
‘Classified’ Intel on the ‘Public’ Telegram Channel: Pentagon US Leak
In the rapidly evolving landscape of digital communication, Telegram has emerged as a prominent platform for various user groups from underground circles. The channels, groups and private chat rooms established by threat actors have exponentially increased. Among these, the channel “Classified Document Sale” has drawn significant attention for selling sensitive data, specifically belonging to the United States. The channel marked a start with its first sale, offering data allegedly linked to the recent Pentagon leak incident.
The rise in popularity of the channel and the valuable documents it offers for sale have sparked interest in the backstory. Who is responsible for operating the channel? What types of classified documents are offered for sale? How were these documents obtained, and are they exclusively accessible through this platform?
Preview of the Channel
The channel was created on April 11, 2023 and has 1.42K subscribers currently. The first sale purpose post aired on the channel was published on April 12, marking a prestigious start with the expression ‘Pentagon US Leak FOR SALE‘. It seems the channel wanted to fill its sails with the winds of the ‘Pentagon Leak’ incident in early April.

The subsequent entry was a post detailed in 6 categories with screenshots presented as evidence and price offers. In the following one, a collection of files tagged as ‘Pentagon Leaks’ was promoted once more.
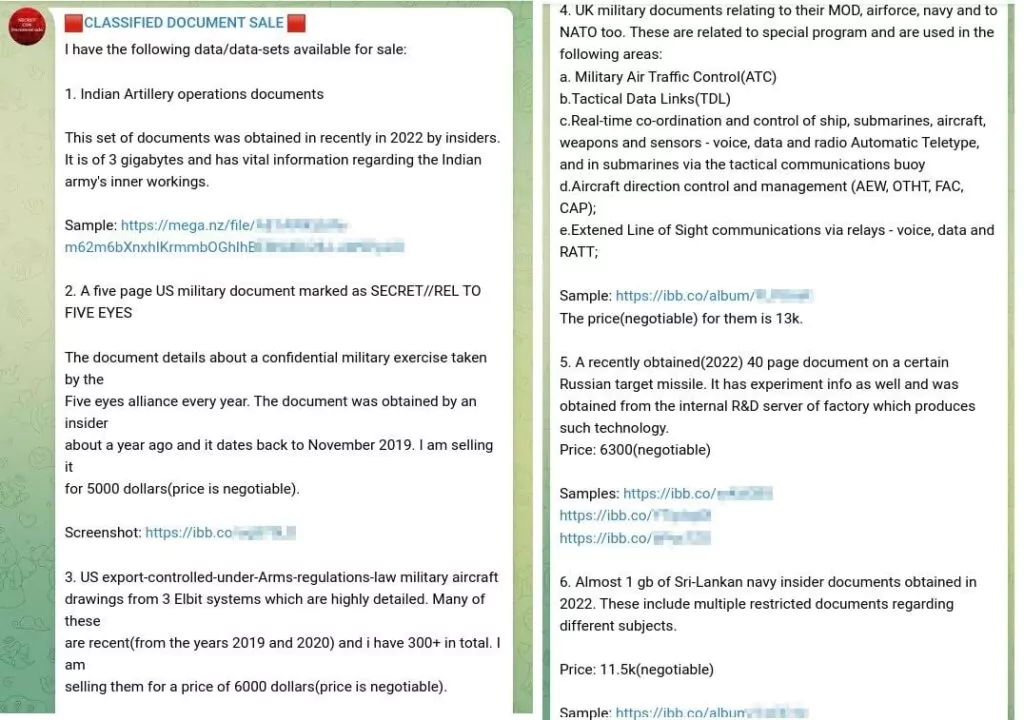
Two of the initial three sales offerings posts explicitly reference the Pentagon Leak. Following this pattern, some of the upcoming posts consistently share files that align with the information originating from this prominent leak.
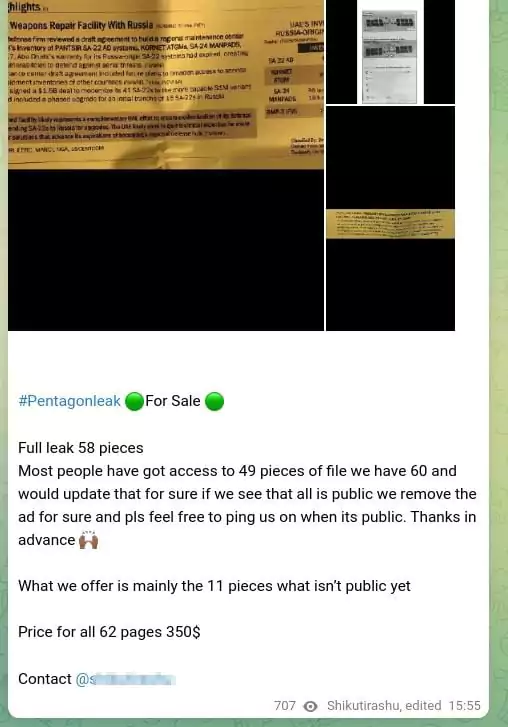
Additionally, posts about the updated list, new price offers, and single or bulk sale ads are frequently published.
Those belonging to Raytheon Technologies stand out among the documents offered for sale. Raytheon is an American multinational aerospace and defense conglomerate and one of the major defense contractors that produces a wide range of electronic systems for the US military. It is especially thought-provoking that a file dated June 2, 2023 was put up for sale on June 7, 2023.
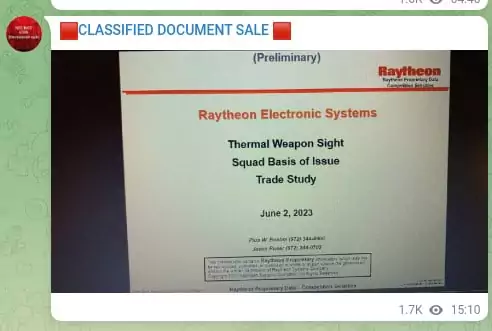
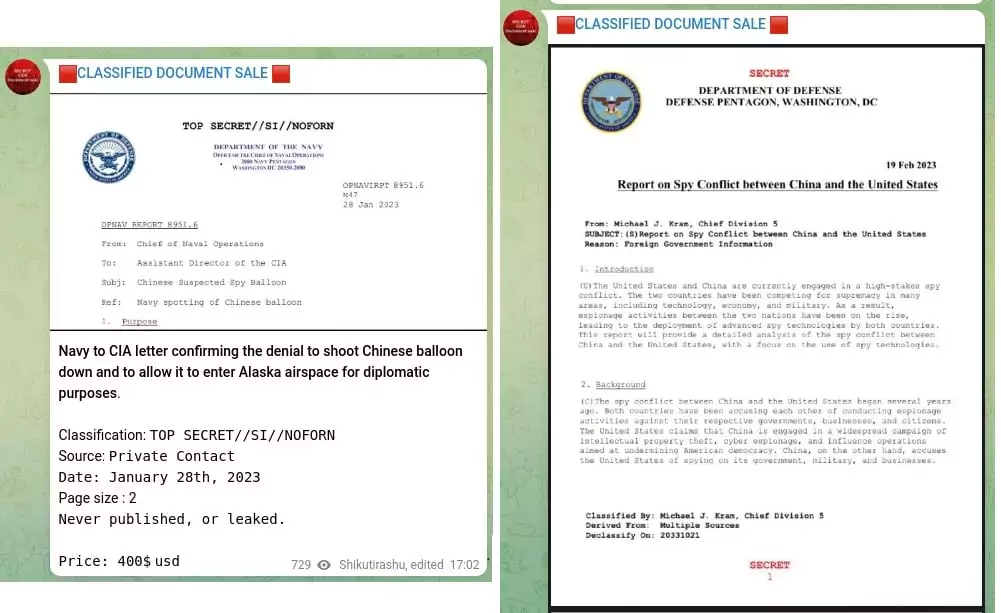
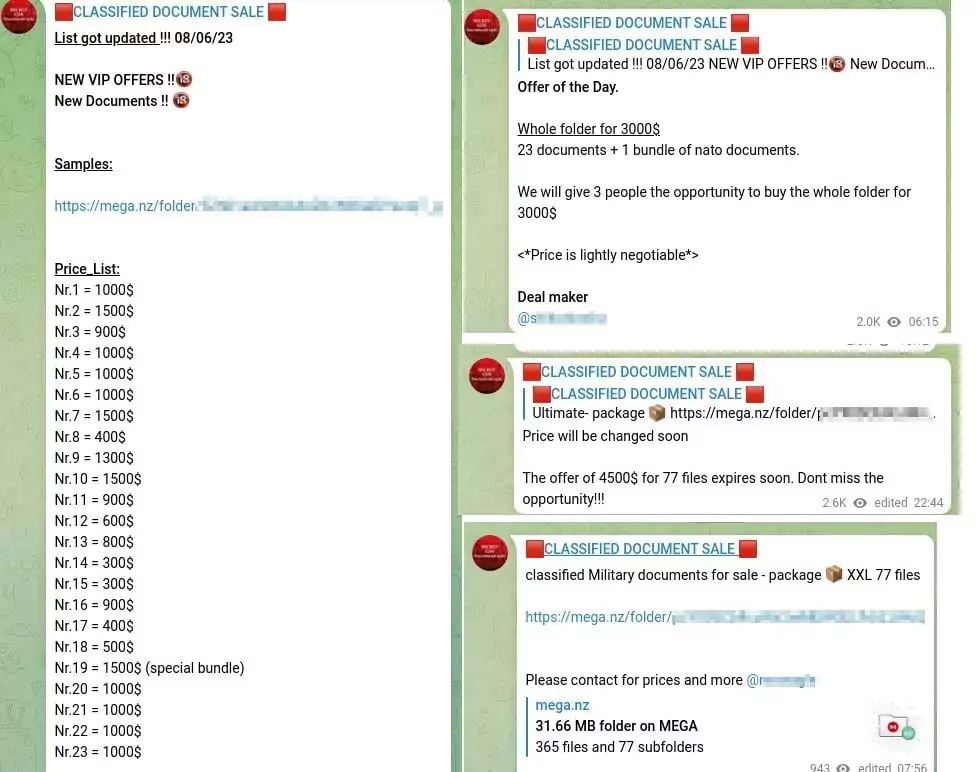
The channel also offers recently published military documents for sale as shown below.
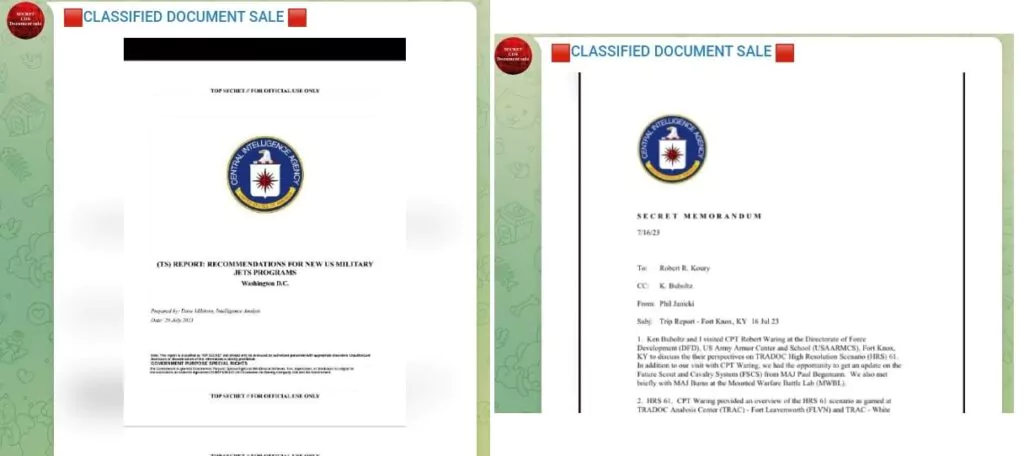
The Background of the Pentagon Leak
Given the channel’s inception date, the timing of document sharing, and the type of shared documents, it appears that one of the primary motivations behind setting up the channel revolves around selling files from the Pentagon leak.
The Pentagon leak was one of the most significant U.S. security breaches since the 2010 WikiLeaks incident. This breach is comparatively small; however, it is crucial due to containing up-to-date information.
These leaked documents appear to provide insights into U.S. and NATO assistance to Ukraine and U.S. intelligence evaluations that could strain relationships with allied nations. Among the information are real-time details from February and March, outlining the positions of Ukraine and Russia on the battlefield and specifying the quantities of battlefield equipment being supplied to Ukraine by its allies.
The leaked documents surfaced in the report of the New York Times on April 6. The Justice Department promptly launched an investigation, and by April 13, the FBI had apprehended the suspected leaker, 21-year-old National Guard airman Jack Teixeira.
Jack Teixeira is a member of the U.S. Air Force’s 102nd Intelligence Wing, an integral part of the Massachusetts Air National Guard. As a “cyber transport systems specialist,” he oversaw military communication networks, encompassing cabling and hubs. Teixeira held access to the Joint Worldwide Intelligence Communications System, a Defense Department hub for top-secret data.
The leak materialized as photographs of printed briefing materials and slides. Some papers exhibit signs of being folded and unfolded before photographing. These documents, mostly created between February and March, were derived from intelligence gathered by prominent agencies such as the NSA, CIA, Defense Intelligence Agency, DEA, and the National Reconnaissance Office, responsible for U.S. spy satellite management. Notably, markings on the documents indicate a classification for sharing with allies or for U.S. exclusive viewing.
Jack Teixeira allegedly distributed these documents within a private chat room named ‘Thug Shaker Central’ on the Discord social media platform. It was claimed that nearly half of the chat group participants resided abroad, and mostly those from Eastern Bloc and post-Soviet countries were interested in the classified content. The documents were reposted across various Discord groups before disseminating to platforms like 4chan, Telegram, and Twitter. According to sources, over 300 documents might have been leaked this way.
The Adventure of the Pentagon Leak
- Late 2022: Leakers began releasing classified information on a private discord server named ‘Thug Shaker Centra.’
- March 1-2: A user from the Thug Shaker Central server begins posting classified document photographs on another Discord server linked to YouTuber “wow_mao.”
- March 4: 10 documents appear on the “Minecraft Earth Map” Discord server, obtained from wow_mao, focusing on the popular video game. Secret and top-secret documents become accessible to thousands of Discord users.
- April 5: Classified documents analyzing the Ukraine war are posted on Russian Telegram channels and the 4chan message board platform. ‘Donbass Devushka‘ is the first Telegram channel found to be posting documents.
- April 6: The New York Times reports on the leak.
- The documents continued to be spread on Twitter.
| ❗ | NO COMMENT: It reported that Sarah Bils, a former aviation electronics technician 2nd Class, most recently stationed at Naval Air Station Whidbey Island, was allegedly behind the Donbass Devushka Telegram channel and associated accounts on various social media platforms. The channel identified as the initial source of the Pentagon leaks on Telegram. |
The Contents of the Pentagon Leak
- Russian Flanking Maneuvers near Bakhmut:
Ukrainian military discussions and response strategies.
Supply shortages in the area.
- Ukrainian Forces Situation and Morale, Casualty Estimates and Military Resources:
U.S.-provided military resources to Ukraine.
Estimated Russian and Ukrainian casualties.
Number of soldiers killed in action for both sides.
- Russian Military Planning:
Russian strategies to counter NATO-provided tanks.
Plans to destroy drones near Odessa.
Impact of Russian military planning.
- Russia-NATO Aircraft Encounters and Shootdown:
The incident of a Russian fighter jet nearly shooting down a British surveillance plane.
Details of the encounter and potential consequences.
Encounters between Russian fighter jets and foreign aircraft.
- Weapons Used by Ukraine:
Depletion of Ukraine’s air defense capabilities by May.
Suggestions of striking within Russia using unmanned aerial vehicles (UAVs).
Use of the LAPIS satellite system by the Ukrainian military.
- Weapons Used by Russia:
Russia’s attempts to disrupt SpaceX’s Starlink systems in Ukraine.
- Western Special Forces and Countries Involved:
List of countries with military special forces operating in Ukraine.
Details of U.S. special forces’ role and location.
Efforts by Russian GRU for information warfare.
- Analysis of Various Countries:
Information warfare efforts by Russia in Africa.
Wagner Group’s presence and actions in Mali.
Analysis of peace talks between the U.S. and Russia.
Chinese military capabilities and cyber-attack developments.
- Efforts by Egypt, Iran, Pakistan, Serbia, South Korea, Israel, Taiwan, Turkey, Canada, Haiti, UAE, and Organizations:
Egypt’s alleged plan to sell rockets and artillery to Russia.
Iran’s discussions and surveillance of the International Atomic Energy Agency (IAEA).
Pakistan’s considerations of alliances with China and the U.S.
Serbia’s involvement in supplying weapons to Ukraine.
South Korea’s debates on providing artillery shells to Ukraine.
Israel’s pressure to provide lethal aid and its relations with Russia.
Taiwan’s assessment of China’s invasion capabilities.
Türkiye’s role in supplying weapons to the Wagner Group.
Canadian gas company compromised by a Russian cybercriminal group.
Wagner Group’s expansion plans in Haiti.
UAE’s ties with Russia and regional weapons repair facility.
- U.S. espionage targets and methods exposed in the leaks.
Backstage of the ‘Classified Document Sale’ Telegram Channel
The channel is managed by Mr. Eagle, a figure widely recognized as the mastermind behind the notorious “Atlas Intelligence Group” (A.I.G), a.k.a. the Atlantis Cyber-Army. Their presence came to light in May of the previous year, rapidly garnering attention due to their leader’s prominence, hiring cyber mercenaries for specific tasks, and offering a comprehensive array of services, such as exclusive data leaks, Distributed Denial-of-Service (DDoS) attacks, Remote Desktop Protocol (RDP) access, and even hacktivism.
Rather than limiting its scope to specific countries or sectors, the group stands out for its strategic business model. They pursue campaigns that yield the highest benefits for services, such as selling classified documents, databases, and exclusive initial access to organizations. Much like sharing Twitter data in January 2023 and December 2022, the acquisition and distribution of Pentagon Leak files underscore their proficiency in profitable ventures.
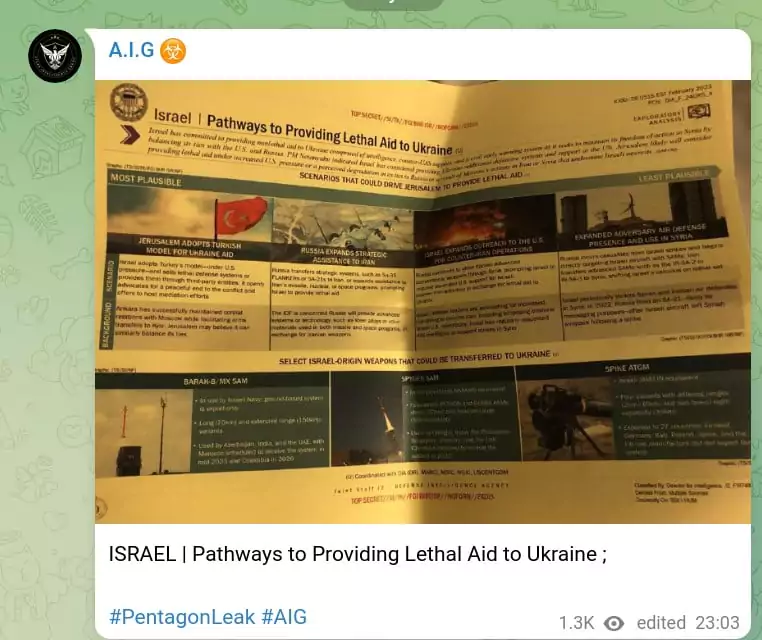
Interesting Fact about Atlas Intelligence Group
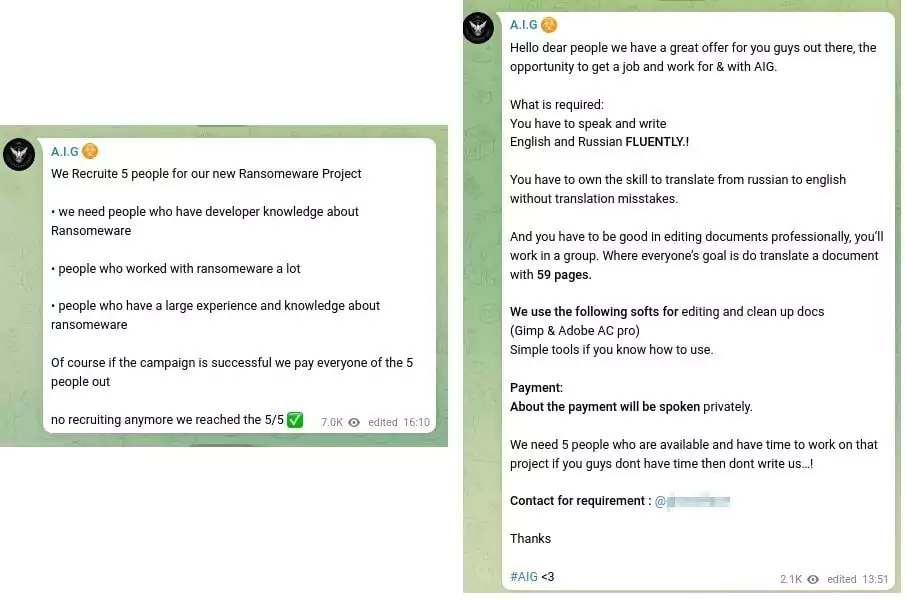
- Recruitment Posts: In line with the hiring independent cyber mercenary approach, one of the group’s prominent features, recruitment posts are frequently aired on the A.I.G. Telegram channel. The group, which previously announced the need of social engineer, pentester, and more to contribute to the malicious activities they will manage, recently published a recruitment post for experts to be used in ransomware attacks.
In addition, a recruitment post in early May for people who speak Russian and can edit documents drew attention.
| ❓ | Question Mark: When the Pentagon Leaks documents started to spread on the internet, it was observed that the number of casualties in the Russian-Ukrainian conflict was different in the versions of the same document published on April 5 on Telegram and 4chan. For this reason, it was thought that one of the documents had been altered by editing.
The A.I.G.’s search for people with editing skills raised questions about the allegedly recently dated documents, offered for sale on the ‘classified document sale’ channel. Are the documents genuine, or have they been dated in an edit to make them more attractive? |
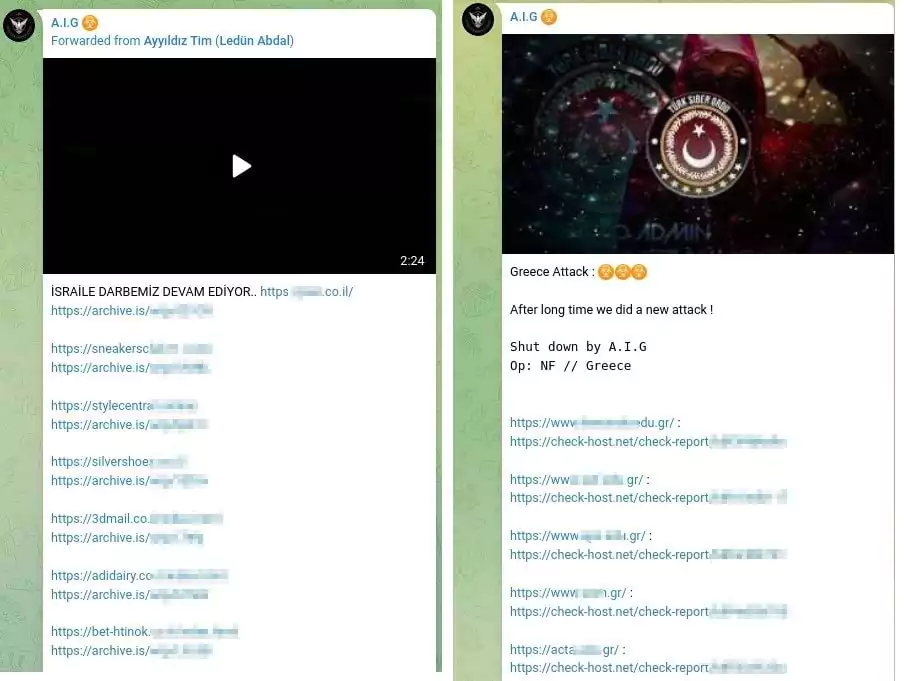
- Turkish-based group sharing: They forwarded a post by ‘Ayyıldız Team,’ a well-known Turkish threat actor group. In addition, they used the ‘Türk Siber Ordu – Turkish Cyber Army’ image to announce an attack they claim to have carried out againstGreece.
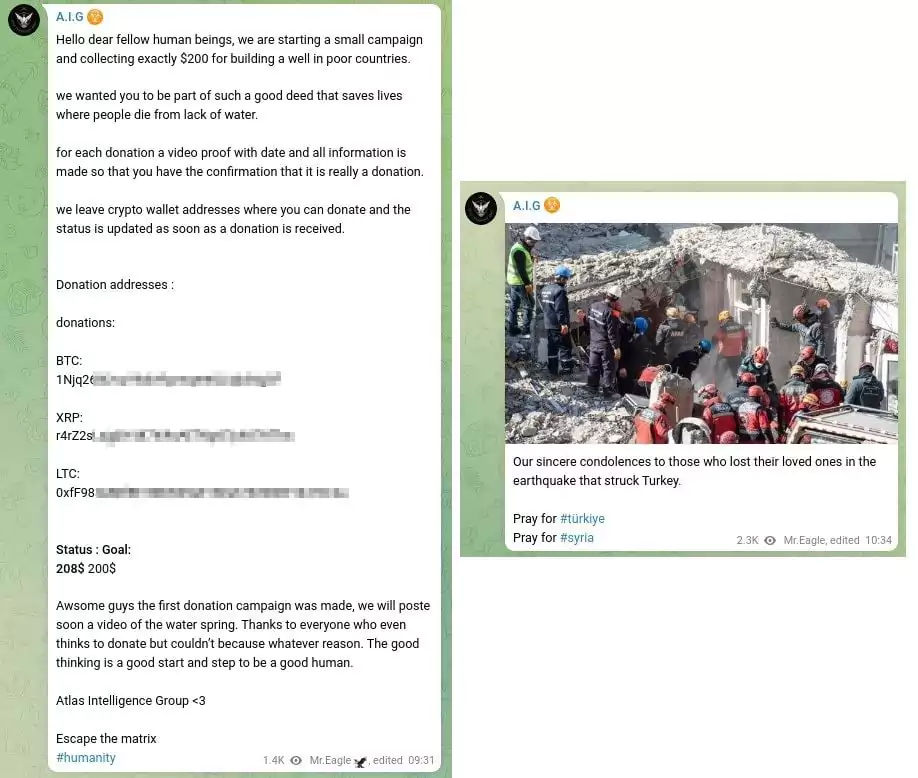
Humanitarian Posts: The group published a post announcing a campaign to drill water wells in poor countries. Furthermore, the group’s expression of condolences and sorrow for the tragic earthquakes that struck Turkey and Syria in February underscores a dimension that contrasts with their usual image.
Conclusion
Telegram channels have been a preferred platform for underground activities for a long time, with their popularity among threat actors. However, the limits of the incomprehensibly expanding digital world have reached such dimensions that even seemingly innocuous platforms like a gaming group or a fan-sharing site can unwittingly become breeding grounds for malicious activities.
New desires, such as being visible and attracting attention have been added to motivations such as money, espionage, and political interests. While malicious activities became easier for threat actors, especially insiders, with growing opportunities and environments for sharing and increasing motivation, security measures against them became more critical.
In the pursuit of comprehending and addressing these challenges as an extended cyber threat intelligence solution, the SOCRadar XTI platform remains vigilant, closely tracking underground activities, especially those found on dark web forums and Telegram channels. In addition, the Brand Protection module’s social media monitoring service closely scans potential breaches that may occur in social media and helps protect brand reputation.




































