
Major Cyber Attacks in Review: June 2024
June 2024 has been a whirlwind of significant cyber attacks targeting high-profile organizations worldwide. Following the ongoing Snowflake-related issues, the past month has seen cases such as a TeamViewer data breach by a notorious Russian espionage group, massive Ethereum and Bitcoin thefts, and the sprawling Polyfill supply chain attack affecting hundreds of thousands of websites.
These incidents have kept the cybersecurity world on high alert, and showcased a range of methodologies, from sophisticated intrusions to clever extortion tactics, offering critical lessons for enhancing cybersecurity strategies.
Without delay, let’s review the major cyber attacks of June 2024 to grasp their scope and far-reaching implications.
TeamViewer Data Breach by APT29
On June 26, 2024, TeamViewer detected an irregularity in its internal corporate IT environment, prompting an immediate investigation.
The company assured that the product environment and customer data remain unaffected. Nevertheless, the breach raised significant concerns due to TeamViewer’s widespread use on over 2.5 billion devices, posing a risk of compromising vast amounts of sensitive information and critical systems globally.

Explore the Dark Web Profile of APT29/CozyBear
Health-ISAC reported that a trusted intelligence partner identified APT29, also known as CozyBear, as the culprit behind the breach.
The Polyfill Supply Chain Attack
Researchers have warned about a supply chain attack originating from the Polyfill[.]io service, impacting over 100,000 websites. The attack began after a Chinese company, Funnull, acquired Polyfill’s domain and GitHub account in February 2024, modifying the script to redirect users to malicious sites.
The issue, initially reported on June 25, 2024, involved the distribution of malware through compromised domains. Any site using “cdn.polyfill.io” was affected, with the latest count of potentially affected hosts being over 380,000. Notably, the malicious code linked to these attacks had been circulating on Chinese forums since June 2023.
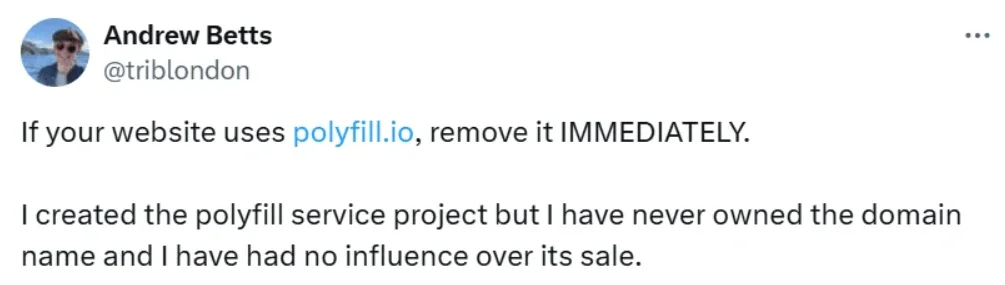
A Tweet by Polyfill’s original author (X)
Google blocked Google Ads for affected e-commerce sites and identified additional sites causing unwanted redirects. Throughout the ordeal, Cloudflare created a secure mirror and automatically redirected Polyfill.io links, while Namecheap deactivated new domains launched by the attackers.
The owners of Polyfill continue to create new domains, and you can follow the whole incident through our blog post: “Polyfill Fuels Supply Chain Concerns with Malicious Redirects: +100,000 Websites Affected.”
$20 Million Ethereum (ETH) Theft Targeted UwU Lend

A visual representing Ethereum (ETH)
UwU Lend, a DeFi platform, reported a theft of nearly $20 million in Ethereum (ETH).
In June 2024, blockchain security firms identified suspicious activity on the platform, with $19.3 million worth of ETH being siphoned. UwU Lend responded on social media, informing users that operations were temporarily paused while the team investigated.
Reportedly, the company has since made an offer to the hacker responsible for the theft.
Information Stolen from The New York Times Contributors Surfaced on 4Chan
In early June 2024, data related to The New York Times, including personal information of freelance contributors, was publicly leaked, prompting the media giant to send out notifications. A 270GB torrent file containing the stolen data was posted on the 4chan message board.
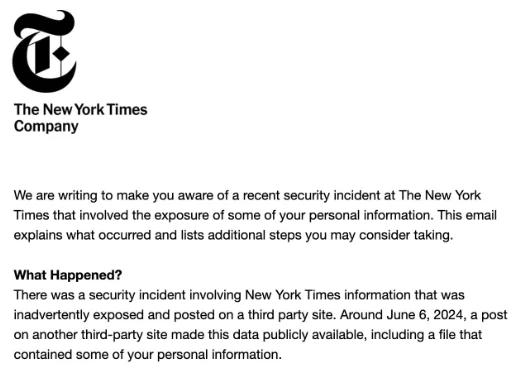
A part of the breach notification by The New York Times (X)
The breach occurred in January 2024 when attackers gained access to The New York Times’ GitHub repositories by exploiting exposed credentials. Fortunately, the newspaper’s internal systems and operations were not affected.
The compromised data includes first and last names, phone numbers, email addresses, mailing addresses, nationality, bios, website URLs, and social media usernames.
Threat Actor Offered 17 Million PandaBuy Records on Forum
The threat actor Sanggiero, associated with the group CyberNiggers, initially leaked 1.3 million PandaBuy user records and in June 2024, claimed to have the entire database of 17 million records for sale at $40,000.
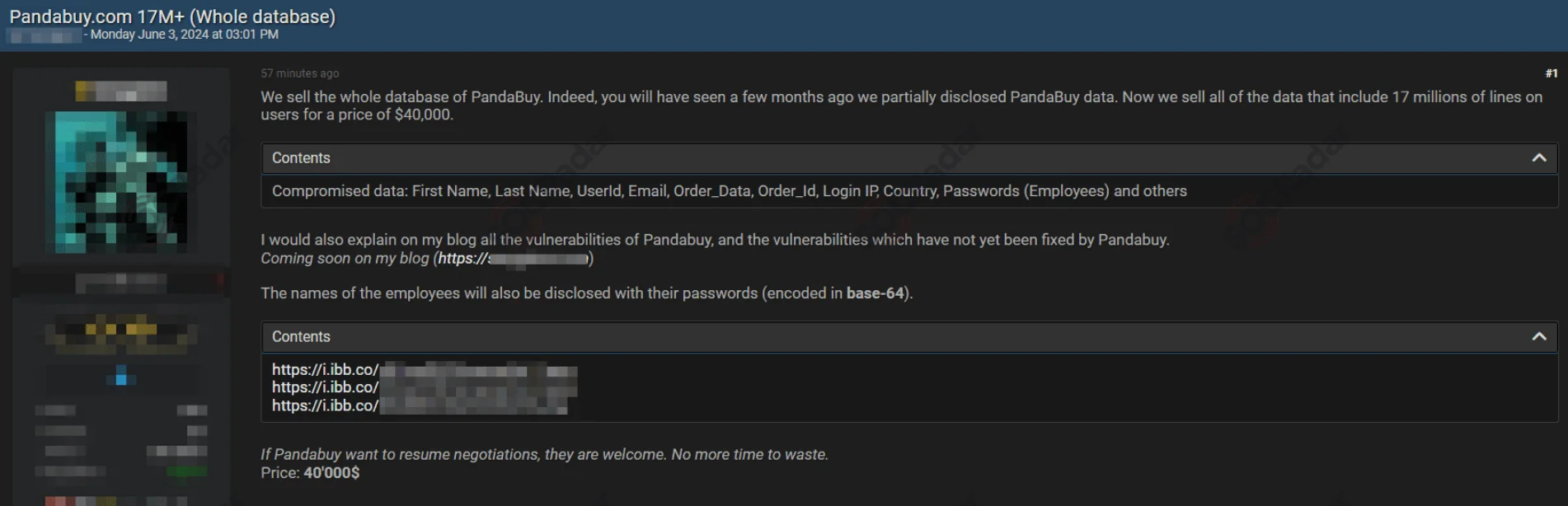
PandaBuy data sale post (SOCRadar Dark Web News)
The data allegedly includes first and last names, user IDs, emails, order details, login IPs, country information, and employee passwords.
Following these events, PandaBuy stated they had previously paid a ransom to prevent the stolen data from being leaked. However, the same threat actor has returned to extort the company again, now claiming possession of the full database.
Qilin Ransomware Attack Crippled Many Hospitals in London
A ransomware attack by the Russian cyber hacking group, Qilin, severely disrupted operations at multiple London hospitals.
The attack targeted Synnovis, a pathology services firm, leading to significant reductions in hospital capacity. This forced hospitals to declare a critical incident, resulting in many canceled operations and tests. Affected hospitals include King’s College Hospital, Guy’s and St Thomas’, Royal Brompton, Evelina London Children’s Hospital, and various primary care services across the city.
Despite the severity of the attack, Qilin’s data leak site remained inaccessible, and the group did not issue any statements.
For more on the Qilin ransomware operation, including TTPs and past events, visit SOCRadar’s Dark Web Profile.

SOCRadar Threat Actor Card of Qilin (Agenda) Ransomware
High-Profile Attack on Indonesia’s National Data Center Affected 200 Government Agencies
A major cyberattack, which occurred on June 20, targeted one of Indonesia’s critical data centers, encrypting government servers and causing widespread disruption.
The Indonesian government confirmed that Brain Cipher, a new and emerging ransomware operation, was responsible for the breach, which targeted Pusat Data Nasional (PDN) and subsequently affected over 200 government agencies.

Brain Cipher’s data leak site
Essential public services were severely impacted by the attack. Immigration services, passport control, event permit issuance, and various other online services experienced significant downtime.
Indonesia had been in the process of establishing national data centers aimed at securely storing government servers and hosting data for online services. The ransomware attack, however, brought these efforts to a standstill.




































