
Critical Patch for Veeam Backup Enterprise Manager (VBEM): CVE-2024-29849 Could Allow Account Takeover
[Update] June 10, 2024: “PoC Exploit Released for the Critical CVE-2024-29849 Vulnerability in Veeam”
Veeam issued patches for a set of vulnerabilities in its Veeam Backup Enterprise Manager (VBEM), a component of the widely used Veeam Backup & Replication suite. One of these vulnerabilities has been categorized as critical due to its potential to enable unauthenticated attackers to take over user accounts.
Veeam Backup Enterprise Manager serves as an administrative console designed to help the management of the tasks relevant to Veeam Backup & Replication across an organization’s backup infrastructure. The application’s role in controlling sensitive backup operations makes it an appealing target for threat actors.
This disclosure is particularly significant considering the extensive deployment of Veeam’s solutions across major global enterprises, including 74% of the Forbes Global 2000 companies such as Shell, Airbus, Volkswagen Group, and Fujifilm.
What Is the Critical CVE-2024-29849 Flaw in Veeam Backup Enterprise Manager?
The critical vulnerability, tagged as CVE-2024-29849, carries a severity score of 9.8 on the CVSS scale. It affects Veeam Backup Enterprise Manager (VBEM), which is not enabled by default.
The fact that Veeam Backup Enterprise Manager is not enabled by default does provide some mitigation, as only those environments with this component activated are exposed to the risk.
CVE-2024-29849 allows unauthenticated attackers to log in to the VBEM web interface as any user, including administrators. This could potentially lead to a complete takeover of the backup and replication management system. An attacker with this type of access would be able to manipulate backups or even access sensitive data handled by the backup manager.
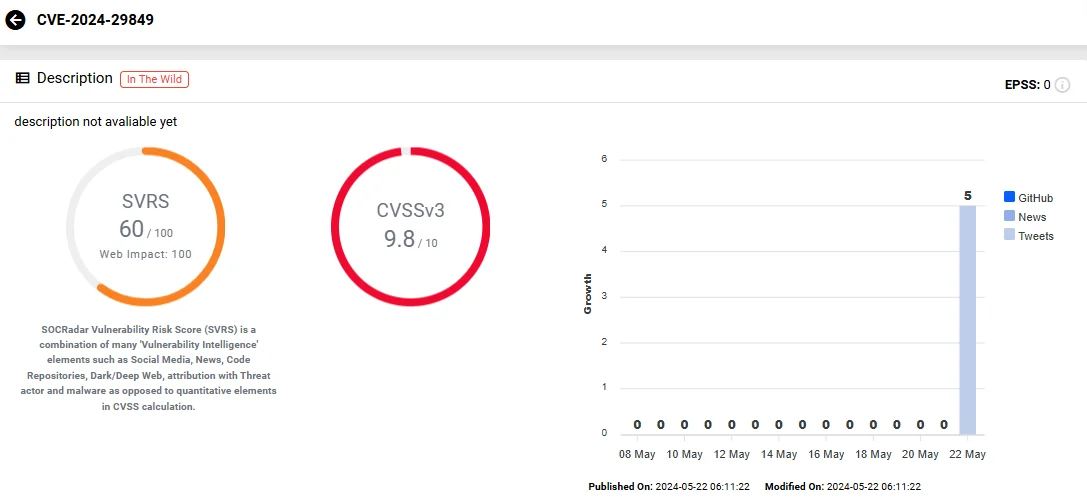
Vulnerability card of CVE-2024-29849 affecting VBEM (SOCRadar Vulnerability Intelligence)
PoC Exploit Released for the Critical CVE-2024-29849 Vulnerability in Veeam
A Proof-of-Concept (PoC) exploit is now available for the critical Veeam Backup Enterprise Manager (VBEM) authentication bypass vulnerability, CVE-2024-29849.
Researcher Sina Kheirkhah (@SinSinology) has announced the development of an exploit through the social platform X, providing a link to the exploit’s GitHub repository.
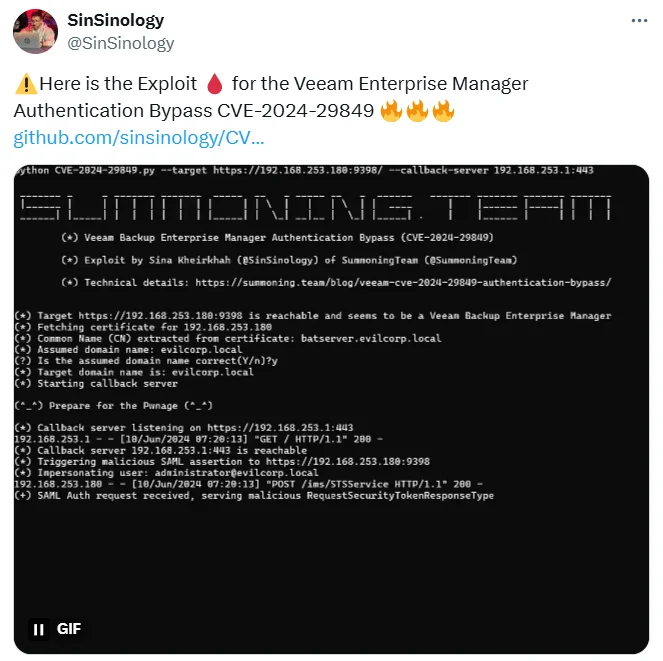
PoC announced by researcher @SinSinology on X
The exploit allows to bypass authentication and impersonate users, gaining unauthorized access to sensitive data. Potential attackers can use such an exploit code to send a malicious SAML assertion, which tricks the system into granting access without proper credentials.
Veeam’s Advisory Lists High-Severity Vulnerabilities: CVE-2024-29850 and CVE-2024-29851
In addition to the critical CVE-2024-29849, Veeam’s security advisory details three other vulnerabilities in Veeam Backup Enterprise Manager.
These include CVE-2024-29850 and CVE-2024-29851, both classified as high-severity threats, and CVE-2024-29852, which concerns backup session log exposure but is less severe.
CVE-2024-29850 (CVSS: 8.8):
This high-severity vulnerability presents a dangerous vector for account takeover through NTLM relay. In environments where NTLM authentication is utilized, this vulnerability could allow attackers to intercept and relay authentication sessions, effectively granting them unauthorized access to the VBEM system.
CVE-2024-29851 (CVSS: 7.2):
Another concerning vulnerability, CVE-2024-29851, allows a high-privileged user to steal the NTLM hash of the VBEM service account if the service account used by VBEM is configured to use credentials other than the default Local System account.
SOCRadar’s Vulnerability Intelligence can aid in monitoring these CVEs and other exploitation trends. The feature provides an extensive database of the latest security vulnerabilities. This resource is invaluable for organizations seeking to stay informed about new threats as soon as they are discovered. By utilizing this feature, your security team can quickly learn about vulnerabilities relevant to your environment and understand their potential impact.
Follow CVE and exploitation trends with SOCRadar’s Vulnerability Intelligence
Which Veeam Backup & Replication Versions Are Affected?
Veeam listed a wide range of its Backup & Replication versions as susceptible to the vulnerabilities recently identified:
- 5.0
- 6.1
- 6.5
- 7.0
- 8.0
- 9.0
- 9.5
- 10
- 11
- 12
- 12.1
How to Secure Veeam Backup & Replication?
To address these vulnerabilities, Veeam released the Veeam Backup Enterprise Manager (VBEM) version 12.1.2.172. This version is integrated with Veeam Backup & Replication 12.1.2 (build 12.1.2.172).
For administrators who cannot immediately upgrade to the latest version, there are temporary mitigation steps to help secure their systems:
- Temporarily stop and disable the VeeamEnterpriseManagerSvc (VBEM) and VeeamRESTSvc (Veeam RESTful API) services to reduce the risk of exploitation. However, it is crucial to keep the ‘Veeam Backup Server RESTful API Service’ running to avoid disrupting other functionalities.
- If VBEM is not actively used, it can be safely uninstalled. This removal effectively eliminates any issues related to the vulnerabilities. You can follow Veeam’s guide to uninstall VBEM.
Furthermore, Veeam notes that VBEM supports Veeam Backup & Replication servers that might be running on versions older than itself. Consequently, if VBEM is installed on a dedicated server, it can be upgraded to version 12.1.2.172 independently, without updating the Veeam Backup & Replication servers it manages.
Stay on Top of the Landscape with SOCRadar, Address Security Vulnerabilities Easily
Staying ahead of potential security vulnerabilities is essential for protecting your organization’s digital assets. To enhance your organization’s vulnerability management practices, SOCRadar offers comprehensive tools, such as Vulnerability Intelligence and Attack Surface Management (ASM).
With real-time alerts and updates, SOCRadar ensures that your organization remains proactive rather than reactive when it comes to cybersecurity. These alerts enable your security team to address vulnerabilities promptly before they can be exploited by malicious actors.
SOCRadar’s Attack Surface Management (ASM) module continuously monitors the digital assets within your organization’s ecosystem, identifies security gaps, and provides actionable insights. By doing so, it helps prevent exploitations and mitigate risks associated with external attack vectors.
Monitor Company Vulnerabilities via SOCRadar’s ASM
By integrating SOCRadar’s advanced security features into your cybersecurity strategy, your organization can enhance its defensive measures and ensure a secure and resilient digital infrastructure.



































