
Top 10 DDoS Attacks
While the concept of a “DDoS attack” might seem intricate, its core essence is actually relatively straightforward. A common strategy involves overwhelming a targeted server with a barrage of communication requests originating from numerous machines. This onslaught incapacitates the server, rendering it unable to attend to legitimate user requests. Another approach disrupts the network connections linking users with the target server, essentially cutting off all communication between these entities.
The attacking devices are often dispersed across various geographical locations and utilize diverse internet connections. As a result, gaining control over these attacks becomes an exceedingly challenging endeavor. This situation can have significant adverse consequences for businesses, especially those heavily reliant on their websites – industries like E-commerce and SaaS-based enterprises come to mind readily. Furthermore, the concept of DDoS, which has been a fixture for a significant duration, maintains its presence as a formidable contemporary menace, progressively amplifying its intensity over time without diminishing its impact.
In this writing, we will list the most famous DDoS attacks from the past to the present and examine their changes over the years and their effects.
The Mafiaboy DDoS Attacks, 2000
During the formative stages of the internet’s security protocols, a young Canadian hacker going by the online alias “Mafiaboy” executed a massive Distributed Denial-of-Service (DDoS) assault in 2000, disrupting numerous high-profile websites. In this era, the term “DDoS attack” had not gained widespread recognition, and the Mafiaboy incident attracted considerable attention to this developing threat.
Mafiaboy, whose actual identity is Michael Calce, was a 15-year-old high school student from Montreal, Canada. Equipped with fundamental hacking know-how and driven to showcase his prowess, he initiated an assault on some of the internet’s most prominent platforms. In February 2000, Mafiaboy meticulously orchestrated DDoS attacks targeting major websites, including household names like Yahoo!, Amazon, eBay, CNN, and Dell. Employing a compromised computer network, colloquially termed a “botnet,” he inundated these websites with an overwhelming deluge of traffic. This inundation of traffic effectively flooded the servers, rendering the websites inaccessible to legitimate users.
![Figure 2. CNN’s website at that time. (blackhatethicalhacking[.]com)](https://socradar.io/wp-content/uploads/2023/08/cnn-website-unavailable.jpg.webp)
The repercussions of the Mafiaboy attack reverberated widely, affecting the targeted websites and the larger internet community. The websites in the crosshairs experienced extended downtime, incurring financial losses and tarnishing their reputations. The attack also underscored the vulnerabilities ingrained in the internet’s foundational structure and the latent potential for malicious actors to exploit these weaknesses. Ultimately, Mafiaboy faced legal ramifications for his actions and was brought to justice. In September 2001, he admitted guilt to 55 charges tied to the attack.
Nonetheless, the Mafiaboy incident reverberated as a clarion call for the Internet community, triggering debates about cybersecurity’s paramount importance and the pressing necessity for enhanced safeguards against DDoS attacks. It was an unequivocal demonstration of the considerable havoc an individual fueled by determination could wreak upon the digital landscape. This episode galvanized businesses and organizations to allocate resources toward bolstering their security measures, recognizing the imperative of proactive defense mechanisms.
The Estonia DDoS Attacks, 2007
During April 2007, the decision of the Estonian government to relocate the Bronze Soldier statue, a Soviet war memorial, from a prominent site in Tallinn to a military cemetery stirred profound discontent among the ethnic Russian population within Estonia, leading to demonstrations and civil unrest. Consequently, this controversy evolved into a cyber confrontation marked by organized DDoS attacks directed at key targets like Estonian government websites, financial institutions, media platforms, and crucial online services.
The DDoS attack against Estonia distinguished itself through its extensive scope and intricate execution. Perpetrators harnessed botnets, complex networks of compromised computers manipulated by malicious operators, to inundate designated websites and servers with overwhelming data traffic. The primary objective of this inundation was to disrupt the operational availability of online services, rendering these platforms inaccessible to legitimate users.
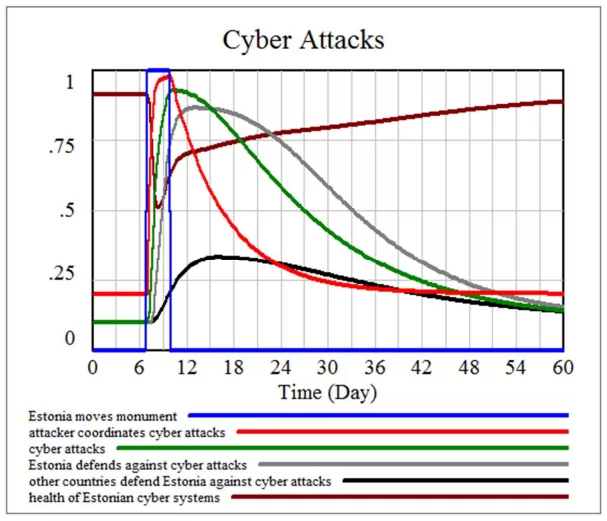
The repercussions of this assault reverberated significantly across Estonia’s digital framework and societal fabric. Government websites, financial institutions, media outlets, and other vital services confronted disruptions, causing financial setbacks and impeding the daily lives of Estonians. The gravity of the situation escalated to the extent that experts from NATO and the European Union were enlisted to assist in lessening the consequences of the attack and reinforcing Estonia’s cyber defenses.
Thus, this attack stands as a pivotal event in the history of cyber warfare. It underscored the vulnerability of modern societies to cyber-attacks and emphasized the importance of proactive cybersecurity and measures. Furthermore, the incident also raised awareness about the need for international collaboration in addressing cyber threats and paved the way for discussions on defining norms and rules for cyberspace.
The Six Banks DDoS Attack, 2012
The Six Banks DDoS Attack of 2012 involved powerful, coordinated attacks on major U.S. banks. These attacks aimed to disrupt online services, revealing digital vulnerabilities and the potential impact of such cyber assaults. A group named “Izz ad-Din al-Qassam Cyber Fighters” declared plans to launch DDoS attacks on key U.S. banks in protest. The attacks were supposedly retaliation for an anti-Islam video. Targets included Bank of America, JPMorgan Chase, Wells Fargo, U.S. Bank, PNC Bank, and Capital One.
Employing diverse tactics, the attackers used botnets and sophisticated application-layer attacks to flood targeted banks’ websites. The attacks were executed through a multitude of compromised servers drawn from a botnet known as Brobot, with each assault producing a staggering flow of over 60 gigabits of DDoS attack traffic per second. The Six Banks DDoS Attack significantly disrupted the targeted financial institutions. Prolonged traffic onslaughts led to online banking service interruptions and slower responses, underscoring large institutions’ vulnerability to cyber threats.
Banks responded by bolstering cybersecurity and collaborating with law enforcement and cybersecurity firms to investigate. Though the Izz ad-Din al-Qassam Cyber Fighters claimed responsibility, the group’s identity and motives remained contentious.
The Spamhaus Attack, 2013
Another instance of the largest-ever attack during that period occurred in 2013, targeting Spamhaus, an entity dedicated to countering spam emails and associated spam-related actions. Playing a pivotal role in filtering up to 80% of all spam, Spamhaus naturally drew attention from individuals keen on ensuring that spam emails reach their intended destinations. According to Cloudflare’s data, during this attack, an immense flow of traffic, surging at a staggering 300 Gbps, was directed toward Spamhaus. Once the assault was initiated, the consequences were swiftly felt.
Under the united banner of ‘STOPhaus,’ the assemblage comprised a diverse cohort of hackers who convened on March 17, 2013, to orchestrate what would rapidly evolve into an assault generating an overwhelming 300+ gigabits per second of traffic against spamhaus[.]org. The group perceived this anti-spam organization as an imminent threat to their spam-related endeavors.
The ‘STOPhaus collective realizes that Spamhaus has fortified itself with Cloudflare’s protection. After this point, attackers shift their focus from Spamhaus to Cloudflare, but the company manages to mitigate the threat.
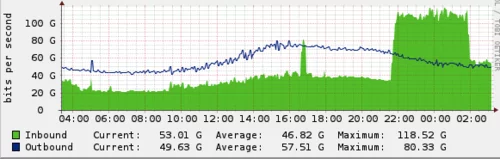
But, the attack, channeling a Torrent of around 300 billion bits of data per second, was of such magnitude that it briefly incapacitates Cloudflare, specializing in fortifying organizations against such attacks, causing a momentary service interruption. Cloudflare named it “The Attack that Almost Broke the Internet.”
The GitHub DDoS Attack of 2015
A pivotal moment in cyber history, this assault stood as the most massive DDoS attack recorded up to that point, and it coincidentally singled out GitHub as its target. According to CloudFlare, allegedly driven by political motives, this lengthy attack spanned multiple days, cunningly adapting to countermeasures against DDoS assaults. Originating from China, the surge of DDoS traffic focused on the URLs associated with two GitHub projects engineered to bypass China’s state-enforced internet censorship. Speculations abound that the attack aimed to coerce GitHub into scrapping these projects.
The attack’s traffic was engineered by inserting JavaScript code into users’ browsers visiting Baidu, China’s premier search engine. This malign code was also injected into websites employing Baidu’s analytics services, which, when triggered, prompted infected browsers to transmit HTTP requests to the specified GitHub pages. Subsequent investigations revealed that the malicious code did not originate from Baidu itself; instead, an intermediary service was found to be responsible for its addition.
Rob Graham, the CEO of Errata Security, has successfully identified the source of the malicious code as originating from China Unicom. This telecom provider had previously been implicated in supporting the extensive censorship mechanism known as the Great Firewall of China. Employing an innovative approach, the ethical hacker utilized a modified traceroute network diagnostic utility variant to uncover the origins. Instead of relying on the conventional UDP or ICMP packets, the adapted traceroute employed HTTP packets to meticulously trace their pathway across the Internet. This strategic adjustment enabled Graham to pinpoint the precise location of the node responsible for transmitting the malicious.
On the other hand, this attack was recorded as an example of how a piece of code placed on a legitimate website without even using a botnet could be an attack vector on a grand scale.
Mirai Botnet Attacks of 2016
In September 2016, during its peak, Mirai (botnet) orchestrated substantial Distributed Denial of Service attacks, causing temporary incapacitation to prominent services and websites, including OVH, Dyn, and Krebs on Security. These attacks reached unprecedented levels, surpassing 1 Tbps as reported by OVH, marking them as the most extensive on public record up to that date.
The remarkable aspect of these attacks was in their execution through unassuming Internet-of-Things (IoT) gadgets such as household routers, air quality monitors, and personal surveillance cameras. Mirai’s pinnacle saw the compromise of more than 600,000 susceptible IoT devices.
- Brian Krebs, a cybersecurity expert, encountered a staggering event in September 2016, when his blog fell victim to a DDoS attack surpassing 620 Gbps. This attack by Mirai Botnet established a new record at the time for its immense scale. Despite Krebs having documented 269 DDoS attacks since July 2012, this attack was nearly three times more substantial than any previous occurrence experienced by his website or the entire internet.
- Mirai also targeted OVH, a prominent hosting provider in Europe. According to their official statistics, OVH is responsible for hosting around 18 million applications catering to over a million clients, with notable entities like Wikileaks being among their most renowned and debated clients. Based on OVH’s telemetry data, the attack reached its maximum intensity at 1TBps and was executed by harnessing a network of 145,000 Internet of Things (IoT) devices.
On September 30, 2017, the individual nicknamed as Anna-senpai, suspected of being the creator of Mirai, made the Mirai source code public by sharing it on a notorious hacking forum. Alongside this release, a forum post was composed in which Anna-senpai declared their withdrawal from their activities. This event triggered a surge in imitative hackers who initiated their Mirai botnets. Following this juncture, the Mirai attacks ceased to be attributed to a solitary actor or infrastructure, instead becoming associated with numerous groups.
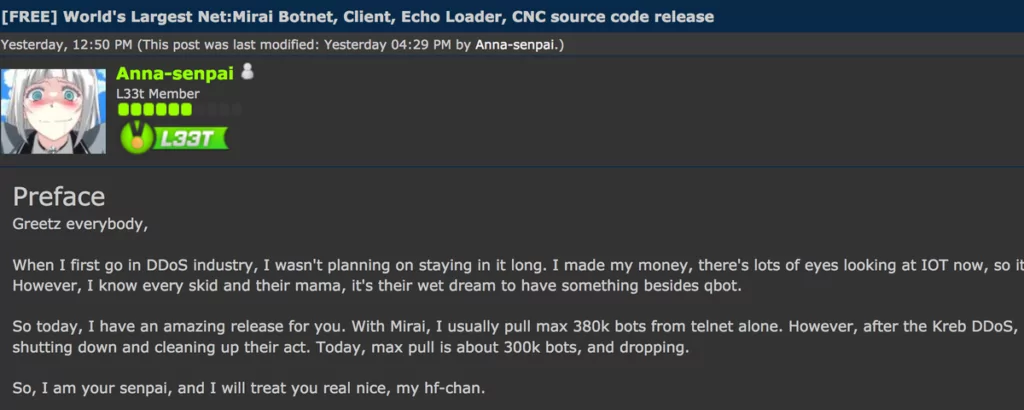
- As for the most famous attack of Mirai Botnet, on October 21, 2016, Dyn, a prominent provider of Domain Name System (DNS), encountered an onslaught of traffic reaching a staggering one terabit per second, setting a fresh benchmark for DDoS attacks. Some indications suggest that this DDoS assault might have surged to a rate of 1.5 terabits per second. The deluge of traffic resulted in the incapacitation of Dyn’s services, causing a range of renowned websites such as GitHub, HBO, Twitter, Reddit, PayPal, Netflix, and Airbnb to become inaccessible. Dyn’s Chief Strategy Officer Kyle York affirmed, “We identified tens of millions of distinct IP addresses linked to the Mirai botnet that played a role in the attack.”
The GitHub DDoS Attack of 2018
On February 28, 2018, GitHub encountered a formidable DDoS attack, measuring a staggering 1.35 terabits per second and enduring for approximately 20 minutes. According to GitHub’s assessment, the traffic originated from “over a thousand distinct autonomous systems spanning tens of thousands of unique endpoints.” Despite GitHub’s proactive preparations for a DDoS attack, their defensive measures were overwhelmed. They were completely unaware that an assault of such magnitude would be launched.
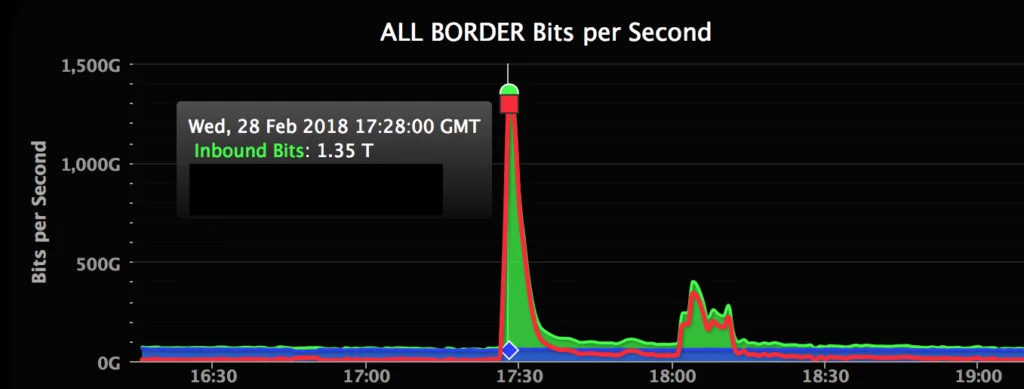
Hackers identified a chance to exploit the Memcached caching system by directly transmitting 1.3 Tbps of data to GitHub’s servers. Notably, this approach diverged from the conventional employment of a zombie bot network. The utilization of memcached servers enabled the hackers to magnify their assault by a staggering factor of 50,000. Luckily, the attack persisted for 20 minutes due to GitHub’s robust DDoS defense protocols. Within 10 minutes of the attack’s commencement, an alert was triggered, prompting the protection service to swiftly halt the DDoS assault before it could escalate beyond control.
The AWS Attack, 2020
In February 2020, Amazon Web Services experienced a colossal DDoS attack of unprecedented scale. This attack marked the most significant recent occurrence in DDoS attacks. It was directed at an undisclosed AWS client, utilizing a tactic known as Connectionless Lightweight Directory Access Protocol (CLDAP) reflection. This method exploits vulnerable third-party CLDAP servers, intensifying the volume of data directed toward the victim’s IP address by 56 to 70. The attack persisted for three days and reached its pinnacle at an astonishing 2.3 terabytes per second. Recently, numerous DDoS attacks have employed this same technique to undermine the security protocols of AWS.
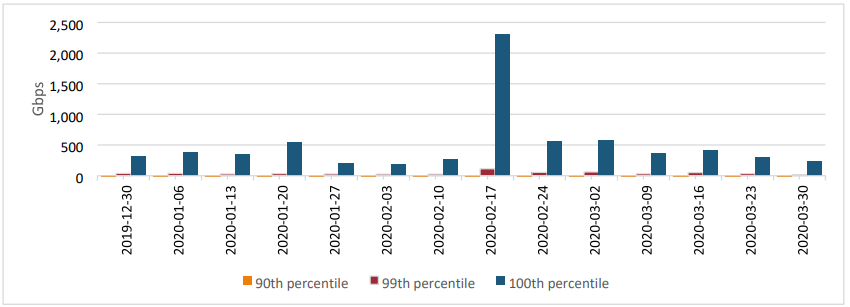
Fortuitously, Amazon managed to counteract the attack before it posed a security threat to its users. At that point in time, the assault on AWS stood as the most sizable DDoS attack ever recorded.
The DDoS Attack on Google’s Customer, 2022
According to Google’s blog: Starting from June 1, a customer utilizing Google Cloud Armor encountered a sequence of HTTPS-based DDoS attacks, reaching their peak at an astonishing 46 million requests per second. This occurrence marks the most substantial Layer 7 DDoS attack on record, surpassing the previously reported record by at least 76%. To put the scale of this attack into perspective, it is akin to receiving the total daily requests directed at Wikipedia within 10 seconds.
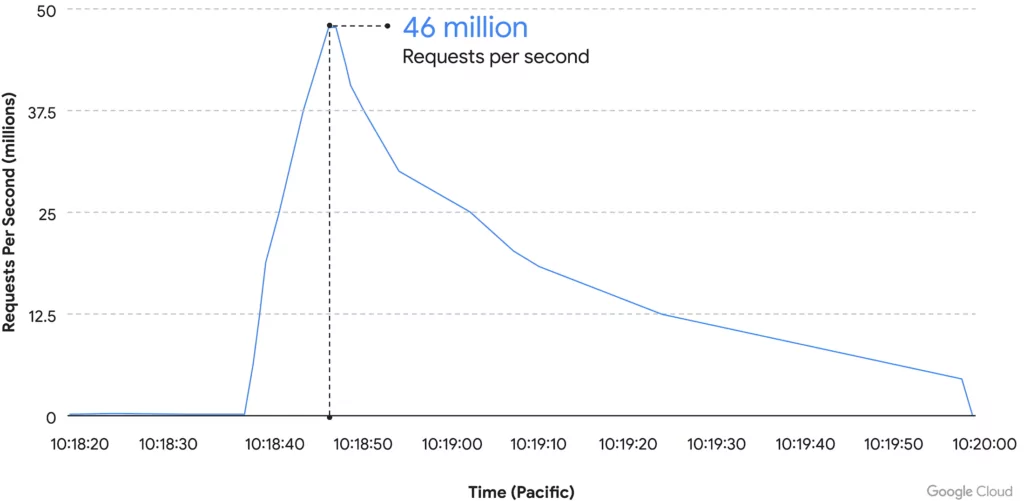
The incident reportedly commenced at around 9:45 a.m. PT, initiating with 10,000 requests per second, then rapidly surging to 100,000 RPS within eight minutes, followed by an additional escalation to a staggering 46 million RPS within just two more minutes, reaching its zenith at 10:18 a.m. PT. The entire DDoS assault persisted for a duration of 69 minutes.
Google highlighted, “The attack leveraged encrypted requests (HTTPS), which would have taken added computing resources to generate.” The characteristics of the geographical distribution and the types of vulnerable services exploited in this attack closely resembled the Mēris family of attacks. Another interesting point is that in September 2021, the Mēris botnet was linked to a DDoS attack on the Russian internet giant Yandex, reaching a peak of 21.8million RPS.
The Largest Reported HTTP DDoS attack, 2023
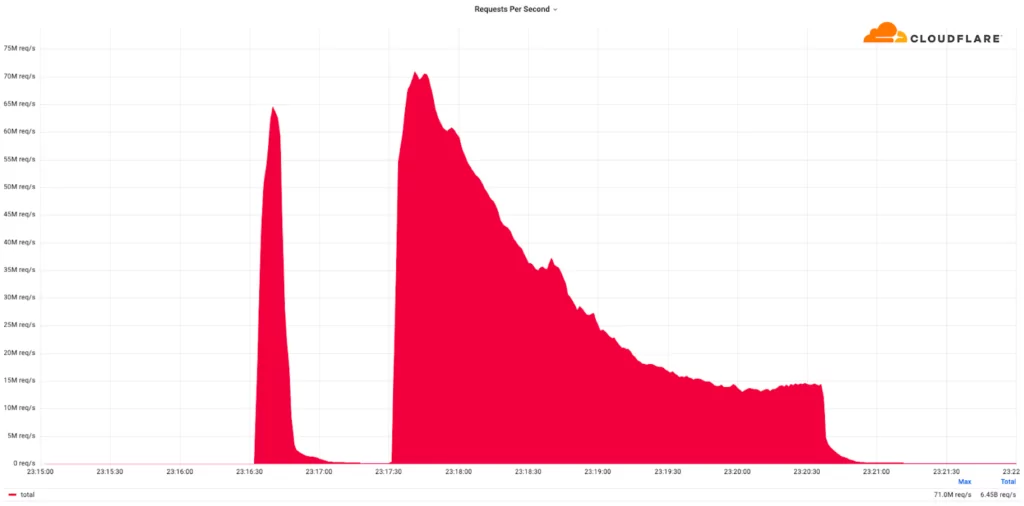
In February 2023, Cloudflare reported identifying and successfully mitigating the most colossal DDoS attack to date. This attack registered a staggering 71 million requests per second, surpassing the previous record of 46 million RPS set in June 2022 by over 54%. Subsequently, a series of attacks also emerged, reaching peak rates of 50-70 million RPS, as outlined by Cloudflare. The targets of these attacks included a popular gaming service, cryptocurrency companies, hosting providers, and cloud computing platforms.
Notably, this is not the first instance in which Cloudflare has asserted to have thwarted the “largest” DDoS attack on record. Nonetheless, the company acknowledged that these attacks are exhibiting an escalating trend in terms of size, complexity, and frequency.
Conclusion
To sum up, when we look at the attacks that have occurred over the years, we can see that both the frequency and volume of attacks have increased.
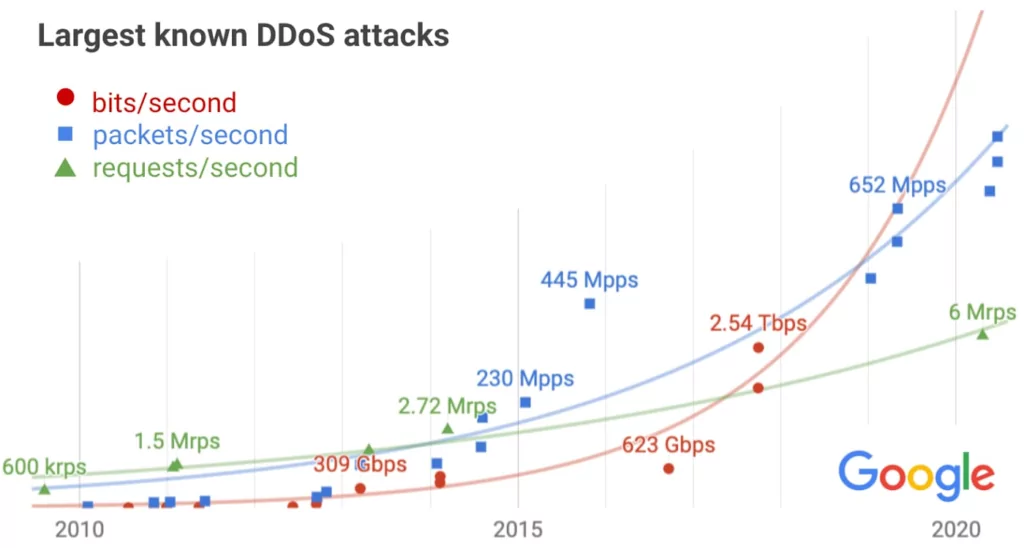
The rapid escalation of Distributed Denial of Service attacks, both in terms of their scale and complexity, underscores the urgent need for enterprises to bolster their defenses against these growing threats. To effectively safeguard against DDoS attacks, it is imperative to grasp their operational mechanisms and analyze the prevailing tactics. You can use the SOCRadar Labs-DOS Resiliency tab for free to measure your strength in this situation. The DoS Resilience Service allows you to check your domain’s or subnet’s resilience against DoS attacks such as slowloris attack, etc. After determining your strengths and weaknesses from DOS Resiliency, you can use the SOCRadar Attack Surface Management module, no matter what action you must take. Our solution for managing the external attack surface offers security teams immediate insight into all internet-exposed technological resources currently utilized, along with assets linked to IP, DNS, domain, and cryptographic infrastructure, facilitated by sophisticated algorithms for comprehensive internet-wide monitoring.
For more information on DDoS attacks and mitigation methods, check out our other blog post.






































