
Is Your Credit Card Info In Danger: 2024 Analysis of E-Commerce Websites in Stealer Logs
The security of sensitive data in e-commerce, such as email addresses and associated accounts, is critical. As we investigate the vulnerabilities and cyber threats that pervade the digital space, it becomes essential to understand the consequences of such exposures.
Our analysis focuses on stealer logs from major e-commerce platforms, specifically data from the first quarter of 2024. This provides an overview of the most recent cybersecurity challenges and trends affecting the industry.
While many people share their email addresses online without considering the risks, this seemingly harmless action can lead to exploitation. Even reputable websites may experience security breaches at some point. Cybercriminals exploit such data by using infostealer malware to steal valuable information. This not only threatens individual users, but it also tarnishes platform reliability and poses serious risks to business owners, whose sensitive information may end up in stolen logs.
Stealer logs, or hidden repositories containing stolen data such as payment card information and user credentials, are a significant threat to the e-commerce industry. These logs are frequently traded on dark web forums, becoming tools for cybercriminals to commit fraud and breaches. These activities have a far-reaching impact, threatening the integrity of numerous e-commerce sites.
This blog post utilizes the SOCRadar Threat Hunting module, an effective resource that enables defenders to proactively detect and address threats found in stealer logs. Through this module, we build on earlier research and analyze the data to identify trends and offer valuable insights.
SOCRadar’s Threat Hunting module
In our thorough examination of the digital commerce landscape, we chose a diverse set of e-commerce platforms. These platforms include user data from eBay, Amazon, Trendyol, Etsy, Delivery Hero, and Bolt, each providing unique insights into various aspects of the e-commerce experience. Let’s look at the results for those websites and explore them.
Stealer Logs Findings from E-Commerce Websites
Recent reviews of stealer logs from prominent e-commerce websites have unveiled a significant breach of user data in Q1 2024. This breach has compromised a massive 1,500,536 user records, sourced from 2,131 unique IP addresses, demonstrating the scale and potential impact of cybersecurity threats in the online shopping sector.
The detailed breakdown of the compromised data includes:
- 179,712 unique IDs and email addresses: These represent the virtual identities of customers, making them prime targets for phishing attacks and identity fraud.
- 180,444 passwords: The exposure of such a large number of passwords provides unauthorized access to personal accounts, heightening the risk of financial and data theft, and the presence of approximately 1,000 more unique passwords than IDs might suggest that some users have been compromised multiple times, which indicates the persistence of the fraudsters.
- 7,837 hashes: Hashes are cryptographic representations of confidential information, which serve as the first line of defense for securing sensitive information. Their compromise suggests that advanced techniques may have been used, increasing the sophistication of the breach.
- 2,454 credit card details: The direct financial risk is apparent, with thousands of users potentially facing fraudulent transactions.
This substantial breach highlights the vulnerabilities present in the e-commerce sector and underscores the need for heightened cybersecurity measures to protect consumer data.
SOCRadar’s free Account Breach Check Guardness
Stealer logs often act as a digital marketplace for cybercriminals, who acquire sensitive data to perpetrate activities like phishing, fraudulent transactions, and unauthorized access to vital assets. The most alarming scenario is when corporate credentials are compromised, allowing criminals to target entire companies, leading to considerable financial and reputational losses.
Identifying which domains are frequently compromised helps us understand where vulnerabilities are most severe.
Use SOCRadar’s free Account Breach Check to spot compromised accounts. This tool, part of the SOCRadar Labs suite, allows users to check if their domain or email has been affected by a breach.
Free Account Breach Check, SOCRadar Labs
Geographic Trends in E-Commerce Stealer Logs
By examining the geographic data from stealer malware affecting e-commerce platforms, we observed that certain countries are more frequently targeted, revealing an uneven distribution of cyber threats such as phishing, fraud, and impersonation.
This analysis aims to provide a deeper understanding of how these threats disproportionately affect various regions, by closely examining the distribution of victim countries by percentage.
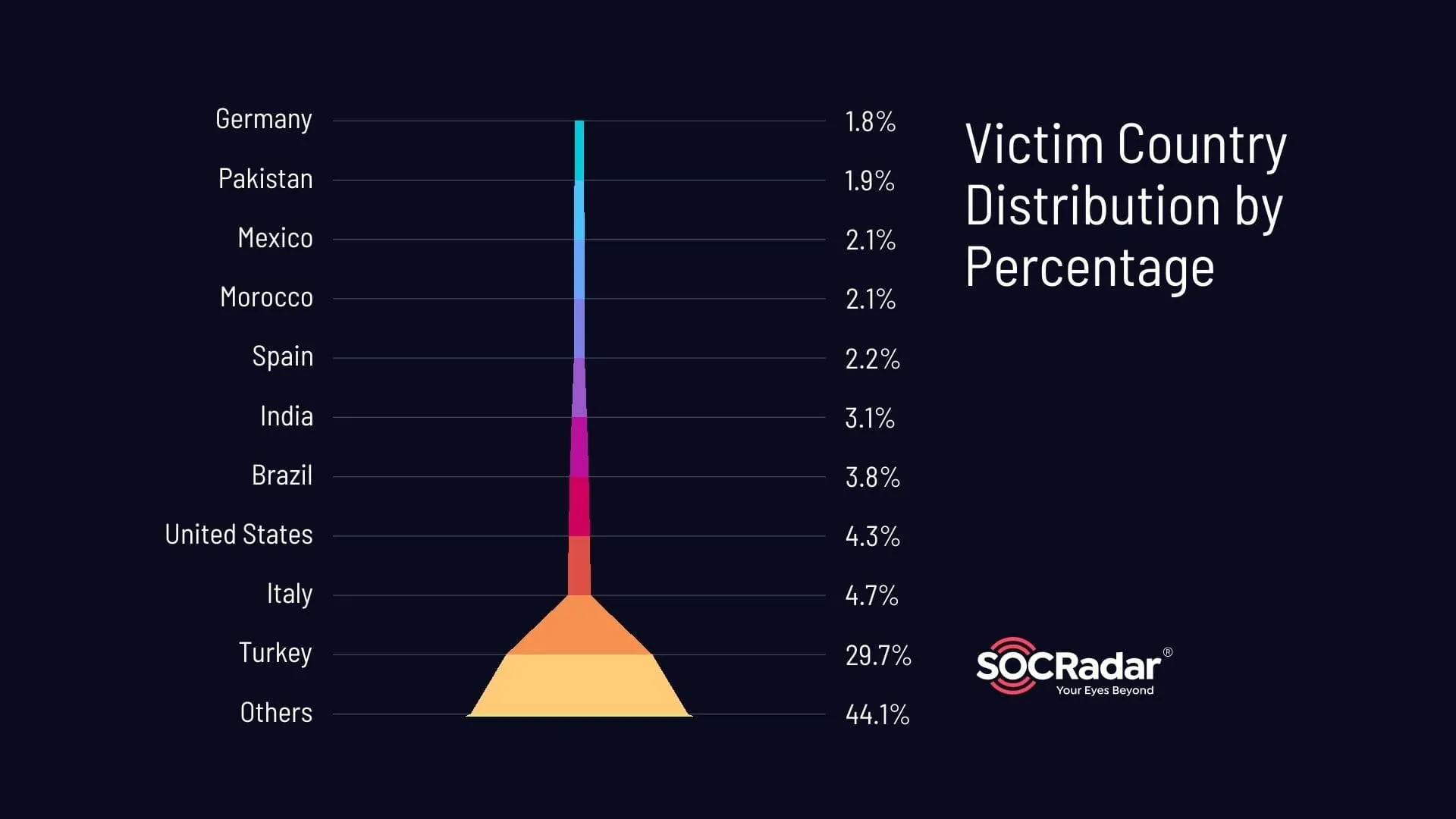
Victim country distribution in stealer logs related to different popular E-Commerce domains
Our analysis of stealer logs affecting e-commerce sites revealed involvement from domains in 144 different countries. The data shows a significant concentration of incidents in certain countries, with Turkey leading at 29.7%—substantially higher than the other top countries. Italy follows at 4.7%, the United States at 4.3%, Brazil at 3.8%, and India at 3.1%.
The stark discrepancy between Turkey and the others likely stems from the high traffic on Trendyol, a popular e-commerce platform in Turkey, which alone accounts for 27% of the incidents from Turkey. In contrast, other Turkish sites combined account for only about 2%.
This concentration indicates that specific local platforms can significantly influence the cyber threat landscape in a country.
Credit Card and Hash Information in E-commerce Stealer Logs
Our analysis of stealer logs from e-commerce sites has revealed a significant presence of compromised credit card details and hash information. We’ll delve into the specifics of these findings below.
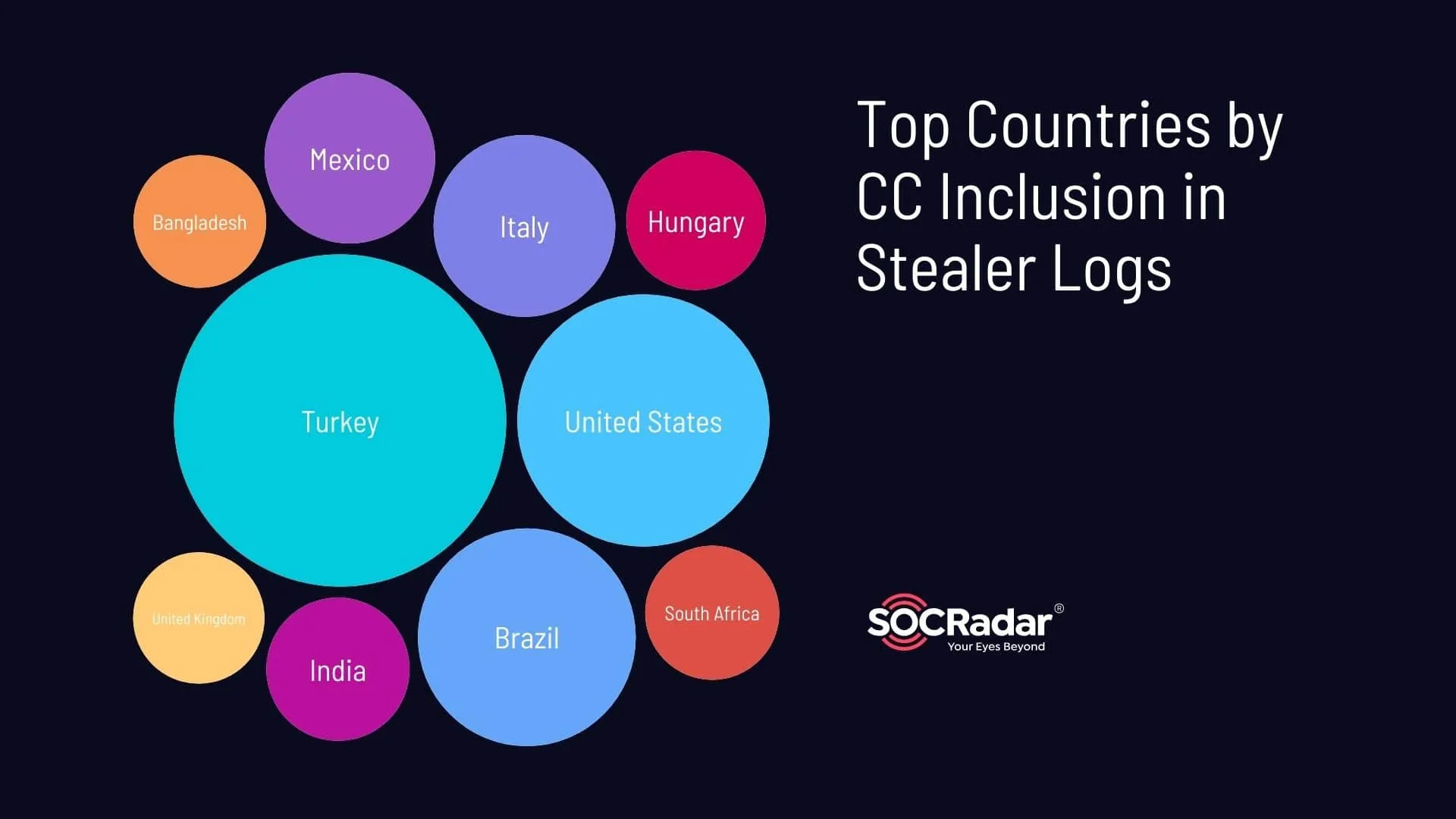
Top countries by CC inclusion
Credit card (CC) data appears in 31.4% of all logs, presenting a substantial risk of financial fraud. The countries most affected are Turkey (14.77%), the United States (8.52%), Brazil (6.35%), Italy (4.43%), and Mexico (3.9%). This indicates a significant exposure to financial risks for consumers in these regions, where cybercriminals might exploit this information for unauthorized transactions.

Top countries by hash inclusion
Hash information, which includes hashed passwords or other sensitive data, is found in 57.15% of all logs. The countries with the highest incidences are Turkey (16.6%), the United States (9.02%), Italy (6.89%), India (5.34%), and Brazil (4.56%). The prevalence of hashed data underscores the widespread risk of cyber-attacks, where these hashes, if cracked, could lead to unauthorized account access and data breaches.
Browser Usage Insights in E-commerce Security Breaches
Understanding which browsers were utilized by victims at the time their data was compromised sheds light on the potential pathways exploited by cybercriminals. This information is crucial for devising effective countermeasures in the e-commerce domain.

Chrome and Edge consistently ranked first and second place for different domains
In our analysis, Chrome stands out as the leading browser where most compromises occurred, accounting for 61.69% of the incidents. This indicates that while Chrome is popular for its features and usability, its widespread use also makes it a prime target for cyber threats.
Edge follows with a substantial 29.37%, demonstrating that major browsers are commonly exploited avenues for data breaches. Other browsers like Brave (3.51%), Firefox (2.32%), and Opera (1.22%) also appear prominently but represent smaller fractions of the compromised data.
Additional browsers such as Chromium, Thunderbird, Vivaldi, Avast Secure Browser, and CentBrowser collectively accounted for around 1.9% of the breaches. This indicates that while less common, these browsers are not immune to security threats.
Strengthening E-commerce Security to Counteract Stealer Malware
To effectively defend against stealer malware, e-commerce businesses must adopt comprehensive security strategies. Here are some tailored best practices:
Enhance Account Security:
Implement stringent access controls on employee accounts. Utilize Multi-Factor Authentication (MFA) to significantly decrease the risk of unauthorized access, ensuring that only verified users can access sensitive data.
Promote Secure Password Practices:
Encourage employees to use password managers. This facilitates the creation and maintenance of strong, unique passwords for each account, greatly reducing the likelihood of credential compromise.
Maintain Updated Systems:
Ensure that all software, is regularly updated. Staying current with security patches is crucial to closing any vulnerabilities that could be exploited by malware.
Immediate Response to Incidents:
Upon detection of stealer malware, quickly isolate the affected devices from the network. Prompt action limits the spread of the malware and mitigates potential data breaches.
Cybersecurity Education:
Educate employees about the dangers of stealer malware and the importance of cybersecurity. Regular training on recognizing suspicious activities like phishing emails or dubious attachments can empower employees to act as a first line of defense.
Safe Software Installations:
Stress the importance of downloading applications only from reputable sources officially approved by the company. This reduces the risk of introducing malicious software through seemingly legitimate applications.
Vigilance Over Credential Integrity:
Conduct frequent scans for credential exposures on public services such as online chat platforms and cloud storage. These areas are often targeted by cybercriminals looking to steal sensitive information, this can be done by using SOCRadar Labs’ free Account Breach Check as mentioned before.
By implementing these practices, e-commerce platforms can enhance their defenses against the growing threat of stealer malware, protecting both their business operations and their customers’ sensitive information.
Stay Protected with SOCRadar’s Dark Web Monitoring
SOCRadar’s Dark Web Monitoring has continuous oversight across the web, including the more concealed segments like the deep and dark web. This tool is necessary for detecting if sensitive information related to your organization has been compromised.
With this monitoring service, you’ll receive instant notifications about compromised account credentials and credit card details, crucial for preventing identity theft and fraud stemming from stealer logs.
Dark Web Monitoring (SOCRadar’s Digital Risk Protection module)
To deepen your understanding of how stealer malware operates and its impact, consider reading our blog post, “The Anatomy of Stealers” For a comprehensive analysis of stealer logs, our “Snapshot of 70 Million Stealer Logs” whitepaper offers extensive insights and data.
Conclusion
Our analysis of stealer malware logs provides vital insights into the cybersecurity threats that plague the e-commerce sector, exposing key vulnerabilities to fraud, and phishing that affect major online marketplaces.
E-commerce businesses should use these findings to anticipate potential threats and improve their cybersecurity measures, ensuring strong protection in an environment where consumer trust is key to success.
Taking advantage of observations from such analyses can be used for improving cybersecurity defenses, mitigating threats, and identifying patterns. Robust security protocols, combined with tools like SOCRadar’s Threat Hunting and Dark Web Monitoring, can provide critical information for developing effective threat mitigation strategies.
Search on stealer logs for Amazon (SOCRadar Threat Hunting)
Our analysis of e-commerce stealer logs provides critical insights into cybersecurity vulnerabilities, highlighting high-risk countries and common threats. Maintain vigilant monitoring of websites, email systems, and login credentials to ensure your digital identity is protected.




































