.txt
path.txt
E:Data
D:Data
locker[.]exe -h host.txt
host.txt
servername1
servername2
servername3
servername4
servername is the DNS or NetBIOS name of the remote server.The Cyclops ransomware payload scans and identifies processes running on the victim’s machine, terminating any processes that could interfere with the encryption of targeted files.
Researchers discovered that using the GetLogicalDriveStrings API, the payload retrieves information about the logical drives in the system and then enumerates the folders, dropping a ransom note file named “How To Restore Your Files.txt” onto the disk.
Before encrypting a file, the payload checks if its file extension matches a predefined list. If not, the file is encrypted and given a .CYCLOPS extension.
The attacker gathers information about shadow copies on the victim’s system, including their IDs, creation times, and volume names. Then, using a specific ID, the payload deletes a chosen shadow copy by running a command through the Windows Management Instrumentation command line utility.
The ransom note of Cyclops provides instructions for the victim to visit an Onion site, where there may be a chance to recover their encrypted files.
Overview of Linux and macOS Versions of Cyclops Ransomware
The Linux version is compiled in Golang and uses CGO with C integration. The binary file is stripped of function names to make reverse engineering challenging.
It encrypts files with specific extensions, excluding files in certain directories. A ransom note is dropped in each encrypted folder, and a statistical report is generated.
The encryption process involves a combination of asymmetric and symmetric encryption, using algorithms such as ECDH on Curve25519, SHA512, and ChaCha.
The macOS version is a Golang-compiled mach-O binary. It offers options for file encryption and places encrypted files in a designated folder along with a ransom note.
Similarities with Babuk and LockBit Ransomware
Cyclops ransomware shares similarities with Babuk and LockBit ransomware in terms of encryption algorithms and string obfuscation techniques.
Both Cyclops and Babuk ransomware utilize Curve25519 and HC-256 for Windows encryption. Additionally, both ransomware employ the combination of Curve25519 and ChaCha algorithms.
In Cyclops ransomware, the executable strings are encoded and stored as stack strings. These encoded strings are dynamically decoded during runtime using various computational operations such as addition, subtraction, shifting, XORing, and more. A similar encoding approach was also observed in LockBit 2.0 ransomware.
Cyclops Ransomware Operation Rebrands with v2.0: Knight Ransomware
The Cyclops ransomware group recently announced the closure of their old dark web portal, as they prepare to roll out version 2.0. Alongside this update, they also revealed their plan to rename themselves as “Knight” upon the release of version 2.0 and their new site.
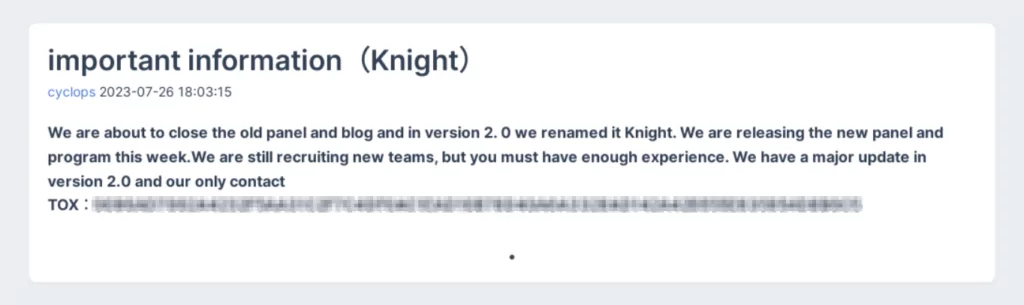
Furthermore, the group actively seeks to expand their operations. They shared a TOX chat link to recruit new threat actors, specifically those with “enough experience.”
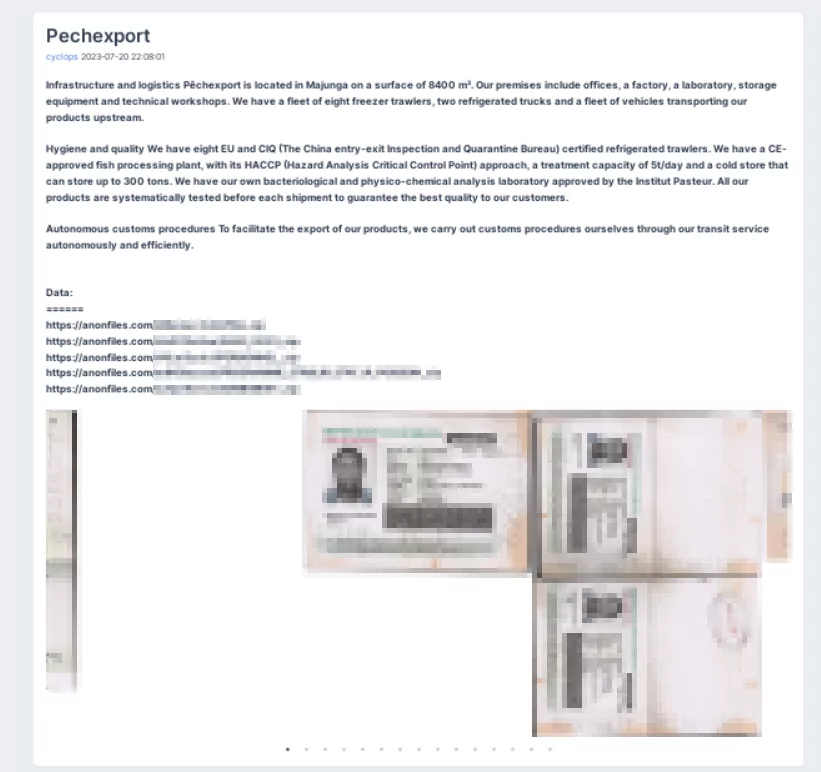
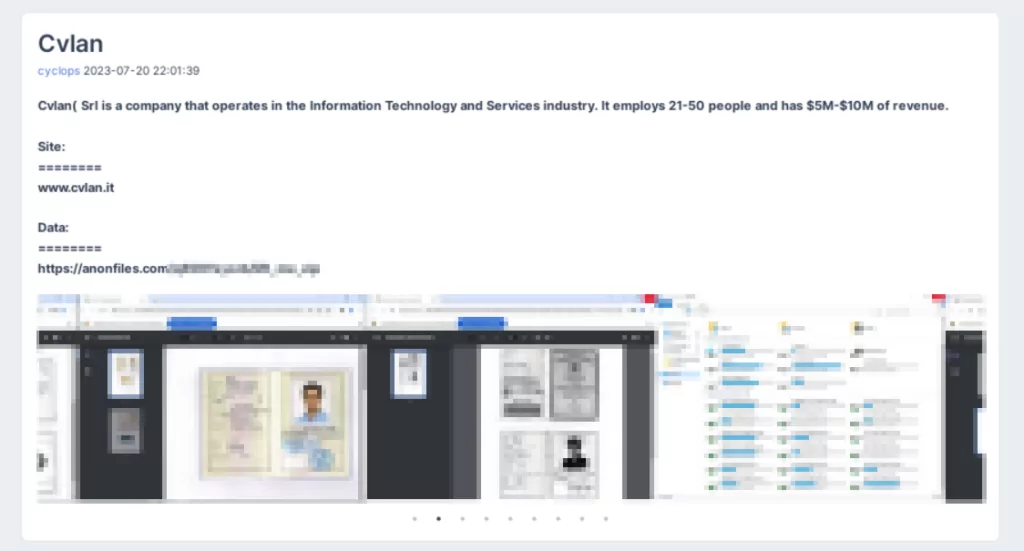
The group’s latest hacking claims were on July 20. One of the targets was Pechexport, a manufacturer based in Madagascar, while the other claim was on Cvlan SRL, an information technology company in Italy. The documents shared regarding these two companies appear to contain employee information.
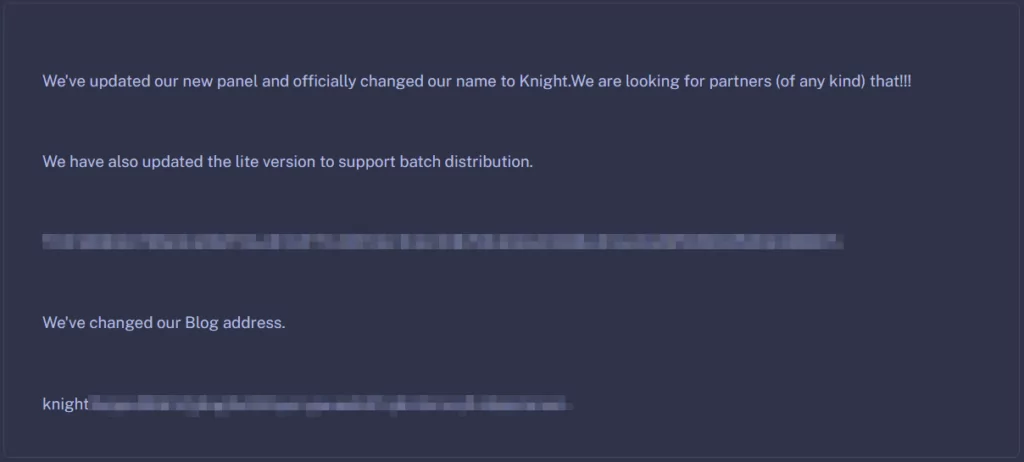
As of August 2023, Cyclops ransomware has undergone the planned rebranding, now operating under the name “Knight.” With the rebranding, they have launched a new panel, updated their lite version to support batch distribution, and introduced a new Blog address.
Cyclops Advertises the New Knight Stealer
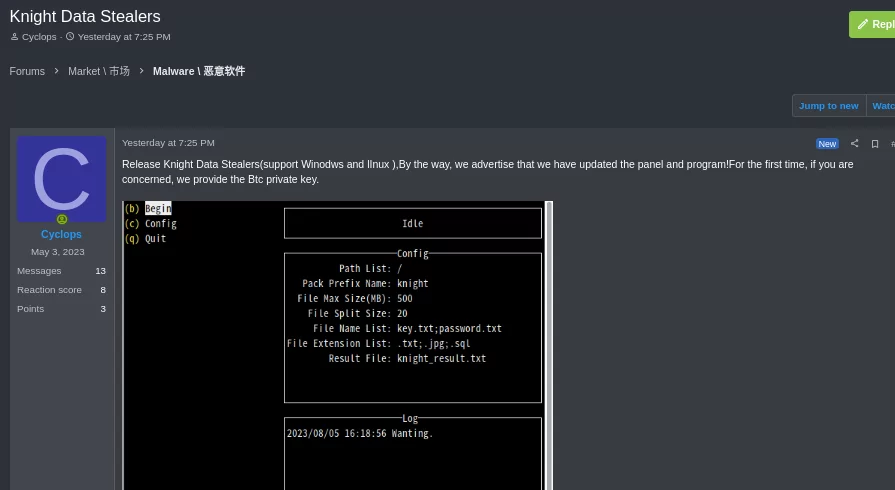
After officially rebranding as Knight, Cyclops has shared their new stealer named “Knight Data Stealer” on a hacking forum.
While the threat actor has not disclosed many details, they stated that the Knight stealer is compatible with both Windows and Linux operating systems. They have also provided the stealer interface in the post, as shown below:
How Can SOCRadar Help?
SOCRadar’s Threat Feed and IoC Management module helps organizations manage their threat intelligence feeds and indicators of compromise (IoCs).

Also, SOCRadar’s Threat Actor Tracking module provides organizations with a comprehensive view of known and emerging threat actors, including their TTPs, IOCs, and infrastructure. This information can be used to identify and respond to threats more quickly and effectively.