
Stealer Malware 101: Understanding the Different Variants and Families
In the realm of cybersecurity, malicious software (malware) continues to evolve, with various types targeting sensitive data for financial gains. Stealer malware, a prominent category, are designed to silently infiltrate systems, pilfer valuable information, and exfiltrate it to malicious actors. We will take a look at some notable stealer malware: Raccoon, Vidar, and RedLine. We will explore their characteristics, methods of infection, impact, and countermeasures, providing insight into the world of cyber threats.
Stealer Malware: An Overview
Stealer malware are programs that specifically target sensitive data, including login credentials, payment information, personal documents, and more. They often operate discreetly, avoiding detection by traditional antivirus software and focusing on data exfiltration. Stealer malware are commonly delivered through phishing emails, malicious websites, or compromised software downloads.
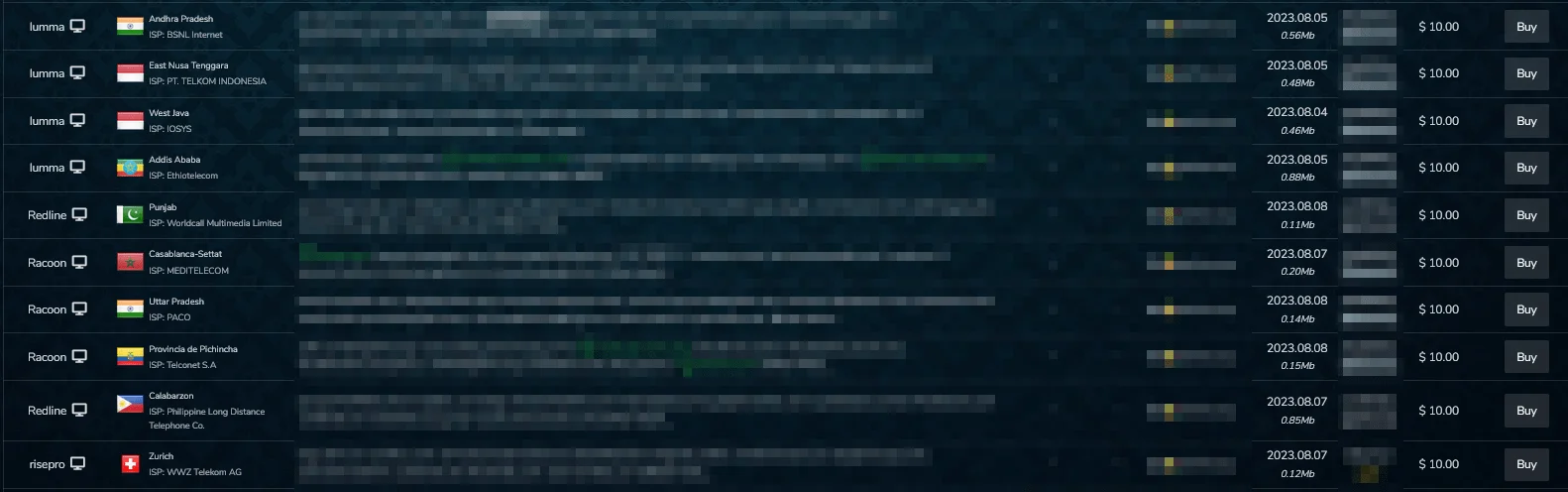
Figure 1 – Bots for sale on the Russian market
There are many families of stealer malware, such as Raccoon, Vidar, RedLine, LummaC2, Meta and more. The combination of potential financial gain, relative ease of development, adaptability, and the lure of exploiting human behavior makes infostealers a preferred choice for many threat actors.
As seen in Figure 2, which has been drawn up on the basis of data provided by the Russian market itself, a table of the sources of stealer logs that are currently on sale on the Russian black market, we can see that 4 stealer software are popular.
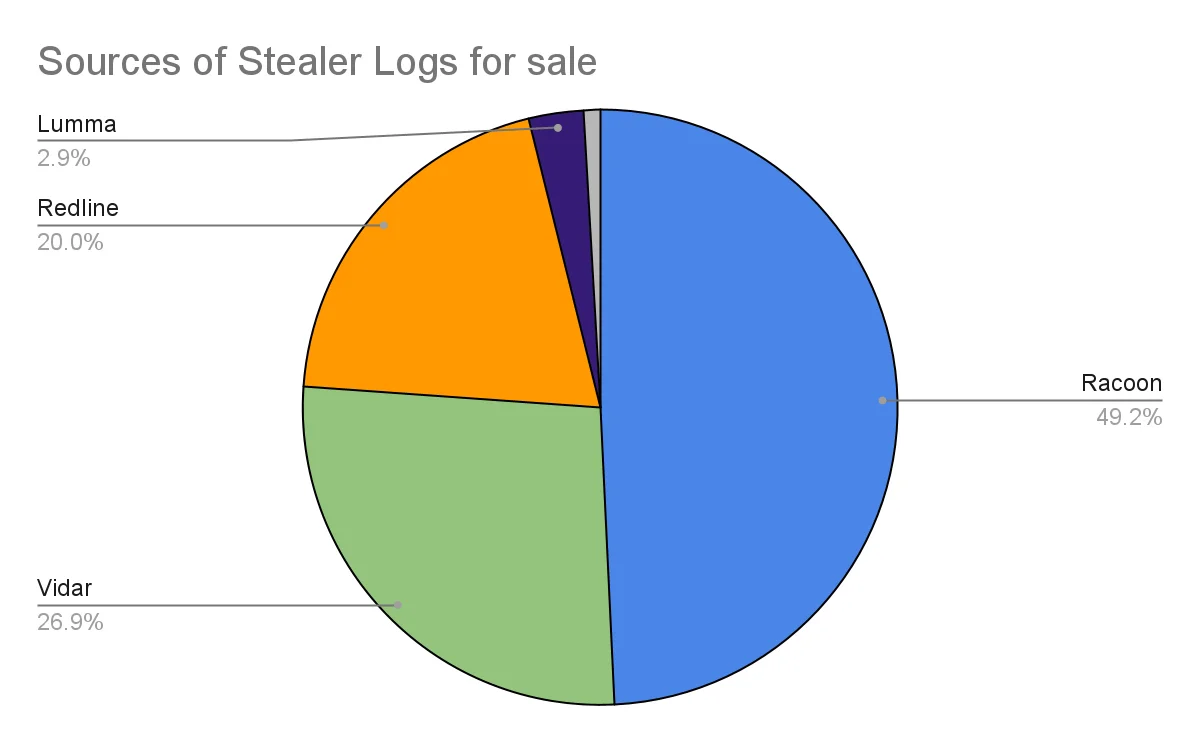
Figure 2 – Stealer logs that are currently on sale on the Russian black market
We can say that RedLine, Raccoon and Vidar are the 3 most used stealing malware, although their percentages may vary in different black markets or exposed stealer logs.
Raccoon Stealer
Raccoon gained prominence in the cybercriminal underground due to its ease of use and effectiveness. Raccoon can be obtained for a subscription and costs $200 per month.
In terms of core functionality, Raccoon can check system settings, capture screenshots, collect basic information such as OS version, IP and user name, and steal passwords and logins from a variety of browsers. It can also retrieve information from Microsoft Outlook and steal cryptocurrency wallets. When the data collection process is complete, the data is packed into a .ZIP archive that is then sent to the attackers’ server.
The execution process is simple but effective. Raccoon makes its way into the infected system, downloads additional modules (mostly DLL dependencies), then the malware begins to steal information from browsers and the system, and stores the stolen data in an archive file. In figure 3, we can see the execution process of Raccoon.
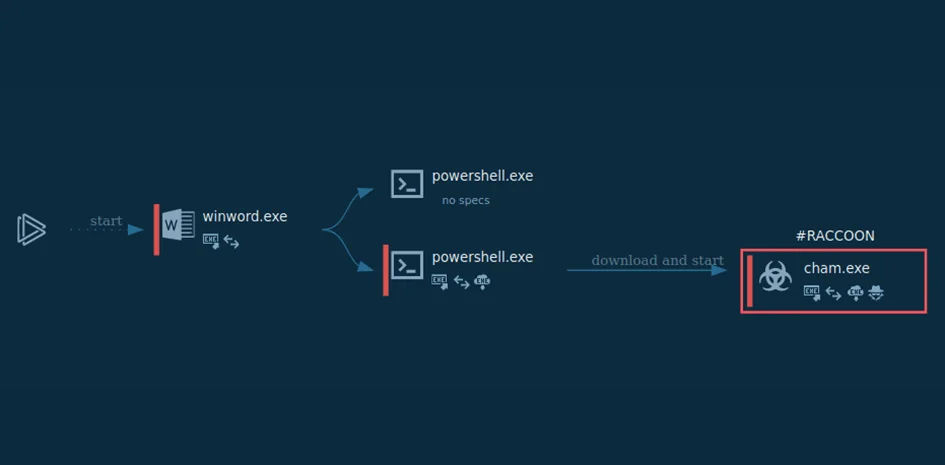
Figure 3 – Infection flow of Raccoon stealer
Raccoon is typically spread through phishing campaigns, malvertising, and exploit kits.
Key Features
- User-Friendly Interface: Raccoon is known for its intuitive dashboard, allowing even novice threat actors to easily configure and deploy the malware.
- Data Collection: It gathers data such as passwords, cookies, autofill data, and credit card information from various applications.
- Data Encryption: Raccoon encrypts the stolen data before transmitting it to its command-and-control (C2) server, making detection and analysis more challenging.
Raccoon’s impact is significant due to its widespread usage in credential-stealing campaigns, which can lead to unauthorized access, financial loss, and identity theft.
Vidar Stealer
Vidar is a data-stealing malware that focuses on gathering sensitive information for financial gain. It is sold as a subscription service on underground forums for $250 to $700.
Purchasing Vidar gives the attacker access to a control panel where they can set up the malware to target specific information on the victim’s PC. The control panel displays the current builder version, user settings, malware status and logs. Vidar can steal browser cookies and history, browser logs including data from TOR, autofill information including bank and credit card details. Vidar is also known to steal digital coins from offline wallets. After collecting all the targeted information, the malware archives it and sends the stolen data to a control server, after which Vidar removes traces of its work and deletes itself from the system. Figure 4 represents Vidar’s execution flow.

Figure 4 – Vidar’s execution flow
Vidar is distributed via malicious email attachments, exploit kits, and compromised websites. Once executed, it silently monitors the victim’s activities, capturing data from various applications.
Key Features
- Stealth: Vidar employs various techniques to evade detection, including anti-sandbox and anti-debugging mechanisms.
- Data Variety: It targets a wide range of data, including credentials, cryptocurrency wallets, browsing history, and chat logs.
- Credential Stuffing: Vidar can use stolen credentials to perform credential stuffing attacks on other online accounts.
Vidar’s impact extends to financial loss, identity theft, and potential compromise of sensitive online accounts.
RedLine Stealer
RedLine is a stealer malware that primarily targets Windows systems. It employs various techniques to avoid detection and exfiltrate data. RedLine behaves similarly to Raccoon, uploading and downloading files, executing commands, and reporting information about the infected machine. Attackers also use RedLine to deliver ransomware, RATs, Trojans, and miners. Figure 5 shows the capabilities of RedLine Stealer. RedLine can be obtained for a subscription and costs $100-$200 per month.
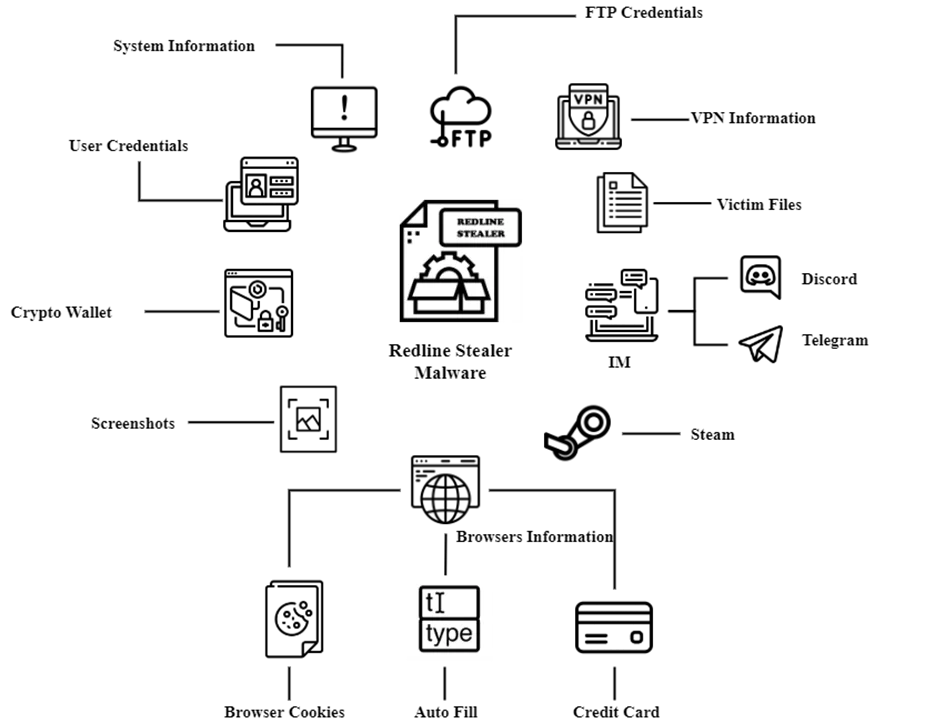
Figure 5 – Execution flow of RedLine stealer
RedLine is distributed through malicious email attachments, exploit kits, and infected downloads. Once activated, it injects malicious code into legitimate Windows processes, making detection challenging.
Key Features
- Living-off-the-Land Techniques: RedLine leverages legitimate Windows utilities and scripts to carry out its malicious activities, making it difficult to distinguish from normal system behavior.
- Process Hollowing: It uses process hollowing to inject its malicious code into legitimate processes, evading detection by traditional security solutions.
- Exfiltration: RedLine employs encryption and disguises its data exfiltration traffic as legitimate network traffic.
The impact of RedLine can range from sensitive data exposure to unauthorized access and financial loss.
Conclusion
Stealer malware like Raccoon, Vidar, RedLine, and Lumma pose significant threats to individuals and organizations alike. The repercussions of infostealer attacks can be severe, leading to data breaches, financial losses, and compromised privacy.
As an example of a recent event, the Airbus cyber-attack incident that occurred in mid-September 2023, more than 3,200 Airbus vendors’ data was leaked by hackers (shown in Figure 6). Investigations into the cause of this major leak revealed that a Turkish Airlines employee’s device had been infected with ‘RedLine’ malware, exposing a large amount of sensitive data.
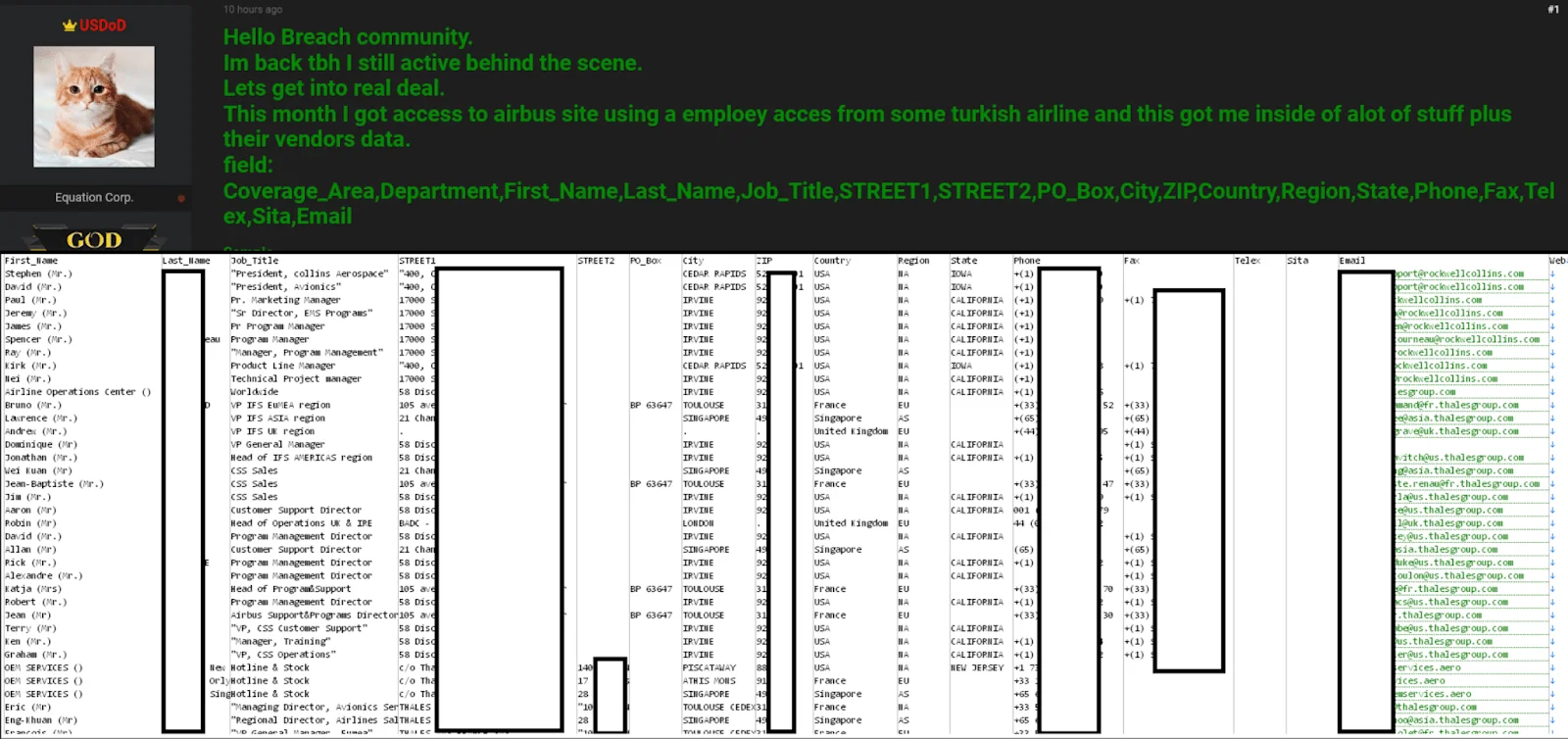
Figure 6 – Announcement of stolen data in a hacker forum regarding latest Airbus incident
SOCRadar helps you to protect your valuable assets by preparing you and your organization against such leaks, which have been on the increase recently. With the alerts it sends, it becomes your **Eyes Beyond**, providing threat intelligence against stealer malware such as Raccoon and RedLine.
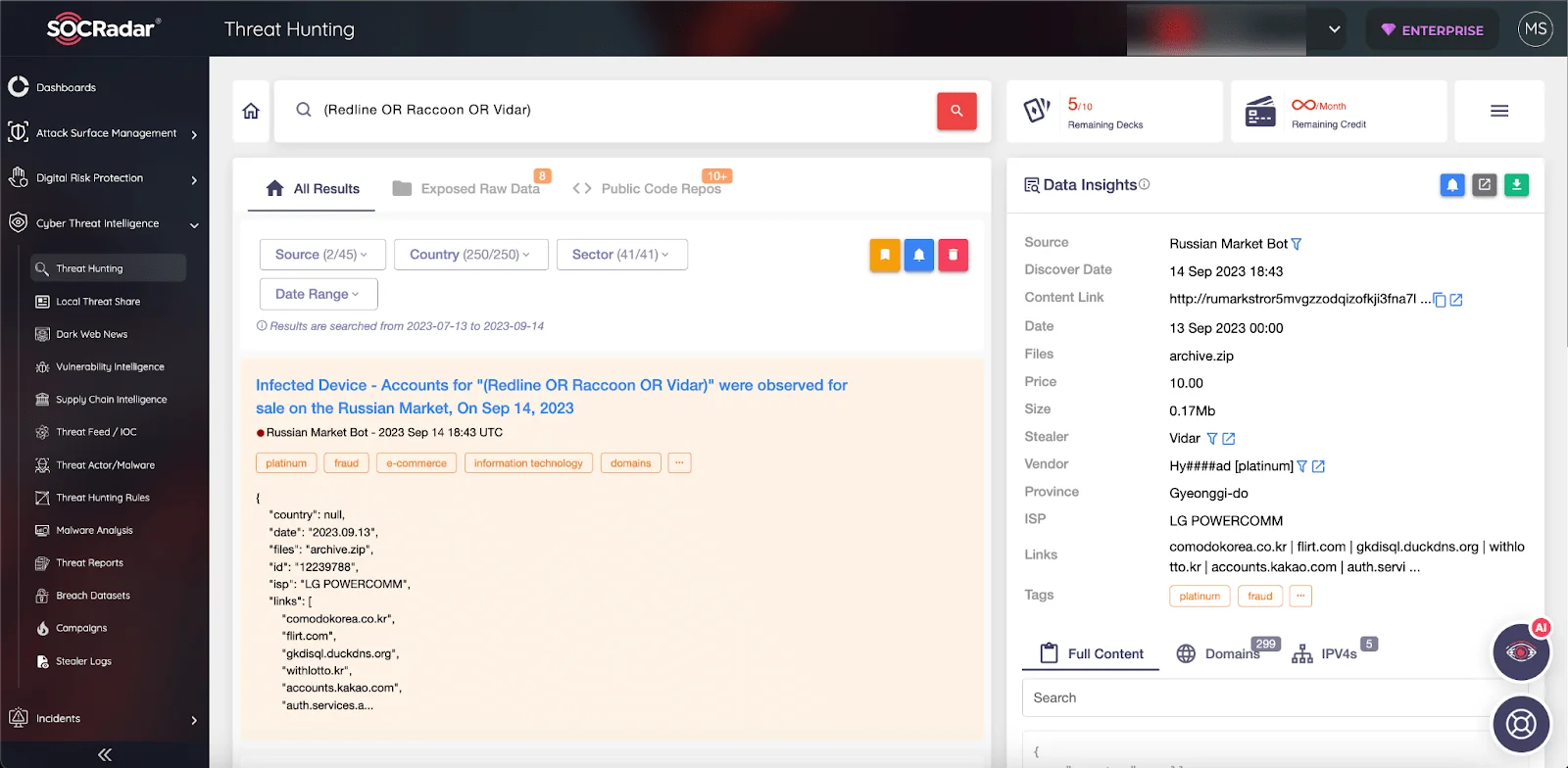
Figure 7 – Threat Hunting module by SOCRadar
With SOCRadar’s Threat Hunting, you can examine whether your valuable assets are safe, and with Threat Actor/Malware, you can examine the details of malicious software and access IoCs, among many other modules.
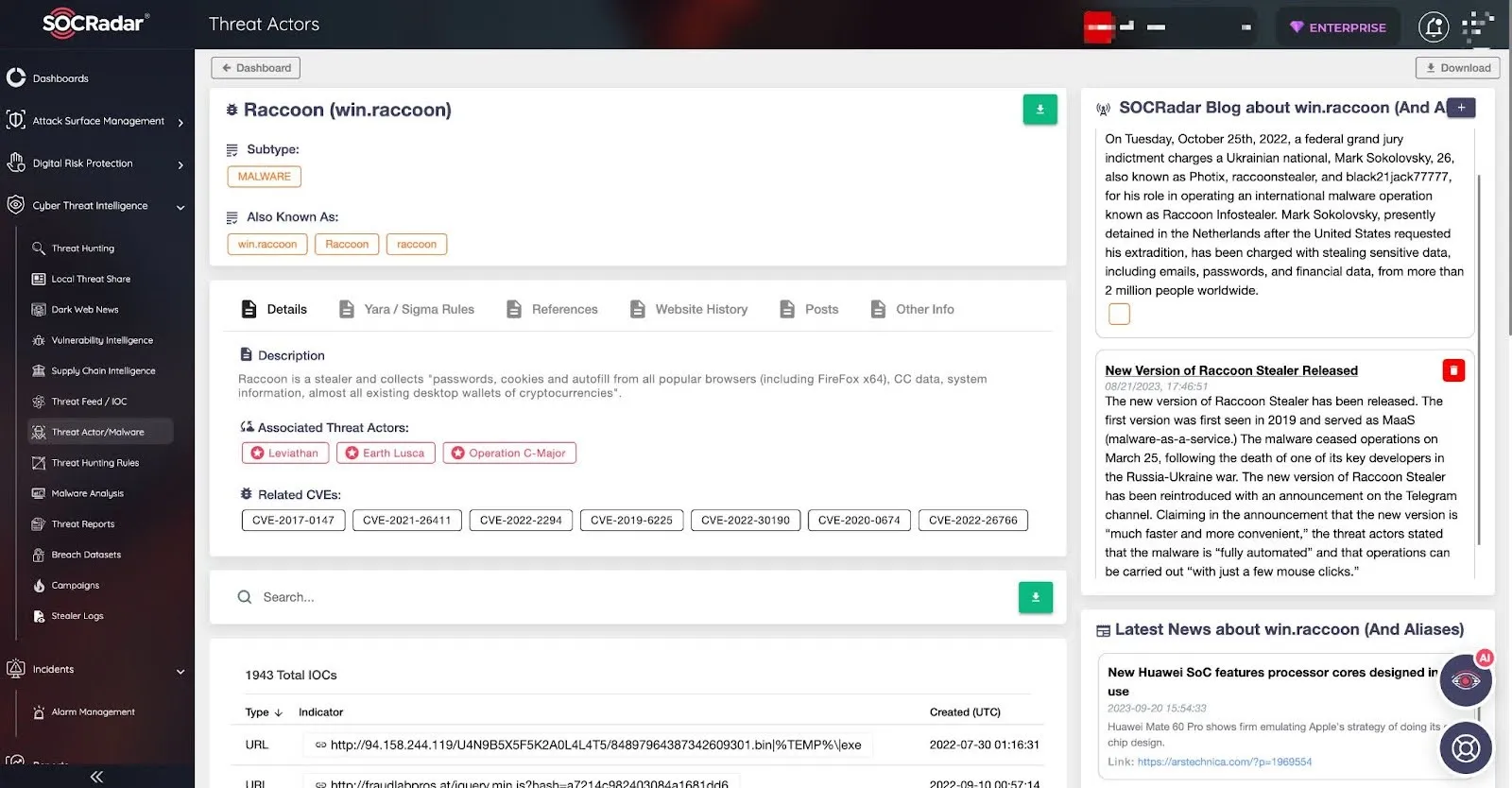
Figure 8 – Threat Actors page offered by SOCRadar platform




































