
The Leidos Leak: What to Know, What Are Its Implications?
In July, a post on BreachForums brought to light a significant leak involving Leidos Holdings Inc., claiming the exposure of internal files. Leidos Holdings Inc., based in Virginia, stands as one of the primary IT service providers to the U.S. government. Upon becoming aware of the issue, Leidos indicated that the compromised documents were from a previously reported breach of a third-party system they used, while the investigation was still ongoing.
Leidos’ notable clientele includes the Department of Defense (DoD), the Pentagon, Homeland Security, and NASA. This association amplified concerns within the cybersecurity community upon the leak’s revelation.
In this blog post, we will examine the threat actor’s claims, the incident’s background, and the information that is claimed to have been compromised, and what it entails.
The Initial Post – Leidos Leak, Part 1
On July 10, a threat actor posted claims of possessing data from Leidos. The leak purportedly included internal documents of the company, comprising various file types such as ZIP archives, text documents, and images. The threat actor aimed to profit from this leak by selling the data.
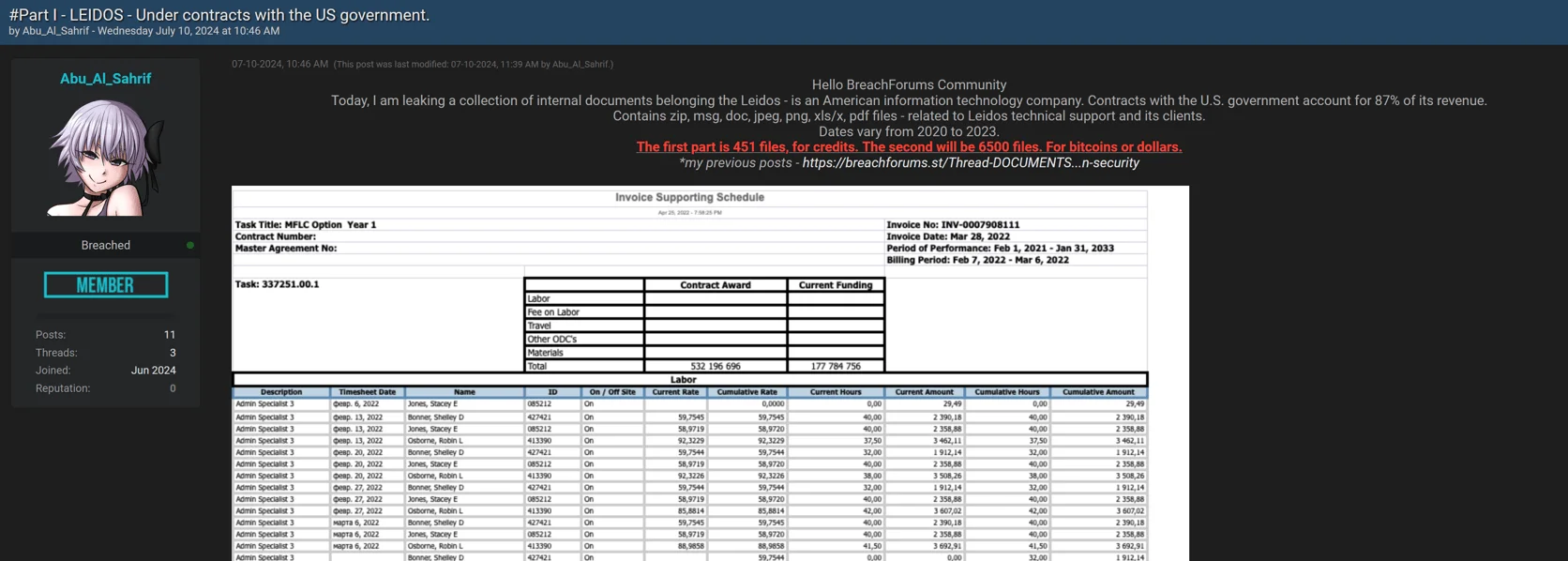
Leidos leak post, part 1
The initial post detailed the leak’s total size, the types of files present, a list of filenames, and screenshots of documents. The threat actor claimed this first part of the leak involved 451 files, which were put up for sale in exchange for forum credits.
The threat actor also announced a forthcoming second sales post demanding higher payments in bitcoins and dollars. This second part was said to contain 6,500 files, significantly more than the initial leak.
The nature of the leaked data allegedly relates to technical support and its clients; there is controversy about the sensitivity of the information and whether it might lead to real complications.
Leidos Leak, Part 2
The second leak post appeared on July 21, over a week after the initial post. This post briefly listed the total size of the file types included in the leak, with ZIP archives constituting the majority of the alleged breach.
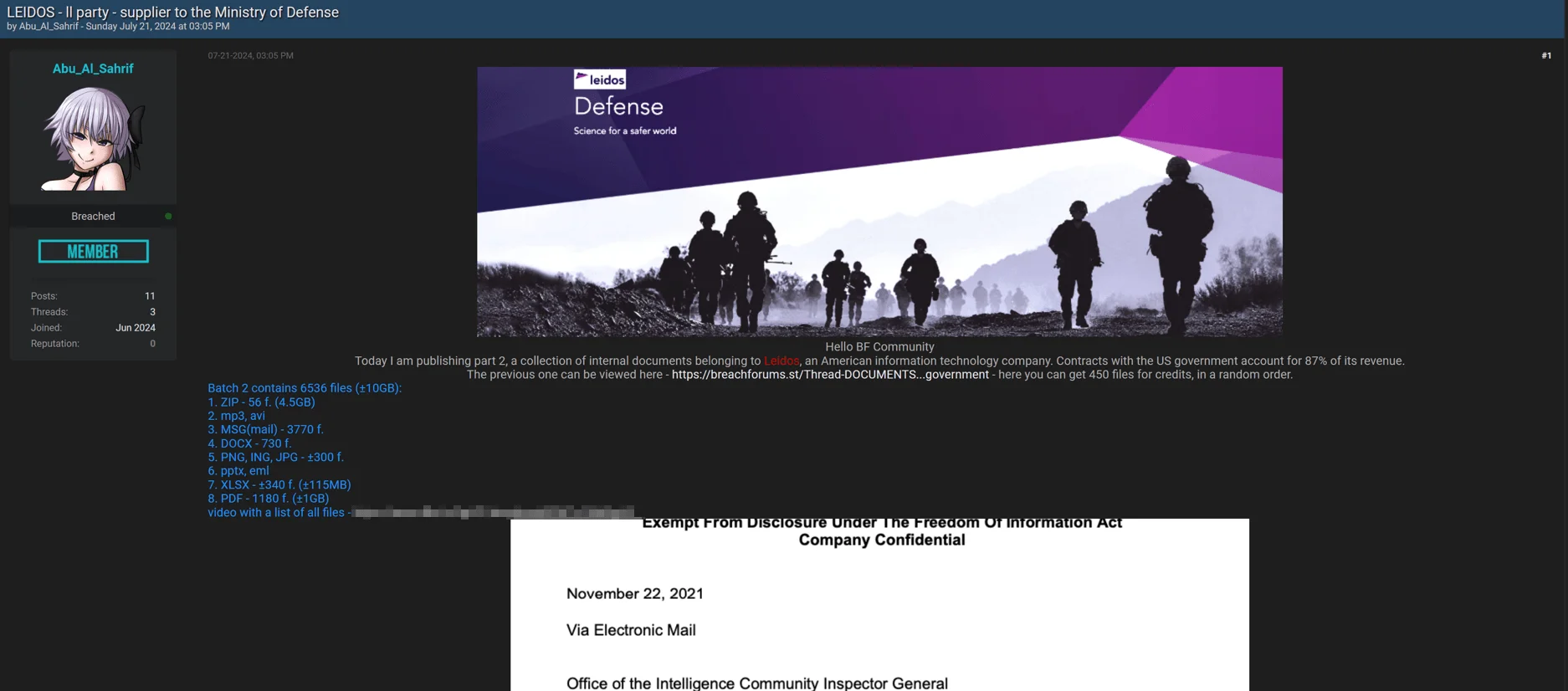
Leidos leak post, part 2
This series of posts by the threat actor emphasized the escalating nature of the leak, suggesting an expanding threat to Leidos and its clients.
Stay informed about the latest events and trends in the dark web landscape with SOCRadar’s Dark Web News. This module enables you to access the latest posts from deep and dark web forums, along with various hacker channels like Telegram, providing insights into emerging threats.
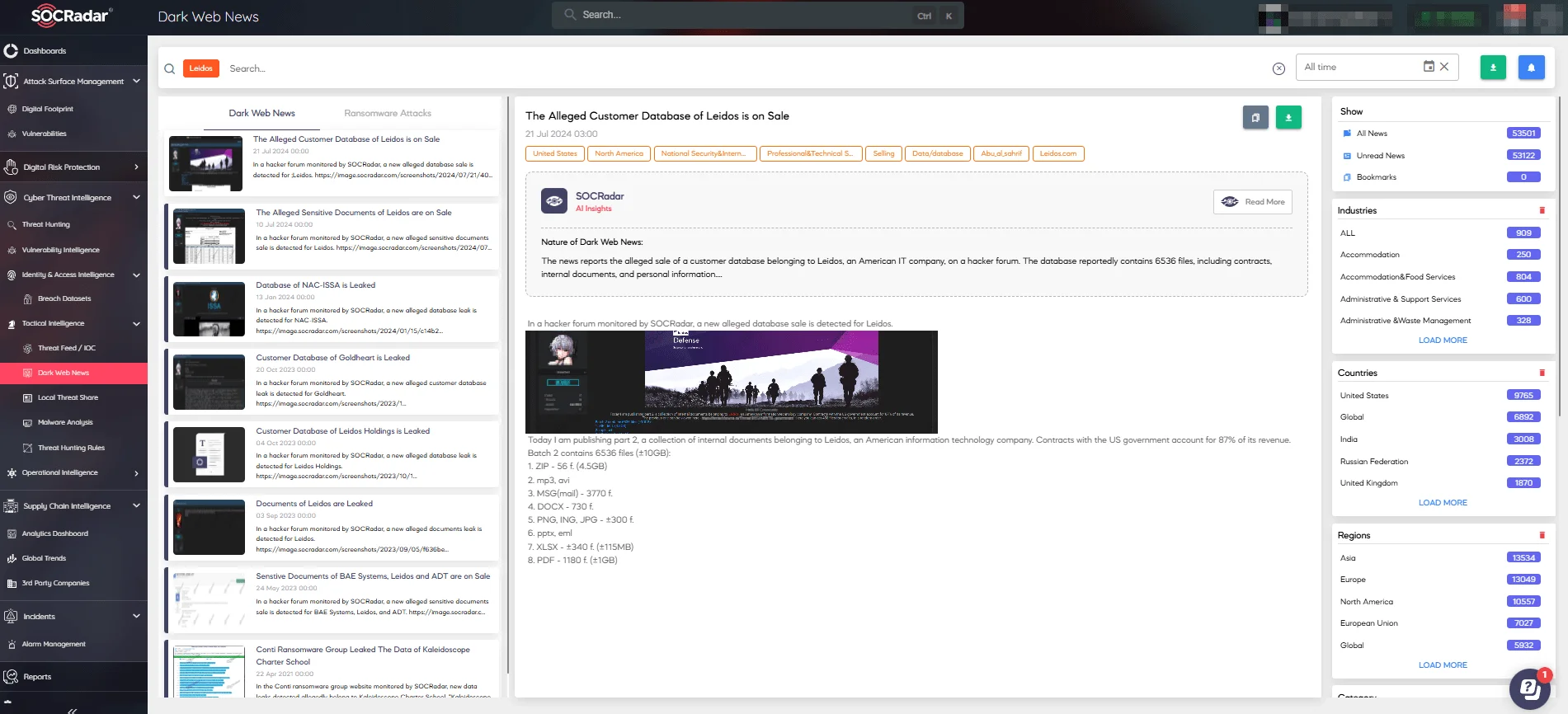
SOCRadar’s Dark Web News. Check out its free version, DarkMirror, on SOCRadar LABS
What Is the Content of the Leidos Leak?
To gain a clear understanding of the Leidos leak, we examined the contents of both parts, which involve reports and various forms of data on internal matters.
The data pertains to specific incidents, communications with external parties about discrepancies in reported activities, and responses to grievances about inappropriate use of company resources.
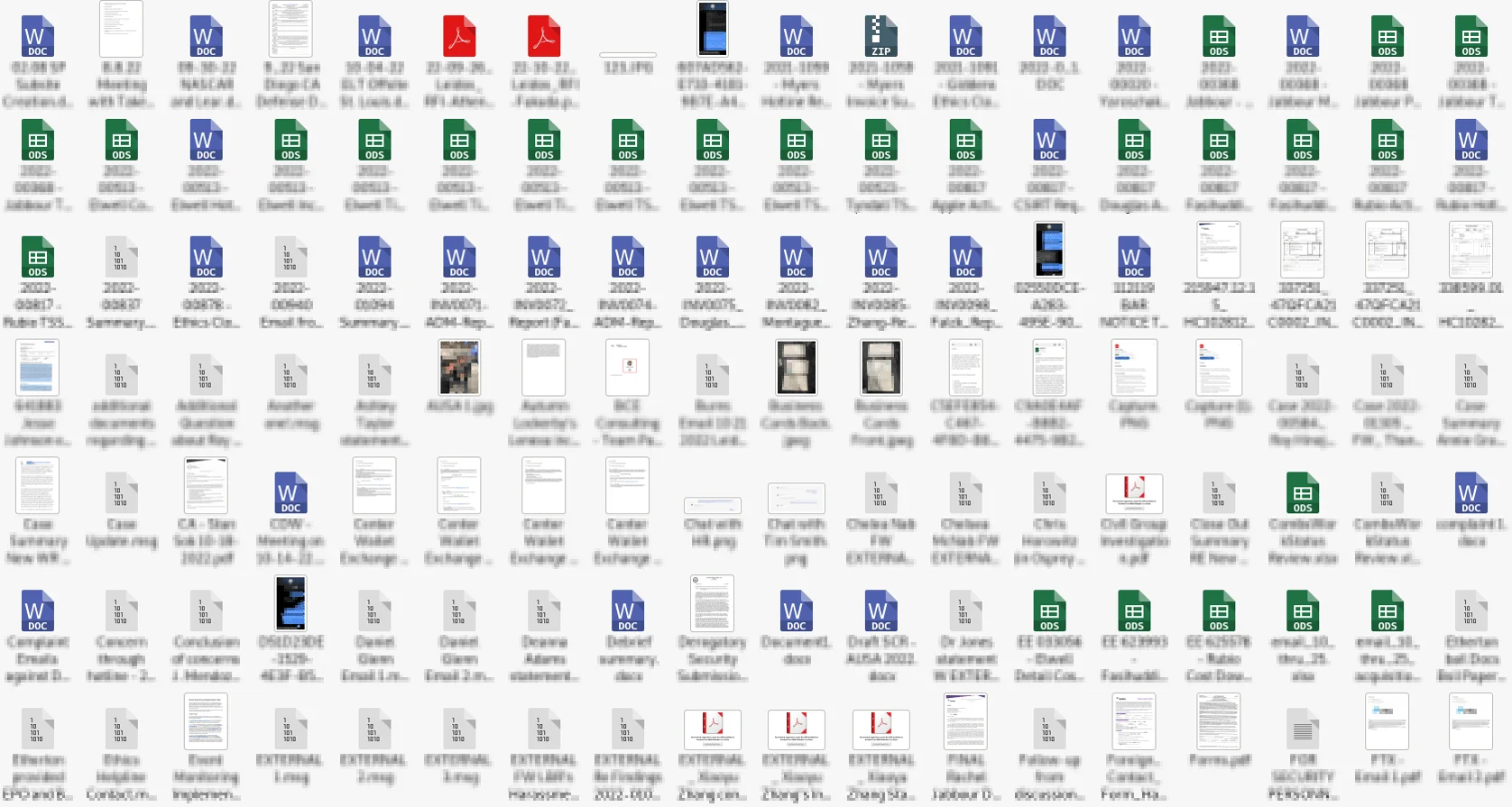
Files from the first part of the leak
The first part of the leak includes reports and documents concerning internal issues, such as a PDF file addressing an overpayment issue. Presentation slides and data sheets related to internal operations are also included, but nothing of significant interest or highly sensitive nature.
A PDF file from the leak
The second part of the leak contains many more files, including sensitive internal communications from 2021-2022. These documents reveal significant issues within the organization, such as:
- Allegation reports of harassment and hostile work environments,
- Retaliation claims,
- Cases of time card mischarging,
- Reports of inappropriate conduct,
- Investigations into potential data exfiltration and network activity violations,
- Records of stolen equipment,
- Various corporate security concerns,
- Requests for employee termination,
- Reports of misuse of government resources,
- Documents on review processes, and more.
This data could offer potential threat actors a glimpse into the internal challenges and security issues faced by Leidos, highlighting potential vulnerabilities and areas of concern for the company and its clients. Individuals involved or mentioned in these documents may be targeted with phishing attacks, as they could serve as background information for a variety of social engineering scenarios aimed at employees.
Advanced dark web monitoring with SOCRadar XTI keeps you ahead of cyber threats, protecting your data and reputation. The SOCRadar platform offers monitoring across all internet surfaces, including the dark web and the deep web. The Dark Web Monitoring module acts as a digital periscope, detecting and tracking unauthorized data distribution across hacker channels.
By keeping watch on dark web discussions and activities related to your organization, SOCRadar ensures you’re always informed of potential threats and can respond swiftly.
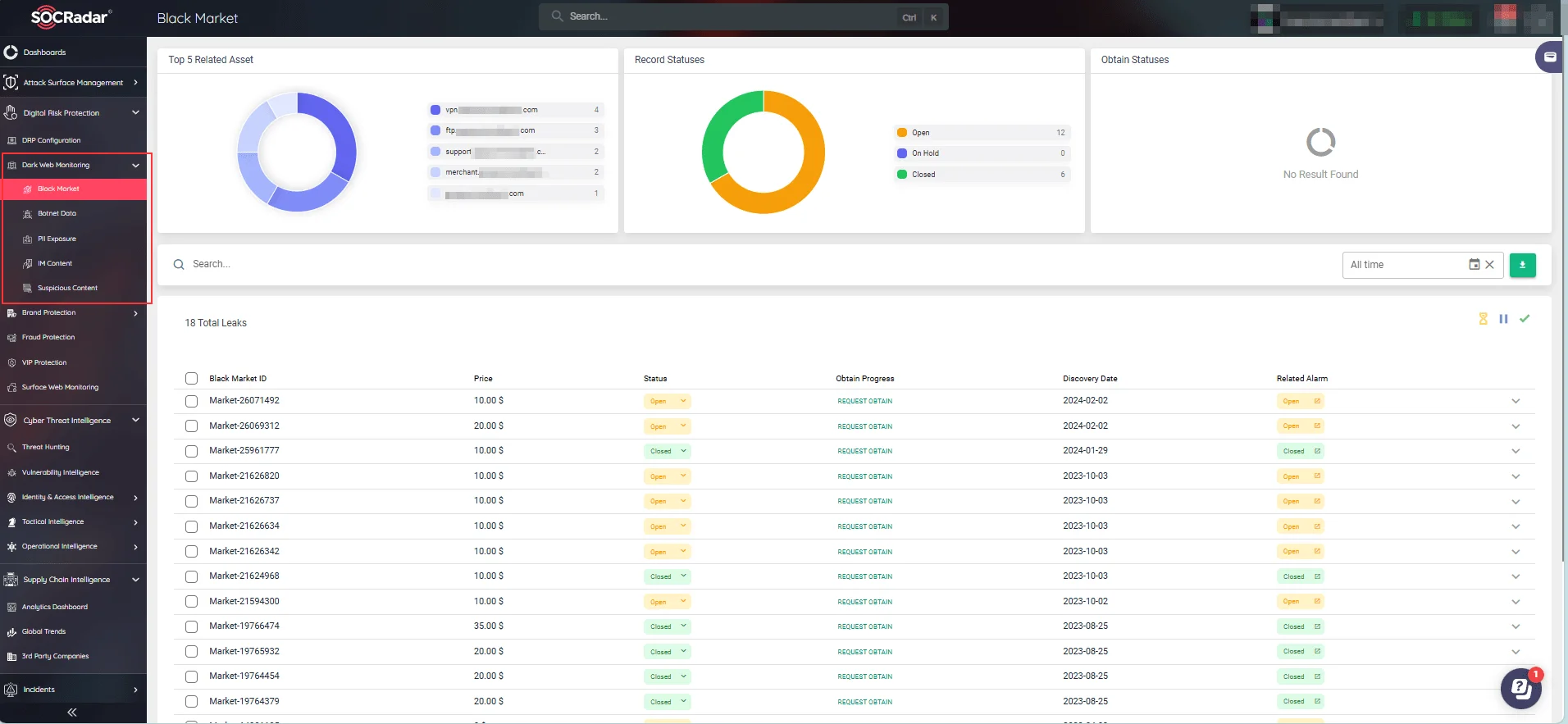
SOCRadar Dark Web Monitoring module
What Is the Impact of the Leidos Breach on Government Security?
Based on the type of files involved in the Leidos leak, it is unlikely to pose a direct threat to the government bodies. The documents primarily include internal reports and communications focused on company-specific issues and internal administrative matters rather than classified or highly sensitive government information.
It’s important to consider that certain threat actors may specifically target government bodies. For instance, in September 2023, we reported on a specific Telegram channel that allegedly sold classified intel on the Pentagon. However, the recent Leidos leak does not involve such files.
The leak highlights internal challenges and vulnerabilities within Leidos but does not directly impact the operations or security of their government clients. The documents do not contain sensitive government data that would directly compromise national security.
Leidos has confirmed that the leak did not affect their network or compromise sensitive customer data. While the breach is serious, at its current threat level, it does not endanger the security or operations of its government clients.
In summary, the primary risk of the Leidos leak is to the company’s internal operations and employees.
How Did It Happen? Here’s the Background of the Leidos Leak
The leak of Leidos’ documents stems from a prior security incident involving a third-party vendor, Diligent Corp. Leidos confirmed that the stolen documents were a result of two breaches of Diligent in 2022. These documents were stored on Diligent’s system, which Leidos used to host information gathered from internal investigations.
The Diligent system, designed for security compliance and incident tracking, contained files related to incident reports and compliance requirements, which aligns with the types of documents found in the leak.
Diligent Corp., through its subsidiary Steele Compliance Solutions, was hacked in 2022. Steele Compliance Solutions, which Diligent acquired in 2021, had fewer than 15 customers, including Leidos, using its product at the time of the breach. Following the breach, Diligent notified the affected customers and took action to contain the incident in November 2022. Leidos also clarifies that all necessary notifications were made in 2023.
About the Diligent Corp. Data Breach (2022)
Looking into the incident from Diligent Corp’s perspective, the incident timeline began when they informed Leidos on November 11, 2022, about a vulnerability that had been exploited to download documents, potentially starting from September 30, 2022.
A second exploitation was reported on February 9, 2023, which allowed unauthorized access to information submitted to Leidos via their Enterprise Case Management System (ECMS), possibly beginning from October 1, 2022.
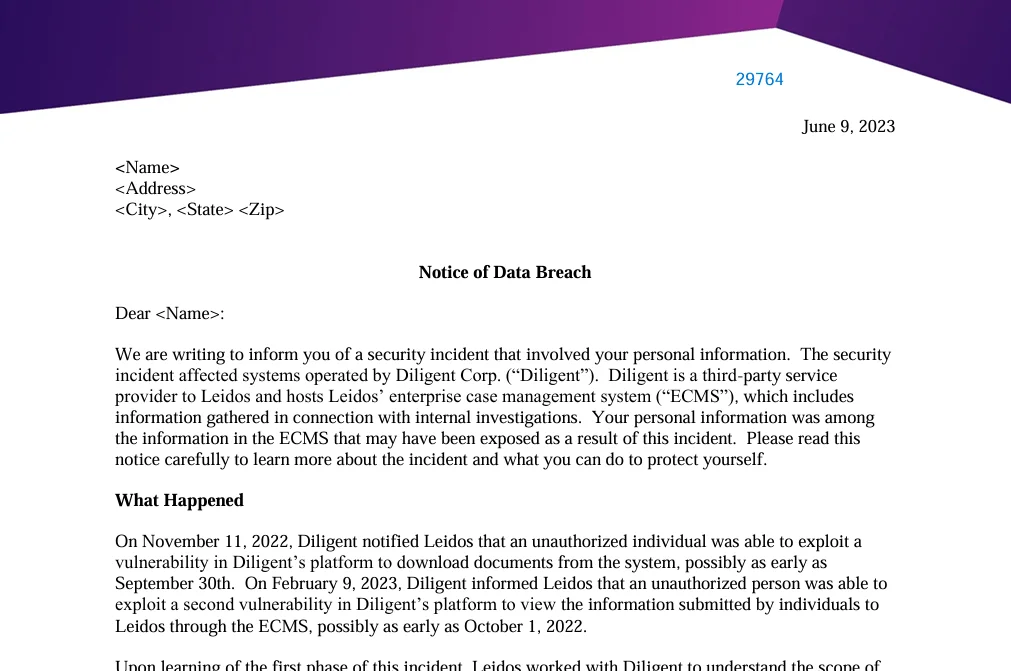
Notice of the Diligent Corp. data breach (mass.gov)
Leidos collaborated with Diligent to assess the scope of the breaches. Initially, Diligent provided copies of affected documents but could not specify their contents or confirm if personal information was compromised.
Leidos conducted manual reviews to identify any personal information and the affected individuals. When the second phase of the incident was discovered, Leidos requested all impacted information from Diligent and manually reviewed it to confirm the involvement of personal data.
The recent leak circulating on dark web forums is connected to this earlier incident. Moreover, Leidos has asserted that this leak did not impact their network or compromise any sensitive customer data.
Enhance your third-party risk management strategy with SOCRadar’s Supply Chain Intelligence module. This advanced tool offers continuous and detailed vendor assessments, to help you determine if your partners maintain top-tier security practices. By automating the detection and mapping of third-party environments, SOCRadar provides a comprehensive view of potential vendor security threats.
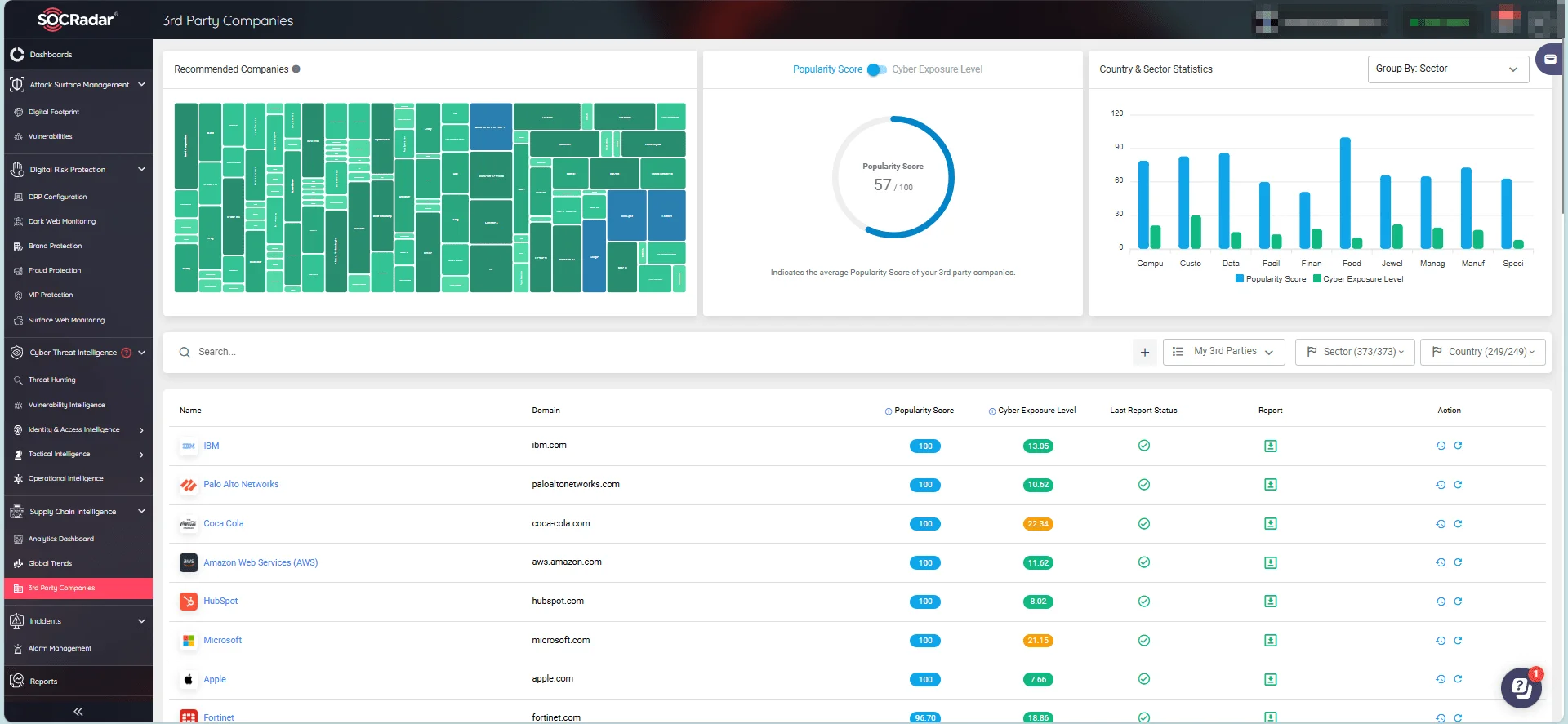
Monitor your third-party companies; keep track of popular vendors and their cyber exposure levels. (SOCRadar Supply Chain Intelligence)
Recommendations
To ensure the security of your organization and prevent incidents like the Leidos leak:
- Enhance Third-Party Risk Management:
- Conduct thorough and continuous security assessments of third-party vendors. For detailed vendor evaluations, use platforms like SOCRadar’s Supply Chain Intelligence module.
- Ensure that vendors maintain high-security standards, particularly those handling sensitive data. This involves scrutinizing their security protocols and incident response strategies.
- Implement Data Protection Measures:
- Encrypt sensitive data both at rest and in transit to prevent unauthorized access.
- Implement strict access controls to limit who can access sensitive information. Use role-based access to minimize the risk of insider threats.
- Advanced Threat Detection and Monitoring:
- Perform regular security audits to identify and mitigate security issues within your systems.
- Utilize advanced dark web monitoring tools like SOCRadar XTI to detect and track unauthorized distribution of data and potential threats.
- You can utilize SOCRadar’s Attack Surface Management (ASM) module to receive critical security alarms, regarding vulnerabilities and other attack vectors.
Alarm: Company-related information detected in exposed raw data (SOCRadar Alarm Management)
Conclusion
The Leidos Holdings Inc. data breach, surging on BreachForums in July, has raised significant concerns due to the company’s prominent role as an IT service provider to various U.S. government agencies, such as Pentagon, and the Department of Defense.
The leaked documents, believed to have originated from a 2022 breach of a third-party vendor, Diligent Corp., included sensitive internal communications and reports on a variety of issues.
Due to the nature of the breach, it is unlikely to pose a direct threat to the government agencies Leidos serves. The leaked documents mainly involve internal reports and communications; consequently, the primary risk remains to Leidos’ internal operations and its employees rather than to the security and operations of their government clients.




































