
The Anatomy of Stealers: How Are They Stealing Our Information? Where Are They Taking It?
The world of cyber security faces new and more complex threats every day. Among these threats, which we encounter anew each day, one of the most significant is malicious software designed to steal personal and corporate information, known as “stealers”. Stealers can be considered one of today’s unseen yet most dangerous corporate threats. As the SOCRadar Threat Research team, we have endeavored to deeply investigate and expose the anatomy of stealer malware.
Publicly submitted Redline stealer example in Any.run
This research was conducted on a total of 1,250 analysis reports (250 each) collected from the public sandbox environment named Any.run. The research not only uncovers the operational mechanisms of stealer malware but also exposes the Tactics, Techniques, and Procedures (TTPs) preferred by cybercriminals. Critical information such as the Command and Control (C2) addresses behind these malware, the traces they create in operating systems, and the command lines they use, provide valuable insights to security researchers and cybersecurity professionals.
Key Points
- Stealer malware is sophisticated malicious software designed to steal personal and corporate information. This study provides an in-depth analysis of the five most popular stealers: LummaC2, Redline, Raccoon, Amadey, and Formbook.
- Based on 250 analysis reports from each stealer collected from the Any.run public sandbox environment, this research sheds light on the operational mechanisms of stealer malware, the Tactics, Techniques, and Procedures (TTPs) preferred by cybercriminals, and the Command and Control (C2) addresses used by the malware.
- The study details the operational methodologies of stealer malware through the MITRE ATT&CK framework. This framework offers valuable insights to cybersecurity professionals about the tactics and techniques that the malware might use.
- The most frequently communicated IP addresses and ASN information by the malware indicate that threat actors tend to use the same infrastructure, highlighting the importance of threat intelligence and how critical it is in detecting malicious network connections.
- The analyses suggest the adoption of a Zero Trust approach and the integration of security systems with Threat Intelligence solutions to develop effective defense strategies.
- The research emphasizes the need for continuous education and awareness, as well as the use of effective security tools and practices, for a robust defense against stealer malware.
This research aims to explore the details of stealers threats and by increasing knowledge and awareness in the cybersecurity field, assist in developing a more effective strategy against malicious software.
Characteristics of Stealer Malware
Stealer malware can infect computers through various methods, primarily including cracked software and game cheats. In the further sections of the research, we will delve into the infrastructures and operational structures of stealers. For more detailed information about the methods of infection and the information stolen by stealers, you can refer to our previously written report, Snapshot of 70 Million Stealer Logs.
For the scope of our research, we have encountered the five most common stealer malware in online sources: LummaC2, Redline, Raccoon, Amadey, and Formbook (Source: Any.run). Each stealer is equipped with its unique features and capabilities. However, stealers share the following common characteristics:
- Stealers aim to steal various pieces of information from the victim’s device. This information includes browser history, autofill information, saved passwords, crypto wallet details, and even system and network information.
- To avoid detection by cybersecurity systems, stealers employ various bypass techniques. Encrypted or obfuscated codes, rootkit-like features, and the ability to alter the malware’s behavior are among these methods. You can look into these techniques under the Stealers’ MITRE ATTACK Scorecard section.
- Stealer malware communicates with a remote server to transfer stolen data and potentially receive new commands. This allows the malware to be remotely updated or have new functionalities added.
- They typically spread themselves through email attachments, fake software updates, or malicious websites. This leads to more devices being infected and more data being stolen.
- Particularly advanced stealer malware can mimic system behavior, thus bypassing behavior-based detection mechanisms. This enables them to remain undetected in the system for a longer period.
We have examined some of the fundamental techniques present in stealer malware reports and the defense strategies that can be employed against these techniques. We attempted to visualize all the MITRE ATT&CK techniques mentioned in these reports using the ATT&CK Navigator ATT&CK Navigator.
Examining Stealer Malware Through MITRE ATT&CK Techniques
Various techniques defined within the MITRE ATT&CK framework are among the best methods to illuminate the operational methodologies of these stealers. Below is a combination of MITRE tactics and techniques for the five stealer malware.

Combination of the five stealers’ MITRE ATT&CK TTPs
Security measures can be developed through techniques of some tactics. For example, let’s interpret the Discovery and C2 tactics from the MITRE table of the five stealers.
Discovery Techniques (e.g., T1012, T1082, T1518)
Discovery techniques are methods that allow attackers to explore the system, networks, and services. For instance, the T1082 system information discovery technique enables attackers to customize their attacks based on system features.
Defense Strategy: Implementing logging and monitoring mechanisms for system queries and unauthorized access attempts is necessary. Regularly updating systems and using Endpoint Detection and Response (EDR) tools can facilitate the detection of a stealer in the discovery phase, thereby reducing risks.
Command and Control (C2) Techniques (e.g., T1071)
C2 techniques allow attackers to communicate with compromised systems to direct malicious activities. Techniques like T1071 enable malicious traffic to blend in with normal traffic, thus concealing it.
Defense Strategy: Network segmentation, advanced firewalls, and the use of Intrusion Detection Systems (IDS) can help identify and block C2 traffic. Behavioral analysis and the detection of anomalies are critical for identifying covert communication channels.
Persistence Techniques (e.g., T1136, T1574)
Persistence techniques ensure that the malicious software remains active in the system between restarts and user logouts. Techniques like T1136 offer attackers continuous access.
Defense Strategy: Regular review of user account lists, Multi-Factor Authentication (MFA), and strict access controls can prevent attackers from gaining persistent access.
Stealer malware poses a serious threat to information security and steals information from target systems through various techniques. Understanding these techniques within the MITRE ATT&CK framework allows cybersecurity professionals to develop effective defense strategies. Strategies based on detection, prevention, and response can significantly mitigate the impacts of stealer malware. Continuous education and awareness, as well as the right security tools and practices, provide a strong defense against these continually evolving threats.
Amadey Stealer MITRE ATT&CK Analysis and Stealers’ MITRE Heatmap Tables
We have prepared a brief analysis based on the sandbox analysis reports of the Amadey Stealer malware, focusing on the MITRE ATT&CK techniques it utilizes. The numbers in parentheses indicate how frequently each technique is mentioned in the reports. Evidence is occasionally added from the appropriate stealer malware analysis report.

Amadey Stealer Malware MITRE ATT&CK Heatmap
Initial Access
(User Execution: Malicious File (44))
This indicates that Amadey Stealer can trick users into opening malicious files, which may be presented through phishing or disguised as legitimate software.
Method 1: The user is persuaded to open an email attachment or run a downloaded file. A malicious file (invoice.pdf..exe) is presented through a phishing campaign, and the user is led to perceive this file as a legitimate document.
Evidence:
| Filename | Parent Path | Stealer | File Type |
| Rar$EXa1844.41509MEMORANDUM.pdf..exe | Appdata Local Temp | Formbook | DROPPED |
Execution
(Command and Scripting Interpreter: Windows Command Shell (534), PowerShell (188), Visual Basic (21), Python (1), System Services: Service Execution (163), Create or Modify System Process: Windows Service (7))
The malware is noted to use common scripting languages to execute malicious commands. It also demonstrates its capability to run malicious code by creating or hijacking system processes.
Method 1: It can combine a malicious executable with an image file, misleading the user into thinking it’s just an image file, and directing them to run the malicious code.
cmd.exe /c “copy /b image.jpg + payload.exe output.jpg”
Method 2: The malware adds a malicious file as a new service to the system and sets it to automatically start.
sc create NewService binPath= “C:BKjade.exe” start= auto
Evidence:
| User | Command Line | Stealer | File Type |
| admin | “C:WindowsSystem32cmd.exe” /q /R cOPY /y “C:UsersadminAppDataLocalTemp7zS0BBD4EFEThu02bbe7aaca36e.exe” ..HuYMRJYt.eXE&& sTArT ..HUYMRJyT.eXe /pH7FDL9cM6JL7&IF “” ==”” for %K iN ( “C:UsersadminAppDataLocalTemp7zS0BBD4EFEThu02bbe7aaca36e.exe” ) do taskkill /f -iM “%~NXK” | Raccoon | MICROSOFT-CMD-SCRIPT |
| admin | “C:WindowsSystem32schtasks.exe” /Create /SC MINUTE /MO 1 /TN mnolyk.exe /TR “C:UsersadminAppDataLocalTemp6d73a97b0cmnolyk.exe” /F | Amadey | MICROSOFT-SCH |
Persistence
(Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (385, Scheduled Task/Job: Scheduled Task (484))
The malware is noted for maintaining its persistence by registering itself in startup locations. Additionally, it ensures persistence by scheduling tasks to run at specific times.
Method 1: It adds a malicious file to the registry to ensure it runs at every system start.
reg add HKCUSoftwareMicrosoftWindowsCurrentVersionRun /v Update /d “C:Pathmalicious.exe”
Method 2: It creates a scheduled task to automatically run the malicious file at specific times.
schtasks /create /sc daily /tn “Update” /tr “C:Pathmalicious.exe
Evidence:
| User | Command Line | Stealer | File Type |
| SYSTEM | C:WindowsSystem32WindowsPowerShellv1.0powershell.exe <#wsyzqeupt#> IF((New-Object Security.Principal.WindowsPrincipal([Security.Principal.WindowsIdentity]::GetCurrent())).IsInRole([Security.Principal.WindowsBuiltInRole]::Administrator)) { IF([System.Environment]::OSVersion.Version -lt [System.Version]”6.2″) { schtasks /create /f /sc onlogon /rl highest /ru ‘System’ /tn ‘NoteUpdateTaskMachineQC’ /tr ”’C:Program FilesNotepadChromeupdater.exe”’ } Else { Register-ScheduledTask -Action (New-ScheduledTaskAction -Execute ‘C:Program FilesNotepadChromeupdater.exe’) -Trigger (New-ScheduledTaskTrigger -AtStartup) -Settings (New-ScheduledTaskSettingsSet -AllowStartIfOnBatteries -DisallowHardTerminate -DontStopIfGoingOnBatteries -DontStopOnIdleEnd -ExecutionTimeLimit (New-TimeSpan -Days 1000)) -TaskName ‘NoteUpdateTaskMachineQC’ -User ‘System’ -RunLevel ‘Highest’ -Force; } } Else { reg add “HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun” /v “NoteUpdateTaskMachineQC” /t REG_SZ /f /d ‘C:Program FilesNotepadChromeupdater.exe’ } | Amadey | UNKNOWN |
Privilege Escalation
(Abuse Elevation Control Mechanism: Bypass User Account Control (4))
It demonstrates the ability to use privilege escalation techniques without the end user’s consent.
Method 1: Exploits or tools are used to bypass the system’s security mechanisms to gain higher privileges, for example, tools like UACMe can be used.
Detailed information: https://github.com/hfiref0x/UACME
Defense Evasion
(Virtualization/Sandbox Evasion: Time Based Evasion (518), System Checks (84), Virtualization/Sandbox Evasion (13), Masquerading: Match Legitimate Name or Location (5), Rename System Utilities (67), Indicator Removal: File Deletion (137), Impair Defenses: Disable or Modify System Firewall (28), Disable or Modify Tools (103))
It reflects efforts to detect analysis environments and avoid these environments. It disguises malicious files or processes as legitimate. It erases traces of its presence and indicates attempts to weaken the system’s cybersecurity defenses.
Method 1: The malicious code attempts to detect virtualization/sandbox environments and avoid such analysis by waiting for a certain period.
Wait & Sleep functions
Method 2: It makes the detection of malicious activities more difficult by disabling system updates.
sc stop WaaSMedicSvc
Evidence:
| User | Command Line | Stealer | File Type |
| admin | C:WindowsSystem32cmd.exe /c sc stop UsoSvc & sc stop WaaSMedicSvc & sc stop wuauserv & sc stop bits & sc stop dosvc & reg delete “HKLMSYSTEMCurrentControlSetServicesUsoSvc” /f & reg delete “HKLMSYSTEMCurrentControlSetServicesWaaSMedicSvc” /f & reg delete “HKLMSYSTEMCurrentControlSetServiceswuauserv” /f & reg delete “HKLMSYSTEMCurrentControlSetServicesbits” /f & reg delete “HKLMSYSTEMCurrentControlSetServicesdosvc” /f | Lumma | MICROSOFT-CMD-SCRIPT |
Credential Access
(Unsecured Credentials: Credentials In Files (1510), Credentials from Password Stores: Credentials from Web Browsers (621), Steal Web Session Cookie (363))
This tactic attempts to steal stored credentials. It steals session cookies to hijack user sessions.
Method 1: Tools and commands are used to steal usernames and passwords from browser databases (for example, Chrome’s ‘Login Data’ file).
SELECT origin_url, username_value, password_value FROM logins
Method 2: Tools and commands are used to steal browser cookies from browser databases (for example, Chrome’s ‘Cookies’ file).
SELECT host_key, path, secure , expires_utc, name, value, encrypted_value FROM cookies
Evidence:
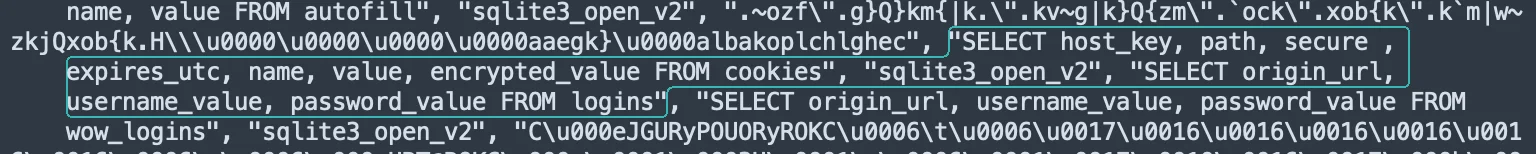
Discovery
(System Information Discovery (5460), Software Discovery (914), Security Software Discovery (3), System Owner/User Discovery (29), System Service Discovery (30), System Network Configuration Discovery (98), System Network Connections Discovery (18))
It aims to gather comprehensive information about the victim’s environment. It executes commands to understand the network and user context
Method 1: The target system is used to collect detailed information.
“systeminfo”, “ver”, “net user”, “ipconfig /all” vb.
Method 2: It is used to gather information about the network the target system is on.
External API’s
Evidence:
| User | Command Line | Stealer | File Type |
| admin | C:WINDOWSsystem32cmd.exe /c “echo ####System Info#### & systeminfo & echo ####System Version#### & ver & echo ####Host Name#### & hostname & echo ####Environment Variable#### & set & echo ####Logical Disk#### & wmic logicaldisk get caption,description,providername & echo ####User Info#### & net user & echo ####Online User#### & query user & echo ####Local Group#### & net localgroup & echo ####Administrators Info#### & net localgroup administrators & echo ####Guest User Info#### & net user guest & echo ####Administrator User Info#### & net user administrator & echo ####Startup Info#### & wmic startup get caption,command & echo ####Tasklist#### & tasklist /svc & echo ####Ipconfig#### & ipconfig/all & echo ####Hosts#### & type C:WINDOWSSystem32driversetchosts & echo ####Route Table#### & route print & echo ####Arp Info#### & arp -a & echo ####Netstat#### & netstat -ano & echo ####Service Info#### & sc query type= service state= all & echo ####Firewallinfo#### & netsh firewall show state & netsh firewall show config“ | lumma | MICROSOFT-CMD-SCRIPT |
| Stealer | Request Domain |
| Amadey, Redline, Raccoon, Lumma | api.myip.com |
MITRE ATT&CK tables of other stealer malware are as follows.

Formbook Stealer Malware MITRE ATT&CK Heatmap

Lumma Stealer Malware MITRE ATT&CK Heatmap

Raccoon Stealer Malware MITRE ATT&CK Heatmap

Redline Stealer Malware MITRE ATT&CK Heatmap
What Are the Common Points in Sandbox Analyses of Stealer Malware?
“You have a finger in every pie!”
There are friends among us who, whenever there’s a blunder somewhere around us, we can directly guess who the person present at that moment might be. Threat actors releasing stealer malware seem no different from these people. When we analyzed 1,250 stealer malware, we were expecting to see quite diverse and colorful results. Starting the research, we anticipated observing the same campaign’s different malware uploaded at different times, but seeing different stealers communicating with the same IP addresses surprised us.
We compiled a list of the 5 most frequently seen IP addresses of stealers. We were hoping this list would total 25 different IP addresses. However, it appears that campaigns prepared with multiple stealer malware often have the same threat actors behind them. This shows that a threat actor wanting to commit information theft tries to ensure their operation by using any kind of stealer malware. Although malicious software uses different evasion techniques day by day, the chance of detecting multiple malicious software using the same C2 address increases with a feed from a threat intelligence solution.
In the table below, the same IP addresses in the list of the most frequently seen IP addresses of stealers are marked with the same colors.
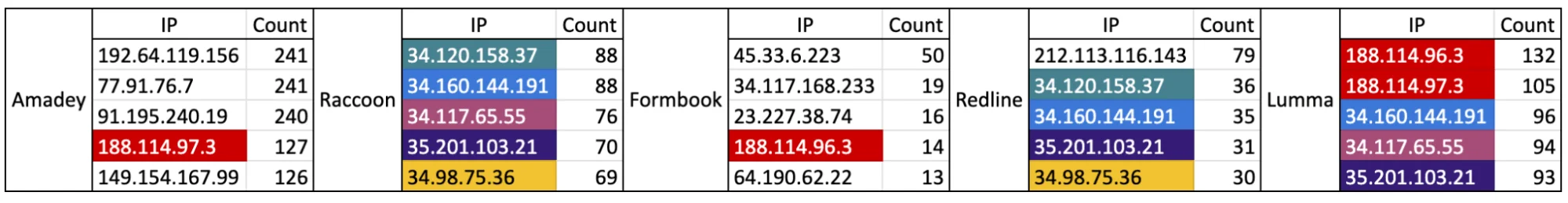
The 5 Most Frequently Connected IPs of Stealers (per connection)
The ports preferred in the IP connections of stealer malware can be among the primary factors affecting whether they can bypass or not bypass a well-configured corporate network. It has been observed that the most frequently preferred port number in these IP connections is port 80. Generally, blocking ports other than 80 and 443 for connections going from the internal network to the external network will be beneficial for the corporation. The main reason for this is the tendency of threat actors to prefer ports other than the most commonly used ports. For example, a request going from an endpoint in your internal network to port 9374 of an IP address outside should not be a connection we expect. Threat actors prefer to set up C2 servers on ports that will not conflict with other services. Nevertheless, our research has shown that the two most frequently used port numbers are 80 and 443. It might be difficult to directly distinguish malicious requests to these ports in connections going from your internal network to the external network. However, encountering requests to other ports should prompt a detailed investigation for your benefit.
| port | count |
| 80 | 2502 |
| 443 | 1155 |
| 4125 | 129 |
| 19062 | 84 |
| 50500 | 82 |
| 23052 | 79 |
| 19071 | 69 |
| 44675 | 31 |
| 48790 | 27 |
| 36457 | 26 |
| 50505 | 26 |
| 42359 | 20 |
| 28121 | 19 |
| 14845 | 17 |
| 2920 | 16 |
| 14433 | 15 |
| 4062 | 15 |
| 81 | 15 |
| 10060 | 14 |
| 16482 | 11 |
So, “Who’s running this place?”.
Let’s take a closer look at the ASN information of the IP addresses. Honestly, this list was almost entirely consistent with the IP addresses listed above. In the analysis reports, the top 5 ASN information holders are Amazon, Cloudflare, Google, Akamai, and Microsoft. Brands favored in the IT sector seem to be the choice of threat actors as well. At this point, using well-known ASN companies can lead to an increased appearance of legitimacy. In Cybersecurity, for an analyst who is still gaining experience, encountering a SOAR alarm showing data traffic to a Google-owned IP address might lead to the conclusion “Traffic is not considered suspicious.” and closing it as such. Therefore, before thinking that threat actors prefer quality, the tendency to use legitimate addresses for malicious purposes should come to mind. This reinforces the importance of the Zero Trust approach once more.
| ASN Name | Count |
| AMAZON-02 | 807 |
| CLOUDFLARENET | 402 |
| 270 | |
| Akamai International B.V. | 269 |
| MICROSOFT-CORP-MSN-AS-BLOCK | 188 |
| AMAZON-AES | 171 |
| Hetzner Online GmbH | 112 |
| AKAMAI-AS | 109 |
| OVH SAS | 108 |
| MEDIAFIRE | 82 |
| LEVEL3 | 48 |
| NAMECHEAP-NET | 43 |
| GOOGLE-CLOUD-PLATFORM | 41 |
| FASTLY | 38 |
| IONOS SE | 34 |
(The 15 Most Common ASN Firms in Stealers’ IP Connections) {pasta grafiği yapılabilir}
When considering endpoint-based observations, the area where stealers makes the most noise could be file writing and deletion operations. Looking at the network communications of an average-sized organization, HTTP connections and DNS connections enter the list of the loudest with high log generation rates. To detect malicious software in these noisy log environments, cybersecurity solutions with superior detection capabilities and continuous updates are needed. Nowadays, with the evolution of malicious software, detecting malicious network connections without a threat intelligence solution has become quite challenging. Three different connection types are listed in the analysis reports of stealer malware: IP Connections, HTTP Connections, and DNS Connections.
When we want to summarize the reports, in 1,250 malicious analysis reports, there have been a total of 24,267 connections made by the malicious software. Of these connections, 4,770 IP connections have been marked as malicious by the sandbox product. This means that on average, about 3 or 4 connections are established during the operation of each stealer malware. Isn’t that a significantly high number? As a result, it was found that out of these 4,770 marked connections, 1,331 were unique IP addresses. Considering the common use of IP addresses we just discussed, this implies that multiple malicious IP addresses are communicated with during the operation of each stealer malware. Are you taking enough precautions to catch at least one of them and prevent potential losses? We see the benefit in repeatedly stating that the best way to record these IP addresses as malicious in your security systems is through a good Threat Intelligence integration.
“There are only two safe ways.”
Stealer malware prepares their distribution environments for malicious activities by either exploiting a web server or setting up a web server for their malicious purposes. Upon examining all the HTTP connections in the reports, quite interesting results emerge. There have been 8,597 malicious web addresses that the stealers communicated with. Only 2 of these 8,597 addresses were using the HTTPS protocol. This corresponds to approximately 0.02%. Knowing this rate, I understand you might imagine a world where you could directly disable the HTTP protocol. However, unfortunately, in the real world, there are too many situations that will prevent you from making this decision. (You can get a better idea of why blocking HTTP requests might not be sensible by looking at a discussion in a forum https://forum.netgate.com/topic/183130/block-all-http-non-https-traffic/6)
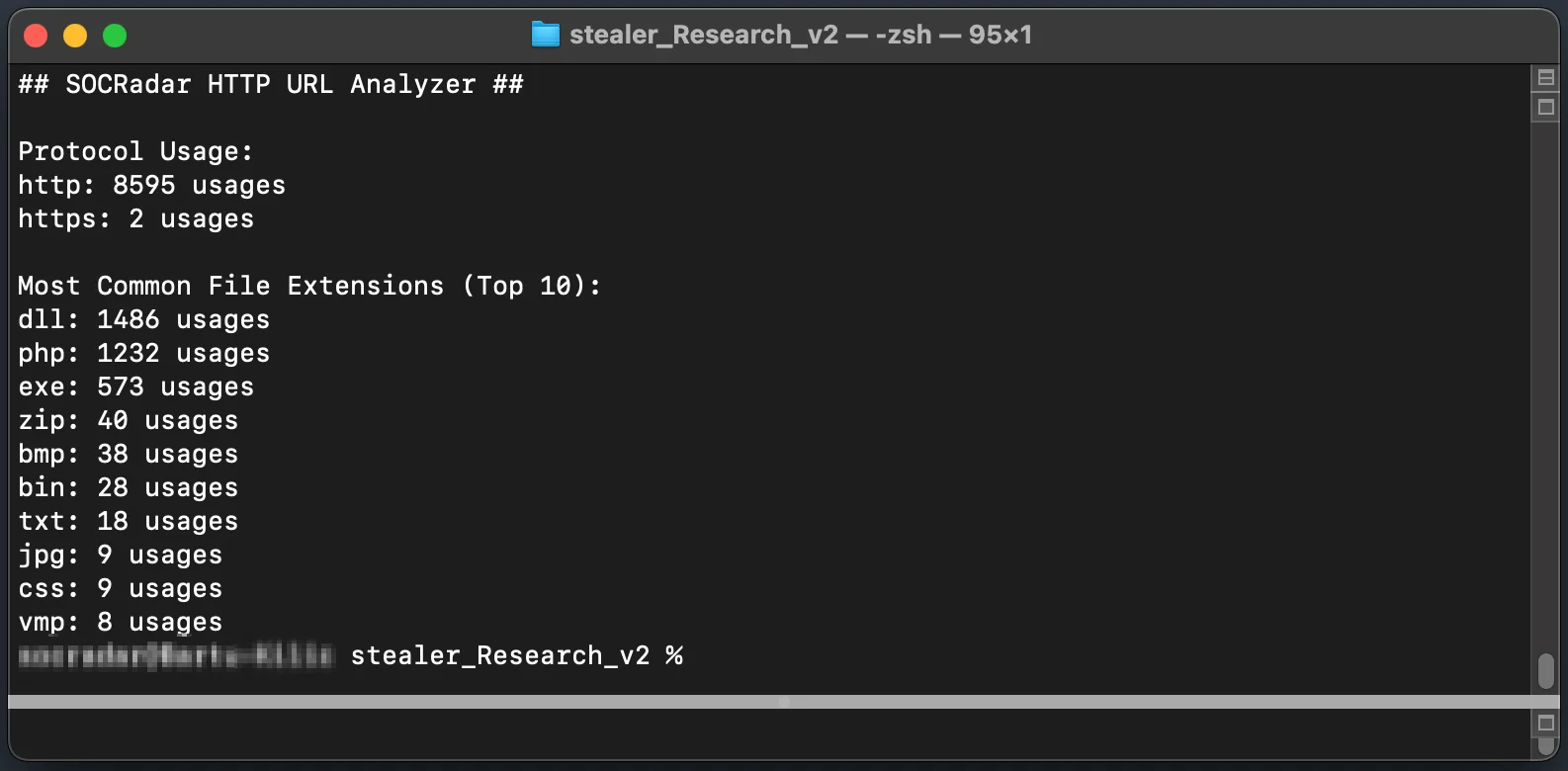
Top 10 file extensions
As seen in the image above, the most common extensions are DLL (Dynamic-link Library), PHP (Hypertext Preprocessor), and EXE (Executable). Two of these extensions should be blocked by default proxy profiles. In fact, within the top 10, allowing only PHP, BMP, TXT, JPG, and CSS extensions in the default proxy profile might seem like a step closer to avoiding thousands of malicious HTTP requests that stealers would make to the external environment.
The most frequently used hosts in HTTP/S requests are as follows:
| Top 20 Malicious Hosts | Count |
| gapi-node.io | 402 |
| 195.123.227.138 | 390 |
| 185.99.133.246 | 274 |
| usdseancer.xyz | 254 |
| 37.220.87.66 | 246 |
| 91.103.252.156 | 235 |
| potunulit.org | 228 |
| glowesbrons.xyz | 204 |
| kudoflowers.xyz | 198 |
| booxshistr.xyz | 163 |
| gservice-node.io | 151 |
| 45.9.74.99 | 144 |
| 193.233.254.61 | 139 |
| 77.73.134.27 | 137 |
| 77.91.68.18 | 127 |
| 83.217.11.6 | 123 |
| app.nnnaajjjgc.com | 120 |
| coursenote.xyz | 105 |
| 77.91.124.20 | 97 |
| 94.142.138.131 | 90 |
There are some TLDs (Top-Level Domains) that, upon seeing them, we think they “must be hosting malicious content.” XYZ has become one of them. Below are the most frequently seen TLDs in the URL addresses that stealer malware communicates with.
Most Common TLDs in Malicious URLs (Top 10):
xyz: 1385
com: 972
io: 580
org: 229
top: 48
net: 47
biz: 47
info: 42
ru: 36
at: 32
Some of the results we encountered while continuing our analysis helped us put pieces in place and connect the dots. DNS requests are critically important for cybersecurity today. A DNS solution that is correctly analyzed and integrated with a good threat intelligence system will move you several steps ahead in catching malicious requests. DNS requests can be used for many purposes, from making ordinary traffic unreadable by mixing it to leaking data. Below are the top 5 most frequently seen DNS requests in the sandbox analysis reports of stealer malware.
| Top 20 Most Seen Domains in DNS Requests | Count |
| hbopenbid-ams.pubmnet.com | 57 |
| telegra.ph | 53 |
| iplis.ru | 51 |
| potatogoose.com | 43 |
| api.myip.com | 39 |
Which countries are stealer malware’s malicious connections most frequently made towards? The United States, Russia, and Deutschland are the top three on this list.
| Top 20 Countries for C2 Servers | Count |
| US | 10,562 |
| RU | 2,545 |
| DE | 2,521 |
| NL | 1,568 |
| GB | 891 |
| FR | 528 |
| IE | 385 |
| BG | 250 |
| DK | 178 |
| HK | 129 |
| SG | 126 |
| KZ | 120 |
| AU | 96 |
| SC | 91 |
| LU | 90 |
| CA | 84 |
| FI | 82 |
| LT | 70 |
| ZA | 70 |
| VG | 68 |
Conclusion
The in-depth examination of stealers underscores one of the most complex threats encountered in the cyber security world. Throughout our research, we endeavored to deeply investigate how malware like Lumma, Redline, Raccoon, Amadey, and Formbook operate, how they steal user and corporate information, and where they send this information. These analyses have revealed not only the technical capabilities of the malware but also how remarkable they are with the strategic approaches adopted by cybercriminals.
The complexity and adaptability of stealer malware have been analyzed through various tactics and techniques defined in the MITRE ATT&CK framework. These analyses have demonstrated how the malware manage to bypass cybersecurity systems and the methods used to maintain a persistent threat. Moreover, the IP addresses and ASN information that the malware communicate with have highlighted the tendency of threat actors to use the same infrastructure, emphasizing once more how vital threat intelligence is in detecting such malicious network connections.
Our research provides valuable insights for cybersecurity professionals to develop more effective defense strategies against stealer malware. Continuous education, awareness, and the use of the right security tools and practices are critical in combating these ever-changing threats. Keeping security systems up to date and integrating Threat Intelligence solutions are of great importance in these attacks, allowing organizations and individuals to stay one step ahead of these sophisticated threats.
With SOCRadar, you can get to know stealers better and be informed in case your organization’s information is exposed in stealer logs. Also, you can prevent attacks before they happen by receiving intelligence through feeds sourced from numerous resources.
With SOCRadar, you can stay informed if your organization’s information is exposed in stealer logs. SOCRadar’s Threat Hunting module enables defenders to analyze large amounts of data from stealer logs, helping them identify and respond to threats early on.
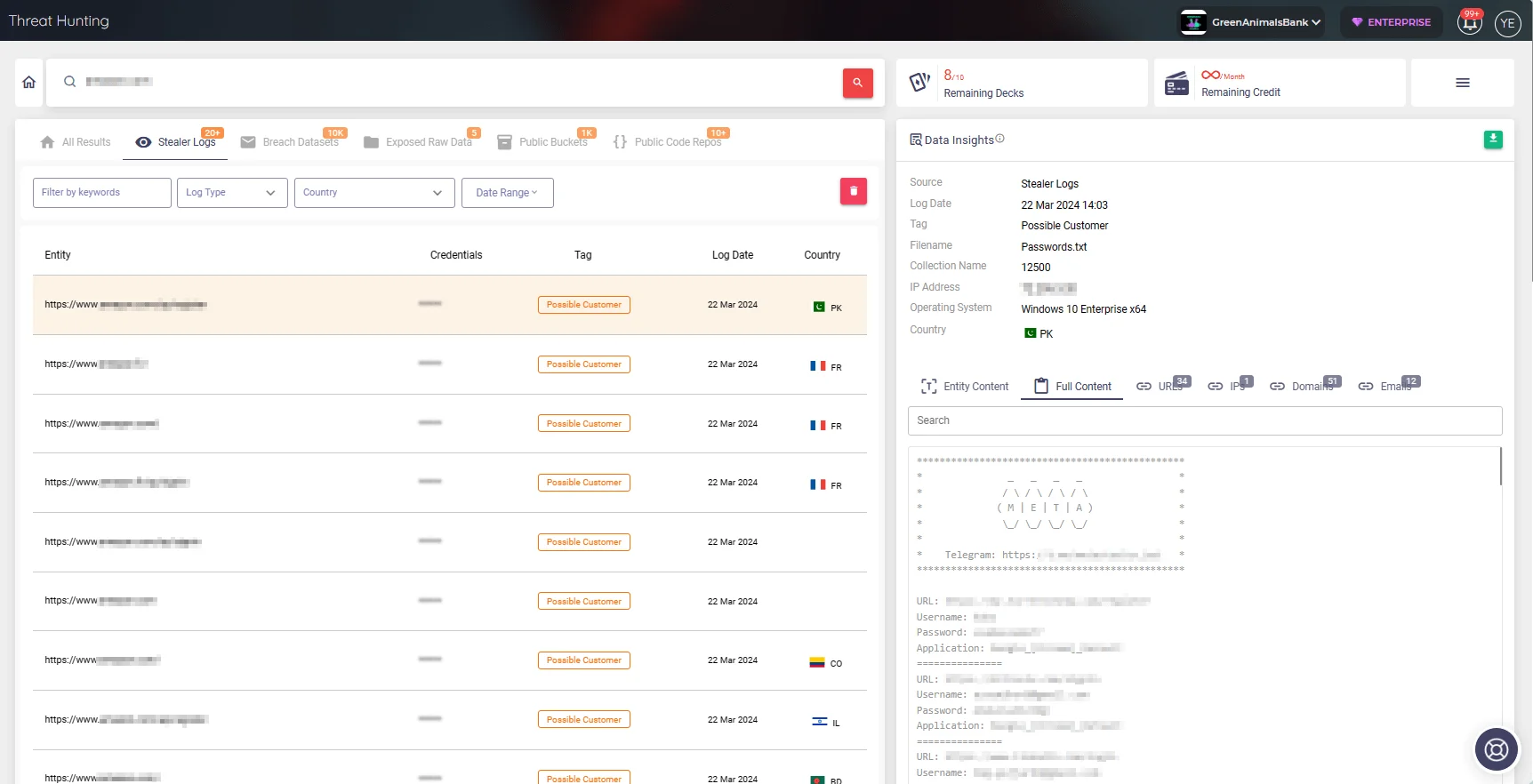
SOCRadar’s Threat Hunting
In conclusion, actors in the cybersecurity field must remain vigilant and ready to adapt to the dynamics of the threat landscape to mount an effective defense against continuously evolving threats like stealer malware. This study emphasizes the necessity of constant monitoring, analysis of threats, and the development of new defense methodologies. This is not just a technical effort but also requires a comprehensive strategic approach.




































