
Quick Facts on the World’s Top InfoStealer Malware Threats
An info stealer is a piece of malicious software (malware) that tries to steal your information. In most cases, this means stealing information that can make money for the cybercriminals. The standard form of info stealer gathers login information, like usernames and passwords, which it sends to another system via email or over a network.
This blog post has compiled everything you need to know about this type of malware threat.
InfoStealers: An Overview
Some types of InfoStealers are called Keyloggers, which collect every keystroke in your system. Keyloggers monitor and gather every accounting credential the user enters with every message the user sends.
After stealing sensitive information from one’s system, InfoStealers send the information to the threat actor. The threat actor may blackmail the victim and ask for money or sell the victim’s statement on black markets and Dark Web Forums.
InfoStealers generally infect one’s system by malicious attachments, Google advertisements, exploited websites, and browser add-ons.
InfoStealers are generally distributed to other threat actors as Malware-as-a-Service and sold on Dark Web Forums.
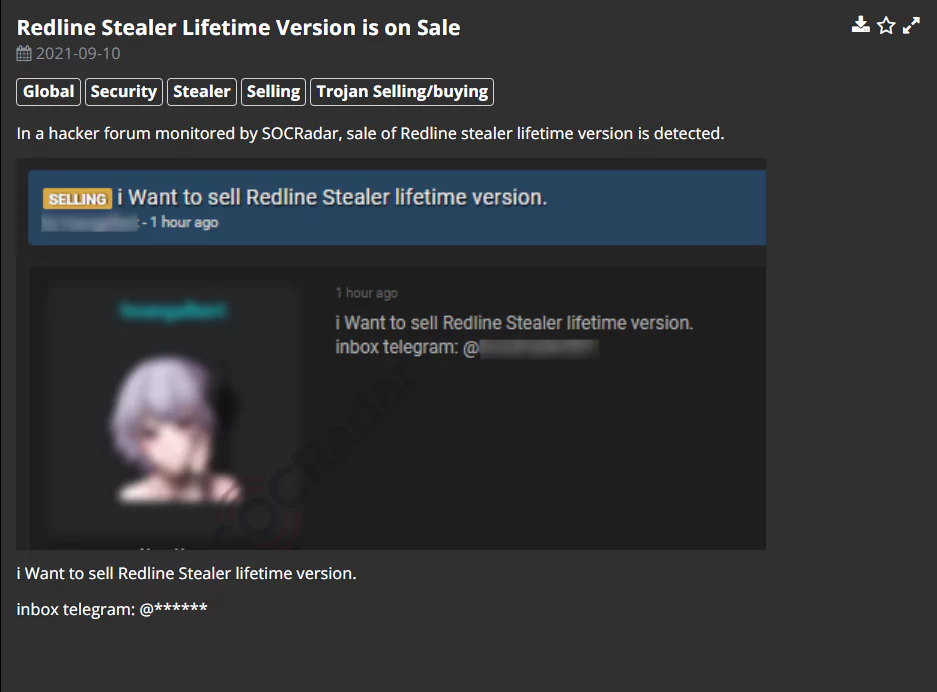
From the Threat Actor to the Customers
The threat actor may use the stolen data in many different ways, but selling the data on the Dark Web is the most common way.
The threat actors mainly choose Dark Web forums like raidforums[.]com and hackforums[.]net, and Dark Web marketplaces like genesis[.]market to sell the stolen data.
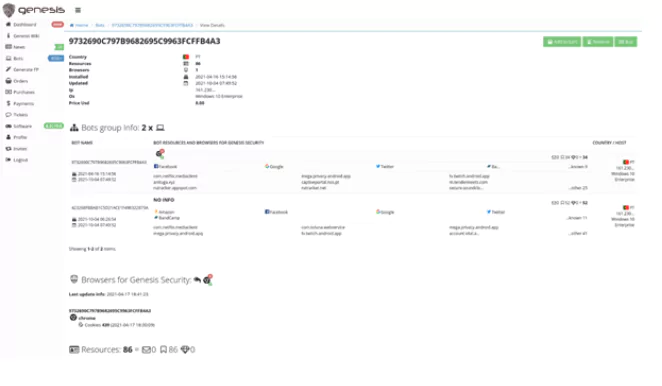
In some cases, the InfoStealer collects and uploads the data automatically onto a black market. Without human intervention, the data selling process is much easier and faster.
Leaders of the Sector: World’s Top InfoStealers
RedLine
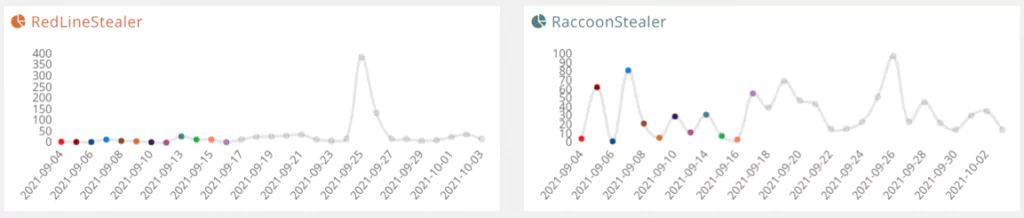
RedLine is a new InfoStealer distributed via COVID-19 phishing email campaigns. The InfoStealer’s capabilities include collecting data such as saved login credentials and saved credit card information from browsers.
Some versions of RedLine also collect other sensitive data such as location data, hardware information, and information about security software programs installed on the system. In the most recent versions of RedLine, the creators have added a functionality to steal cryptocurrency from the system. RedLine is believed to have originated in a Russian-speaking country, and the malware has been sold as Malware-as-a-Service mostly on Russian Dark Web forums.
Raccoon
Raccoon is a classic InfoStealer distributed as Malware-as-a-Service that gathers autofill data, login credentials, and cookies from the infected system. Raccoon InfoStealer is very popular among cyber threat actors even though it is not a sophisticated or advanced malware. The InfoStealer has infected over 100.000 devices and continues to spread. In 2019, the InfoStealer became one of the most mentioned malware on the Dark Web forums.
Agent Tesla
Agent Tesla, a Remote Access Tool (RAT), is an InfoStealer capable of exfiltrating data from browsers, VPNs, and File Transfer Protocol (FTP) servers. Agent Tesla also has keylogging capabilities and a screenshot feature. First initialized on a Turkish-language WordPress site in 2014, the creators of Agent Tesla are still adding new functionality to their product.
FormBook
Initially called “Babushka Crypter,” FormBook is an InfoStealer distributed as Malware-as-a-Service capable of keylogging, webform hijacking, and clipboard monitoring. First began its activity on the 1st of January, 2016; FormBook is still an active and dangerous trojan which added the latest Microsoft Office zero-day vulnerability (CVE-2021-40444) into its capabilities. Most inexperienced threat actors
Vidar
Vidar InfoStealer, an evolved version of the Arkei InfoStealer, is a commonly-used InfoStealer among cyber attackers. Vidar is believed to have been created in a Russian-speaking country because the InfoStealer is programmed to stop if the system is located in one of the ex-USSR countries. Vidar’s capabilities include collecting browser cookies and history, taking screenshots, gathering two-factor authentication data, and collecting information about digital wallets. After Vidar collects data from the system, the InfoStealer erases itself and sends the compressed data to the threat actor.
Azorult
Created by the threat actor “Gorgon Group, “Azorult InfoStealer was first discovered in 2016. Azorult InfoStealer is believed to have originated from one of the ex-USSR countries.
Primarily bought in Russian Dark Web forums, Azorult’s capabilities include collecting browser cookies and history, stealing login credentials, and collecting system information such as the username and the operating system version. Some newer versions of Azorult InfoStealer include setting up a Remote Desktop Protocol (RDP) connection for the threat actor to take control of the system.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free

































